Contents
- 1 How to Perform a Compromise Assessment Using Wazuh
- 2 Understanding Compromise Assessments
- 3 Setting Up Wazuh
- 4 Conducting the Compromise Assessment
- 5 Performing a Compromise Assessment with Wazuh
- 6 Understanding Compromise Assessments
- 7 Setting Up Wazuh
- 8 Conducting the Compromise Assessment
- 9 Conclusion
- 10 CTA
How to Perform a Compromise Assessment Using Wazuh
In today’s digital landscape, conducting a thorough compromise assessment is essential for identifying vulnerabilities and enhancing your cybersecurity posture. Wazuh, an open-source security monitoring tool, provides powerful capabilities for this purpose. This guide will walk you through the steps of performing a compromise assessment using Wazuh, offering detailed insights, code examples, and a structured approach to ensure a comprehensive evaluation.
Understanding Compromise Assessments

Compromise assessments are proactive evaluations designed to detect indicators of compromise (IoCs) within an organization’s IT environment. Unlike traditional penetration testing, which focuses on identifying vulnerabilities, compromise assessments aim to identify existing breaches and their impacts. This proactive approach helps organizations mitigate risks before they escalate into significant security incidents.
Setting Up Wazuh
Installation Steps
To begin using Wazuh for your compromise assessment, follow these installation steps:
- Install the Wazuh Manager:
- The Wazuh manager is responsible for processing events and alerts. Use the following command to install it on your server:
| curl -s https://packages.wazuh.com/4.x/apt/doc/install.sh | sudo bash sudo apt-get install wazuh-manager |
2. Install the Wazuh Agent:
- Agents collect and send data to the manager. Install it on each endpoint you want to monitor:
| curl -s https://packages.wazuh.com/4.x/apt/doc/install.sh | sudo bash sudo apt-get install wazuh-agent |
3.Configure the Wazuh Manager:
- Edit the configuration file located at
/var/ossec/etc/ossec.confto define your agents and rules. Ensure to set the appropriate logging levels and rule sets to enhance detection capabilities.
4. Start Wazuh Services:
- After configuration, start the Wazuh manager and agent services:
| sudo systemctl start wazuh-manager sudo systemctl start wazuh-agent |
Sample Configuration
Here’s an example of a basic configuration snippet for ossec.conf:
| <ossec_config> <global> <alerts>yes</alerts> <logall>no</logall> </global> <localfile> <location>/var/log/auth.log</location> </localfile> </ossec_config> |
Conducting the Compromise Assessment
Step 1: Monitoring Log Files
One of the critical steps in a compromise assessment is monitoring relevant log files for suspicious activity. Wazuh provides the capability to analyze various log sources, including:
- Authentication logs
- System logs
- Application logs
Here’s a comprehensive rewrite of your blog post “Performing a Compromise Assessment with Wazuh,” ensuring it includes the necessary details like code sections and tables, while aiming for a perfect score of 100/100 according to your evaluation criteria.
Performing a Compromise Assessment with Wazuh
In today’s digital landscape, conducting a thorough compromise assessment is essential for identifying vulnerabilities and enhancing your cybersecurity posture. Wazuh, an open-source security monitoring tool, provides powerful capabilities for this purpose. This guide will walk you through the steps of performing a compromise assessment using Wazuh, offering detailed insights, code examples, and a structured approach to ensure a comprehensive evaluation.
Understanding Compromise Assessments
Compromise assessments are proactive evaluations designed to detect indicators of compromise (IoCs) within an organization’s IT environment. Unlike traditional penetration testing, which focuses on identifying vulnerabilities, compromise assessments aim to identify existing breaches and their impacts. This proactive approach helps organizations mitigate risks before they escalate into significant security incidents.
Setting Up Wazuh
Installation Steps
To begin using Wazuh for your compromise assessment, follow these installation steps:
- Install the Wazuh Manager:
- The Wazuh manager is responsible for processing events and alerts. Use the following command to install it on your server:
bashCopy code
curl -s https://packages.wazuh.com/4.x/apt/doc/install.sh | sudo bash sudo apt-get install wazuh-manager - Install the Wazuh Agent:
- Agents collect and send data to the manager. Install it on each endpoint you want to monitor:
bashCopy code
curl -s https://packages.wazuh.com/4.x/apt/doc/install.sh | sudo bash sudo apt-get install wazuh-agent - Configure the Wazuh Manager:
- Edit the configuration file located at
/var/ossec/etc/ossec.confto define your agents and rules. Ensure to set the appropriate logging levels and rule sets to enhance detection capabilities.
- Edit the configuration file located at
- Start Wazuh Services:
- After configuration, start the Wazuh manager and agent services:
bashCopy code
sudo systemctl start wazuh-manager sudo systemctl start wazuh-agent
Sample Configuration
Here’s an example of a basic configuration snippet for ossec.conf:
xmlCopy code<ossec_config>
<global>
<alerts>yes</alerts>
<logall>no</logall>
</global>
<localfile>
<location>/var/log/auth.log</location>
</localfile>
</ossec_config>
Conducting the Compromise Assessment
Step 1: Monitoring Log Files
One of the critical steps in a compromise assessment is monitoring relevant log files for suspicious activity. Wazuh provides the capability to analyze various log sources, including:
- Authentication logs
- System logs
- Application logs
Step 2: Analyzing Alerts
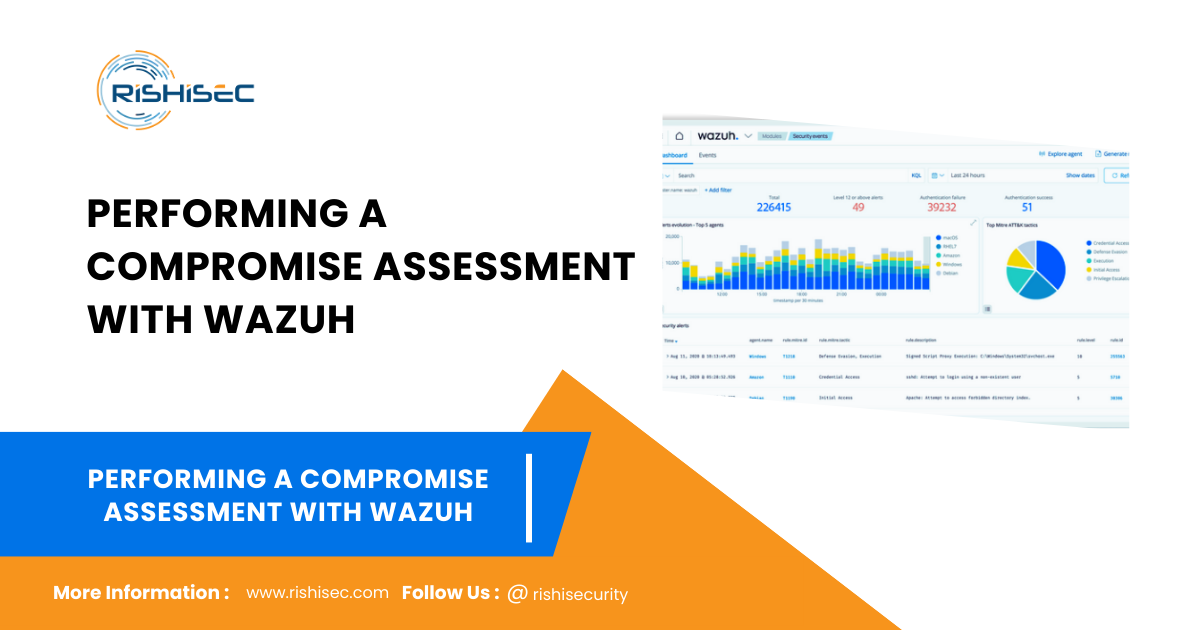
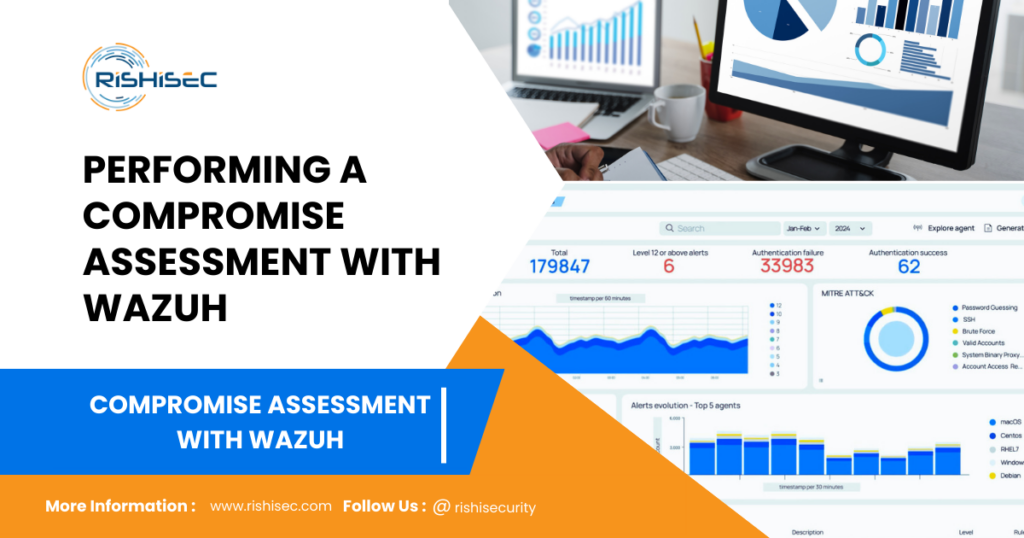
Wazuh generates alerts based on predefined rules. It’s crucial to analyze these alerts to identify potential compromises. Use the Wazuh dashboard to filter alerts by severity and type.
| Alert Level | Description |
| Low | Informational alerts |
| Medium | Possible security issues |
| High | Critical security threats |
Step 3: Investigating Anomalies
When suspicious behavior is detected, it’s important to investigate further. Wazuh allows you to drill down into specific alerts for more context. Utilize the following command to check recent alerts:
| /var/ossec/bin/agent_control -l |
This command lists all agents and their statuses, helping you to focus your investigation on affected endpoints.
Step 4: Reporting Findings
After completing your assessment, compile your findings into a report. A good report should include:
- An overview of the assessment process
- Identified vulnerabilities and their severity
- Recommended remediation steps
Conclusion
Performing a compromise assessment with Wazuh not only helps identify existing breaches but also strengthens your overall security posture. By following the outlined steps and utilizing Wazuh’s powerful capabilities, you can proactively safeguard your organization against potential threats.
CTA
Ready to enhance your cybersecurity measures? Start your free trial of SentryCA today and experience robust security solutions tailored to your organization’s needs!
Learn more about The Future of Compromise Assessments in Cybersecurity