In 2011, security researchers infiltrated HBGary Federal by exploiting a single weakness: publicly available information about their employees. Using nothing but open source intelligence, attackers mapped the company’s organizational structure, identified key personnel, and crafted targeted phishing emails that appeared to come from trusted colleagues. Within hours, they had complete access to the network. This breach demonstrates a critical truth: the most sophisticated technical defenses crumble when human vulnerabilities are exploited through OSINT social engineering.
OSINT social engineering represents the convergence of publicly available data and psychological manipulation. Red teams, the ethical hackers hired to test organizational security, use these techniques to demonstrate how adversaries weaponize information that employees freely share online. Understanding this process is essential for security operations centers, red teams, and defense contractors who need to protect their organizations from similar attacks.
Why OSINT is the Red Team’s Social Engineering Superpower
Every employee leaves digital breadcrumbs across the internet. These fragments of information seem harmless in isolation, but when connected through OSINT techniques, they create detailed profiles that attackers exploit. Red teams leverage this reality to simulate real-world threats and expose organizational weaknesses.
Digital Breadcrumbs Employees Leave Behind
Modern professionals maintain extensive online presences without realizing the intelligence value they provide. LinkedIn profiles reveal job titles, responsibilities, and reporting structures. GitHub repositories expose technology stacks, coding standards, and even sensitive configuration files accidentally committed to public repos. Twitter posts share conference attendance, business travel, and professional frustrations that provide social engineering hooks.
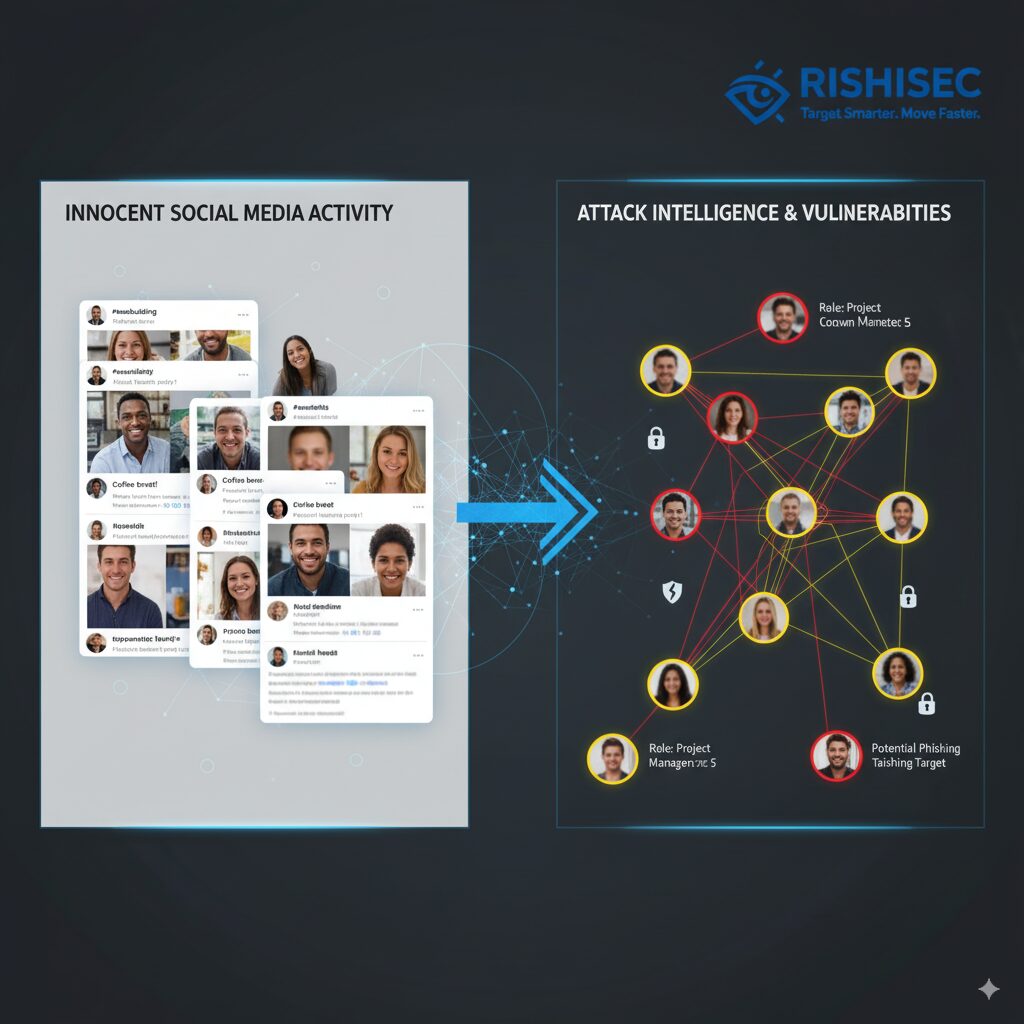
A single Instagram post showing a conference badge can reveal an employee’s email format, company naming conventions, and physical location. When combined with LinkedIn endorsements, this information identifies potential allies within the organization who might be leveraged for additional access. These seemingly innocent shares become attack vectors when processed through credential leakage OSINT techniques.
How Adversaries Connect Weak Signals
The power of OSINT social engineering lies in correlation. A conference badge photograph provides an email format. That format, tested against breach databases, reveals password patterns. Those passwords, tried against corporate VPN portals, grant network access. Each piece of information amplifies the next, creating attack chains from scattered data points.
Red teams demonstrate this process by mapping seemingly unrelated information into coherent attack strategies. They identify employees who recently changed roles, have family members on social media, or expressed frustration about company policies online. These emotional and situational factors serve as pretexts for targeted phishing campaigns that circumvent technical controls by exploiting human psychology.
Case Examples from Real Red Team Engagements
The 2011 HBGary breach remains a textbook example of OSINT-driven compromise. Attackers used publicly available information to impersonate the CEO in emails to IT staff, requesting password resets that provided complete system access. Similarly, security researcher Chris Hadnagy has documented numerous penetration tests where OSINT reconnaissance identified employees willing to circumvent security protocols when approached with seemingly legitimate requests.
| Attack Vector | OSINT Source | Exploitation Method |
|---|---|---|
| Spear Phishing | LinkedIn job changes, Twitter posts | Pretexting as HR or new manager |
| Credential Stuffing | Breach databases, password patterns | Testing reused passwords across services |
| Physical Access | Job postings, vendor contracts | Impersonating contractors or delivery personnel |
| Vishing | Organizational charts, phone numbers | Voice calls posing as internal support |
Core OSINT Techniques Used in Red Team Social Engineering
Red teams employ systematic methodologies to transform public information into exploitable intelligence. These techniques mirror adversary tactics, providing organizations with realistic assessments of their security posture against human-targeted attacks.
Profiling Employees and Organizational Structure
LinkedIn serves as an organizational blueprint for red teams. By analyzing connection patterns, job histories, and endorsements, security testers reconstruct reporting hierarchies and identify high-value targets. Facebook profiles reveal family relationships, hobbies, and personal interests that inform pretext development. Twitter behavior analysis exposes communication styles, political views, and emotional triggers that enhance phishing effectiveness.

This profiling extends beyond individual employees to map entire departments. Red teams identify which teams handle sensitive data, who has administrative privileges, and which employees might have access to critical systems. This intelligence guides targeting decisions, focusing social engineering efforts on individuals most likely to provide valuable access.
Credential and Breach Data Analysis
Billions of credentials are circulated through data breaches, many of which involve corporate email addresses. Red teams search these databases for target organization domains, then analyze password patterns to predict current credentials. Employees who reused passwords across personal and professional accounts create direct access vectors requiring minimal technical sophistication.
Beyond direct credential reuse, breach data reveals security question answers, password construction patterns, and email formats. An employee’s pet name found on Instagram might unlock their password reset system. Their college name from LinkedIn could answer security questions. These connections turn public information into authentication bypasses.
Infrastructure Mapping Through Technical OSINT
While social engineering targets humans, understanding technical infrastructure enhances attack credibility. Whois records reveal domain registration details and the administrative contacts associated with a domain. Shodan searches expose internet-facing systems, technology stacks, and misconfigured services. Job postings accidentally disclose internal tool names, security products, and technical requirements that inform convincing pretexts.
A job listing seeking “experience with Okta SSO and Salesforce integration” tells red teams exactly which systems to reference in phishing emails. Technical reconnaissance makes social engineering attempts more believable by incorporating authentic organizational details that employees expect in legitimate communications.
Exploiting Behavioral Cues and Public Leaks
Public Slack workspaces, Discord servers, and Reddit discussions sometimes include current or former employees discussing company matters. These conversations leak internal terminology, project names, and organizational frustrations that red teams weaponize. A disgruntled employee’s Twitter rant about management decisions provides emotional hooks for manipulation.
Behavioral analysis identifies optimal attack timing. Employees posting about upcoming vacations create opportunities for executive impersonation. LinkedIn job changes signal transition periods when new employees lack established verification procedures. Conference attendance creates windows when employees expect legitimate contact from unfamiliar parties.
Turning OSINT Into Effective Pretexts
Raw intelligence becomes weaponized through pretext development. Red teams transform collected data into scenarios that manipulate targets into desired actions, demonstrating how attackers bypass technical controls through psychological exploitation.
Crafting Believable Phishing Campaigns
Generic phishing emails trigger suspicion; personalized messages based on OSINT slip past defenses. Red teams incorporate internal project names, reference recent company announcements, and use communication styles matching organizational culture. A phishing email mentioning a specific initiative found in press releases, addressed from a legitimate department identified through LinkedIn, achieves significantly higher success rates than mass campaigns.
The most effective phishing pretexts create urgency around plausible scenarios. A message from “HR” about benefits enrollment, timed to actual enrollment periods discovered through company announcements, compels immediate action. Reference to legitimate vendors identified through contract databases adds authenticity. These contextual details, all derived from OSINT, transform obvious attacks into convincing communications.
Voice Pretexts and Vishing Campaigns
Vishing, or voice phishing, leverages organizational reconnaissance to impersonate internal personnel. Red teams call targets pretending to be IT support, referencing real help desk ticket systems and security products identified through job postings. They name-drop actual managers found on LinkedIn, creating authority and compliance pressure.
These calls exploit natural human tendencies to help colleagues and defer to authority. An attacker claiming to be from the security team, investigating a supposed breach, and needing the target’s help to “verify their account,” uses social proof and urgency to bypass skepticism. The OSINT foundation makes the scenario believable enough to succeed.
Physical Pretexts and Tailgating Scenarios
OSINT enables physical security testing by identifying legitimate pretexts for facility access. Job postings for facilities maintenance reveal vendor names. LinkedIn shows recent hires who might not know all employees by sight. Conference schedules identify periods when visitor traffic increases, masking unauthorized presence.
Red teams impersonate delivery personnel, contractors, or new employees, using details gleaned from public sources to answer challenge questions. They carry props, such as badges or equipment cases, that match vendors identified through OSINT, creating visual credibility that bypasses physical security measures.
Defensive Lessons Blue Teams Must Learn
Red team insights reveal vulnerabilities that blue teams must address to ensure effective security. Understanding attacker methodologies enables organizations to implement effective countermeasures against OSINT-driven social engineering.
Security awareness training traditionally focuses on generic threats; however, effective programs show employees their actual digital footprints. Organizations should conduct OSINT audits of their personnel, demonstrating what attackers see when they research the company. This personalized approach makes abstract threats concrete and actionable.
Policy changes should address the root causes of OSINT exposure. Guidelines for social media use, restrictions on technical details in job postings, and metadata scrubbing procedures limit the availability of intelligence. Email security training should emphasize verification procedures for unusual requests, particularly those creating urgency or involving sensitive actions.
Technical controls complement awareness efforts. Multi-factor authentication prevents credential reuse attacks. Anomaly detection systems flag unusual access patterns. Role-based access controls limit damage from compromised accounts. These defenses assume social engineering will occasionally succeed and focus on limiting impact rather than preventing all attempts.
Organizations should also monitor their own OSINT footprint proactively, using tools similar to those employed by attackers. Regular searches for exposed credentials, leaked documents, and excessive social media sharing by employees provide early warning of increased risk. OSINT compliance frameworks help structure these monitoring efforts within legal and ethical boundaries.
How Kindi Enhances Red Team Social Engineering Simulations
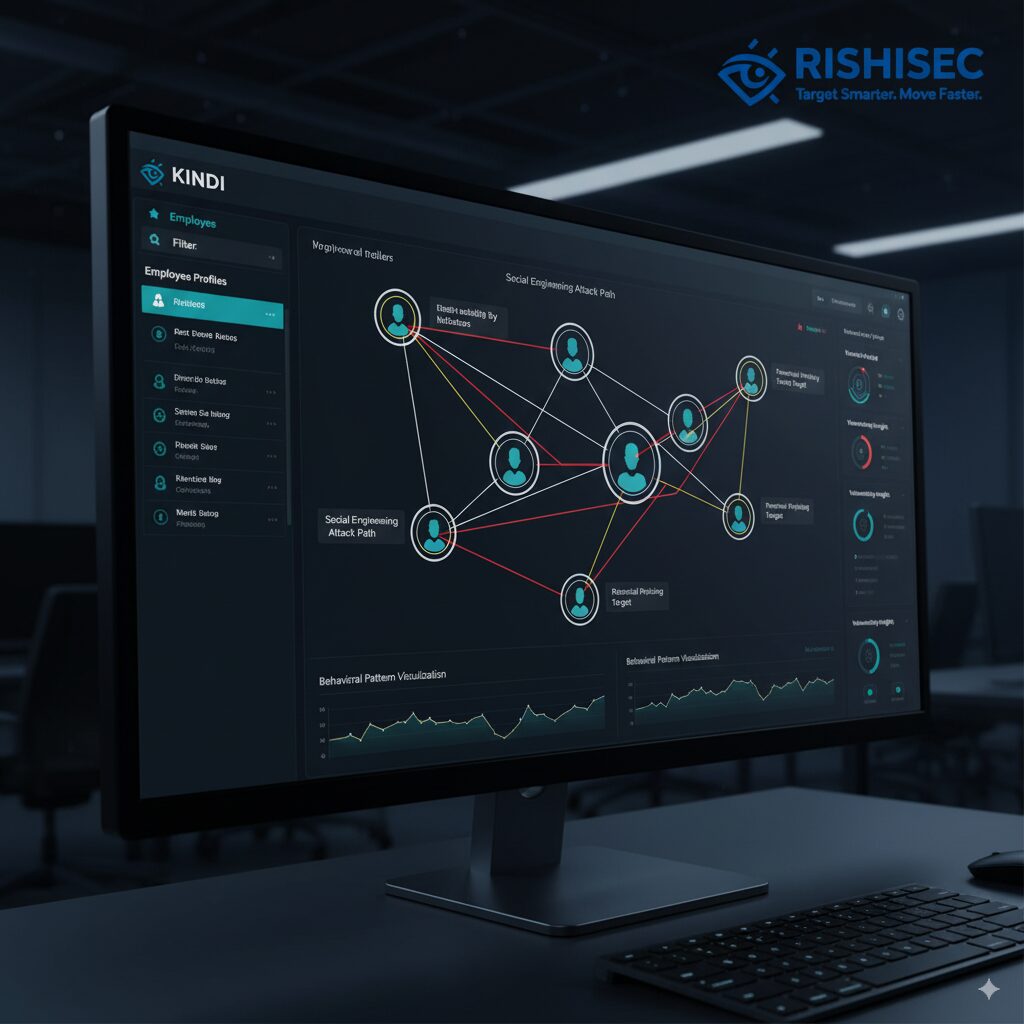
Modern red teams require efficient tools to manage complex OSINT operations at scale. Kindi, RishiSec’s AI-powered OSINT platform, accelerates the reconnaissance phase by automating data collection and correlation across multiple sources.
Where manual OSINT might take days to map an organization’s structure, Kindi completes this analysis in minutes. Its link analysis capabilities automatically identify relationships between employees, vendors, and infrastructure, visualizing attack paths that might otherwise remain hidden in disconnected data points.
For red team engagements, Kindi streamlines pretext development by correlating social media activity, breach data, and organizational information into comprehensive profiles. Teams can quickly identify high-value targets, understand their digital behavior patterns, and craft personalized social engineering scenarios backed by solid intelligence.
The platform’s collaboration features enable multiple analysts to work simultaneously on complex engagements, sharing findings and building collective intelligence about target organizations. Export capabilities transform raw OSINT into professional reports that demonstrate vulnerabilities to clients, complete with evidence chains and remediation recommendations.
By reducing the time spent on manual data collection, Kindi enables red teams to focus on creative attack simulations and thorough documentation. This efficiency improves engagement quality while lowering costs, making comprehensive security testing accessible to more organizations.
Conclusion
OSINT social engineering represents the intersection of technical reconnaissance and psychological manipulation. Red teams demonstrate how publicly available information becomes weaponized against human vulnerabilities, bypassing sophisticated technical defenses through targeted exploitation of trust and authority.
Organizations must understand that their security posture extends beyond firewalls and endpoint protection. Every employee’s digital footprint contributes to organizational risk, and adversaries systematically exploit these exposures through social engineering attacks grounded in thorough OSINT reconnaissance.
Defensive strategies require both awareness and technical controls. Employees need to understand their digital exposure and recognize social engineering attempts. Organizations need tools that monitor their OSINT footprint and detect exploitation attempts before significant damage occurs.
Explore how Kindi accelerates red team reconnaissance and strengthens your organisation’s defences against OSINT-driven social engineering attacks.
Want to strengthen your OSINT skills and master social engineering defenses? Check out our OSINT courses for practical, hands-on training that prepares security professionals to recognize and counter these evolving threats.
FAQ
What is OSINT social engineering?
OSINT social engineering combines open source intelligence gathering with psychological manipulation techniques. Attackers collect publicly available information about targets from social media, data breaches, and online sources, then use this intelligence to craft convincing pretexts that manipulate victims into revealing credentials, granting access, or performing actions that compromise security. This approach bypasses technical defenses by exploiting human psychology rather than system vulnerabilities.
How do red teams use OSINT for social engineering?
Red teams conduct systematic reconnaissance of target organizations using OSINT techniques, mapping employee relationships, identifying technology stacks, and analyzing digital behavior patterns. They use this intelligence to develop realistic attack scenarios that test organizational defenses, demonstrating how adversaries could exploit human vulnerabilities. Red team exercises help organizations identify weaknesses in security awareness, policies, and technical controls before real attackers exploit them.
What information do attackers gather during OSINT reconnaissance?
Attackers collect employee names, job titles, email formats, phone numbers, reporting structures, technology systems, vendor relationships, and personal information from social media. They search breach databases for credentials, analyze GitHub repositories for technical details, and monitor company announcements for operational information. This data creates detailed profiles that inform targeted phishing, vishing, and physical access attempts designed to bypass security awareness.
How can organizations defend against OSINT-driven social engineering?
Effective defense requires security awareness training that shows employees their actual digital footprint, policies limiting sensitive information sharing online, technical controls like multi-factor authentication, and regular monitoring of the organization’s public intelligence exposure. Organizations should conduct red team exercises to identify vulnerabilities, implement verification procedures for unusual requests, and use OSINT monitoring tools to detect when their information appears in breach databases or is being actively researched by potential attackers.
What role does automation play in OSINT social engineering?
Automation dramatically accelerates OSINT collection and analysis, enabling both attackers and defenders to process vast amounts of information quickly. Tools like Kindi help red teams map organizations efficiently, correlate disparate data points, and identify attack paths that manual analysis might miss. For defenders, automated OSINT monitoring provides early warning when organizational information appears in compromising contexts, while AI-powered analysis detects patterns indicating active reconnaissance by potential adversaries.

