Every day, SOC teams across law enforcement, defense, and private organizations drown in an ocean of cybersecurity information. Log entries, IP addresses, domain names, and malware hashes flood their systems. However, most of this information remains just that: raw data that creates noise rather than clarity.
The critical distinction between threat data and threat intelligence determines whether security teams respond effectively to genuine threats or waste valuable time chasing false leads. Understanding this difference can transform your organization’s cybersecurity posture from reactive to proactive.
What Is Threat Data?
Threat data represents raw, unprocessed information collected from various cybersecurity sources. This includes IP addresses from firewall logs, domain names from DNS queries, file hashes from antivirus systems, and vulnerability scan results.
While threat data provides the foundation for security operations, it lacks context and analysis. For example, an IP address flagged as malicious tells you nothing about the attack campaign, threat actor motivation, or appropriate response measures.
Common examples of threat data include:
- IP addresses and domain names from security feeds
- Malware signatures and file hashes
- Network traffic logs and connection records
- Vulnerability scan results and patch status reports
- Security alert notifications from various tools
- User behavior logs and access records
The challenge with raw threat data is its volume and noise ratio. Organizations typically collect thousands of indicators daily, but most lack sufficient context to drive meaningful security decisions.
What Is Threat Intelligence?
Threat intelligence transforms raw data into actionable information through analysis, correlation, and contextualization. It answers critical questions about threat actor motivations, attack methodologies, and potential impacts on your specific organization.
True threat intelligence operates at three distinct levels, each serving different organizational needs and decision-making processes.
Strategic Threat Intelligence
Strategic intelligence provides high-level insights for executive decision-making. It focuses on long-term trends, geopolitical factors, and industry-specific threats that affect business strategy and resource allocation.
Operational Threat Intelligence
Operational intelligence supports campaign-level security operations. It identifies attack patterns, threat actor capabilities, and campaign indicators that help security teams understand ongoing threats and plan defensive measures.
Tactical Threat Intelligence
Tactical intelligence provides immediate, actionable information for frontline security operations. It includes indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs) that enable rapid detection and response.
| Intelligence Level | Audience | Purpose | Timeline |
|---|---|---|---|
| Strategic | Executives, Board Members | Business risk assessment, resource allocation | 6-12 months |
| Operational | Security Managers, Team Leaders | Campaign tracking, threat hunting | Weeks to months |
| Tactical | SOC Analysts, Incident Responders | Detection, blocking, immediate response | Hours to days |
Key Differences Between Threat Data and Threat Intelligence
Understanding the fundamental differences between data and intelligence enables security teams to focus their efforts more effectively. These differences impact everything from tool selection to analyst training and operational procedures.
Context and Analysis
Threat data lacks context about attack campaigns, threat actor motivations, or potential impact on your organization. In contrast, threat intelligence provides rich context that enables informed decision-making and appropriate response measures.
Actionability
Raw data requires significant analysis before it becomes actionable. Intelligence, however, comes pre-analyzed with clear recommendations for security teams. This distinction dramatically affects response times and effectiveness.
Relevance
Threat data often includes information irrelevant to your organization’s risk profile. Threat intelligence focuses on threats specifically relevant to your industry, geography, and technology stack.
| Aspect | Threat Data | Threat Intelligence |
|---|---|---|
| Context | Minimal or none | Rich contextual information |
| Processing | Raw, unanalyzed | Analyzed and correlated |
| Actionability | Requires interpretation | Immediately actionable |
| Relevance | Often generic | Tailored to organization |
| Volume | High volume, high noise | Focused, filtered content |
Why Threat Intelligence Matters for Security Operations
The transformation from data to intelligence directly impacts security team effectiveness. Organizations that successfully make this transition report significant improvements in threat detection, response times, and overall security posture.
Reducing False Positives
Quality threat intelligence helps security teams distinguish between genuine threats and benign activities. This reduction in false positives allows analysts to focus on real security incidents rather than investigating harmless anomalies.
Organizations using contextual threat intelligence report up to 70% reduction in false positive rates. Consequently, analyst productivity increases while alert fatigue decreases significantly.
Improving Attribution
Threat intelligence enables better attribution of security incidents to specific threat actors or campaigns. This understanding helps law enforcement teams build stronger cases and supports strategic security planning.
Enhancing Incident Response
When security incidents occur, threat intelligence provides critical context about attack methodologies, likely next steps, and appropriate countermeasures. This information accelerates response times and improves containment effectiveness.
Transforming Data Into Intelligence With OSINT
Open Source Intelligence (OSINT) plays a crucial role in converting raw threat data into actionable intelligence. By correlating internal security data with external sources, organizations gain comprehensive visibility into threat landscapes.
For example, an IP address flagged by internal systems becomes more meaningful when OSINT research reveals its association with specific malware campaigns or threat actor groups. This context enables appropriate response measures and helps predict potential attack evolution.
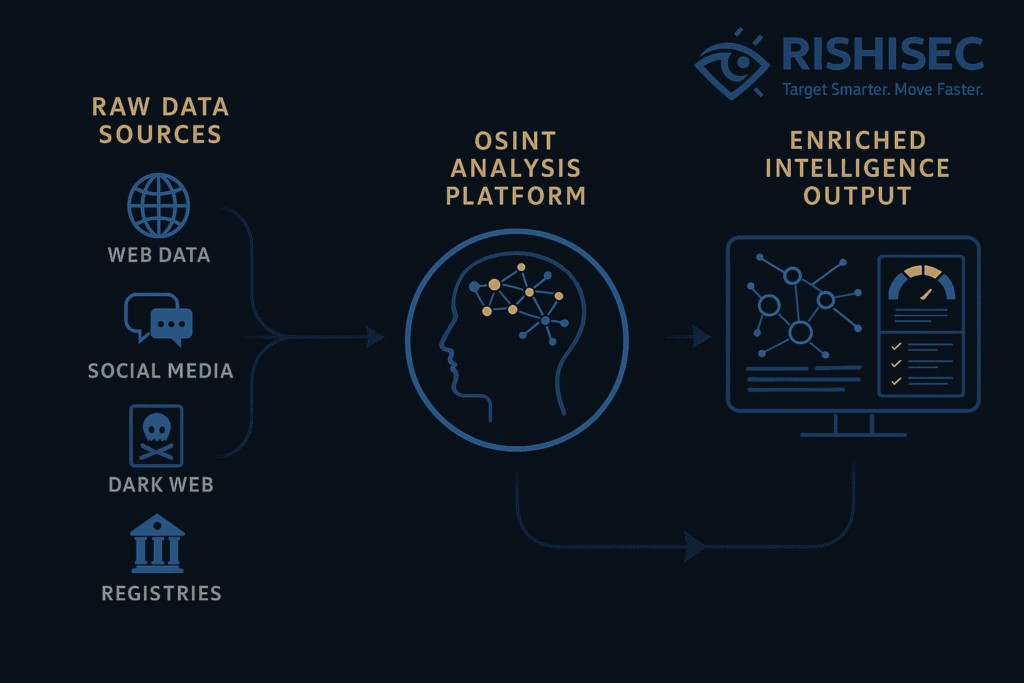
How Kindi Transforms Threat Data Into Intelligence
RishiSec’s Kindi platform exemplifies how modern OSINT tools transform raw threat data into actionable intelligence. Through automated correlation and AI-powered analysis, Kindi helps security teams overcome information overload.
The platform ingests threat feeds from multiple sources and applies machine learning algorithms to identify patterns and relationships. This automated analysis provides the context that transforms generic indicators into organization-specific intelligence.
Furthermore, Kindi’s link analysis capabilities visualize complex relationships between threat indicators, helping analysts understand attack campaigns and predict threat evolution. This visual approach makes complex intelligence accessible to analysts at all skill levels.
For SOC environments, Kindi’s automated enrichment reduces the time required to investigate alerts from hours to minutes. Analysts receive pre-analyzed intelligence that enables immediate decision-making and appropriate response actions.
Best Practices for Intelligence-Driven Security
- Establish clear intelligence requirements aligned with organizational risk priorities
- Implement automated correlation tools to identify relationships between disparate data points
- Develop standardized processes for intelligence analysis and dissemination
- Create feedback loops to validate intelligence accuracy and relevance
- Train analysts to think beyond indicators and consider broader campaign context
- Integrate threat intelligence platforms with existing security tools and workflows
- Regularly review and update intelligence sources to maintain relevance and quality
The Future of Threat Intelligence
Artificial intelligence and machine learning technologies will continue transforming how organizations process threat data. Automated analysis tools will handle routine correlation tasks, allowing human analysts to focus on strategic intelligence development and complex threat hunting.
The integration of OSINT capabilities into security operations will become standard practice. Organizations need external context to understand how internal security events fit into broader threat campaigns and industry trends.
Moreover, threat intelligence sharing between organizations will expand, creating collective defense capabilities that benefit entire industries. Platforms that facilitate secure intelligence sharing while protecting sensitive information will become increasingly valuable.
For organizations serious about improving their security posture, the message is clear: data alone isn’t enough. The future belongs to those who can transform information into intelligence and intelligence into effective action.
Want to strengthen your OSINT skills and threat analysis capabilities? Check out our OSINT courses for practical, hands-on training that prepares you for modern threat intelligence operations.
Ready to transform your threat data into actionable intelligence? Discover how Kindi automates the intelligence analysis process and helps your team focus on what matters most.
FAQ
What is the main difference between threat data and threat intelligence?
Threat data consists of raw, unprocessed information like IP addresses and file hashes, while threat intelligence is analyzed, contextualized information that provides actionable insights about threats, their origins, and appropriate response measures.
How can organizations improve their threat intelligence capabilities?
Organizations should invest in automated correlation tools, establish clear intelligence requirements, train analysts in advanced analysis techniques, and implement platforms that can enrich raw data with external context from OSINT sources.
Why do many SOC teams struggle with threat intelligence?
Many teams lack the tools and processes to transform raw data into intelligence. They often have access to vast amounts of data but struggle to identify relevant patterns, add context, and create actionable insights from the information.
How does OSINT contribute to threat intelligence development?
OSINT provides external context that enriches internal security data. By correlating internal indicators with open source information, security teams can understand threat actor motivations, campaign objectives, and attack patterns that aren’t visible from internal data alone.
What skills do analysts need for effective threat intelligence work?
Analysts need strong analytical thinking skills, understanding of threat actor tactics and techniques, familiarity with intelligence frameworks like MITRE ATT&CK, and proficiency with analysis tools and platforms that can correlate and visualize complex threat data.