Synthetic identity fraud represents one of the most sophisticated and rapidly growing threats facing the insurance industry today. Unlike traditional identity theft, where fraudsters steal existing identities, synthetic identity fraud involves creating entirely new personas using a combination of real and fabricated information. For insurance companies, this type of fraud is particularly dangerous because it can remain undetected for years, allowing fraudsters to build credible profiles and file multiple claims.
Recent industry reports indicate that synthetic identity fraud accounts for nearly 20% of all credit losses in the financial services sector, with insurance companies increasingly targeted. The Federal Trade Commission estimates that synthetic identity fraud costs businesses over $6 billion annually, with insurance fraud representing a significant portion of these losses. Moreover, the sophisticated nature of synthetic identities makes them incredibly difficult to detect using traditional verification methods.
Understanding Synthetic Identity Fraud: Beyond Traditional Identity Theft
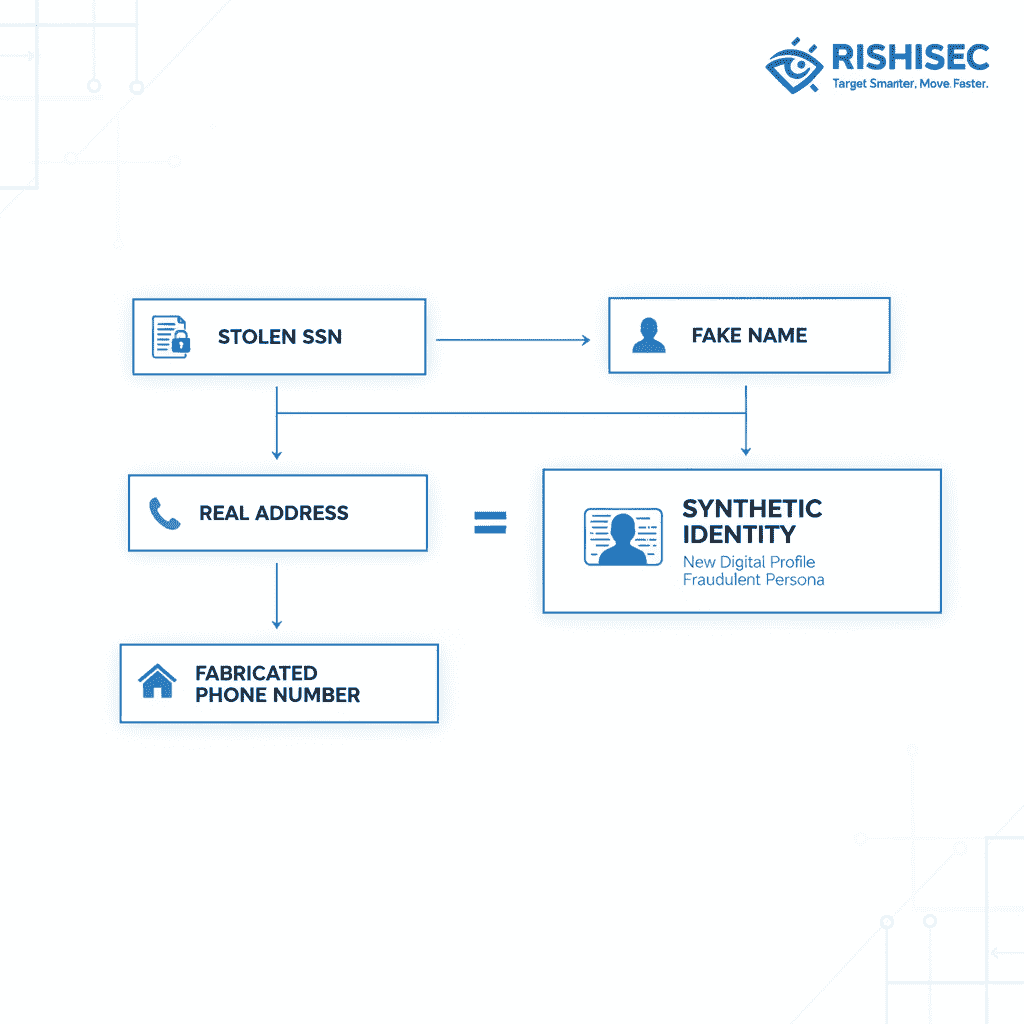
Synthetic identity fraud differs fundamentally from conventional identity theft in both construction and detection challenges. Traditional identity thieves steal complete identities, typically targeting individuals with established credit histories and financial accounts. However, synthetic identity fraudsters construct new identities by combining real and fabricated personal information, creating personas that don’t correspond to any actual person.
The construction process typically begins with a legitimate Social Security Number, often obtained from data breaches or purchased from dark web marketplaces. Fraudsters then pair this SSN with fictitious names, addresses, and phone numbers, creating a patchwork identity that can pass initial verification checks. Because credit bureaus create new files for previously unseen SSN-name combinations, these synthetic identities can establish credit histories and appear legitimate to automated screening systems.
Furthermore, synthetic identity fraud often involves a long cultivation period. Fraudsters may spend months or even years building credit histories, making small purchases, and establishing behavioral patterns that mirror legitimate customers. This patience allows them to apply for higher-value insurance policies and file more substantial claims when they eventually “bust out” the identity.
The Anatomy of Synthetic Identity Construction
Creating a synthetic identity requires specific components and techniques that fraud investigators must be familiar with. The foundation typically begins with a valid Social Security Number, often belonging to children, deceased individuals, or recent immigrants who haven’t yet established a credit file. These SSNs are particularly valuable because they’re less likely to trigger immediate alerts in verification systems.
Next, fraudsters layer on fabricated personal details: names that sound plausible, addresses from affluent neighborhoods to suggest creditworthiness, and phone numbers that route to burner phones or voice-over-IP services. They may also create supporting documentation, including fake pay stubs, utility bills, and employment records, often using sophisticated design software to replicate official documents.
Common Tactics and Red Flags in Insurance Applications
Fraud investigators should be particularly vigilant for several key indicators that suggest synthetic identity fraud in insurance applications. These red flags often appear in clusters, making pattern recognition crucial for effective detection.
One of the most common tactics involves manipulating application timing and geography. Fraudsters frequently submit multiple applications across different insurance companies within short timeframes, hoping to secure policies before cross-verification can occur. They also tend to target specific geographic regions where they’ve established synthetic addresses, often clustering applications in areas with higher property values to justify larger coverage amounts.
Another significant indicator involves documentation inconsistencies. Synthetic identities often exhibit minor but telling discrepancies in supporting documents: fonts that don’t match official templates, addresses that correspond to vacant lots or commercial properties listed as residences, or employment information that doesn’t align with available business records. Additionally, these applications frequently lack the digital footprints associated with genuine identities, such as long-standing social media profiles, online purchase histories, or consistent address histories.
The application behavior itself can also reveal synthetic fraud attempts. Legitimate applicants typically ask questions about policy terms, coverage limits, and premium options. Synthetic identity fraudsters, however, often demonstrate unusual urgency to complete applications quickly and show less interest in policy details, focusing instead on securing approval and moving to the claims phase.
Network-Based Fraud Patterns
Synthetic identity fraud rarely occurs in isolation. Sophisticated operations often involve networks of connected synthetic identities that share common elements: similar addresses with slight variations, phone numbers with consecutive digits, or employment at the same fictitious companies. Modern fraud investigation techniques emphasize the importance of analyzing these network connections to uncover larger fraud schemes.
Advanced Detection Strategies Using OSINT and Link Analysis
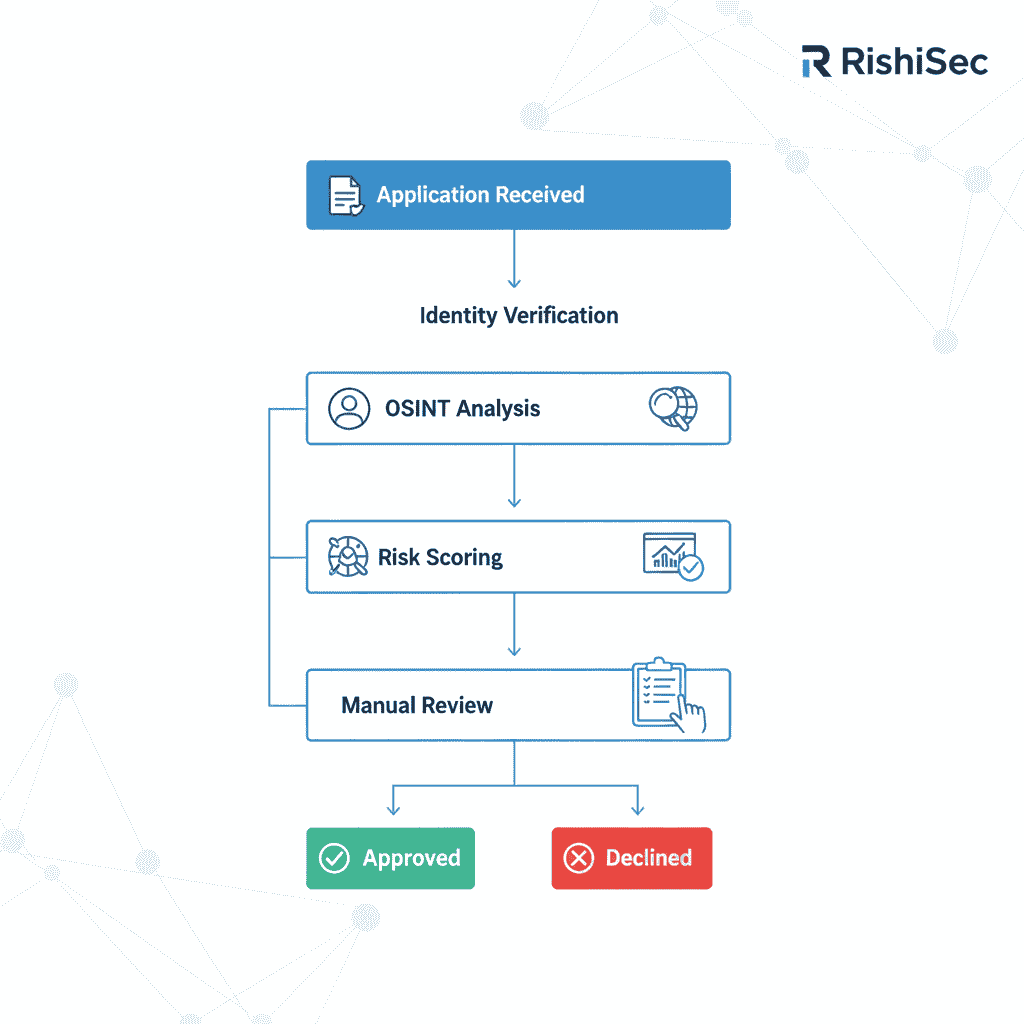
Detecting synthetic identity fraud requires a multi-layered approach that combines traditional verification methods with advanced open source intelligence techniques. Modern fraud investigators must look beyond standard identity verification and examine the broader digital footprint associated with each application.
OSINT techniques prove particularly valuable in validating the authenticity of personal information provided in applications. Social media analysis can reveal whether claimed addresses, employers, or personal details align with an individual’s online presence. However, the absence of such presence can itself be a red flag, particularly for applicants claiming to be active professionals or long-term residents of specific areas.
Tools like Kindi excel in this environment by automating the correlation of data points across multiple sources and identifying connection patterns that might escape manual review. The platform’s link analysis capabilities can reveal relationships between seemingly unrelated applications, exposing fraud networks that operate across geographic boundaries and time periods.
Data Enrichment and Cross-Reference Verification
Effective synthetic identity detection relies heavily on data enrichment processes that validate claimed information against authoritative sources. This involves checking Social Security Numbers against death master files, verifying addresses against postal service records, and confirming employment information through business databases and professional networks.
The verification process should also examine behavioral patterns associated with the application. Legitimate applicants typically demonstrate consistent digital behaviors: using devices and IP addresses associated with their claimed locations, accessing applications during reasonable hours for their stated time zones, and showing browsing patterns consistent with their claimed demographics and interests.
Technology Solutions and Prevention Frameworks
Insurance companies must implement comprehensive technology solutions that address synthetic identity fraud at multiple stages of the customer lifecycle. This begins with enhanced onboarding processes that incorporate advanced identity verification techniques, including biometric authentication, device fingerprinting, and real-time document verification.
Machine learning algorithms play a crucial role in identifying synthetic identities by analyzing application patterns, document characteristics, and behavioral indicators that may not be apparent to human reviewers. These systems can process vast amounts of data to identify subtle correlations and anomalies that suggest synthetic fraud attempts.
However, technology alone cannot solve the problem of synthetic identity fraud. Organizations must also develop comprehensive training programs that educate fraud investigators about emerging techniques and red flags. Insurance fraud detection requires continuous adaptation to evolving threats and methodologies.
Building Collaborative Defense Networks
The most effective approach to combating synthetic identity fraud involves collaboration between insurance companies, regulatory bodies, and law enforcement agencies. Shared databases of known synthetic identities and fraud patterns enable faster detection and prevention across the industry. However, such collaboration requires careful attention to privacy regulations and data sharing protocols.
Industry consortiums are increasingly developing standardized approaches to synthetic identity detection, sharing anonymized fraud indicators and patterns while protecting customer privacy. These collaborative efforts significantly enhance the industry’s collective ability to identify and prevent synthetic identity fraud before significant losses occur.
Practical Tips for Fraud Investigation Units
- Implement automated screening for applications with limited digital footprints or recent credit file establishment dates
- Cross-reference application data against multiple authoritative databases, including utility companies, postal services, and employment verification services
- Monitor for clustering patterns in applications, particularly those sharing similar addresses, phone numbers, or employment information
- Establish clear escalation procedures for applications that exhibit multiple red flags, even if they pass initial verification checks
- Regularly update detection criteria based on emerging fraud patterns and industry intelligence sharing
- Train investigators to recognize document manipulation techniques and inconsistencies in supporting materials
- Develop relationships with specialized OSINT tools and services that can provide enhanced verification capabilities
The Road Ahead: Emerging Challenges and Solutions
As synthetic identity fraud continues to evolve, insurance companies must remain vigilant and adaptive in their prevention strategies. Fraudsters are increasingly sophisticated in their techniques, using artificial intelligence to create more convincing synthetic identities and leveraging social engineering to overcome verification challenges.
The integration of advanced technologies like blockchain for identity verification and artificial intelligence for pattern recognition shows promise in combating synthetic identity fraud. However, these solutions must be implemented thoughtfully, balancing fraud prevention with customer experience and privacy protection.
Organizations that invest in comprehensive synthetic identity fraud prevention today will be better positioned to protect themselves against future threats while maintaining competitive advantages in customer acquisition and retention.
Want to strengthen your OSINT skills and fraud investigation capabilities? Check out our OSINT courses for practical, hands-on training. Additionally, discover how Kindi’s AI-powered OSINT automation can enhance your fraud detection capabilities and streamline your investigation workflows.
FAQ
How long does it typically take for synthetic identity fraud to be detected?
Synthetic identity fraud can remain undetected for 6 months to several years. The sophisticated nature of these schemes, combined with fraudsters’ patience in building credible profiles, makes early detection challenging without advanced monitoring systems.
What makes synthetic identity fraud particularly difficult to detect in insurance?
Insurance applications often involve less stringent real-time verification compared to banking products. Additionally, the time gap between policy issuance and claims filing allows synthetic identities to establish longer histories, making them appear more legitimate when claims are eventually submitted.
Can OSINT techniques help detect synthetic identities that have minimal online presence?
Yes, the absence of expected digital footprints is itself a valuable indicator. OSINT techniques can verify whether claimed addresses, employers, or personal details align with available public information, and the lack of corroborating evidence can signal synthetic fraud.
What role does machine learning play in synthetic identity detection?
Machine learning algorithms excel at identifying subtle patterns and correlations across large datasets that human reviewers might miss. They can analyze application behaviors, document characteristics, and cross-reference patterns to flag potentially synthetic identities for further investigation.
How should insurance companies balance fraud prevention with customer experience?
Effective synthetic identity detection should be largely invisible to legitimate customers. Advanced verification systems can process most applications automatically, only flagging suspicious cases for manual review. The key is implementing layered security that doesn’t create friction for genuine applicants.




