Modern investigations move at network speed. Threat actors pivot across domains, social platforms, and infrastructure in hours. Meanwhile, teams still copy indicators by hand, pivot between tabs, and paste screenshots into reports. The gap widens. This is why OSINT automation is no longer optional for security operations and intelligence teams. You still need expert judgment; however, you cannot afford manual steps that slow discovery, enrichment, and collaboration.
This guide explains what to automate, how to measure impact, and where platforms like Kindi reduce toil without removing control. We focus on practical workflows for SOC analysts, threat intel leads, and incident responders who must turn open sources into decisions that hold up under pressure.
Why manual OSINT breaks at scale
Manual work creates friction at every stage. Analysts spend time retyping selectors, repeating searches, and reconciling names across formats. As sources multiply, the investigation slows, and context gets lost. Three patterns stand out.
- Volume and velocity: domains, hashtags, breach posts, and malware samples grow daily. Manual pivoting cannot keep pace.
- Variety and veracity: data arrives as screenshots, JSON, PDFs, and forum posts. Without standard enrichment, false positives multiply.
- Visibility gaps: evidence lives across registries, social platforms, dark web markets, and code repos. Context is scattered, so linkage is missed.
As a result, good leads stall and low-value tasks soak up hours. SOC teams feel this as alert fatigue and long queues. Intelligence units feel it as slow investigations and late insights. To address these gaps, you need a repeatable automation layer that assists, not replaces, investigators.
What OSINT automation really means
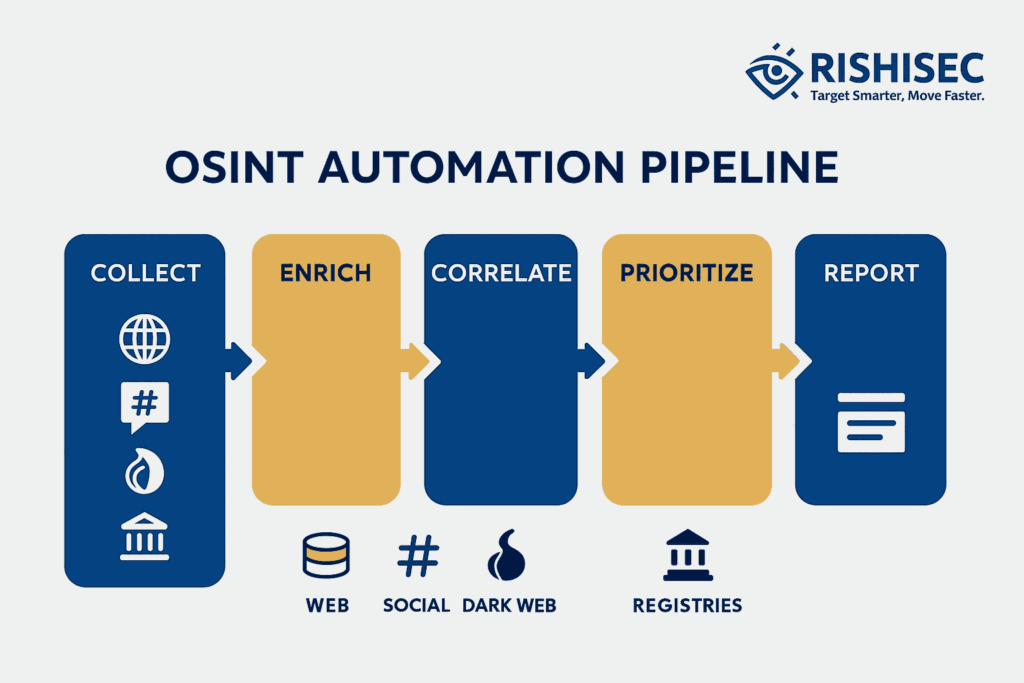
OSINT automation is not a black box. It is a set of repeatable steps that reduces toil while preserving analyst control. The aim is speed with documented rigor.
- Collection: pull data from registries, paste sites, social platforms, leak sites, and media, then normalize formats.
- Enrichment: resolve entities, expand selectors, extract metadata, and tag confidence levels.
- Correlation: link people, domains, wallets, and infrastructure with time and location context.
- Deduplication: remove repeats and near-dupes so queues stay lean.
- Prioritization: score items by relevance to active incidents or watchlists.
- Reporting: turn graphs and notes into clean briefs with sources and timestamps.
These steps free analysts to ask better questions, validate narratives, and decide what to do next. Automation handles the plumbing, analysts own the judgment.
High-value SOC and intel use cases
1. Alert enrichment and triage
When an endpoint or SIEM fires, automation can pivot to registries, passive DNS, paste sites, and social chatter. It then returns a brief, with related indicators and a confidence tag. Analysts start with context, not a blank page. See our perspective on using OSINT to prioritize alerts in SOC environments for deeper triage patterns.
2. Phishing and malware infrastructure mapping
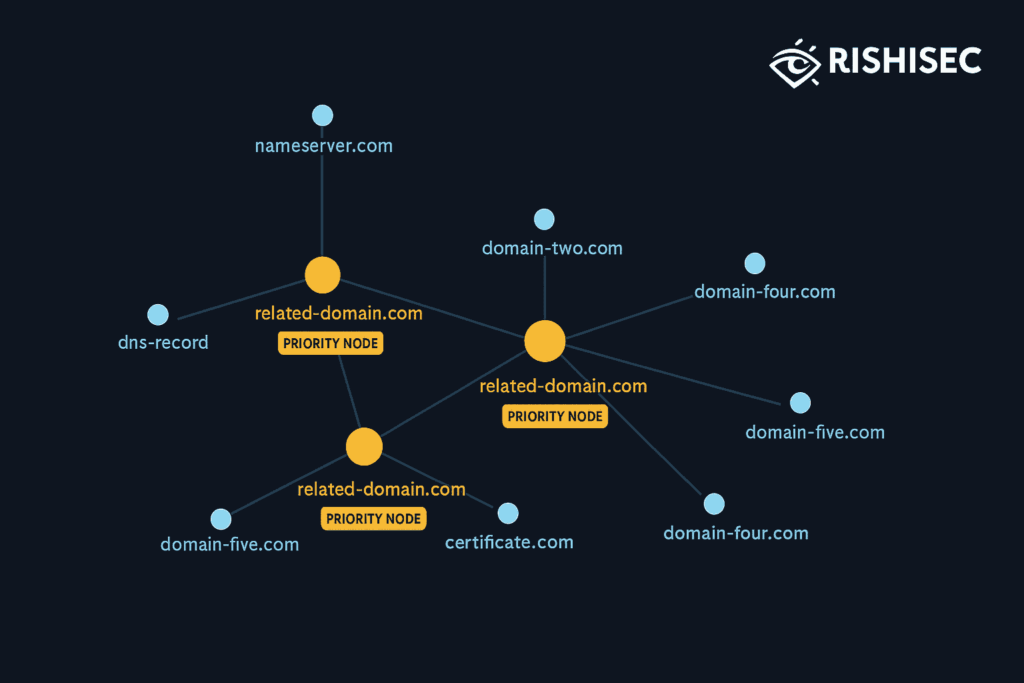
Campaigns reuse nameservers, certificates, or hosting blocks. Automated pivots reveal sibling domains and operator patterns. Link analysis then shows clusters that inform blocking and takedowns.
3. Identity, brand, and executive risk
Monitors scan marketplaces, breach posts, and copycat sites, then flag items that match protected names or assets. Analysts receive verified hits, with screenshots and archive links.
4. Ransomware and extortion monitoring
Leak sites and forums evolve fast. Automation captures changes, extracts victims and timelines, and alerts only when items match your sector or region. Summaries include mirrors and hashes for chain of custody.
5. Social signal checks during incidents
During a live event, social signals confirm reach, claims, and copies. Automated filters remove noise, then surface posts that match incident selectors. For open-source techniques on community discovery, see our Reddit OSINT guide.
How Kindi accelerates OSINT automation
Kindi is RishiSec’s AI-powered platform for automated OSINT investigations and link analysis. It reduces manual steps without removing analyst control.
- Multi-source collection: one workflow for corporate registries, sanctions, code repos, social platforms, and leak sites. Less tab switching, more consistent inputs.
- Entity and selector enrichment: expand indicators, resolve aliases, and attach metadata. Trace links between identities, domains, and infrastructure.
- Link analysis graphs: visualize networks that cross platforms and borders. See actors, assets, and time pivots in one view.
- AI summaries with citations: produce concise briefs for incidents and weekly reporting. Each fact links back to a captured source.
- Collaboration and export: share cases with role-based access, then export to PDF, CSV, or JSON for audit and response handoffs.
For a strategic layer on why context matters in tooling, read our article on integrating OSINT into threat intelligence platforms. If you shape intel products for leadership, the frameworks in OSINT strategy also help.
A practical OSINT automation workflow
Step 1: Define the question and scope
Write the question that automation must answer. List selectors, watchlists, and the decision you need to make. Keep the scope tight so outputs stay useful.
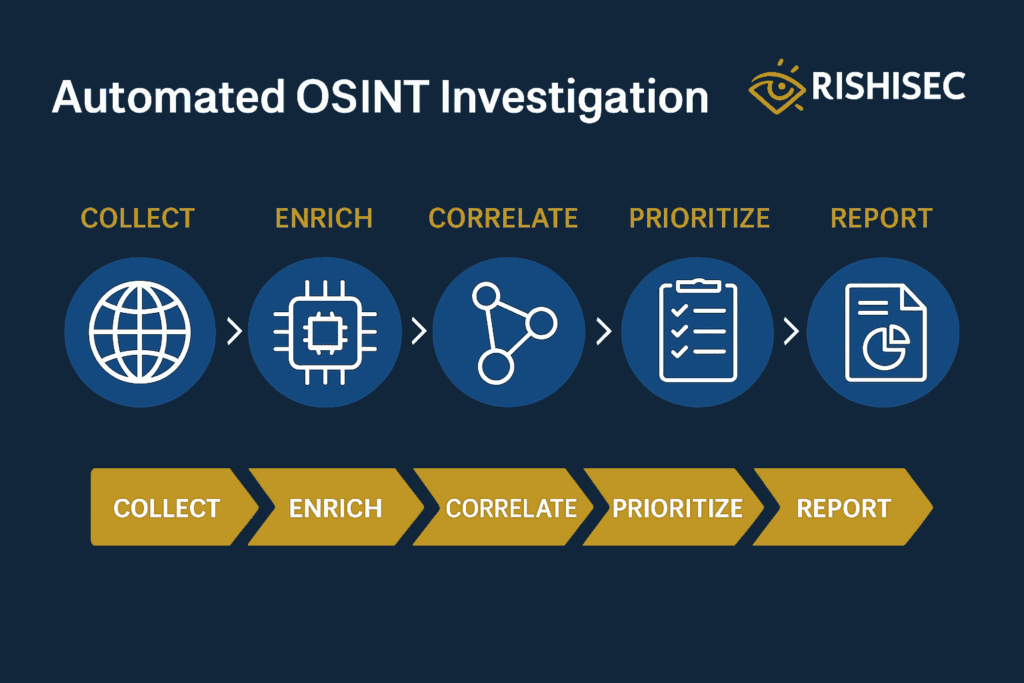
Step 2: Collect and normalize
Pull items from registries, social platforms, paste sites, and media. Convert to a common schema. Deduplicate aggressively. Store source URLs and timestamps for audit.
Step 3: Enrich and correlate
Expand domains to infrastructure. Resolve names to entities. Map relationships by time and place. Mark confidence levels so triage stays honest.
Step 4: Prioritize and route
Score items against current incidents and policy. Send high-value hits to analysts with short briefs. Park low-value items for later review.
Step 5: Visualize and brief
Turn findings into clear graphs and two-paragraph summaries. Each statement needs a citation. Export to the formats your response teams use.
Governance, ethics, and safe collection
Automation amplifies capabilities, so teams must protect people and adhere to rules. Use the Traffic Light Protocol for sharing; tag sources and sensitivity. Respect platform terms, privacy laws, and internal policy. Keep a short retention policy for volatile items and a longer archive for items used in reports. Train teams to record consent and to minimize personal data in briefs. For shared language on behaviors and techniques, see the MITRE ATT&CK knowledge base. For public advisories and guidance, see CISA.
Measuring the impact of OSINT automation
Executives want to see outcomes, not only counts. Use a small set of metrics that show speed, quality, and value.
- Speed: median time to first context, median time to triage, and mean time to detect linked assets.
- Quality: false positive rate, citation coverage, and analyst satisfaction after pilot.
- Value: alerts closed with automated context, incidents with automated linkage, and time saved per case.
Report these monthly. Pair numbers with one narrative case that shows how automation changed the outcome. Stories travel farther than spreadsheets.
30-60-90 day rollout plan
- Days 0–30: select two use cases, for example, alert enrichment and phishing cluster mapping. Instrument the pipeline and define success metrics.
- Days 31–60: integrate with SIEM, SOAR, and ticketing. Add link analysis and summaries. Run weekly reviews to trim noisy steps.
- Days 61–90: expand to ransomware leak monitoring or executive risk. Publish an internal playbook. Share a monthly win story with your leadership team.
Common pitfalls and how to avoid them
- Automating chaos: weak processes create bad outputs faster. Stabilize the workflow before you scale.
- Hidden black boxes: keep explainability. Store citations and let analysts trace every fact.
- Collector sprawl: too many feeds create noise. Start with the sources that match your sector and incidents.
- No change management: train, document, and co-design with analysts. Adoption is the real goal.
Conclusion
Manual OSINT will not keep pace with modern threats. Automation does the heavy lifting, analysts do the thinking. With a clear workflow and a platform that respects rigor, teams move from raw signals to linked evidence in minutes. That is what OSINT automation delivers. If you need to reduce triage queues, enrich alerts, and explain networks with confidence, now is the time to build the layer that helps your people focus.
See Kindi in action to automate collection, visualize links, and brief stakeholders faster. You can request a walkthrough or start a pilot with your live use cases. Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training.