Cybersecurity consultants operating in 2025 face an increasingly complex regulatory landscape that fundamentally changes how open-source intelligence (OSINT) investigations must be conducted. The intersection of data privacy laws, international regulations, and evolving cybersecurity requirements creates both opportunities and significant compliance challenges for consulting practices.
Gone are the days when OSINT practitioners could freely gather and analyze publicly available data without considering legal implications. Today’s regulatory environment demands sophisticated understanding of OSINT compliance requirements that span multiple jurisdictions, data types, and investigative contexts. Furthermore, cybersecurity consultants must balance thorough intelligence gathering with strict adherence to privacy regulations that vary significantly across different regions and client requirements.
The stakes have never been higher for compliance failures. Organizations face substantial penalties, reputational damage, and potential criminal liability when OSINT activities violate privacy laws or exceed authorized boundaries. This reality demands that cybersecurity consultants develop comprehensive compliance frameworks that protect both their practices and their clients while maintaining investigative effectiveness.
Understanding the Regulatory Landscape for OSINT Activities
The regulatory environment governing OSINT activities encompasses multiple layers of legislation, international agreements, and industry-specific requirements. Cybersecurity consultants must navigate this complex landscape while maintaining operational effectiveness and client satisfaction.
Data protection regulations form the cornerstone of modern OSINT compliance requirements. The European Union’s General Data Protection Regulation (GDPR) establishes strict guidelines for processing personal data, even when that data originates from publicly available sources. Similarly, the California Consumer Privacy Act (CCPA) and emerging state-level regulations create additional compliance obligations for consultants working with US-based clients.
International data transfer regulations add another layer of complexity to OSINT operations. Consultants must understand adequacy decisions, standard contractual clauses, and binding corporate rules that govern cross-border intelligence sharing. These requirements become particularly challenging when investigating international threat actors or supporting multinational organizations with diverse regulatory obligations.
Key Regulatory Frameworks Impacting OSINT
Several critical regulatory frameworks directly impact how cybersecurity consultants conduct OSINT investigations. Understanding these frameworks helps consultants develop appropriate compliance strategies and avoid costly violations.
| Regulation | Jurisdiction | Key OSINT Requirements | Maximum Penalties |
|---|---|---|---|
| GDPR | European Union | Data minimization, purpose limitation, consent requirements | €20M or 4% global revenue |
| CCPA/CPRA | California, USA | Consumer rights, data disclosure requirements | $2,500-$7,500 per violation |
| PIPEDA | Canada | Reasonable purposes, consent principles | $100,000 per violation |
| LGPD | Brazil | Legitimate interest requirements, data subject rights | 2% revenue up to R$50M |
Essential Compliance Requirements for Cybersecurity Consultants
Cybersecurity consultants must implement comprehensive compliance programs that address multiple regulatory requirements simultaneously. These programs should encompass data handling procedures, client relationship management, and operational security measures that protect both consultant practices and client organizations.
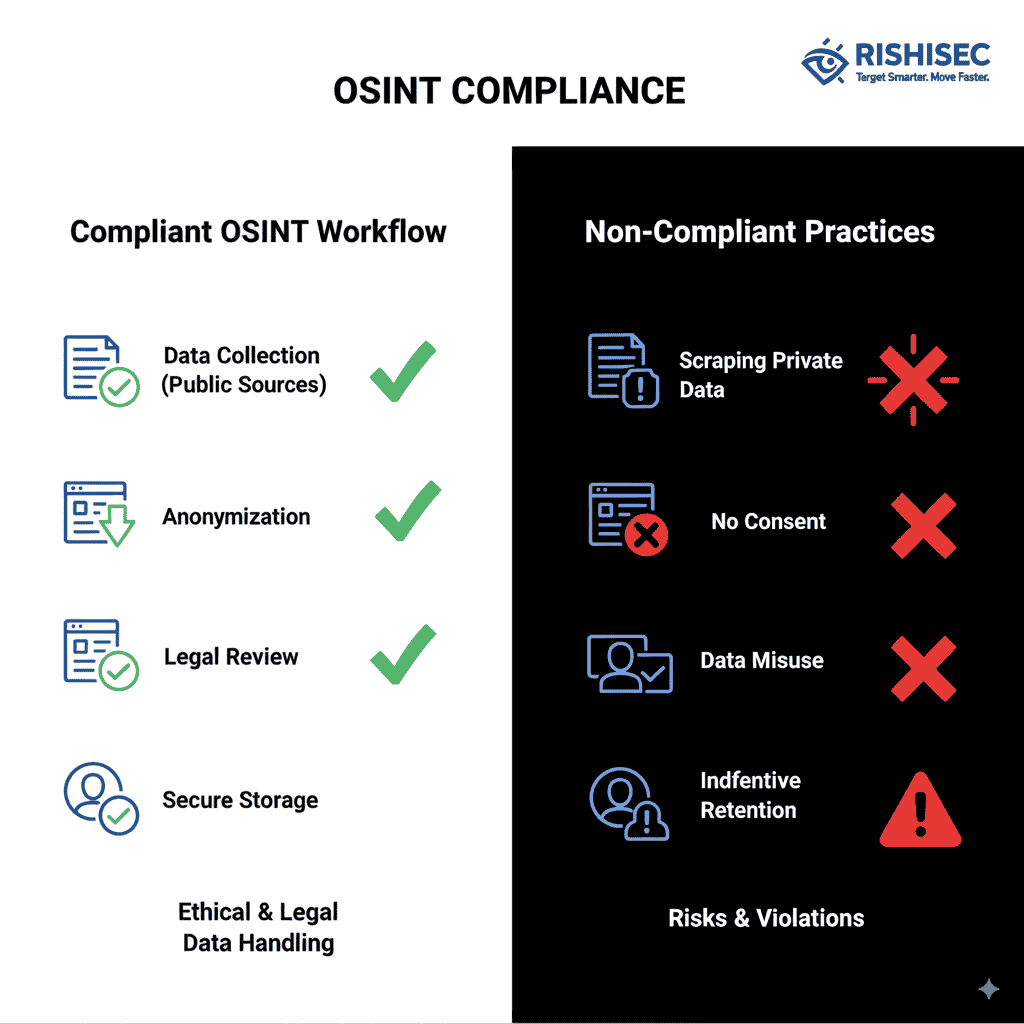
Data minimization principles require consultants to collect only the information necessary for specific investigative purposes. This approach challenges traditional OSINT methodologies that often involve comprehensive data gathering followed by selective analysis. Modern compliance frameworks demand that consultants define investigative scope precisely before beginning data collection activities.
Purpose limitation requirements restrict how consultants can use collected intelligence data. Information gathered for one investigation cannot automatically be repurposed for different clients or objectives without appropriate authorization. This requirement necessitates sophisticated data governance systems that track data sources, processing activities, and authorized uses throughout the intelligence lifecycle.
OSINT strategy frameworks become essential tools for maintaining compliance while delivering valuable intelligence products to clients. These frameworks help consultants balance thorough investigation with regulatory constraints.
Client Authorization and Scope Definition
Proper client authorization forms the foundation of compliant OSINT operations. Cybersecurity consultants must establish clear contractual frameworks that define investigation scope, data handling requirements, and compliance responsibilities before beginning any intelligence gathering activities.
Written authorization should specify exactly what data sources consultants may access, what information they may collect, and how that information may be used. Additionally, authorization documents should address data retention requirements, sharing restrictions, and destruction timelines that align with applicable regulatory requirements.
Scope definition becomes particularly critical when investigating threats that may involve personal data or cross international boundaries. Consultants must clearly understand the legal basis for processing personal data and ensure that investigation activities remain within authorized parameters throughout the engagement.
Data Subject Rights and Notification Requirements
Modern privacy regulations grant individuals specific rights regarding their personal data, even when that data is collected through OSINT activities. Cybersecurity consultants must understand these rights and implement appropriate procedures for responding to data subject requests.
Right to information requirements may obligate consultants to provide individuals with details about data processing activities, legal basis for processing, and retention periods. However, these obligations often conflict with the covert nature of security investigations, creating complex balancing challenges that require legal expertise to navigate effectively.

Building Compliant OSINT Workflows and Procedures
Effective compliance requires systematic approaches that integrate regulatory requirements into every aspect of OSINT operations. Cybersecurity consultants must develop standardized workflows that ensure consistency, traceability, and accountability across all investigation activities.
Documentation requirements form a critical component of compliant OSINT workflows. Consultants must maintain detailed records of data sources, collection methods, processing activities, and sharing decisions. These records serve both compliance and operational purposes, enabling audits while supporting ongoing investigation activities.
Access controls and data security measures protect collected intelligence while ensuring that only authorized personnel can access sensitive information. Role-based access systems should restrict data access based on job functions, client requirements, and security clearance levels where applicable.
Tools like Kindi provide essential capabilities for maintaining compliance while conducting sophisticated OSINT investigations. The platform’s collaboration features enable secure information sharing while maintaining granular access controls that protect sensitive intelligence data.
Risk Assessment and Legal Basis Documentation
Every OSINT investigation should begin with comprehensive risk assessment that identifies potential compliance challenges, privacy implications, and mitigation strategies. This assessment should consider applicable regulations, data sensitivity levels, and potential impact on investigated individuals.
Legal basis documentation establishes the regulatory foundation for data processing activities. Consultants must clearly identify whether they are relying on legitimate interests, legal obligations, public tasks, or other legal bases for processing personal data through OSINT activities.
Regular risk reassessment ensures that investigation activities remain compliant as circumstances change or new information emerges. Dynamic risk management approaches help consultants adapt to evolving regulatory requirements while maintaining investigation effectiveness.
International Considerations and Cross-Border Investigations
Cross-border OSINT investigations present unique compliance challenges that require sophisticated understanding of international legal frameworks. Cybersecurity consultants must navigate conflicting regulatory requirements, jurisdictional boundaries, and data transfer restrictions while supporting clients with global security concerns.
Data localization requirements in various jurisdictions may restrict where consultants can store or process collected intelligence. Countries like Russia, China, and India have implemented strict data residency requirements that impact how consultants conduct investigations involving local data sources or subjects.
Mutual legal assistance treaties (MLATs) and bilateral agreements between nations can provide frameworks for legitimate intelligence sharing. However, these agreements typically apply to formal law enforcement activities rather than private cybersecurity consulting engagements, creating gaps that consultants must carefully navigate.
Cross-border investigations require careful consideration of multiple legal frameworks simultaneously, making compliance significantly more complex than domestic engagements.
Data Transfer Mechanisms and Adequacy Decisions
International data transfers require specific legal mechanisms that ensure adequate protection for personal data crossing jurisdictional boundaries. Cybersecurity consultants must understand these mechanisms and implement appropriate safeguards for cross-border intelligence sharing.
Adequacy decisions by data protection authorities provide streamlined transfer mechanisms for certain jurisdictions. However, these decisions can change rapidly based on political or regulatory developments, requiring consultants to monitor adequacy status continuously.
Standard contractual clauses (SCCs) and binding corporate rules (BCRs) provide alternative transfer mechanisms when adequacy decisions are unavailable. These instruments require careful implementation and may include additional security measures or audit requirements that impact investigation workflows.
Technology Solutions for Compliance Management
Modern compliance requirements demand sophisticated technology solutions that automate compliance processes while supporting complex OSINT investigations. Cybersecurity consultants must invest in platforms and tools that streamline regulatory compliance without compromising investigative capabilities.
Privacy-by-design principles should guide technology selection and implementation decisions. Consultants should choose OSINT platforms that incorporate data minimization, purpose limitation, and access control features as core functionalities rather than add-on capabilities.
Automated compliance monitoring systems can track data processing activities, identify potential violations, and generate compliance reports that satisfy regulatory requirements. These systems reduce manual compliance overhead while providing audit trails that demonstrate good faith compliance efforts.
Data Governance and Lifecycle Management
Comprehensive data governance frameworks ensure that collected intelligence data is properly classified, protected, and managed throughout its lifecycle. These frameworks should address data classification, retention schedules, access controls, and destruction procedures that align with regulatory requirements.
Retention schedule management becomes critical for compliance, as various regulations impose different retention requirements for different data types. Automated systems can help consultants implement appropriate retention schedules while ensuring that data is available when needed for ongoing investigations.
Data destruction procedures must ensure complete and verifiable destruction of personal data when retention periods expire or legal requirements no longer justify continued processing. These procedures should address both digital and physical data destruction with appropriate verification measures.
Training and Awareness Programs for Compliance
Effective compliance requires comprehensive training programs that ensure all team members understand regulatory requirements, ethical obligations, and operational procedures. Cybersecurity consultants must invest in ongoing education that keeps pace with evolving regulatory landscapes and emerging compliance challenges.
Role-specific training programs should address different compliance requirements based on job functions, access levels, and client interaction responsibilities. Senior investigators may require advanced training on legal basis assessment and risk management, while junior team members need thorough grounding in basic data handling procedures.
Regular compliance updates help teams stay current with regulatory changes, new privacy laws, and evolving best practices. These updates should include practical guidance on how regulatory changes impact day-to-day OSINT operations and investigation procedures.
Incident Response and Compliance Violations
Despite best efforts, compliance incidents may occur during complex OSINT investigations. Consultants must implement robust incident response procedures that minimize harm, satisfy notification requirements, and restore compliant operations quickly.
Incident detection systems should identify potential compliance violations promptly, enabling rapid response that can prevent regulatory penalties or client relationship damage. These systems should monitor data access patterns, processing activities, and sharing decisions for compliance with established procedures.
Notification procedures must align with regulatory requirements for data breach notifications, unauthorized access incidents, and other compliance violations. Consultants should maintain current contact information for relevant regulators, clients, and legal counsel to ensure timely notifications when required.
Industry-Specific Compliance Considerations
Different industries impose unique compliance requirements that cybersecurity consultants must understand and accommodate. Healthcare, financial services, government, and critical infrastructure sectors each have specific regulations that impact how OSINT investigations can be conducted.
Healthcare sector engagements must consider HIPAA requirements, medical privacy laws, and patient safety regulations. OSINT investigations involving healthcare data require additional safeguards and may be subject to stricter consent requirements than other sectors.
Financial services regulations like PCI DSS, SOX, and banking secrecy laws create specific compliance obligations for consultants working with financial institutions. These regulations often include strict data handling requirements and audit obligations that impact investigation methodologies.
Government and defense contractors face additional security clearance requirements, export control regulations, and national security considerations that significantly impact OSINT operations. Military OSINT modernization requires careful attention to these specialized compliance requirements.
Sector-Specific Risk Mitigation Strategies
Each industry sector requires tailored risk mitigation strategies that address specific regulatory requirements and operational constraints. Consultants must develop sector-specific compliance frameworks that align with industry best practices and regulatory expectations.
Regular compliance audits help identify sector-specific risks and ensure that mitigation strategies remain effective as regulations evolve. These audits should involve independent assessors who understand both cybersecurity consulting practices and industry-specific compliance requirements.
Client education programs help organizations understand their compliance obligations and how OSINT investigations can support their regulatory requirements. These programs should address data governance, incident response, and ongoing compliance monitoring that extends beyond individual consulting engagements.
Future Trends in OSINT Compliance and Regulation
The regulatory landscape for OSINT activities continues evolving rapidly, driven by technological advances, changing privacy expectations, and emerging security threats. Cybersecurity consultants must anticipate future compliance requirements and adapt their practices proactively.
Artificial intelligence and machine learning technologies are attracting increased regulatory attention, with potential implications for automated OSINT processing and analysis. Proposed AI regulations may impose specific requirements for algorithmic transparency, bias testing, and human oversight that impact OSINT tool selection and deployment.
International regulatory harmonization efforts may simplify cross-border compliance requirements over time, but consultants should expect continued complexity as different jurisdictions balance security needs with privacy protections. Emerging economies are implementing new data protection laws that may create additional compliance obligations for global consulting practices.
Preparing for Regulatory Evolution
Proactive compliance strategies enable consultants to adapt to regulatory changes without disrupting ongoing client relationships or compromising investigation capabilities. These strategies should include regulatory monitoring, impact assessment procedures, and implementation planning that anticipates future requirements.
Industry engagement through professional associations, regulatory consultations, and standards development helps consultants influence emerging regulations while staying informed about likely future requirements. Active participation in industry discussions provides early visibility into regulatory trends and the challenges of implementation.
Technology investment strategies should consider regulatory trajectory and ensure that selected platforms can adapt to evolving compliance requirements. Consultants should prioritize vendors who demonstrate commitment to compliance innovation and regulatory alignment.
Conclusion: Building Sustainable Compliance Practices
OSINT compliance represents both a challenge and an opportunity for cybersecurity consultants operating in today’s regulatory environment. Organizations that develop comprehensive compliance frameworks gain competitive advantages through reduced legal risk, enhanced client confidence, and operational efficiency improvements.
Successful compliance requires ongoing investment in training, technology, and procedural development that keeps pace with regulatory evolution. Consultants must balance thorough compliance with operational effectiveness, ensuring that regulatory requirements enhance rather than hinder their ability to deliver valuable intelligence services.
The future belongs to consulting practices that embed compliance into their core operations rather than treating it as an afterthought. By developing robust compliance capabilities, cybersecurity consultants can confidently navigate complex regulatory requirements while delivering exceptional value to their clients.
Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training. Discover how Kindi’s secure collaboration features can support your compliant OSINT investigations. Sign up for our newsletter to stay updated on regulatory developments and compliance best practices.
FAQ
What is OSINT compliance, and why is it important for cybersecurity consultants?
OSINT compliance refers to adhering to privacy laws, data protection regulations, and ethical guidelines when conducting open-source intelligence investigations. It’s crucial for consultants to avoid legal penalties, maintain client trust, and operate ethically in regulated environments.
How does GDPR affect OSINT investigations conducted by cybersecurity consultants?
GDPR requires consultants to have legal basis for processing personal data, implement data minimization principles, respect data subject rights, and ensure appropriate security measures. Even publicly available data may be subject to GDPR requirements when processed systematically.
What are the key compliance challenges for cross-border OSINT investigations?
Cross-border investigations face challenges including conflicting privacy laws, data transfer restrictions, varying consent requirements, and jurisdictional complexities. Consultants must navigate multiple regulatory frameworks simultaneously while ensuring adequate data protection.
How can cybersecurity consultants ensure their OSINT tools are compliant?
Consultants should select tools that incorporate privacy-by-design principles, provide audit trails, support data minimization, and offer granular access controls. Regular compliance assessments and vendor due diligence help ensure continued compliance as tools evolve.
What documentation is required for compliant OSINT investigations?
Required documentation typically includes legal basis assessments, data processing records, risk assessments, client authorizations, retention schedules, and audit trails. Specific requirements vary by jurisdiction and may include additional sector-specific documentation.




