Traditional vulnerability management approaches are undeniably failing organizations worldwide. While security teams scramble to patch thousands of vulnerabilities, attackers exploit the gaps that periodic scans miss. The solution? Continuous Threat Exposure Management (CTEM) is a revolutionary framework that transforms how organizations discover, assess, and remediate security exposures in real-time.
For SOC analysts, law enforcement teams, and defense organizations, understanding CTEM isn’t just beneficial. It’s essential for staying ahead of sophisticated threat actors who never sleep.
Understanding Continuous Threat Exposure Management (CTEM)
Continuous Threat Exposure Management represents a fundamental shift from reactive vulnerability management to proactive exposure management. Moreover, Gartner formally introduced this framework to address the growing complexity of modern attack surfaces that span cloud environments, IoT devices, and distributed networks.
Unlike traditional approaches that rely on scheduled scans and static asset inventories, CTEM provides continuous visibility into an organization’s security posture. Furthermore, it combines automated discovery with real-world attack simulation to identify genuine risks rather than theoretical vulnerabilities.
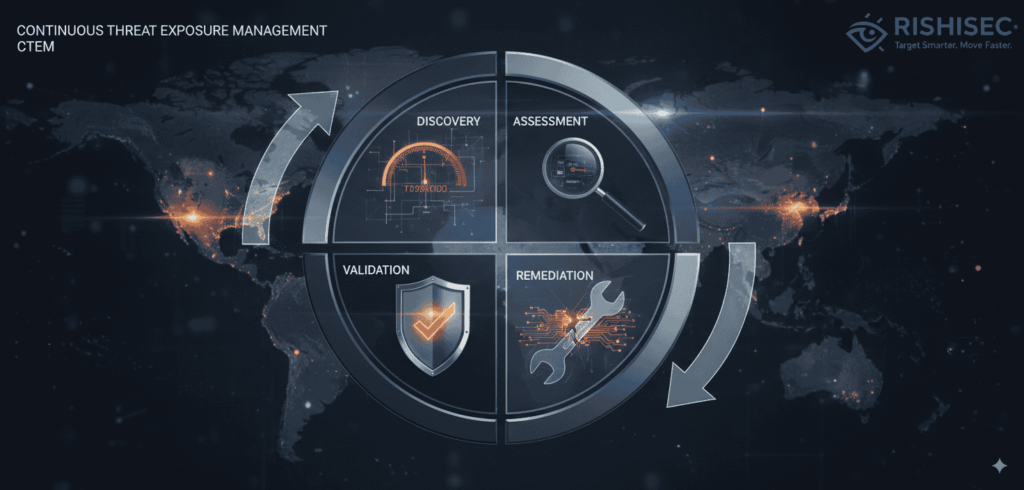
The Four Phases of CTEM Implementation
CTEM operates through a continuous cycle that ensures comprehensive security coverage. Each phase builds upon the previous one, creating a self-reinforcing loop of improvement.
Discovery: Mapping Your Complete Attack Surface
The discovery phase involves comprehensive asset identification across all environments. This includes cloud instances, on-premises systems, mobile devices, and third-party integrations. Additionally, it encompasses shadow IT assets that traditional inventory systems often miss.
Organizations typically discover 30-40% more assets than their existing inventory systems reveal. These unknown assets represent significant blind spots that attackers frequently exploit.
Assessment: Evaluating Real-World Risk
Assessment goes beyond simple vulnerability scoring to evaluate actual exploitability. This phase considers threat intelligence, attack trends, and environmental context to determine genuine risk levels.
For instance, a critical vulnerability in an isolated development system poses less immediate risk than a medium-severity flaw in a public-facing application. CTEM frameworks account for these contextual factors.
Validation: Simulating Attack Scenarios
Validation involves testing identified exposures through controlled attack simulations. This phase confirms whether theoretical vulnerabilities translate into practical attack paths.
Organizations using validation techniques reduce false positives by up to 75%. Consequently, security teams can focus resources on genuine threats rather than chasing phantom vulnerabilities.
Remediation: Prioritizing and Fixing Issues
The remediation phase prioritizes fixes based on validated risk levels and business impact. This approach ensures that critical exposures receive immediate attention while lower-priority items are scheduled appropriately.
| CTEM Phase | Key Activities | Expected Outcomes |
|---|---|---|
| Discovery | Asset mapping, surface enumeration, inventory updates | Complete visibility into attack surface |
| Assessment | Risk evaluation, threat correlation, context analysis | Prioritized vulnerability list with business context |
| Validation | Attack simulation, penetration testing, proof of concept | Confirmed exploitable vulnerabilities and attack paths |
| Remediation | Patch deployment, configuration changes, risk mitigation | Reduced exposure and improved security posture |
CTEM vs Traditional Vulnerability Management
Traditional vulnerability management relies on periodic scanning and generic risk scoring. However, this approach creates significant gaps between scan cycles and fails to account for real-world attack scenarios.
CTEM addresses these limitations through continuous monitoring and contextual analysis. While traditional methods might identify thousands of vulnerabilities, CTEM focuses on the subset that represent genuine threats to your organization.
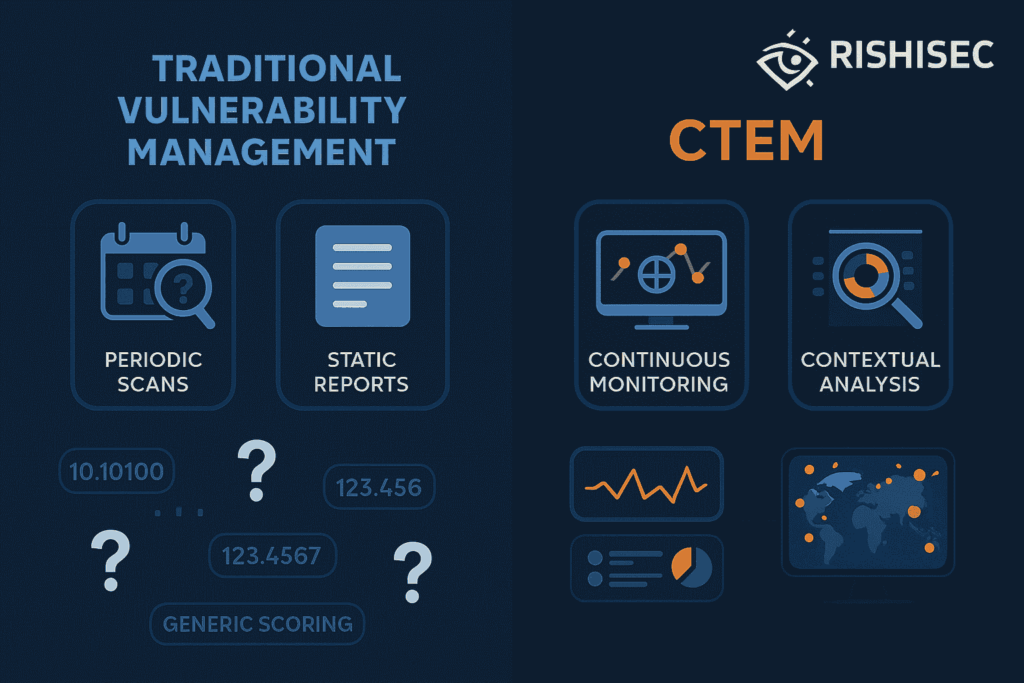
The business impact of this shift is substantial. Organizations implementing CTEM report 60% faster remediation times and 45% reduction in successful attacks. Furthermore, security teams experience less alert fatigue and can focus on strategic initiatives rather than chasing false positives.
Why CTEM Matters More Than Ever
Several trends make CTEM increasingly critical for modern organizations. First, attack surfaces continue expanding through cloud adoption, remote work, and IoT deployment. Traditional inventory systems struggle to track these dynamic environments.
Second, artificial intelligence empowers both attackers and defenders. While AI helps security teams analyze threats faster, it also enables attackers to identify and exploit vulnerabilities more efficiently. CTEM frameworks must evolve to address AI-driven threats.
Third, regulatory requirements increasingly demand continuous monitoring and rapid response capabilities. Government agencies and private organizations face growing compliance obligations that traditional vulnerability management cannot meet.
How Kindi Enables CTEM in Practice
RishiSec’s Kindi platform transforms CTEM from theoretical framework into practical reality. Through AI-powered OSINT automation, Kindi provides the continuous discovery and assessment capabilities that CTEM requires.
The platform integrates multiple threat intelligence feeds to provide real-time context for discovered assets and vulnerabilities. Additionally, Kindi’s link analysis capabilities help security teams understand attack paths and prioritize remediation efforts effectively.
For law enforcement and defense organizations, Kindi’s collaboration features enable coordinated response to emerging threats. The platform’s automated reporting reduces administrative burden while ensuring stakeholders receive timely updates on security posture changes.
Implementing CTEM: Best Practices
- Start with comprehensive asset discovery across all environments and business units
- Integrate multiple threat intelligence sources for contextual vulnerability assessment
- Establish automated workflows for continuous monitoring and alert generation
- Implement attack simulation capabilities to validate identified exposures
- Create clear escalation procedures and remediation playbooks for different risk levels
- Ensure cross-team collaboration between security, IT, and business stakeholders
- Regularly review and update CTEM processes based on emerging threats and lessons learned
The Future of Exposure Management
CTEM represents the evolution of cybersecurity from reactive patching to proactive risk management. As attack surfaces continue expanding and threats become more sophisticated, organizations need frameworks that provide continuous visibility and context-aware prioritization.
The integration of OSINT capabilities into CTEM frameworks will become increasingly important. SOC teams require external threat intelligence to understand how their vulnerabilities fit into the broader threat landscape.
Furthermore, artificial intelligence will play a crucial role in automating CTEM processes and reducing the manual effort required for effective implementation. Organizations that embrace these technologies today will be better positioned to defend against tomorrow’s threats.
Want to strengthen your OSINT skills and cybersecurity capabilities? Check out our OSINT courses for practical, hands-on training that prepares you for modern threat landscapes.
Ready to experience CTEM in action? Discover how Kindi transforms threat exposure management through AI-powered OSINT automation and collaborative intelligence analysis.
FAQ
What is the main difference between CTEM and traditional vulnerability management?
CTEM provides continuous monitoring and contextual risk assessment, while traditional vulnerability management relies on periodic scans and generic scoring. CTEM focuses on real-world exploitability rather than theoretical vulnerabilities, resulting in more effective prioritization and faster remediation.
How long does it take to implement a CTEM program?
Implementation typically takes 3-6 months depending on organization size and existing security infrastructure. The process involves asset discovery, tool integration, process development, and staff training. However, organizations often see initial benefits within the first few weeks of deployment.
What tools are required for effective CTEM implementation?
CTEM requires vulnerability scanners, threat intelligence platforms, attack simulation tools, and automated orchestration capabilities. Platforms like Kindi integrate multiple functions into a single solution, simplifying implementation and reducing complexity for security teams.
How does CTEM help with compliance requirements?
CTEM provides continuous monitoring and documented risk assessment processes that many regulatory frameworks require. The automated reporting and audit trails help organizations demonstrate due diligence and maintain compliance with standards like PCI DSS, SOX, and various government regulations.
Can small organizations implement CTEM effectively?
Yes, cloud-based CTEM solutions make the framework accessible to organizations of all sizes. Many platforms offer scalable pricing and simplified deployment options that allow smaller teams to benefit from continuous threat exposure management without extensive infrastructure investments.