Encrypted messaging apps have fundamentally changed how criminals communicate, and law enforcement agencies worldwide are scrambling to keep up. With billions of people now using end-to-end encrypted platforms like Signal, WhatsApp, and Telegram, investigators face a new reality: the evidence they need is often locked behind unbreakable digital walls. According to recent FBI training documents, different messaging platforms offer varying levels of access to investigators, even when investigators possess proper legal authority. While some apps, like WhatsApp, provide metadata and limited message content with warrants, others, like Signal, offer virtually no investigative access.
This encryption barrier isn’t just a technical inconvenience; it represents a fundamental shift in criminal investigations. Drug trafficking organizations, human smuggling rings, and organized crime syndicates have migrated to encrypted platforms precisely because they know traditional surveillance methods won’t work. However, this doesn’t mean investigations have hit a dead end. Smart law enforcement agencies are developing new strategies that combine OSINT techniques, legal frameworks, and cutting-edge technology to work around encryption challenges.
Understanding What Data You Can Actually Access
Before developing an investigation strategy, it is essential to understand exactly what information each platform will provide. The landscape varies dramatically from app to app, and this knowledge can make or break your case.
Metadata vs Message Content: Knowing the Difference
Most encrypted platforms will provide metadata even when the message content remains inaccessible. This includes timestamps, IP addresses, device information, and connection logs. While this might seem like limited intelligence, experienced investigators know that metadata often tells a compelling story. You can establish patterns of communication, identify associate networks, and build timelines that corroborate other evidence sources.
For instance, if you’re investigating a drug trafficking network, metadata showing that suspect devices connected from the same geographic locations at the same times can establish co-conspiracy. Similarly, sudden spikes in communication frequency before known criminal events can demonstrate coordination and planning.
Platform-Specific Access Levels
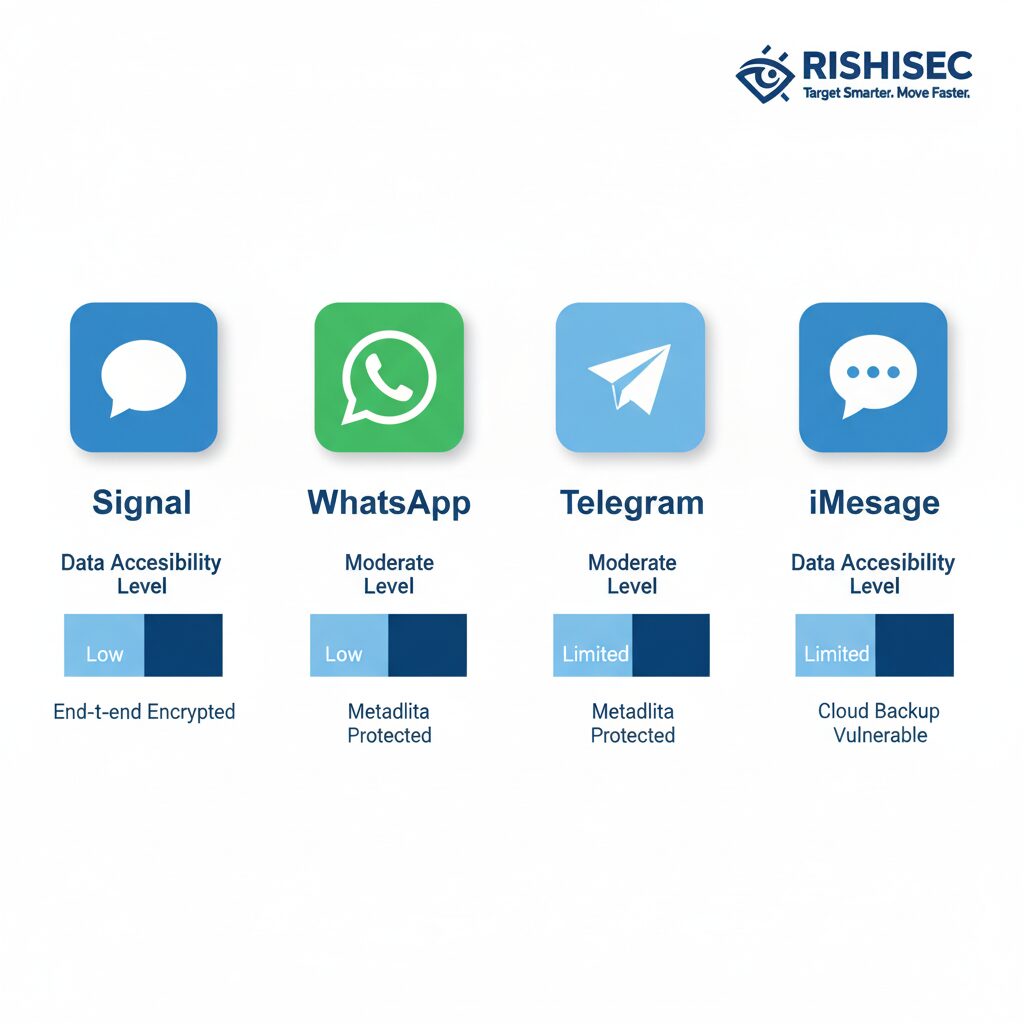
WhatsApp, despite its end-to-end encryption marketing, actually provides significant data to law enforcement with proper legal process. Investigators can obtain message content for stored, undelivered messages, along with comprehensive metadata, including contact lists and group membership information. This makes WhatsApp investigations substantially more productive than many realize.
Signal, by design philosophy and technical architecture, provides almost nothing. Even with court orders, investigators typically receive only account creation dates and last connection times. This minimal data collection is precisely why sophisticated criminal organizations have migrated to Signal.
Telegram occupies a middle ground, being controversial due to its selective cooperation with authorities. The platform provides IP addresses and phone numbers for confirmed terrorists with proper legal requests, but has historically resisted broader law enforcement cooperation. Understanding these nuances helps investigators prioritize their efforts and set realistic expectations.
OSINT Strategies for Encrypted Communication Investigations
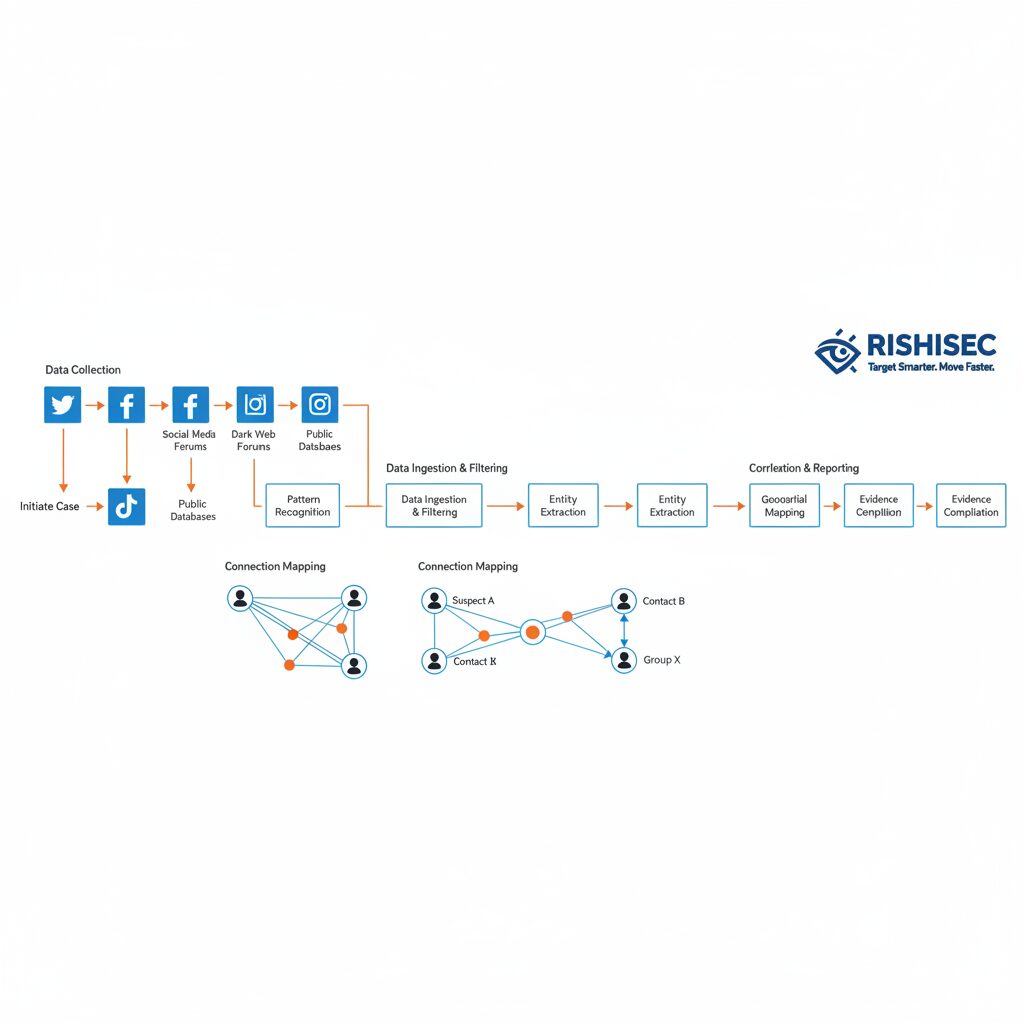
When direct access to encrypted messages isn’t possible, OSINT becomes your primary investigative tool. The key is understanding that while you can’t read the messages, you can often identify who is communicating, establish their networks, and gather corroborating evidence from public sources.
Social Media Cross-Referencing Techniques
Criminals using encrypted apps for operational security often maintain normal social media presences for their cover identities. By monitoring public social platforms, investigators can identify behavioral patterns that align with encrypted communication activity. Look for suspects who post about locations that match metadata timestamps, or who reference meetings that correspond with communication spikes.
This approach requires patience and systematic documentation. Tools like Kindi excel at automating this cross-referencing process, allowing investigators to track multiple suspects simultaneously across dozens of platforms while building visual relationship maps that reveal hidden connections. The AI-powered link analysis can identify patterns that would take weeks to discover manually, especially in complex multi-jurisdictional cases.
Username and Identifier Tracking
Many users reuse handles, email addresses, or phone numbers across multiple platforms. This operational security failure creates investigative opportunities. By documenting all identifiers associated with encrypted messaging accounts, you can search for those same identifiers on forums, marketplaces, gaming platforms, and dating sites.
Dark web marketplaces are particularly valuable for this approach. Vendors using encrypted messaging for transactions often advertise using the same handles they use on Telegram or Signal. Dark web OSINT can connect encrypted communications to criminal marketplaces, providing the evidence needed for warrants and indictments.
Device and Infrastructure Analysis
Encrypted messaging apps still run on devices connected to the internet through identifiable infrastructure. IP addresses, Wi-Fi networks, and cellular towers all create investigative trails. When suspects use encrypted apps from locations you can identify through metadata, you can often gather additional evidence through traditional surveillance or geospatial intelligence.
Furthermore, many suspects make mistakes by taking screenshots of encrypted conversations and posting them elsewhere, or by backing up encrypted chats to unencrypted cloud services. Thorough OSINT investigation often uncovers these security lapses.
Legal Frameworks and International Cooperation
Successfully investigating encrypted communications requires understanding the legal landscape and knowing how to leverage international cooperation mechanisms. Different jurisdictions have vastly different approaches to encryption and data access.
Mutual Legal Assistance Treaties
Most major encrypted messaging platforms are headquartered in the United States or Europe, making Mutual Legal Assistance Treaties your primary tool for formal data requests. However, MLAT processes are notoriously slow, often taking months or even years to produce results. This timeline problem means you need to submit requests early in investigations, not as last-minute efforts.
Recent international operations have shown the value of coordinating MLAT requests across multiple jurisdictions simultaneously. When investigating transnational crime networks using encrypted apps, parallel requests to multiple countries can create comprehensive intelligence pictures even when individual responses are limited.
Emergency Disclosure Requests
Most platforms maintain emergency disclosure processes for imminent threats to life or serious bodily harm. These requests bypass normal warrant requirements but require clear articulation of the immediate danger. Understanding when and how to use emergency disclosures can save lives in kidnapping, terrorism, or active threat scenarios.
However, investigators should never abuse emergency disclosure processes. Platforms track these requests carefully, and misuse damages the credibility needed for future legitimate emergencies. Maintain detailed documentation justifying every emergency request.
| Platform | Metadata Available | Message Content | Response Time |
|---|---|---|---|
| Comprehensive (contacts, timestamps, IP logs) | Undelivered messages only | 2-4 weeks | |
| Signal | Minimal (creation date, last connection) | None | 1-2 weeks |
| Telegram | Limited (IP, phone number for terrorists) | Cloud chats only (not secret chats) | Variable |
| iMessage | Moderate (user data, device info) | None for encrypted messages | 2-3 weeks |
Technology Solutions and AI-Powered Investigation Tools
While legal processes grind slowly forward, technology offers immediate solutions for managing the complexity of encrypted messaging investigations. Modern OSINT platforms leverage artificial intelligence to automate the time-consuming work of data collection, correlation, and analysis.
Automated Link Analysis and Pattern Recognition
Traditional investigations required analysts to manually map relationships between suspects, associates, and criminal activities. This process could take weeks for complex cases involving dozens of individuals. AI-powered platforms like Kindi automate this entire workflow, ingesting data from multiple sources and automatically generating visual network maps that highlight key relationships and hidden connections.
For encrypted messaging investigations specifically, this means you can feed metadata from legal disclosures, OSINT from social media monitoring, and intelligence from informant reports into a single platform that identifies patterns across all these data sources. The system can flag when suspects start communicating more frequently, when new individuals join established networks, or when communication patterns shift in ways that suggest operational planning.
Cross-Platform Investigation Management
Modern criminal investigations rarely involve just one communication platform. Suspects use WhatsApp for some conversations, Signal for others, and traditional phone calls when they think surveillance isn’t active. Managing investigations across these multiple channels creates overwhelming data complexity.
Integrated investigation platforms solve this problem by providing single interfaces where investigators can track all communication channels simultaneously. Rather than switching between different systems and manually correlating information, everything appears in one unified timeline with automated correlation highlighting when the same individuals appear across different platforms.
Collaborative Investigation Environments
Encrypted messaging investigations often span multiple agencies and jurisdictions. Federal, state, and local investigators need to share intelligence while maintaining proper security and chain of custody. Traditional methods, such as email and shared drives, create version control nightmares and security risks.
Modern platforms offer secure collaborative environments that enable multi-agency teams to work together in real-time. Investigators from different departments can contribute intelligence, view updates as they occur, and maintain comprehensive audit trails that show exactly who accessed what information and when. This collaboration capability is especially crucial for tracking criminal networks that operate across jurisdictional boundaries.
Building Successful Cases Without Direct Message Access
Prosecutors and defense attorneys both understand the limitation that encryption places on evidence gathering. Building successful cases in this environment requires different strategies focused on corroborating evidence and demonstrating patterns of behavior.
Constructing Circumstantial Evidence Networks
When you cannot present the smoking gun of actual message content, you need to build comprehensive circumstantial cases. This means documenting every connection between suspects, every financial transaction, every location where they met, and every public statement that aligns with criminal activity you’re investigating.
Modern juries understand encryption exists and accept that investigators won’t always have direct access to communications. What they need to see is a preponderance of evidence that tells a clear story. Metadata showing suspects communicated right before crimes occurred, combined with OSINT showing them at crime scenes, combined with financial records showing unexplained income creates compelling narratives.
Leveraging Cooperating Witnesses
When one member of an encrypted messaging group decides to cooperate, they can provide screenshots, detailed testimony about conversation content, and context that transforms metadata into robust evidence. Developing cooperating witnesses should be a priority in investigations involving encrypted communication.
The key is identifying which group members have the least criminal culpability or the most to lose from prosecution. Focus investigation resources on creating leverage that encourages cooperation, such as documenting their involvement thoroughly while offering favorable plea arrangements in exchange for detailed testimony.
Device Seizure and Forensic Analysis
Encryption protects messages in transit and at rest on servers, but it doesn’t always protect them on seized devices. Many users don’t enable encryption on their phones, or they use weak passcodes that forensic tools can crack. Even when device encryption is strong, suspects often have backups, screenshots, or other evidence of encrypted conversations stored in accessible formats.
Thorough digital forensics on seized devices frequently uncovers evidence that encryption should have protected but didn’t because of user error or backup misconfigurations. This makes proper evidence collection during arrests critical. Ensure devices are seized before suspects can remotely wipe them, and engage digital forensics specialists immediately.
Practical Tips for Encrypted Messaging Investigations
- Document everything from day one. Metadata that initially appears insignificant often becomes crucial evidence later in investigations.
- Submit legal process requests early. The weeks or months required for responses mean you should request data as soon as investigations begin, not when you need it for imminent prosecutions.
- Build redundancy into your evidence gathering. Never rely solely on encrypted platform disclosures. Always pursue parallel OSINT and traditional investigation methods.
- Maintain a detailed chain of custody for all digital evidence. Defense attorneys will challenge how evidence was gathered and stored, especially in cases involving sophisticated defendants.
- Invest in training your team on new platforms and techniques to enhance their skills and capabilities. The encrypted messaging landscape is constantly evolving, and what worked six months ago may no longer be effective today.
- Establish relationships with platform legal teams before you need emergency assistance. Knowing who to contact and having established credibility speeds up critical time-sensitive requests.
- Use OSINT automation tools to manage investigation complexity. Manual processes simply cannot keep pace with the data volumes involved in modern encrypted messaging cases.
Moving Forward With Encrypted Communication Investigations
Encrypted messaging represents one of the most significant challenges facing modern law enforcement, but it’s far from insurmountable. Agencies that invest in proper training, leverage advanced OSINT techniques, and deploy AI-powered investigation tools are successfully prosecuting cases that once would have been impossible.
The key is accepting that investigations have fundamentally changed. You won’t always get direct access to message content, but that doesn’t mean investigations fail. By building comprehensive cases using metadata, OSINT intelligence, traditional surveillance, and forensic evidence, you can achieve successful prosecutions even when encryption protects the actual conversations.
Success requires embracing new technology and new methodologies. The investigators who adapt to this reality will thrive, while those clinging to outdated approaches will increasingly struggle. The criminal world has already adapted to encrypted communications. Law enforcement must do the same.
Want to modernize your encrypted messaging investigations? Discover how Kindi automates OSINT collection and analysis, providing AI-powered link analysis that reveals hidden networks and connections across encrypted platforms. Start your free trial today.
Looking to strengthen your digital investigation skills? Explore our OSINT courses for practical, hands-on training designed specifically for law enforcement professionals addressing modern encrypted communication challenges.
FAQ
Can law enforcement decrypt end-to-end encrypted messages?
No, true end-to-end encryption cannot be broken by law enforcement or the platform providers themselves. However, investigators can often obtain metadata, access backups that aren’t encrypted, or leverage device forensics to recover message content from seized phones. The key is understanding what data is available through legal process and building cases using alternative evidence sources when message content is inaccessible.
Which encrypted messaging apps provide the most data to law enforcement?
WhatsApp provides the most comprehensive data to law enforcement with proper legal authority, including metadata like contact lists, timestamps, IP logs, and even undelivered message content. iMessage provides moderate metadata and user information but no encrypted message content. Signal and Telegram provide minimal data by design, making investigations significantly more challenging.
How long does it take to get data from encrypted messaging platforms?
Response times vary significantly by platform and request type. Emergency disclosure requests for imminent threats typically receive responses within 24 to 48 hours. Standard warrant responses range from one to four weeks for most major platforms. International MLAT requests can take months or even years, making early submission critical for investigation success.
Can OSINT replace direct access to encrypted messages?
OSINT cannot replace encrypted message content, but it can provide sufficient alternative evidence to build successful prosecutions. By monitoring public social media, tracking usernames across platforms, analyzing metadata patterns, and correlating multiple intelligence sources, investigators can establish criminal activity, network relationships, and timeline evidence that supports strong cases even without direct message access.
What legal authority do I need to request data from encrypted messaging platforms?
Requirements vary by jurisdiction and platform. In the United States, most platforms require search warrants or court orders for metadata and content disclosure. Emergency situations may allow immediate disclosure without warrants when imminent threats to life exist. International investigations typically require Mutual Legal Assistance Treaty requests, though some platforms respond to properly authorized foreign warrants. Always consult your legal counsel for specific guidance on your jurisdiction’s requirements.
How can AI tools help with encrypted messaging investigations?
AI-powered investigation platforms automate the time-consuming work of collecting OSINT, correlating metadata, and identifying patterns across multiple data sources. These tools can monitor dozens of suspects simultaneously across numerous platforms, automatically generating network maps that reveal hidden connections. AI also identifies behavioral patterns and communication anomalies that human analysts might miss, significantly speeding investigation timelines while improving evidence quality.

