Fraud investigators face an unprecedented challenge in today’s digital landscape. Moreover, with global fraud losses exceeding $5.8 trillion annually, traditional investigation methods are no longer sufficient to combat sophisticated online deception schemes. Consequently, modern fraudsters exploit digital platforms, social media networks, and encrypted communications to orchestrate complex schemes that span multiple jurisdictions and platforms.
Open Source Intelligence has emerged as a game-changing methodology for fraud investigation units. Furthermore, OSINT fraud investigation techniques enable investigators to track digital footprints, unmask false identities, and correlate evidence across multiple platforms without alerting suspects. These methods have proven particularly effective in combating insurance fraud, online romance scams, and marketplace deception schemes.
This comprehensive guide explores advanced OSINT methodologies specifically designed for fraud investigation applications. Additionally, from analyzing social media metadata to tracking cryptocurrency transactions, these techniques provide fraud investigators with the tools needed to combat digital deception in an increasingly complex threat environment.
Understanding Modern Fraud Patterns Through OSINT
OSINT fraud investigation techniques require specialized approaches that can identify deception indicators across multiple digital platforms. Subsequently, modern fraud schemes often involve sophisticated social engineering, identity theft, and cross-platform coordination that traditional investigation methods struggle to detect effectively.
Contemporary insurance fraud schemes extend beyond simple claim exaggeration. Therefore, fraudsters now create elaborate digital personas, fabricate supporting evidence, and coordinate with networks of accomplices across social media platforms. Fraud investigators need comprehensive analytical frameworks that can process vast amounts of digital evidence while maintaining legal admissibility standards.
Advanced fraud detection requires understanding how criminals exploit legitimate platforms for illicit purposes. Dating apps, social media networks, online marketplaces, and professional networking sites all provide opportunities for fraudsters to establish credibility while executing deception schemes.
Furthermore, OSINT fraud investigation techniques must account for evolving criminal methodologies. Sophisticated fraud networks now employ operational security measures, encrypted communications, and distributed infrastructure to avoid detection by traditional investigative approaches.
Social Media Intelligence for Fraud Detection
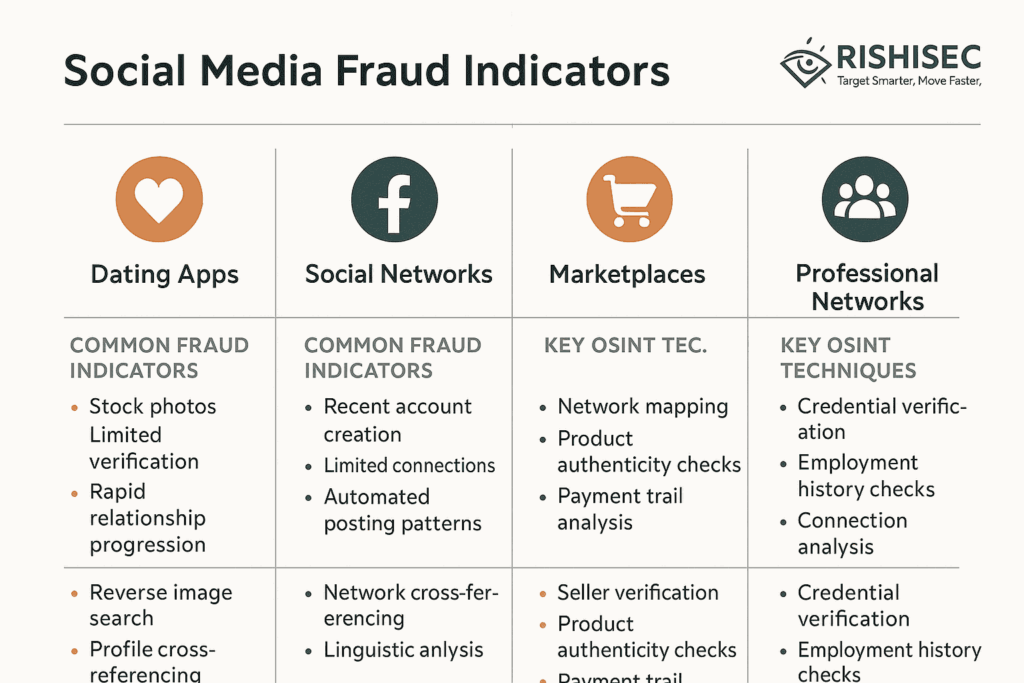
Social media analysis represents a cornerstone of modern OSINT fraud investigation techniques. Consequently, fraud investigators must master methods for detecting fabricated profiles, identifying coordinated deception networks, and correlating activities across multiple platforms simultaneously.
| Platform Type | Common Fraud Indicators | Key OSINT Techniques |
|---|---|---|
| Dating Apps | Stock photos, limited verification, rapid relationship progression | Reverse image search, profile cross-referencing, linguistic analysis |
| Social Networks | Recent account creation, limited connections, automated posting patterns | Network mapping, temporal analysis, engagement pattern recognition |
| Marketplaces | Too-good prices, poor seller history, payment method restrictions | Seller verification, product authenticity checks, payment trail analysis |
| Professional Networks | Inflated credentials, fake endorsements, suspicious job histories | Credential verification, employment history checks, connection analysis |
Profile authentication has become increasingly complex as fraudsters employ sophisticated techniques to create convincing fake identities. Therefore, investigators need technical capabilities that can analyze profile creation patterns, image authenticity, connection networks, and behavioral indicators that reveal deceptive intentions.
Metadata analysis provides valuable insights into fraudulent activities that criminals often overlook. Photo metadata can reveal location discrepancies, device information, and temporal inconsistencies that contradict fraudulent claims. Additionally, posting patterns and linguistic analysis can identify coordinated accounts or reveal geographic locations that contradict claimed identities.
Advanced platforms like Kindi enable fraud investigation teams to automate social media analysis across multiple platforms simultaneously. By correlating posting patterns, connection networks, and content similarities, these tools help investigators identify fraud networks that would be impossible to detect through manual analysis methods.
Cross-platform correlation has become essential for modern fraud investigations. Criminals often maintain multiple social media profiles across different platforms, requiring investigators to track activities and connections across diverse digital environments while maintaining the integrity of evidence for legal proceedings.
Financial Intelligence and Transaction Analysis
Effective OSINT fraud investigation techniques must include comprehensive financial intelligence capabilities that can trace money flows and identify suspicious transaction patterns. Moreover, modern fraud schemes often involve complex financial networks that span traditional banking systems, digital payment platforms, and cryptocurrency exchanges.
Cryptocurrency analysis has become particularly important for fraud investigations as many schemes now involve digital assets to obscure money trails. Therefore, investigators need blockchain analysis capabilities that can trace transactions, identify wallet clusters, and correlate cryptocurrency activities with traditional financial systems.
Digital payment platforms provide valuable intelligence sources for fraud investigations. Payment histories, transaction patterns, and associated account information can reveal connections between seemingly unrelated fraud schemes. However, investigators must understand legal requirements and platform-specific data access procedures.
Traditional financial intelligence remains crucial for comprehensive fraud investigations. Bank records, credit reports, and financial disclosure documents provide essential context for understanding fraud schemes and identifying additional victims or co-conspirators.
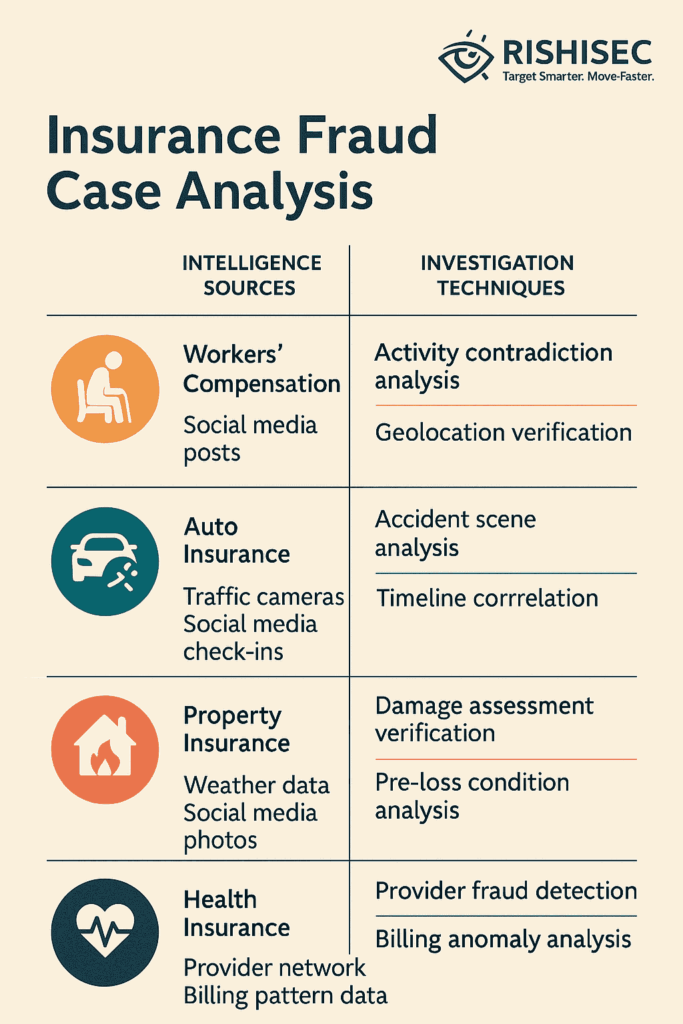
Insurance Fraud Investigation Methods
Insurance fraud represents a specialized application area where OSINT fraud investigation techniques prove particularly valuable. Furthermore, insurance fraud investigators must develop capabilities that can verify claim authenticity, detect exaggerated losses, and identify coordinated fraud schemes.
| Insurance Fraud Type | OSINT Evidence Sources | Investigation Techniques |
|---|---|---|
| Workers’ Compensation | Social media posts, GPS metadata, public surveillance footage | Activity contradiction analysis, geolocation verification, timeline reconstruction |
| Auto Insurance | Traffic cameras, social media check-ins, repair shop records | Accident scene analysis, vehicle history tracking, staged accident detection |
| Property Insurance | Weather data, social media photos, public records, satellite imagery | Damage assessment verification, timeline correlation, pre-loss condition analysis |
| Health Insurance | Provider network analysis, billing pattern data, patient social media | Provider fraud detection, billing anomaly analysis, treatment verification |
Claim verification requires multi-source intelligence that can confirm or contradict information provided in insurance applications and claims. Social media analysis can reveal activities that contradict claimed injuries or disabilities, while public records research can identify patterns of suspicious claims or undisclosed assets.
Geolocation analysis has become essential for insurance fraud investigations. GPS metadata from photos and social media posts can reveal location discrepancies, while surveillance footage and public cameras can provide independent verification of claimed events. These techniques prove particularly effective when investigating workers’ compensation fraud or staged accident claims.
The integration of OSINT techniques with traditional investigation methods enhances overall effectiveness. For instance, combining OSINT approaches with conventional law enforcement methodologies, as demonstrated in comprehensive OSINT guides for law enforcement investigations, creates more robust investigative frameworks.
Network analysis helps identify coordinated insurance fraud schemes involving multiple claimants, medical providers, or legal representatives. By mapping relationships between parties involved in suspicious claims, investigators can uncover larger fraud conspiracies that individual case analysis might miss.
Advanced Technical Investigation Techniques
Modern OSINT fraud investigation techniques utilize advanced technical capabilities that can analyze digital evidence at scale while adhering to legal admissibility standards. Subsequently, fraud investigation teams need automated tools that can process vast datasets while identifying subtle indicators of deception.
| Technical Analysis Type | Data Sources | Fraud Detection Applications |
|---|---|---|
| Metadata Analysis | Image EXIF data, document properties, communication headers | Location verification, device identification, timestamp validation |
| Blockchain Analysis | Cryptocurrency transactions, wallet addresses, exchange records | Money laundering detection, asset tracing, payment verification |
| Network Correlation | Domain registrations, IP addresses, hosting services | Infrastructure mapping, campaign attribution, coordination detection |
| Behavioral Analytics | Posting patterns, response times, linguistic markers | Bot detection, coordinated account identification, geographic profiling |
Image analysis has become increasingly sophisticated, enabling investigators to detect manipulated photos, identify stock images used in fraudulent profiles, and extract hidden metadata that reveals essential case details. Reverse image searching and facial recognition capabilities help identify recycled images and false identities across multiple platforms.
Communication pattern analysis offers valuable insights into the operations of fraud networks. By analyzing messaging patterns, response times, and linguistic characteristics, investigators can identify coordinated accounts, reveal geographic locations, and predict fraudulent activities before they fully develop.
Technical infrastructure analysis enables investigators to understand the digital backbone supporting fraudulent operations. Domain registration records, hosting services, and content delivery networks can reveal connections between seemingly unrelated fraud schemes and identify command-and-control infrastructure.
Additionally, specialized OSINT techniques developed for tracking criminal networks on social media provide valuable methodologies that fraud investigators can adapt for their specific investigation requirements.
According to the FBI’s Financial Crimes Section, the integration of open-source intelligence techniques has significantly enhanced the capabilities of fraud investigation and prosecution success rates across federal and local law enforcement agencies.
Online Fraud Detection Across Digital Platforms
OSINT fraud investigation techniques must address the diverse landscape of online fraud schemes across dating apps, marketplaces, and social networks. Therefore, investigators need specialized approaches for each platform type while maintaining consistent analytical standards.
Dating app fraud investigations require an understanding of how scammers create convincing romantic personas and gradually manipulate victims into participating in financial schemes. Social media cross-referencing, reverse image searches, and linguistic analysis help investigators identify recycled profiles and coordinated romance scam operations.
Marketplace fraud schemes often involve fake seller profiles, counterfeit products, and payment manipulation tactics. Consequently, investigators must analyze seller histories, product authenticity indicators, and payment processing networks to identify fraudulent operations and protect potential victims.
Advanced fraud schemes now target specialized communities, including professional networks, gaming platforms, and cryptocurrency exchanges. Each environment requires tailored OSINT fraud investigation techniques that account for platform-specific communication patterns and community behaviors.
The Federal Trade Commission’s fraud data highlights the increasing sophistication of online fraud schemes and underscores the crucial importance of advanced investigative techniques in protecting consumers and prosecuting offenders.
Implementation Framework for Fraud Investigation Units
Successful deployment of OSINT fraud investigation techniques requires systematic planning and resource allocation across fraud investigation teams. Consider these essential implementation elements:
- Establish a secure investigation infrastructure with appropriate legal safeguards and evidence preservation protocols for court proceedings
- Develop specialized training programs for fraud investigators covering advanced OSINT techniques and legal compliance requirements.
- Implement automated fraud detection systems for high-risk indicators and suspicious activity patterns across multiple platforms.
- Create secure case management platforms for multi-investigator collaboration and evidence sharing while maintaining case integrity.
- Design legal compliance frameworks that ensure evidence admissibility while enabling effective investigation capabilities
- Establish source verification protocols designed explicitly for fraud investigation intelligence and evidence authentication.
- Develop rapid response procedures for addressing time-sensitive fraud schemes and asset recovery operations.
- Create inter-agency coordination mechanisms for complex fraud cases involving multiple jurisdictions or victim group.s
Fraud investigation units should also consider partnerships with financial institutions, technology companies, and law enforcement agencies that can provide additional intelligence sources and investigative support.
Emerging Technologies and Future Considerations
The future of OSINT fraud investigation techniques lies in the integration of artificial intelligence and predictive analytics, which can identify fraud patterns before schemes fully develop. Furthermore, machine learning algorithms can process enormous datasets while identifying subtle deception indicators that human investigators might overlook.
However, technology integration must be balanced with human expertise and legal requirements. While AI can enhance collection and initial analysis, experienced fraud investigators remain essential for contextual interpretation, evidence evaluation, and the preparation of legal testimony.
Fraud investigation teams should prepare for emerging challenges, including deepfake technology, advanced identity theft techniques, and quantum-resistant encryption methods. Therefore, these evolving threats require proactive capability development and continuous training programs.
Investment in next-generation OSINT platforms will become increasingly important for maintaining investigative effectiveness. Tools that offer advanced correlation capabilities, automated evidence collection, and secure collaboration features will provide significant advantages for fraud investigation operations.
FAQ
What makes fraud investigation OSINT different from general intelligence gathering?
OSINT fraud investigation techniques focus specifically on deception detection, evidence preservation, and legal admissibility requirements. Therefore, fraud investigators need specialized skills in financial analysis, identity verification, and evidence documentation that differ from general intelligence applications.
How can fraud investigators ensure OSINT evidence is legally admissible?
Legal admissibility requires proper evidence collection procedures, a chain of custody documentation, and compliance with privacy regulations. Additionally, investigators must understand jurisdiction-specific requirements and maintain detailed records of investigation methodologies and source verification procedures.
What are the most critical technical skills for fraud investigators using OSINT?
Essential skills include social media analysis, financial intelligence, metadata extraction, and digital forensics capabilities. Moreover, investigators require strong analytical thinking, awareness of legal compliance, and practical communication skills to present complex findings in legal proceedings.
How should fraud investigation units assess the effectiveness of OSINT tools?
Evaluation should focus on accuracy, legal compliance features, integration capabilities, and the effectiveness of case resolution. Therefore, units should consider evidence quality, investigation speed, and successful prosecution rates when assessing tool performance and return on investment.
Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training. Ready to revolutionize your fraud investigations? Discover how Kindi can streamline your OSINT investigations and enhance your team’s analytical capabilities with advanced link analysis and automated intelligence gathering.


