Government intelligence operations face increasingly sophisticated adversaries who understand surveillance techniques, employ advanced operational security, and deliberately manipulate their digital footprints to deceive analysts. Generic threat intelligence that treats all actors within a category as interchangeable fails to capture the nuanced behaviors, capabilities, and intentions that distinguish specific threats. Special agents and senior intel analysts require granular adversary profiles that reveal individual or group-specific patterns, enabling predictive analysis and targeted countermeasures.
Advanced adversary profiling builds comprehensive dossiers that go beyond basic attribution to understand motivation structures, decision-making processes, technical capabilities, resource constraints, and operational patterns. This depth of understanding transforms intelligence from reactive threat reporting to proactive strategic planning. When cyber crime unit leads understand not just what an adversary has done but why they chose specific targets, how they adapted to defensive measures, and what constraints limit their operations, they can anticipate future activities and position defenses accordingly.
The challenge intensifies as threat actors operate across multiple domains simultaneously. Nation-state actors conducting cyber espionage also run influence campaigns and may support proxy forces engaged in physical operations. Terrorist networks coordinate across encrypted messaging platforms while maintaining a public-facing social media presence for recruitment purposes. Criminal organizations leverage legitimate business structures to launder proceeds from cybercrime. Tracking criminal networks on social media requires understanding their full operational ecosystem, not just isolated activities on individual platforms.
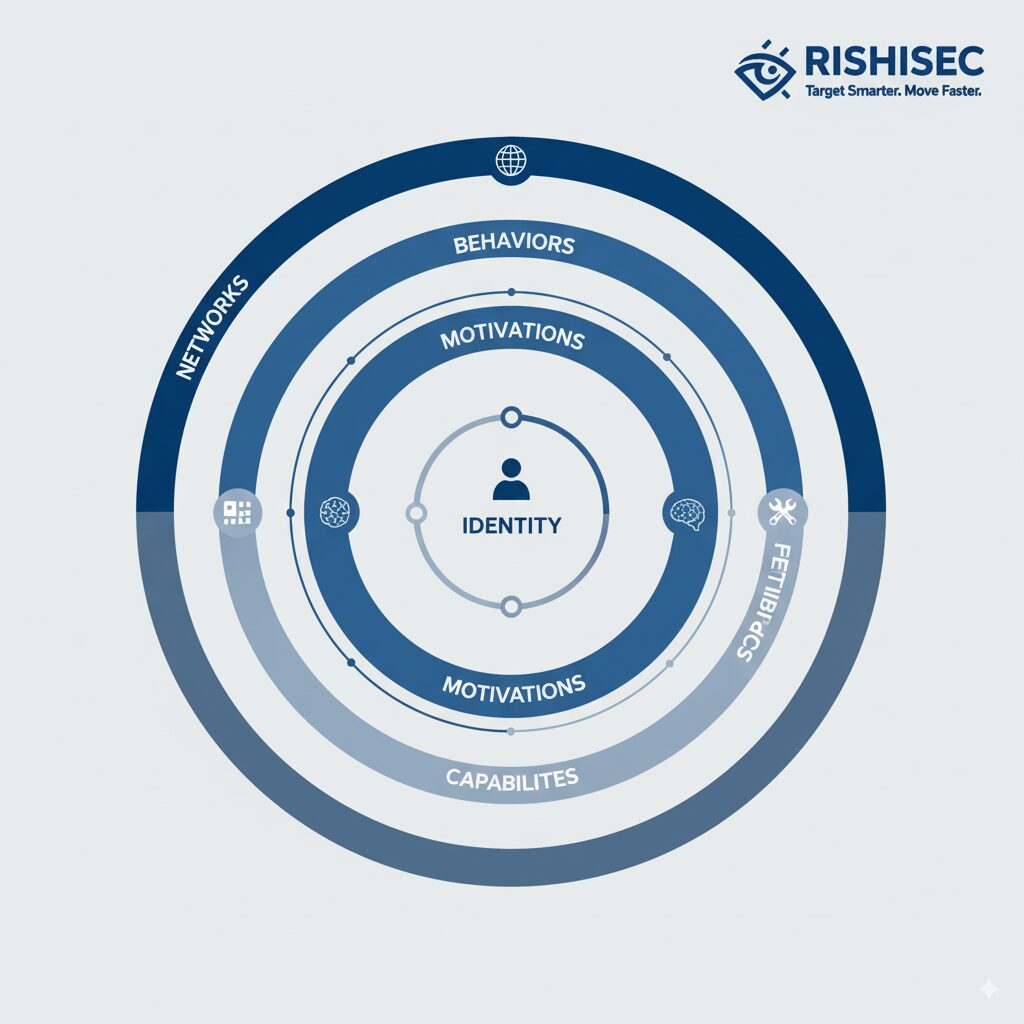
Building Comprehensive Threat Actor Dossiers Through Multi-Source Intelligence
Effective adversary profiling synthesizes information from technical indicators, behavioral analysis, network mapping, and contextual intelligence about operational environments. Technical profiling examines tools, techniques, and procedures (TTPs) that adversaries employ during operations. This includes malware signatures, infrastructure preferences, encryption methods, communication protocols, and evasion techniques. While technical indicators prove valuable for detection, they represent only surface-level understanding of adversary capabilities.
Behavioral profiling reveals deeper patterns about decision-making processes and operational preferences. Some threat actors demonstrate risk tolerance, conducting brazen operations despite high detection probability, while others prioritize operational security above all other considerations. Certain groups rapidly adapt their TTPs when defenses emerge, while others persist with familiar methods even after they become less effective. These behavioral patterns help predict how adversaries will respond to specific countermeasures or environmental changes.
Network analysis maps relationships between individual actors, supporting infrastructure, and organizational structures. Advanced adversary profiling identifies not just the primary threat actor but their suppliers, collaborators, financiers, and operational support networks. When cyber crime unit leads map these networks comprehensively, they can identify pressure points where disruption would cascade through the adversary’s operational ecosystem. A single arrest or infrastructure takedown becomes more valuable when positioned to destabilize an entire network rather than removing a single node.
Essential Components of Advanced Threat Actor Profiles
- Identity and attribution foundations: Establish baseline identity information including known aliases, associated personas, infrastructure ownership, and confirmed attribution from previous operations while maintaining appropriate skepticism about deliberately planted false indicators.
- Capability assessment: Document technical skills, access to specialized tools or exploits, financial resources, language capabilities, and operational reach to understand what adversaries can accomplish versus what they might attempt.
- Motivation and intent analysis: Identify driving factors behind adversary activities, whether ideological commitment, financial gain, state direction, personal grievance, or combination of motivations that may shift over time.
- Operational patterns and preferences: Catalog typical attack vectors, target selection criteria, operational timing, response to defensive measures, and other behavioral consistencies that distinguish this adversary from others.
- Network and infrastructure mapping: Chart relationships between actors, document infrastructure usage patterns, identify command and control mechanisms, and map supply chains for tools, exploits, or other operational necessities.
Leveraging OSINT for Behavioral Pattern Recognition in Threat Actors
Open-source intelligence provides unique advantages for behavioral profiling because adversaries cannot completely eliminate their digital presence without sacrificing operational effectiveness. Even highly sophisticated threat actors must communicate with collaborators, research targets, acquire tools and services, and maintain some level of online presence. The key lies in identifying which open-source signals reliably indicate adversary activity versus noise or deliberate deception.
Social media analysis reveals behavioral patterns that technical indicators miss. How adversaries discuss their operations, interact with communities, respond to public exposure, and adapt their messaging provides psychological insight into decision-making processes. Special agents analyzing extremist networks often find that public statements predict operational shifts weeks before technical indicators change. Social signals advanced OSINT techniques for government intelligence enable analysts to recognize emerging threats before they fully materialize.
Kindi accelerates behavioral pattern recognition through AI-powered analysis of vast open-source data volumes. The platform automatically identifies linguistic patterns, network interaction changes, and operational tempo shifts that human analysts might miss when reviewing thousands of data points manually. Senior intel analysts can define specific behavioral indicators relevant to their threat actors, then let Kindi continuously monitor for pattern changes that warrant detailed investigation. This automation ensures no significant behavioral shift goes unnoticed while freeing analysts to focus on interpretation rather than data collection.
Technical Infrastructure Analysis for Attribution and Forecasting
Infrastructure profiling reveals adversary capabilities, resource constraints, and future operational potential. Sophisticated threat actors invest in resilient infrastructure that survives takedown attempts, while less capable actors rely on easily disrupted free or low-cost services. Understanding these choices helps cyber crime unit leads assess threat severity and prioritize response efforts. An adversary who maintains multiple backup command-and-control servers across jurisdictions presents different challenges than one relying on a single compromised website.
Domain registration patterns, hosting provider selections, and SSL certificate reuse create intelligence opportunities even when adversaries employ privacy services. Careful analysis often reveals infrastructure clusters where multiple adversary operations share common elements, suggesting either the same actor operating under different personas or collaboration between distinct groups. These technical linkages complement behavioral and network analysis to build comprehensive threat pictures.
| Infrastructure Type | Intelligence Value | Analysis Methods |
|---|---|---|
| Domain Infrastructure | Registration patterns reveal operational security sophistication; naming conventions may indicate targets or campaigns; registration timing can predict operational tempo | WHOIS history analysis, DNS record tracking, SSL certificate correlation, domain age assessment |
| Hosting and Servers | Geographic distribution indicates operational reach; provider selection shows resource level; server configurations reveal technical capability | IP space analysis, autonomous system mapping, server fingerprinting, hosting provider identification |
| Communication Platforms | Platform selection reveals target audience; usage patterns indicate operational security awareness; account networks map organizational structure | Platform activity monitoring, account relationship mapping, communication pattern analysis, metadata extraction |
| Tool and Service Usage | Exploit frameworks used indicate technical skill; service purchases show resource availability; tool customization reveals development capability | Malware analysis, tool version identification, service subscription tracking, custom code recognition |
Infrastructure analysis benefits enormously from automation because adversaries frequently rotate infrastructure faster than human analysts can track manually. When Kindi monitors infrastructure indicators continuously, it alerts analysts immediately when adversaries establish new operational infrastructure, reuse previous patterns, or connect new infrastructure to known adversary networks. This real-time awareness enables proactive defensive positioning before adversaries fully operationalize new infrastructure.
Linguistic Analysis and Communication Pattern Profiling
Language provides powerful fingerprints for adversary identification and behavioral analysis. Native language indicators, linguistic quirks, vocabulary choices, and writing styles persist even when adversaries attempt anonymity. Senior intel analysts investigating state-sponsored operations often find linguistic evidence that narrows attribution to specific organizations or even individual operators, particularly when combined with timezone activity patterns and cultural references embedded in communications.
Communication pattern analysis extends beyond content to examine interaction dynamics. How quickly adversaries respond to events, which communities they engage with, whether they initiate conversations or respond to others, and how their communication volume fluctuates all provide behavioral insight. Some threat actors maintain consistent online presence to build credibility within target communities, while others appear only when conducting specific operations. These patterns help distinguish sophisticated operations from opportunistic activities.

Automated linguistic analysis dramatically improves profiling efficiency when dealing with multilingual adversaries or high-volume communications. Manual translation and analysis of thousands of messages proves impractical for most intelligence units, but AI-powered platforms can process massive communication volumes while flagging linguistically significant patterns for human review. This capability proves particularly valuable when monitoring adversaries who deliberately communicate across multiple languages to complicate surveillance.
Integrating Adversary Profiling into Operational Planning and Threat Forecasting
Advanced adversary profiling delivers maximum value when integrated into forward-looking threat forecasting and operational planning. Understanding adversary capabilities, motivations, and behavioral patterns enables intelligence teams to move beyond reactive threat reporting to predictive analysis that identifies likely future activities before they occur. Special agents planning operations against specific threats can leverage detailed adversary profiles to anticipate defensive measures, identify operational windows, and select approaches most likely to succeed given adversary characteristics.
Threat forecasting requires continuous profile updates as adversaries evolve. Static profiles quickly become outdated as threat actors acquire new capabilities, shift targets, adapt to countermeasures, or experience organizational changes. Cybercrime unit leads should establish systematic profile review cycles, perhaps monthly for active, high-priority threats and quarterly for monitored, lower-priority actors. These reviews incorporate new intelligence from recent operations, updates from partner agencies, and analysis of adversary responses to environmental changes.
Collaboration between intelligence and operational elements proves essential for effective profile utilization. Operational personnel provide feedback about profile accuracy based on adversary behaviors observed during field operations, while intelligence analysts gain operational context that improves interpretation of collected information. This feedback loop continuously refines profiles to better support operational needs while ensuring intelligence collection focuses on operationally relevant questions.
Overcoming Common Challenges in Advanced Adversary Profiling
Deception represents the primary challenge in adversary profiling. Sophisticated threat actors deliberately plant false indicators, create misleading personas, and manipulate their digital footprints to waste intelligence resources or misdirect attribution. Senior intel analysts must maintain healthy skepticism about collected information while avoiding paralysis where every indicator is dismissed as potential deception. Corroboration across multiple independent sources, consistency with known adversary patterns, and technical validation help distinguish genuine intelligence from planted deception.
Attribution confidence levels require careful calibration. Intelligence consumers need to understand the difference between confirmed attribution supported by multiple independent sources and probable attribution based on pattern matching to previous operations. Overstating attribution confidence can lead to diplomatic incidents or misdirected operations, while excessive caution prevents actionable intelligence from supporting necessary decisions. AI-powered threat actor attribution</a> helps by quantifying confidence levels based on indicator correlation and historical accuracy.
Resource constraints force prioritization decisions about which adversaries warrant detailed profiling versus basic threat tracking. Not every cybercriminal, hacktivist, or foreign intelligence service deserves comprehensive profiling; intelligence organizations must focus deep analysis on threats most relevant to their mission and most capable of causing significant harm. Threat prioritization frameworks that consider adversary capability, intent, and opportunity help intelligence leaders allocate analytical resources effectively.
Practical Tips for Effective Adversary Profiling
- Start with known confirmed information: Build profiles outward from verified facts rather than speculation; clearly distinguish confirmed intelligence from analytical assessment or unverified reporting.
- Document intelligence gaps explicitly: Identify what you don’t know about adversaries as clearly as what you do know; these gaps guide future collection priorities and prevent overconfidence in incomplete profiles.
- Cross-reference with partner agencies: Other intelligence organizations may possess complementary information about your adversaries; collaboration often reveals critical profile elements that single agencies miss.
- Track profile changes over time: Document how adversary capabilities, behaviors, and networks evolve; understanding change patterns helps predict future evolution and reveals what factors drive adversary adaptation.
- Test profiles against operational outcomes: Compare predicted adversary behaviors from profiles against actual observed activities; discrepancies indicate where profile assumptions require revision.
- Leverage automation for scale: Use AI-powered platforms to monitor adversary infrastructure, communications, and behavioral patterns continuously; human analysts should focus on interpretation of automated findings rather than manual collection.
Transforming Intelligence Operations Through Adversary Understanding
Advanced adversary profiling represents a fundamental shift from reactive threat reporting to proactive intelligence operations. When special agents and senior intel analysts deeply understand their adversaries, they can anticipate operations before they occur, position defenses where they will prove most effective, and conduct offensive operations with higher probability of success. This depth of understanding transforms intelligence from an information service to a strategic advantage that shapes operational outcomes.</p>
The investment required for comprehensive adversary profiling pays dividends across the entire intelligence enterprise. Collection becomes more focused when guided by specific profile gaps rather than generic collection requirements. Analysis improves when analysts understand adversary context deeply enough to recognize significant deviations from established patterns. Operations succeed more frequently when planned against detailed adversary profiles rather than generic threat categories.
Modern profiling capabilities, particularly those leveraging AI-powered OSINT automation, enable intelligence organizations to maintain detailed profiles on far more adversaries than manual methods allowed. Where previous generations might have deeply profiled only a handful of top-priority threats, today’s senior intel analysts can maintain a comprehensive understanding of dozens of significant adversaries while monitoring hundreds of lower-priority actors for signs that they warrant elevated attention. This scalability fundamentally changes what intelligence organizations can accomplish with existing personnel.
Looking forward, adversary profiling will continue to increase in importance as threat actors become more sophisticated and operational environments become more complex. Government intelligence agencies that invest in advanced profiling capabilities now position themselves for continued effectiveness against evolving threats. Those that rely on outdated generic threat models will find themselves increasingly unable to distinguish significant threats from background noise or predict adversary actions with sufficient accuracy to support operational planning.
Want to master advanced profiling techniques and elevate your threat intelligence capabilities? Explore our specialized OSINT courses designed for government intelligence professionals. Ready to automate adversary profiling and scale your intelligence operations? Discover how Kindi transforms threat actor analysis through AI-powered OSINT automation and comprehensive link analysis.
FAQ
What is advanced adversary profiling in intelligence operations?
Advanced adversary profiling is the comprehensive analysis of specific threat actors to understand their capabilities, motivations, behavioral patterns, technical infrastructure, and operational networks. Unlike generic threat intelligence that categorizes actors broadly, advanced profiling creates detailed individualized dossiers that reveal nuanced characteristics enabling predictive analysis and targeted countermeasures. This approach examines not just what adversaries have done but why they made specific operational choices and how they will likely behave in future scenarios.
How does adversary profiling differ from traditional threat intelligence?
Traditional threat intelligence often focuses on technical indicators like malware signatures and attack patterns that apply broadly across threat categories. Adversary profiling goes deeper by examining the specific actors behind attacks, their unique operational preferences, decision-making patterns, and organizational structures. While traditional intelligence helps detect attacks, profiling helps predict future adversary actions, understand their strategic objectives, and identify vulnerabilities in their operational ecosystems that intelligence and operational teams can exploit.
What OSINT sources are most valuable for behavioral profiling of threat actors?
The most valuable OSINT sources include social media platforms where adversaries interact with communities, underground forums where they discuss techniques and tools, domain registration and infrastructure data revealing operational patterns, communication metadata showing network relationships, and linguistic analysis of their public statements or intercepted communications. Technical infrastructure including hosting choices, domain naming patterns, and tool selections also provides behavioral insight about adversary sophistication, resources, and operational security priorities.
How can smaller intelligence units conduct effective adversary profiling with limited resources?
Smaller units should prioritize profiling adversaries most relevant to their mission rather than attempting comprehensive coverage of all potential threats. Focus on depth over breadth by selecting 3 to 5 high-priority actors for detailed profiling while maintaining basic tracking of other threats. Leverage information-sharing partnerships with larger agencies to supplement limited collection capabilities, and employ AI-powered OSINT automation platforms that enable small teams to maintain profile coverage that would require much larger personnel investments using manual methods.
How often should adversary profiles be updated to remain operationally relevant?
Active high-priority threat actors warrant monthly profile reviews with continuous monitoring for significant changes in capabilities, infrastructure, or behavioral patterns. Medium-priority adversaries typically require quarterly updates unless intelligence suggests major operational shifts. Annual comprehensive reviews ensure no adversary profiles become critically outdated. However, significant events such as arrests, infrastructure disruptions, or major operations by or against the adversary should trigger immediate profile reassessment regardless of scheduled review cycles.
