Security teams invest heavily in threat intelligence feeds and subscribe to premium services, yet many struggle to demonstrate measurable improvements in their security posture. The problem isn’t the quality of intelligence; instead, it’s the failure to operationalize that intelligence into defensive action that actually stops threats.
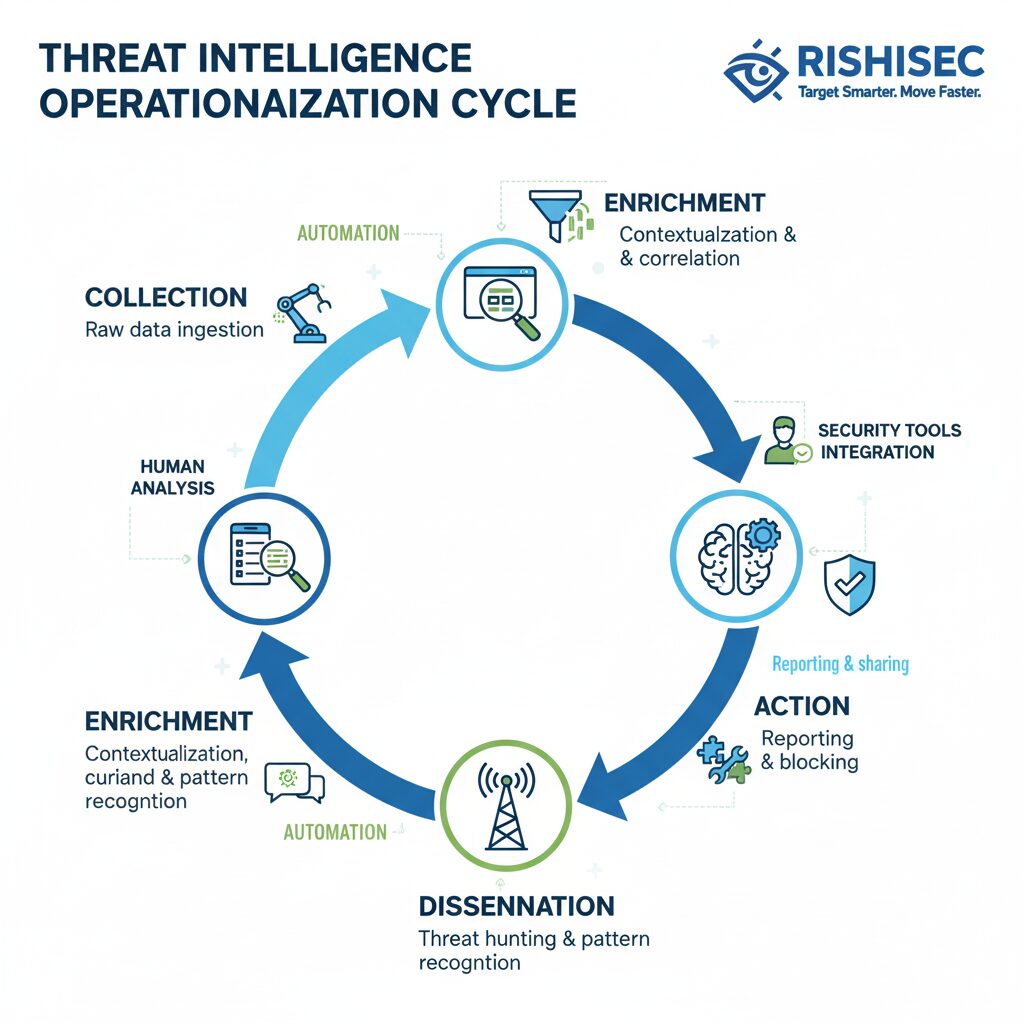
Threat intelligence operationalization is the discipline that transforms raw threat data into measurable defensive action. Furthermore, it ensures intelligence doesn’t just sit in repositories or analyst reports but actively drives detection rules, response playbooks, and protective measures across your entire security stack. For threat intel analysts, cyber threat leads, and cybersecurity analysts, operationalization represents the difference between intelligence as an academic exercise and intelligence as a force multiplier for security operations.
The challenge intensifies as threat landscapes evolve rapidly. Adversaries adapt their tactics faster than traditional intelligence workflows can process and disseminate findings. By the time human analysts manually review intelligence, create reports, and coordinate with security operations teams to implement changes, the threat landscape has already shifted. Understanding key differences between threat intelligence and threat data becomes essential for building effective operationalization frameworks.
Understanding the Intelligence to Action Gap in Modern Security Operations
Most organizations suffer from what security professionals call the “intelligence to action gap.” In this scenario, valuable threat intelligence exists within the organization but never translates into improved security outcomes. Threat intel analysts identify emerging threats and document adversary tactics; however, security operations teams continue responding to incidents that intelligence predicted weeks earlier.
This gap emerges from several structural problems. First, intelligence and operations teams often work in silos with limited communication channels. Intelligence teams focus on strategic analysis and reporting, while security operations teams prioritize immediate incident response and alert triage. Without formal mechanisms ensuring intelligence flows into operational workflows, valuable insights remain trapped in reports that operational teams lack time to read.
Second, much collected threat intelligence arrives in formats that operational teams cannot directly use. A detailed report about adversary tactics proves intellectually interesting; nevertheless, it provides no immediate actionable guidance for security operations center (SOC) analysts monitoring alerts. Converting strategic intelligence into tactical indicators, detection rules, and response procedures requires dedicated effort that many organizations lack resources to perform consistently.
Common Operationalization Challenges Facing Security Teams
- Data volume overload: Organizations subscribe to dozens of threat intelligence feeds producing millions of indicators daily. Consequently, this overwhelms analysts who lack automated methods to prioritize which intelligence actually matters for their specific environment and threat model.
- Context deficiency: Raw indicators without context about adversary intent, targeting patterns, or attack methodologies provide limited value. SOC teams need to understand why specific intelligence matters to their organization, not just receive lists of suspicious IP addresses or file hashes.
- Integration complexity: Enterprise security stacks typically include dozens of tools from multiple vendors. Therefore, integrating threat intelligence across firewalls, endpoint detection systems, SIEM platforms, and other security controls requires significant engineering effort.
- Timeliness problems: Manual intelligence processing introduces delays that reduce effectiveness. By the time analysts review, validate, and disseminate intelligence, adversaries have often moved to new infrastructure or tactics.
- Measurement difficulties: Organizations struggle to demonstrate return on investment for threat intelligence programs because they lack metrics showing how operationalized intelligence prevented incidents or reduced response times.
Building Effective Threat Intelligence Operationalization Frameworks
Successful threat intelligence operationalization requires systematic frameworks that define how intelligence flows from collection through analysis to defensive action. The most effective frameworks establish clear processes for each stage while incorporating automation that eliminates manual bottlenecks preventing timely action.
Collection prioritization represents the first critical step. Rather than attempting to consume all available threat intelligence, organizations should focus collection on sources most relevant to their industry, technology stack, and threat model. A financial services company faces different threats than a healthcare provider or manufacturing firm. Threat intel analysts should tailor collection to answer specific intelligence requirements derived from organizational risk assessments.
Enrichment and contextualization transform raw indicators into actionable intelligence. When an indicator appears in threat feeds, enrichment processes add context about associated campaigns, targeted industries, observed tactics, and confidence levels. This context enables SOC teams to prioritize responses appropriately rather than treating all indicators as equally important. Integrating OSINT to prioritize alerts and unmask real threats provides frameworks for effective contextualization.
| Operationalization Stage | Key Activities | Success Metrics |
|---|---|---|
| Collection & Aggregation | Gather intelligence from internal sources, commercial feeds, open sources, and industry sharing groups; normalize data formats; deduplicate indicators | Coverage of relevant threat actors; time from indicator publication to ingestion; percentage of indicators with sufficient context |
| Enrichment & Analysis | Add context from multiple sources; assess relevance to organization; determine confidence levels; identify relationships between indicators | Percentage of indicators enriched; average enrichment time; false positive rate reduction |
| Dissemination & Integration | Push intelligence to security tools; create detection rules; update response playbooks; brief security teams on emerging threats | Number of security tools receiving intelligence; time from analysis to tool integration; coverage of detection rules |
| Action & Response | Automatically block known malicious indicators; trigger alerts for suspicious activity; guide incident response procedures | Blocked threats; reduced dwell time; decreased mean time to respond (MTTR) |
| Feedback & Refinement | Measure intelligence effectiveness; identify gaps in coverage; adjust collection priorities; improve enrichment processes | Intelligence quality scores; percentage of incidents predicted by intelligence; stakeholder satisfaction |
Dissemination mechanisms must match intelligence to appropriate audiences and tools. Strategic intelligence about emerging threat actor campaigns goes to security leadership and architecture teams planning long-term defenses. Meanwhile, tactical indicators flow directly into security tools for automated blocking or alerting. Operational intelligence about adversary tactics informs SOC playbook updates and analyst training programs.
Leveraging Automation and AI for Scalable Threat Intelligence Operations
Manual threat intelligence processes cannot scale to meet modern requirements. Adversaries operate at machine speed, launching attacks within minutes of discovering vulnerabilities. Defense must operate at similar speed, which requires automation that processes intelligence, makes prioritization decisions, and implements protective measures faster than human analysts can work.
Kindi addresses this challenge through AI-powered intelligence operationalization specifically designed for enterprise security teams. The platform automatically ingests intelligence from multiple sources, enriches indicators with contextual information from OSINT and proprietary databases, and prioritizes threats based on relevance to your specific environment. Rather than analysts manually reviewing thousands of indicators daily, Kindi surfaces the high-priority intelligence requiring human attention while automatically actioning routine defensive measures.
The link analysis capabilities prove particularly valuable for understanding complex threat campaigns. When investigating suspicious indicators, cyber threat leads need to understand relationships between domains, IP addresses, file hashes, and threat actor infrastructure. Kindi automatically maps these connections, revealing campaign scope and enabling comprehensive defensive measures rather than piecemeal responses to individual indicators. This visibility transforms how security teams respond to threats, moving from reactive incident handling to proactive campaign disruption.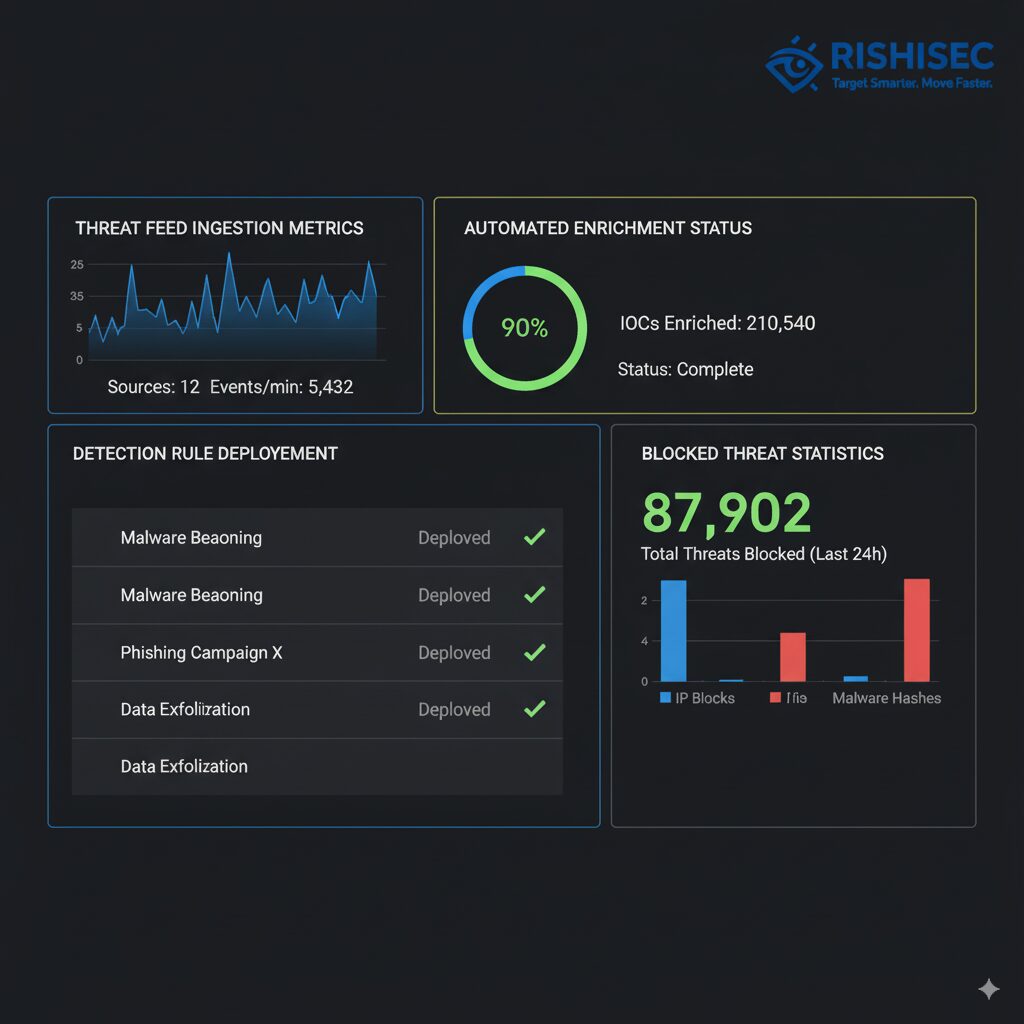
Automation should augment rather than replace human analysts. Machines excel at processing vast data volumes, identifying patterns, and executing repetitive tasks at scale. Humans excel at strategic thinking, understanding organizational context, and making judgment calls about ambiguous situations. Effective operationalization combines these strengths, with automation handling routine intelligence processing while analysts focus on complex analysis, strategic planning, and continuous program improvement.
Integrating Threat Intelligence Across Enterprise Security Architecture
Operationalized threat intelligence must integrate across the entire security stack to maximize defensive effectiveness. Siloed intelligence that informs only specific tools leaves gaps that adversaries exploit. Comprehensive integration ensures every security control benefits from current threat intelligence, creating defense in depth where multiple layers incorporate the same intelligence insights.
Network security devices represent the first integration point. Firewalls, intrusion prevention systems, and web proxies can automatically block connections to known malicious infrastructure based on operationalized threat intelligence. This prevents initial compromise attempts and reduces attack surface before adversaries establish footholds. However, blocking alone proves insufficient; security teams must also log blocked connection attempts to identify targeting patterns and potential reconnaissance activities.
Endpoint security platforms benefit enormously from operationalized intelligence. Detection rules informed by current threat intelligence identify malicious file execution, suspicious registry modifications, and anomalous network connections that indicate compromise. Response automation can isolate infected endpoints immediately upon detection, preventing lateral movement before security teams begin manual investigation. This rapid response capability dramatically reduces dwell time and limits damage from successful intrusions.
SIEM and security analytics platforms consume threat intelligence to enrich alerts and guide investigation workflows. When an alert fires, enrichment with threat intelligence context helps analysts immediately understand whether the activity relates to known threat campaigns, which adversary tactics it resembles, and what response procedures apply. This contextualization accelerates triage and ensures appropriate response urgency. According to Gartner research, organizations that effectively operationalize threat intelligence reduce incident response times by an average of 40%.
Measuring Threat Intelligence Operationalization Program Effectiveness
Demonstrating threat intelligence value requires metrics that show how operationalized intelligence improves security outcomes. Cyber threat leads face pressure to justify intelligence program investments, particularly when leadership questions whether expensive threat feeds and specialized analyst positions produce measurable returns. Effective measurement frameworks connect intelligence activities to concrete security improvements.
Prevention metrics quantify threats blocked before causing harm. How many malicious connections did intelligence-informed firewall rules block? How many malicious files did endpoint security prevent from executing based on intelligence-derived indicators? How many phishing domains did intelligence enable proactive blocking of before employees encountered them? These metrics demonstrate direct defensive value from operationalized intelligence.
Detection and response metrics show how intelligence improves incident handling. Did operationalized intelligence reduce mean time to detect (MTTD) incidents? Did it decrease mean time to respond (MTTR) by providing response guidance alongside alerts? Did it reduce false positive rates by improving alert accuracy? Organizations that effectively operationalize intelligence typically see dramatic improvements across these metrics compared to organizations relying solely on signature-based detection.

Efficiency metrics reveal operational improvements beyond direct threat prevention. Did operationalization reduce analyst workload through automation? Did it improve collaboration between intelligence and operations teams? Did it enable more proactive security posture rather than constant reactive firefighting? These operational benefits often prove as valuable as direct threat prevention, particularly for organizations struggling with analyst burnout and retention challenges.
Practical Implementation Strategies for Operationalizing Threat Intelligence
- Start with quick wins: Begin operationalization with highest-confidence intelligence from most reliable sources, proving value before expanding scope. Early successes build organizational support for broader implementation.
- Automate repetitive tasks first: Identify manual intelligence processing activities consuming significant analyst time but requiring minimal human judgment, then implement automation to free analysts for higher-value work.
- Establish clear escalation paths: Define which intelligence automatically flows to security tools versus which requires human analysis before action. Unclear escalation creates bottlenecks that delay protective measures.
- Create feedback mechanisms: Build processes where operations teams report intelligence effectiveness back to intelligence teams, enabling continuous refinement of collection priorities and enrichment procedures.
- Measure and communicate value: Track metrics demonstrating operationalization benefits and regularly brief leadership on prevented incidents, improved response times, and operational efficiencies gained.
- Invest in analyst development: Operationalization requires new skills combining intelligence analysis with security operations knowledge. Provide training that develops these hybrid capabilities across teams.
Want to transform your threat intelligence from reports to action? Explore our specialized courses on operationalizing threat intelligence for enterprise security teams. Ready to automate intelligence operations and accelerate your threat response? Discover Kindi’s AI-powered platform for seamless threat intelligence operationalization.
FAQ
What is threat intelligence operationalization?
Threat intelligence operationalization is the systematic process of transforming raw threat data into measurable defensive actions across your security infrastructure. It involves collecting intelligence from multiple sources, enriching it with context, analyzing relevance to your organization, disseminating it to appropriate teams and tools, and implementing protective measures that block threats or enable rapid response. Operationalization ensures intelligence actively improves security outcomes rather than remaining in reports or databases.
How does operationalized threat intelligence differ from traditional threat feeds?
Traditional threat feeds provide raw indicators of compromise (IOCs) like IP addresses, domains, or file hashes without context or integration guidance. Operationalized threat intelligence adds contextual enrichment about adversary campaigns, targeting patterns, and tactical recommendations, then automatically integrates this intelligence into security tools for immediate defensive action. The key difference is moving from passive information consumption to active defensive measures that prevent or detect threats based on intelligence insights.
What are the biggest challenges in operationalizing threat intelligence?
The biggest challenges include organizational silos between intelligence and operations teams that prevent effective collaboration, data volume overload from too many intelligence sources producing millions of indicators, technical integration complexity across diverse security tool stacks, lack of contextual enrichment that helps prioritize which intelligence matters most, and difficulties measuring program effectiveness to justify continued investment. Successful operationalization requires addressing these challenges systematically through automation, clear processes, and cross-team alignment.
How can small security teams operationalize threat intelligence effectively?
Small teams should focus on quality over quantity by selecting fewer high-quality intelligence sources most relevant to their threat model, leveraging automation platforms that handle routine processing and integration tasks, starting with highest-confidence intelligence to prove value quickly, and integrating intelligence with security tools providing maximum defensive impact first. Cloud-based threat intelligence platforms enable small teams to access enterprise-grade operationalization capabilities without large infrastructure investments or specialized personnel.
What metrics demonstrate threat intelligence operationalization success?
Key metrics include threats prevented (blocked connections, stopped malware, prevented phishing), detection improvements (reduced mean time to detect, lower false positive rates), response enhancements (decreased mean time to respond, improved incident accuracy), operational efficiency (reduced analyst workload, increased automation percentage), and strategic benefits (better risk prioritization, improved security architecture decisions). Effective measurement combines technical metrics showing direct threat prevention with operational metrics demonstrating process improvements and strategic value.