The 2025 Intelligence Authorization Act represents the most significant transformation of open-source intelligence operations in decades. Congressional leaders are implementing sweeping House Intel Bill 2025 OSINT reforms that fundamentally change how intelligence agencies collect, procure, and manage open-source data across the intelligence community.
These changes extend far beyond minor policy adjustments, creating structural reforms in oversight mechanisms, procurement processes, and operational definitions that will impact every senior intelligence analyst, special agent, and cybercrime unit leader. Furthermore, the Federal News Network reports that the bill aims to centralize how the intelligence community purchases commercial data and utilizes open-source intelligence, representing a complete overhaul of current practices.
Senior analysts must understand these reforms immediately because implementation timelines are aggressive, and non-compliance risks operational disruption. Moreover, the changes present opportunities for forward-thinking intelligence professionals to lead organizational transformation while positioning themselves as subject matter experts in the new regulatory environment.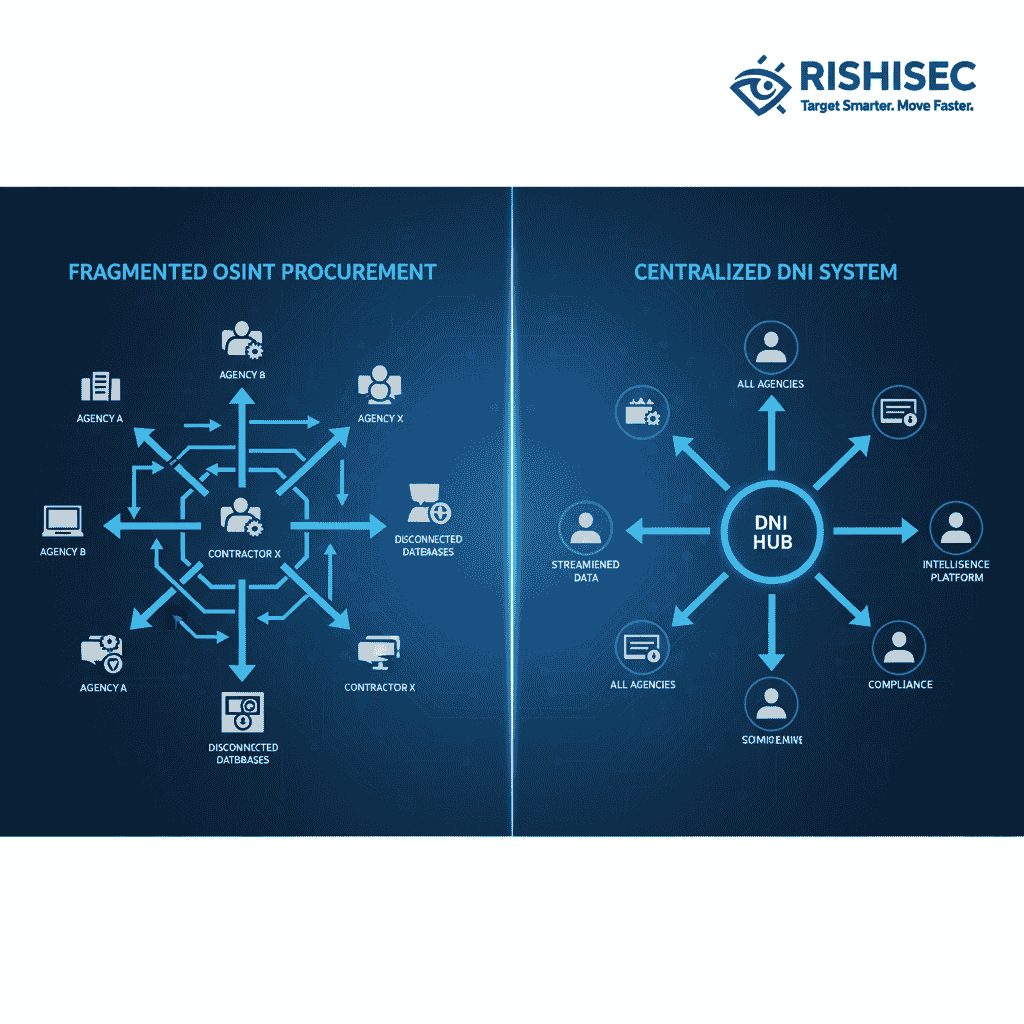
Key Structural Changes in the House Intel Bill 2025 OSINT Reforms
The legislation introduces fundamental changes that redefine how intelligence agencies approach open-source intelligence operations. These reforms address long-standing inefficiencies while establishing new accountability mechanisms that affect every aspect of OSINT activities.
Congressional leadership recognized that current OSINT practices suffer from fragmentation, duplication, and insufficient oversight. Consequently, the new legislation establishes comprehensive frameworks that standardize operations across agencies while maintaining operational flexibility for mission-specific requirements.
Additionally, the reforms acknowledge the growing importance of commercial data sources in modern intelligence operations. However, they also recognize the need for better governance mechanisms that ensure appropriate use while preventing waste and potential security vulnerabilities.
Clarifying Definitions and Scope
One of the most significant aspects of the House Intel Bill 2025 OSINT reforms involves establishing clear definitions that eliminate confusion between different types of open-source data. These definitional changes have immediate operational implications for intelligence analysts.
The bill specifically distinguishes between publicly available information (PAI) and commercially available information (CAI), creating separate regulatory frameworks for each category. Furthermore, OSINT is formally defined to include intelligence derived from both publicly and commercially available sources, expanding the official scope of open-source intelligence operations.
These definitional changes matter because they establish different procurement procedures, oversight requirements, and operational constraints for different types of data sources. Therefore, analysts must understand which category applies to their specific sources and adjust their procedures accordingly.
Enhanced Oversight and Accountability Mechanisms
The legislation creates unprecedented oversight structures designed to improve coordination and accountability across intelligence community OSINT activities. These mechanisms represent significant changes in how agencies manage and document their open-source intelligence operations.
Central oversight responsibility falls under the Director of National Intelligence (DNI), who will coordinate OSINT activities across agencies to reduce duplication and improve effectiveness. Additionally, the bill mandates comprehensive documentation and sharing requirements that ensure OSINT work is visible across appropriate agencies.
Moreover, agencies must now coordinate their OSINT activities to prevent overlapping efforts and conflicting approaches. This coordination requirement extends to sharing intelligence products, methodologies, and lessons learned across organizational boundaries.
| Reform Area | Previous System | New Requirements | Implementation Timeline |
|---|---|---|---|
| Oversight Structure | Agency-specific oversight | Centralized DNI coordination | 6 months |
| Data Definitions | Informal classifications | Legal PAI/CAI distinctions | 3 months |
| Procurement Process | Independent agency purchasing | Coordinated acquisition strategy | 12 months |
| Documentation | Internal agency records | Cross-agency sharing requirements | 9 months |
Procurement and Budgeting Transformation
The House Intel Bill 2025 OSINT reforms fundamentally restructure how intelligence agencies purchase commercial data and OSINT services. These changes address wasteful spending while improving the quality and accessibility of commercial intelligence sources.
Duplicative spending represents a major target of the new legislation. Multiple agencies often purchase similar commercial data sources independently, resulting in unnecessary costs and missed opportunities for bulk pricing advantages. Consequently, the reforms establish coordination mechanisms that prevent this duplication while ensuring agencies maintain access to necessary information.
Streamlined acquisition processes specifically target unclassified OSINT data procurement, which has traditionally been hindered by security-focused acquisition procedures designed for classified systems. Military OSINT modernization efforts have highlighted the need for these streamlined processes that balance security with operational efficiency.
Commercial Data Integration Standards
New integration standards ensure that commercially acquired OSINT data can be effectively utilized across different agency systems and analytical platforms. These standards address technical compatibility while maintaining appropriate security controls.
Vendor qualification requirements establish baseline standards for commercial OSINT providers, ensuring that purchased data meets intelligence community quality and security requirements. Similarly, contract standardization reduces administrative overhead while improving vendor accountability and performance measurement.
Furthermore, bulk purchasing arrangements enable cost savings through coordinated procurement across multiple agencies. However, these arrangements must balance cost efficiency with agency-specific operational requirements and security considerations.
Budget Allocation and Resource Management
The reforms establish new budget allocation mechanisms that improve visibility into OSINT spending while ensuring resources are distributed based on operational priorities and demonstrated effectiveness. These mechanisms require agencies to justify OSINT expenditures more rigorously.
Performance measurement requirements mandate that agencies demonstrate the value and effectiveness of their OSINT investments. Additionally, resource sharing agreements enable agencies to leverage each other’s OSINT capabilities rather than building redundant internal capacity.
Cost-benefit analysis becomes mandatory for significant OSINT procurements, requiring agencies to demonstrate that commercial purchases provide better value than alternative sources or methods. Therefore, analysts must understand how to articulate the value proposition of their OSINT requirements.
Operational Implications for Senior Intelligence Professionals
The House Intel Bill 2025 OSINT reforms create immediate operational changes that affect how senior intelligence professionals conduct their daily responsibilities. Understanding these implications helps analysts prepare for successful adaptation to the new environment.
Workflow modifications become necessary as analysts must integrate new documentation, coordination, and approval processes into their routine operations. However, these changes also create opportunities to improve analytical rigor and cross-agency collaboration that can enhance intelligence effectiveness.
Decision-making processes must now incorporate compliance considerations that were previously optional or informal. Consequently, analysts need training on the new requirements and decision trees that help them navigate complex regulatory scenarios while maintaining operational effectiveness.
Tools like Kindi become essential for managing the increased documentation and collaboration requirements. The platform’s link analysis and collaboration features help analysts track source relationships while maintaining compliance with new sharing and coordination mandates.
Source Selection and Vendor Management
New vendor qualification standards require analysts to evaluate commercial OSINT sources against specific compliance criteria before incorporating them into intelligence products. These evaluations must consider both analytical value and regulatory compliance.
Existing vendor relationships may require reevaluation to ensure compliance with new definitions and procurement standards. Similarly, analysts must understand how to work within new approval processes for accessing commercial data sources that may have previously been readily available.
Documentation requirements extend to source selection decisions, requiring analysts to maintain records that justify their choice of sources and methodologies. Furthermore, these records must be accessible for oversight reviews and cross-agency coordination purposes.
Analytical Process Adaptations
Structured analytical techniques must incorporate new verification and documentation requirements while maintaining analytical rigor and timeliness. SOC environments integrating OSINT must particularly focus on adapting their analytical processes to meet these new requirements.
Quality assurance procedures need updates to address compliance verification alongside traditional analytical accuracy measures. Additionally, analysts must understand how to balance thoroughness with operational timelines when new documentation requirements add process steps.
Collaboration mechanisms with other agencies become more formal and structured, requiring analysts to understand inter-agency protocols and information sharing procedures that were previously informal or ad hoc.
Training and Organizational Development Requirements
The successful implementation of the House Intel Bill 2025 OSINT reforms requires comprehensive training programs that address both the technical requirements and the cultural changes within intelligence organizations. These programs must be implemented rapidly to meet legislative timelines.
Compliance training becomes essential for all personnel involved in OSINT operations, covering new definitions, procedures, and documentation requirements. However, training must go beyond compliance to address the analytical and operational opportunities created by improved coordination and standardization.
Leadership development programs must prepare senior analysts to guide organizational transformation while maintaining mission effectiveness during the transition period. Similarly, these programs should incorporate change management techniques that enable teams to adapt to new procedures while retaining institutional knowledge.
Skill Development Priorities
Procurement literacy becomes a critical skill for senior analysts who must understand new acquisition processes and vendor management requirements. Additionally, analysts need training in regulatory compliance that enables them to navigate complex requirements while maintaining analytical independence.
Inter-agency coordination skills require development as analysts must work more closely with counterparts in other organizations. Furthermore, documentation and record-keeping skills become more important as oversight requirements demand comprehensive audit trails.
Technology proficiency must expand to include new platforms and systems that support compliance monitoring and cross-agency collaboration. Therefore, organizations must invest in training programs that address both technical and procedural aspects of the new requirements.
Career Development Opportunities
The reforms create new career opportunities for analysts who develop expertise in OSINT governance, compliance management, and inter-agency coordination. These specializations will become increasingly valuable as organizations adapt to the new regulatory environment.
Subject matter expert positions in OSINT reform implementation offer advancement opportunities for senior analysts who can guide organizational transformation. Similarly, training and mentorship roles become available for analysts who successfully navigate the transition period.
Cross-agency assignment opportunities expand as coordination requirements create demand for analysts who understand multiple organizational cultures and procedures. Additionally, these opportunities provide valuable experience that enhances career development prospects.
Strategic Opportunities and Risk Mitigation
While the House Intel Bill 2025 OSINT reforms present implementation challenges, they also create significant strategic opportunities for intelligence professionals who approach them proactively. Understanding both risks and opportunities helps analysts position themselves for success.
Efficiency improvements result from reduced duplication and better coordination across agencies. Moreover, standardized procedures and shared resources can improve analytical quality while reducing individual workload burdens. Automated OSINT investigations become more feasible when agencies coordinate their technology investments and share best practices.
Enhanced credibility for OSINT operations emerges from improved oversight and standardization. Consequently, intelligence products based on open-source analysis may receive greater acceptance from decision-makers who have confidence in the rigor of underlying processes.
Competitive Advantages for Early Adopters
Organizations that implement reforms quickly and effectively gain competitive advantages in resource allocation, vendor relationships, and inter-agency partnerships. Early adopters can influence implementation standards while positioning themselves as centers of excellence.
Vendor relationships improve for organizations that understand new procurement requirements and can help commercial partners navigate compliance expectations. Similarly, these organizations may gain preferential access to high-quality commercial data sources.
Operational efficiency improvements provide lasting advantages for organizations that successfully integrate new procedures into their workflows. Furthermore, these improvements create capacity for expanded analytical coverage or deeper investigation capabilities.
Risk Management Strategies
Implementation risks include operational disruption, compliance failures, and resistance to change within established teams. However, proactive risk management can minimize these challenges while maximizing the benefits of reform implementation.
Phased implementation strategies help manage transition risks by allowing organizations to test new procedures on limited operations before full deployment. Additionally, pilot programs provide opportunities to identify and resolve implementation challenges before they affect mission-critical operations.
Stakeholder engagement ensures that affected personnel understand the rationale for changes and participate in implementation planning. Moreover, engagement helps identify potential resistance sources and develops strategies to address concerns constructively.
Immediate Action Steps for Senior Analysts
Senior intelligence professionals must take specific actions immediately to prepare for House Intel Bill 2025 OSINT reforms implementation. These steps help ensure smooth transitions while positioning analysts for success in the new environment.
Current source inventory becomes the first priority, requiring analysts to catalog all OSINT sources against new PAI and CAI definitions. This inventory must include vendor relationships, procurement methods, and integration procedures that may require modification under new regulations.
Stakeholder engagement with procurement, policy, and legal teams ensures that analysts understand organizational implementation plans and can influence decisions that affect their operations. Furthermore, early engagement helps identify training needs and resource requirements.
Documentation and Process Preparation
Standard operating procedures require immediate review and updating to incorporate new compliance requirements and coordination mechanisms. These procedures must address both routine operations and exception handling that maintains mission effectiveness during transition periods.
Quality assurance processes need expansion to include compliance verification alongside traditional analytical accuracy measures. Additionally, audit trail requirements demand new record-keeping procedures that support oversight reviews and inter-agency coordination.
Training plan development ensures that team members receive necessary preparation for new requirements. Moreover, training should address both compliance technicalities and the strategic opportunities created by improved coordination and standardization.
Technology and Vendor Assessment
Existing technology platforms require evaluation against new compliance and coordination requirements. This assessment should identify capability gaps that need addressing through upgrades, replacements, or additional tools.
Vendor compliance assessment ensures that commercial OSINT sources can meet new qualification standards and procurement requirements. Similarly, this assessment helps identify alternative sources that may be necessary if current vendors cannot adapt to new requirements.
Integration planning addresses how new compliance and coordination requirements will be incorporated into existing workflows and technology systems. Therefore, planning must balance operational effectiveness with regulatory compliance demands.
Conclusion: Embracing Transformation for Enhanced Effectiveness
The House Intel Bill 2025 OSINT reforms represent a watershed moment for intelligence operations that will fundamentally improve how agencies collect, analyze, and utilize open-source intelligence. Senior analysts who embrace these changes proactively will lead organizational transformation while enhancing their professional capabilities.
Implementation success depends on understanding both the technical requirements and strategic opportunities created by the reforms. Organizations that approach implementation systematically while maintaining focus on mission effectiveness will emerge stronger and more capable than before.
The reforms create opportunities for intelligence professionals to demonstrate leadership, develop new competencies, and contribute to improved intelligence community effectiveness. However, realizing these opportunities requires immediate action and sustained commitment to excellence during the transition period.
Forward-thinking analysts will view these reforms not as burdens but as catalysts for professional development and operational improvement. By positioning themselves as subject matter experts in OSINT governance and compliance, senior analysts can advance their careers while contributing to enhanced national security capabilities.
Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training. Discover how Kindi’s collaboration and documentation features can help you comply with new OSINT reform requirements. Sign up for our newsletter to stay updated on intelligence community developments and reform implementation guidance.
FAQ
What are the key differences between PAI and CAI under the new House Intel Bill 2025 OSINT reforms?
PAI (Publicly Available Information) refers to data accessible to the general public without payment, while CAI (Commercially Available Information) requires purchase or subscription. The reforms establish separate procurement and oversight procedures for each category, affecting how analysts access and utilize these sources.
How will the centralized DNI oversight affect individual agency OSINT operations?
DNI oversight focuses on coordination and reducing duplication rather than micromanaging operations. Agencies retain operational autonomy while participating in information sharing and collaborative procurement that improves efficiency and effectiveness across the intelligence community.
What training do senior analysts need to comply with the new OSINT reforms?
Essential training includes procurement procedures, compliance documentation, inter-agency coordination protocols, and new quality assurance requirements. Additionally, analysts need training on vendor management and source qualification under the new standards.
How do the reforms affect existing commercial OSINT vendor relationships?
Existing vendors must meet new qualification standards and may need to adapt their services to comply with updated procurement procedures. Analysts should assess current vendors against new requirements and identify alternative sources if needed.
What are the implementation timelines for different aspects of the OSINT reforms?
Data definitions and basic compliance requirements take effect within 3-6 months, while procurement coordination and full documentation systems have 9-12 month implementation timelines. Agencies must begin preparation immediately to meet these deadlines.