Contents [hide]
Performing a Compromise Assessment with ELK
In today’s digital landscape, organizations face an increasing number of cyber threats. Conducting a compromise assessment is vital to understanding vulnerabilities and safeguarding sensitive data. Performing a compromise assessment with ELK not only streamlines the process but also enhances your ability to analyze and visualize security data effectively. This guide will walk you through performing a comprehensive compromise assessment using the ELK stack (Elasticsearch, Logstash, and Kibana), offering in-depth insights and practical applications for your security team. By leveraging the capabilities of ELK, you can gain a clearer understanding of your security posture and respond more effectively to potential threats.
Understanding Compromise Assessments
A compromise assessment is a proactive measure to determine whether an organization has been breached or compromised. Unlike traditional audits, these assessments focus on uncovering undetected intrusions and assessing the overall security posture.
Why Choose the ELK Stack?
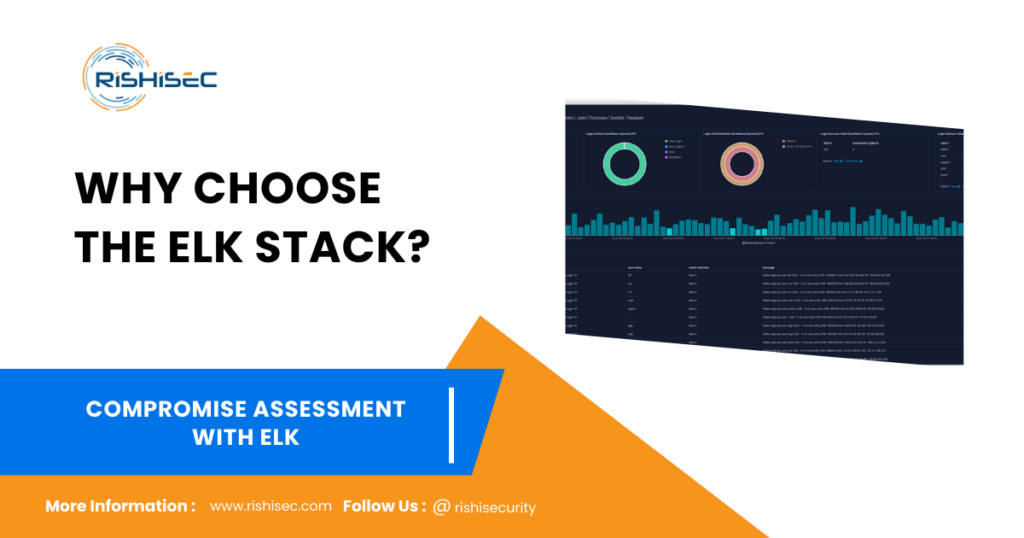
The ELK stack is a powerful tool for security analysis due to its ability to aggregate, analyze, and visualize log data. With Elasticsearch’s search capabilities, Logstash’s data processing, and Kibana’s visualization tools, security teams can gain real-time insights into potential threats.
- Elasticsearch: A distributed search and analytics engine that enables fast retrieval of data.
- Logstash: A data processing pipeline that ingests data from various sources and transforms it for storage in Elasticsearch.
- Kibana: A visualization tool that allows users to interact with data stored in Elasticsearch through dashboards and reports.
Steps to Perform a Compromise Assessment with ELK

Step 1: Define Objectives and Scope
Before starting your assessment, clarify your objectives. Are you investigating a specific incident, or are you conducting a routine check? Defining the scope will help tailor your approach and focus your resources effectively.
Step 2: Set Up the ELK Stack
- Install Elasticsearch, Logstash, and Kibana: Follow the official documentation to set up the ELK stack in your environment.
- Configure Data Sources: Identify and configure the logs you want to analyze—this may include server logs, firewall logs, and application logs.
Step 3: Ingest Data Using Logstash
Use Logstash to collect and process log data. Create configuration files to specify your input sources, filters, and output destinations. For example, you can filter out irrelevant log entries, ensuring that only pertinent data reaches Elasticsearch.
Step 4: Analyze Data in Elasticsearch
Once your data is ingested, leverage Elasticsearch’s powerful search capabilities to identify suspicious patterns and anomalies. Common indicators of compromise (IoCs) include unusual login attempts, unauthorized access to sensitive files, and unexpected changes to configurations.
Step 5: Visualize Findings with Kibana
Utilize Kibana to create informative dashboards that visualize your findings. Use graphs and charts to highlight trends and patterns in your data, making it easier to communicate findings to stakeholders. Dashboards can also help monitor ongoing activities in real time.
Step 6: Report and Remediate
Document your findings in a detailed report that outlines identified vulnerabilities, potential risks, and recommended remediation actions. Share this report with relevant teams to facilitate informed decision-making.
Best Practices for Effective Compromise Assessments

- Regular Assessments: Conduct compromise assessments regularly to stay ahead of potential threats.
- Collaborate with Teams: Engage different teams within your organization, such as IT and compliance, to gather comprehensive insights.
- Continuous Monitoring: Implement continuous monitoring of your network to detect threats as they arise.
Conclusion
Performing a compromise assessment with the ELK stack can significantly enhance your organization’s security posture. By following the steps outlined in this guide, you’ll be better equipped to identify and address potential vulnerabilities, ensuring your data remains protected.
CTA
Ready to strengthen your cybersecurity defenses? Try SentryCA for a free trial and discover how our solutions can help you perform effective compromise assessments and safeguard your organization against evolving threats.
Read this eye catchy post to know How to Respond to a Compromise: Best Practices


