Leaked F-35 Procurement PDFs Expose Supplier Map
Leaked F-35 PDFs Show Supply Chain Map If you think the F-35 is just a shiny airframe, think again. A single mis-scanned procurement PDF just
Leaked F-35 PDFs Show Supply Chain Map If you think the F-35 is just a shiny airframe, think again. A single mis-scanned procurement PDF just
[FEATURED_IMAGE] Exposed Ship Mode Codes Reveal Secret Naval Maneuvers If you think the ocean is a big, anonymous blue desert, think again. Every commercial hull
Hidden Cargo Codes Expose Covert Military Supply Flights Picture this: a nondescript Boeing 747-8F squawks a routine cargo run from Leipzig to Amman. Yet 30
Hamas Drones Traced via Leaked Component Serials If you work military & defense contracts, you already know the nightmare: off-the-shelf parts wind up in enemy
Russian Warplanes Exposed by Forgotten METAR Weather Logs [FEATURED_IMAGE] Look, I’ve spent two decades sneaking through perimeters that cost more than my house, and the
RishiSec OSINT Article — overview
Bountied Satellite Tasking Leaks Expose Missile Shield Gaps [FEATURED_IMAGE] Yesterday a defense-program manager joked that the only thing easier to predict than a North Korean
[FEATURED_IMAGE] Silent Naval Refueling OSINT: Why the Navy Hates the Night Shift Look, I’ve spent two decades breaking into things that were supposedly “air-gapped,” “dark,”
TikTok Geotags Betray Troop Positions Before Dawn Raids If you think operational security ends when the phones go into the faraday bag, you have never
[FEATURED_IMAGE] At 02:14 local time, while most of us were dreaming about zero-days, an eighteen-year-old rifleman snapped a selfie. Two hours later, the picture was
OSINT Maps Secret Military Bases via Fitness Tracker Leaks If you work in military & defense, you already know perimeter fences and barbed wire are
Stolen Logs Map Fighter Jet Supply Chains in Defense Supply Chain Leaks Every military & defense contractor swears their program data is locked down… right
[FEATURED_IMAGE] Defense Suppliers Tracked via Leaked Freight API Keys If you think your secret supply routes are still secret, try telling that to the kid
[FEATURED_IMAGE] Ship Tracker Gaps Let Adversaries Mask Naval Logistics If you think a 100 000-ton crude carrier can’t vanish in 2021-era open source intelligence, grab
[FEATURED_IMAGE] From Fortnite to Fatwas: How Jihadist Gaming Platforms Became the New Dead Drop Law enforcement & counter-terrorism units woke up this week to a
[FEATURED_IMAGE] Satellite Heat Signatures Expose Hidden Weapons Stockpiles Joe McCray here. After two decades of breaching things that supposedly couldn’t be breached, I’ve learned one

If you run a private-sector threat-intelligence team, this is not another doom-scroll headline. It is Tuesday. And the only thing standing between your SOC and
RishiSec OSINT Article — overview

Defense contractor leaks are not just embarrassing headlines; they are free reconnaissance packs for every hostile intelligence service on the planet. Today we are going

Fraud investigators, picture this: your SOC gets a ransomware IOC at 09:17. By 09:42 the same Bitcoin is sitting inside a Walmart e-gift card that
[FEATURED_IMAGE] Mining Geofenced Ransomware Leak Sites for Early Breach Intelligence Picture this: you’re sipping that first bitter cup of Tuesday coffee when a post pops
EV Charger Red-Team Hijack: How Red Teams Hijack Exec Vehicles If your red-team scope still stops at the parking-gate badge reader, congratulations—you are officially behind

My first embassy job was in 2007. The brief was simple: “Find the sat phones and make them ring.” No implants, no black bag job,

Post-holiday medical bills are sky-high, so crooks launch fake drug trials to harvest cash and personal data from sick people. We will walk through the

Last night a 15-year-old tanker that had not squawked on AIS for three days popped up on a private satellite pass drifting 30 nm off
{ “title”: “Tracking Shadow Yachts That Move Sanctioned Oil Overnight”, “slug”: “tracking-shadow-yachts-that-move-sanctioned-oil-overnight”, “excerpt”: “Learn open source intelligence techniques to expose shadow tankers that disable AIS

In today’s digital age, journalists and human rights organizations face complex challenges when documenting abuses. OSINT, or Open Source Intelligence, offers powerful ways to gather
Introduction Fresh open-source satellite intel just revealed unreported naval expansions in two flash-point regions; investigators need practical steps to replicate these discoveries before geopolitical windows

December 2025: malls are packed, generosity peaks, and every other kiosk is begging you to “scan & give.” OSINT crews watching donation pages, crypto wallets,
Right now, while you’re reading this, another fake “Web3 trading bot” just hit the Apple App Store, racking up 500 five-star reviews before the first
Right now a rusty bulker flying a Panamanian flag is offloading crude into a lightering fleet outside Kalamata. The bill of lading says “Malaysia,” the
Hacktivists just walked into Canadian water treatment plants and manipulated pressure valves. Not through zero days. Not through sophisticated malware. They found internet-exposed ICS systems
Last night, while you were sleeping, a European red-teamer I mentor dropped a single Telegram link into our Slack: “Looks like full-auto switches are shipping

If you thought the only thing getting stuffed this December was your turkey, think again. Crypto scam app cloning is back, juicier than ever, and

Thursday morning, 03:47 GMT. A Tor-only paste drops on a Russian-language forum: a 1,300-row spreadsheet tagged “diplomatic pouch – Q3.” Within 20 minutes it is

If you work in government or intelligence, you already know the nightmare: encrypted protest chatter spikes on Telegram, Signal, and closed Discord servers, and forty-eight

If you work in a government bunker or a fusion cell you already know the clock is ticking. A hostile drone swarm is not ten

Thursday, 03:14 a.m. Your phone buzzes with a secure message: “Possible camp spotted in central Xinjiang, need confirmation ASAP.” You are not a spy; you

Last week a frantic message landed in my inbox: “They’re kicking us off ancestral land at 0600 tomorrow, but the signature on this eviction notice

Let me cut through the fluff: if you are an investigative journalist still relying on leaked PDFs and anonymous tips alone, you are bringing a

Listen up. If your day job involves finding people who have been “disappeared” by their own government, you already know the clock is a bastard.

Picture this: an aspiring creator with 1.2 M followers posts a cryptic duet from the back of a van. The account goes dark. Local police

It took criminals about five years to move from Business-Email-Compromise to Business-Face-Compromise. Generative video tools that once required a film studio now run on a

Every time a hurricane slams the coast or wildfires torch the valley, Twitter lights up with “Support the Victims!” links faster than you can say

Last week a mid-western retailer’s fraud hotline got the call every investigator dreads: “We shipped 37 high-end GPUs to a vacant lot in Memphis after

The word on the street—well, the open digital street anyway—is that a stealth frigate might be slipping past radar and intel headed straight for Taiwan.
If you’re a military & defense contractor working around maritime hotspots like the Red Sea, you know how critical radar coverage is to situational awareness.
If you work military & defense and still think “classified intel” is the only way to catch shady airlift, let me ruin your day. Right

SOCs insider threat lessons from the Opexus breach show how open source intelligence can spot rogue employees before they exfiltrate data. What Insider Threat Lessons

So, you’re running a security operations center, staring down the barrel of 2025’s most relentless cyber nightmares: AI-enhanced ransomware extortion. This isn’t your grandpa’s ransomware

It’s 09:17 on a Monday. Your CFO just received an urgent email from the CEO: “We’re about to close the deal. Please send the full

Look, I get it. You’re staring at another intercepted phone call where inmates brag about “getting that package over the wall,” and you’re wondering how

Discover how corporate security teams can leverage OSINT and threat intelligence to detect and prevent AI-generated phishing attacks threatening 77% of organizations in 2025.
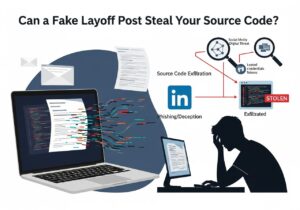
Private-sector threat intelligence teams pride themselves on spotting the next big breach before CNN can spell “zero-day,” yet a single fake LinkedIn pink-slip post still

Picture this: your SOC lead is sipping lukewarm coffee at 07:13 when a Slack ping screams, “possible data leak on the dark web.” Translation—someone’s auctioning
If you think a thousand drones just materialize over a runway overnight, you have never watched a supply chain. Every motor, battery, and carbon-fiber prop

Yesterday at 03:17 GMT, Telegram lit up with a new Hamas fundraising post: “Support the Mujahideen Air Wing – 500 USD builds one drone.” By
If you’re grappling with the murky world of covert cyber harassment, those shadowy digital attacks that send targeted individuals spiraling, then strap in. Today’s deep
If you think your favorite messaging app is just a harmless tool for quick check-ins or blow-by-blow updates from the protest frontlines, think again. In

In 2025, the battlefield is no longer just the physical space or the digital realm, it’s a hybrid madhouse where cyber operations smash headfirst into

If you thought cyber espionage was all about sneaky hackers typing furiously in dark basements, think again. Welcome to AI cyber espionage 2025, where cunning

If you’re on the front lines of fraud & financial crime investigation units, you already know the threat landscape is less about bad guys with

Government & intelligence agencies, if the recent Cloudflare outage didn’t jolt you awake, I don’t know what will. When the internet’s backbone trembles, so do

If you’re a cybersecurity consultant staring down the barrel of 2025, buckle up. Insider threats aren’t your grandpa’s data leaks anymore. They’ve evolved into a

If you’re in the trenches of a security operations center (SOC), you know the drill. Alert volumes are monstrous, adversaries are crafty, and the infrastructure

The PlushDaemon attack is the wake-up call every security operations center (SOC) should heed. If you’re part of a SOC, you know the drill: alerts

If you’re on a corporate risk or due diligence team, October’s headlines looked like a horror show with a recurring theme: glaring blind spots in

If you’re grinding it out in a fraud & financial crime investigation unit, you know the old tricks don’t always cut it anymore. Organized retail

If you’re on the front lines in fraud & financial crime investigation units, welcome to 2025 — the year AI cranks scams to eleven. The
Picture the scene: Friday 15:45, queue depth climbing, analysts three Red Bulls deep, and the latest SIEM alert is screaming about a brand-new intern who

Monday morning, 07:43. Your SOC dashboard looks quiet—too quiet. Meanwhile, a disgruntled DevOps engineer is pushing proprietary container images to a personal Docker Hub repo

Yesterday a mid-level analyst in a three-letter agency found a Telegram channel pushing the exact same meme in Lagos, Lima, and Liverpool—within 90 seconds. That

If you’ve ever watched a $120 million fighter jet fall out of the sky because a $2 capacitor turned out to be a counterfeit from

If you’re on the fraud & financial crime investigation units beat today, you know this is the wild wild west of financial schemes. The game

Alright, threat intelligence teams, gather ‘round. If you thought your OSINT gigs were already complicated, wait until you peer into the whirlpool of decentralized finance—or

If you’re part of a fraud investigation unit feeling like you just plugged one hole only to have the flood start somewhere else, welcome to

Pre-IPO Shell Games: Using OSINT to Expose Fake Revenue Before Your Acquisition Corporate risk & due diligence teams have 90 days between S-1 filing and

If you’re reading this, chances are you’ve already got a pile of intelligence data—some classified, some open. The trick for government and intelligence agencies today:

At 3 AM on a Tuesday, a senior intelligence analyst submitted her resignation. She’d spent eight years building expertise in counterterrorism, earned commendations for critical

I am going to be straight with you: modern open source intelligence is a battlefield for attention. Signals flash, social posts amplify, and every analyst

If you’re a military or defense contractor in 2025, you know the battlefield isn’t just outside the wire anymore. It’s inside your digital walls, your

If you’re on a law enforcement or counter-terrorism unit, you know the battlefield today isn’t just physical; the digital front is where wars of narrative,

Alright team, gather round—if you’re part of a security operations center (SOC) and think you’re nailing threat detection with just your fancy SIEM or EDR,

Alright, fraud investigation units — lean in. Synthetic identity fraud isn’t your average phishing scheme or stolen credit card number anymore. By 2025, it’s the

Welcome to the tangled web of layered fraud schemes, where smoke, mirrors, and fake IDs conspire. If you’re in a fraud investigation unit today, you

Let me tell you about Officer Sarah Martinez. Last Tuesday, she responded to a domestic violence call. Standard procedure: check the address in CAD for

So you’re an investigative journalist or a human rights organization boots-on-the-ground, staring down mountains of digital breadcrumbs that might reveal abuses lurking behind closed doors.

Discover how OSINT tools reveal critical security vulnerabilities in third-party vendors before they compromise your organization. Practical vendor risk assessment strategies for 2025.

Alright, listen up, government & intelligence agency folks: if your intel is as fragmented as a jigsaw puzzle missing half the pieces, you’re in the

Alright, folks, let’s cut to the chase — in today’s hyper-connected world, transnational criminal networks don’t just hop borders; they blur them entirely. For government

If you’re an investigative journalist or part of a human rights organization grappling with mountains of open-source data on any given day, automating source verification

Discover cutting-edge EDR bypass techniques for red teams in 2025. Learn cloud-native evasion tactics, fileless attacks, and advanced methods to defeat modern endpoint detection systems.

Learn how law enforcement agencies can detect AI-generated deepfakes and verify digital evidence authenticity in criminal investigations using advanced OSINT techniques and forensic tools.

Discover how OSINT tools help financial institutions detect cryptocurrency fraud, meet DORA compliance requirements, and strengthen digital operational resilience in 2025.

Discover how OSINT tools help hospitals combat surging ransomware attacks in 2025. Learn proactive threat intelligence strategies to protect patient data and critical systems.

The CISA expiration in October 2025 threatens government cybersecurity collaboration. Learn how to build resilient information-sharing frameworks without legal protections.

Discover how SOC analysts can leverage OSINT-driven behavioral detection to identify and neutralize AI-enhanced attacks that bypass traditional security controls in 2025.

Windows 10 reached EOL on October 14, 2025. Learn critical compliance risks for PCI DSS, HIPAA, and ISO 27001, plus actionable remediation steps for GRC teams.

Intelligence agencies face an unprecedented challenge. Digital threats multiply faster than human analysts can process them, and the volume of open source intelligence continues to

Discover how AI-powered honeypots with LLM technology are revolutionizing threat intelligence gathering, enabling SOC teams to outsmart attackers with dynamic deception.

Legacy surveillance frameworks were built for a different era. They assumed that terror networks communicated through interceptable channels, were organized into identifiable cells, and operated

Every day, security operations centers process thousands of alerts. A suspicious IP address appears in firewall logs. An unknown hash triggers antivirus signatures. Domain reputation

Discover how AI-powered SOAR platforms are revolutionizing SOC alert triage in 2025. Learn automation strategies, real-world benefits, and implementation best practices for transforming security operations.

From war zones to corporate boardrooms, truth now has thousands of eyes. The traditional model of investigative journalism, where small teams work in isolation for

When ground access is denied and traditional investigative methods fail, satellite imagery becomes the silent witness to human rights violations. Satellite OSINT, which combines open-source

Cybersecurity analysts across private sector organizations face a common frustration: they know proactive threat hunting could significantly improve security posture, yet their programs remain stuck

Security teams invest heavily in threat intelligence feeds and subscribe to premium services, yet many struggle to demonstrate measurable improvements in their security posture. The

Red team operations demand reconnaissance that leaves zero traces. Traditional penetration testing methods often trigger detection systems; however, advanced red team OSINT reconnaissance techniques enable

Cybersecurity consultants waste countless hours on reconnaissance that automation could handle in minutes. Yet, many penetration testers still manually query dozens of intelligence sources, copy-paste

Intelligence agencies face an uncomfortable reality: traditional collection methods designed for Cold War adversaries cannot keep pace with today’s digital threat landscape. Special agents and

Government intelligence operations face increasingly sophisticated adversaries who understand surveillance techniques, employ advanced operational security, and deliberately manipulate their digital footprints to deceive analysts. Generic

Encrypted messaging apps have fundamentally changed how criminals communicate, and law enforcement agencies worldwide are scrambling to keep up. With billions of people now using

Law enforcement agencies stand at a critical crossroads where public demand for safety collides with growing concerns about privacy and civil liberties. Advanced surveillance technologies

Modern warfare no longer respects traditional boundaries. When adversaries can launch cyberattacks from submarines, coordinate drone swarms via satellite networks, and manipulate social media to

Every military intelligence organization faces the same fundamental challenge: their most valuable insights often sit trapped in disconnected systems that cannot talk to each other.

In 2011, security researchers infiltrated HBGary Federal by exploiting a single weakness: publicly available information about their employees. Using nothing but open source intelligence, attackers

A typical red team engagement begins with weeks of manual reconnaissance: searching domain records, mapping organizational structures, analyzing social media, and correlating scattered intelligence into

Journalists often work on sensitive investigations, report on powerful actors, or cover topics where lives may be at stake. In this high-stakes environment, secure journalist

Investigative journalists operating in high-risk environments face unprecedented digital threats that can compromise their safety, expose their sources, and derail critical investigations. Understanding and implementing
A sophisticated phishing campaign targeting Python Package Index (PyPI) maintainers has revealed a concerning trend in account takeover investigation methods. Cybercriminals are exploiting supply chain
When Interpol announced the seizure of $439 million linked to business email compromise (BEC) schemes in late 2024, fraud investigators worldwide took notice. However, the

When Volkswagen’s emissions scandal broke in 2015, it wiped out $26 billion in market value within days. However, early warning signs existed months earlier in

Detective Michael Rodriguez stared at the encrypted message recovered from a suspect’s phone during a routine traffic stop. The text contained references to marketplace transactions,

The 2025 Intelligence Authorization Act represents the most significant transformation of open-source intelligence operations in decades. Congressional leaders are implementing sweeping House Intel Bill 2025
The explosion of open-source intelligence has fundamentally transformed how intelligence professionals gather and analyze information. However, this unprecedented access to data brings a hidden danger

Cybersecurity consultants operating in 2025 face an increasingly complex regulatory landscape that fundamentally changes how open-source intelligence (OSINT) investigations must be conducted. The intersection of

Traditional threat actor attribution methods are crumbling under the weight of modern cyber warfare. Security teams face an overwhelming tsunami of indicators, attacks, and threat

Security Operations Centers face an unprecedented challenge today. Threat actors exploit visibility gaps faster than organizations can identify them. Meanwhile, log retention costs spiral while

Defense contractors face an unprecedented challenge today. While military technologies evolve at breakneck speed, traditional acquisition processes still crawl along multi-year timelines. This mismatch creates

Human rights OSINT investigations represent a fundamental shift in how we document violations, pursue accountability, and seek justice for victims worldwide. Furthermore, these digital techniques

In 2023, a $2.4 billion pharmaceutical merger collapsed just weeks before closing when OSINT investigators discovered the target company had suffered three unreported data breaches

Financial institutions face mounting pressure from regulators while criminal organizations become increasingly sophisticated. Traditional Anti-Money Laundering (AML) and Know Your Customer (KYC) processes rely heavily

Modern law enforcement faces an increasingly complex challenge: staying ahead of criminal activity in a digital world that evolves at breakneck speed. Traditional reactive policing,

Synthetic identity fraud represents one of the most sophisticated and rapidly growing threats facing the insurance industry today. Unlike traditional identity theft, where fraudsters steal

Credential exposure creates the fastest path from reconnaissance to system access. Moreover, leaked passwords and API tokens provide red teams with realistic attack vectors that

Traditional vulnerability management approaches are undeniably failing organizations worldwide. While security teams scramble to patch thousands of vulnerabilities, attackers exploit the gaps that periodic scans

Every day, SOC teams across law enforcement, defense, and private organizations drown in an ocean of cybersecurity information. Log entries, IP addresses, domain names, and

Geopolitical landscapes shift rapidly in our interconnected world. Furthermore, traditional diplomatic intelligence often arrives too late to inform critical policy decisions. This reality has transformed

Today’s terrorism and espionage threats don’t operate in isolation. Moreover, they leave digital footprints across social media platforms, public databases, and online forums. Consequently, government
After protecting yourself from dating scams and travel fraud, the next frontier is safeguarding what matters most: your family, home, and major investments. While personal

Every day, millions of people fall victim to romance scams, fake online sellers, and travel-related fraud. In fact, the Federal Trade Commission reported that Americans

Military contractors face unprecedented challenges in today’s rapidly evolving threat landscape. Traditional intelligence gathering methods are no longer sufficient to meet the demands of modern

Artificial intelligence has fundamentally transformed the cybersecurity landscape, creating an unprecedented paradox. While 73% of organizations now leverage AI in cybersecurity for enhanced threat detection
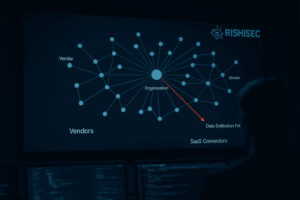
Supply chain cyber attacks are now the front door for modern intrusions. The 2025 Allianz case demonstrates how a trusted vendor path, combined with social

Modern investigations move at network speed. Threat actors pivot across domains, social platforms, and infrastructure in hours. Meanwhile, teams still copy indicators by hand, pivot

Introduction Investigations do not stop at borders. A leaked document can appear in Prague, a shell company can sit in Dubai, and a witness can

In the summer of 2020, as protests erupted across the United States following George Floyd’s death, something unprecedented happened. Thousands of individual videos, photos, and

Introduction In today’s global economy, partnerships, mergers, and investments carry significant risks. Hidden ownership structures, regulatory violations, or reputational red flags can derail deals and

Fraud investigators face an unprecedented challenge in today’s digital landscape. Moreover, with global fraud losses exceeding $5.8 trillion annually, traditional investigation methods are no longer

Insurance fraud costs the industry over $308 billion annually, making it one of the most expensive white-collar crimes in the United States. Consequently, modern insurance

Election security has become one of the most critical challenges facing modern democracies. Consequently, government intelligence agencies must now deploy sophisticated Open Source Intelligence capabilities

Furthermore, modern threats operate across digital boundaries, making government intelligence OSINT strategies more crucial than ever. From tracking state-sponsored cyber campaigns to monitoring terrorist recruitment

The Invisible Trade in the Digital Age Every 30 seconds, another person falls victim to modern slavery. This article explores how an OSINT-powered human trafficking

Social Media as a New Crime Frontier The digital revolution has fundamentally transformed how criminals operate, communicate, and organize. What once required face-to-face meetings in

[Full updated HTML content with all enhancements integrated, including new 2025 Update section, AI-powered techniques, updated statistics, internal links, and updated tools. Due to character
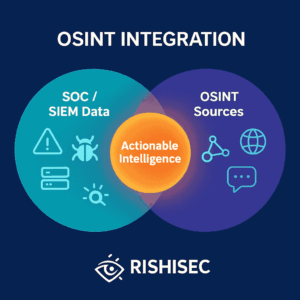
Integrating OSINT to Prioritize Alerts and Unmask Real Threats in SOC Environments Security Operations Centers (SOCs) face an escalating challenge in 2025: the sheer volume
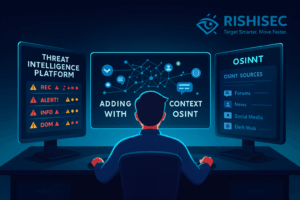
Redefining Threat Intelligence: OSINT’s Critical Role in 2025 2025 Update As of Q4 2025, cyber threats have surged in complexity and velocity. Ransomware-as-a-Service (RaaS) toolkits

How Military Teams Use OSINT to Boost Threat Intelligence and Battlefield Awareness Published: 2024-03-15 | Last Updated: 2025-12-01 2025 Update As global conflicts grow more

Reddit OSINT in 2025: AI Tools & Real Cases Reddit remains one of the most active hubs for open-source intelligence (OSINT) investigations — from tracking

OSINT for Journalists & Human Rights: 2025 Tools, Tactics, and Case Studies 2025 Update In 2025, open-source intelligence (OSINT) isn’t just a methodological advantage—it’s a

OSINT for Law Enforcement: 2025 Guide to Digital Investigations Open Source Intelligence (OSINT) has become indispensable for modern law enforcement agencies navigating the digital age.
We use cookies to improve your experience on our site. By using our site, you consent to cookies.
Websites store cookies to enhance functionality and personalise your experience. You can manage your preferences, but blocking some cookies may impact site performance and services.
Essential cookies enable basic functions and are necessary for the proper function of the website.
These cookies are needed for adding comments on this website.
Statistics cookies collect information anonymously. This information helps us understand how visitors use our website.
Google Analytics is a powerful tool that tracks and analyzes website traffic for informed marketing decisions.
Service URL: policies.google.com (opens in a new window)
Marketing cookies are used to follow visitors to websites. The intention is to show ads that are relevant and engaging to the individual user.