When Interpol announced the seizure of $439 million linked to business email compromise (BEC) schemes in late 2024, fraud investigators worldwide took notice. However, the operation revealed something more significant than the dollar amount. It exposed sophisticated red flags and mule typologies that fraud investigation units can no longer afford to overlook.
Moreover, this coordinated takedown demonstrates how traditional AML triggers are evolving. Consequently, fraud investigators must adapt their detection methods to keep pace with increasingly complex schemes targeting both corporate executives and insurance claim processors.
The financial impact extends beyond direct losses. Furthermore, these schemes create cascading effects across multiple industries, making early detection absolutely critical for fraud analysts working in today’s interconnected economy.
Understanding the BEC Kill Chain: From Email Spoof to Cryptocurrency Cash-Out
Business email compromise attacks follow a predictable pattern that fraud investigators can exploit for detection. Initially, attackers conduct extensive reconnaissance using open source intelligence (OSINT) techniques to identify high-value targets within organizations.
The typical kill chain progresses through several stages. First, cybercriminals create convincing email spoofs or compromise legitimate accounts through phishing campaigns. Next, they initiate fraudulent wire transfers or payment redirections to mule accounts. Subsequently, funds undergo rapid layering through multiple financial institutions before being converted to cryptocurrency or withdrawn as cash.
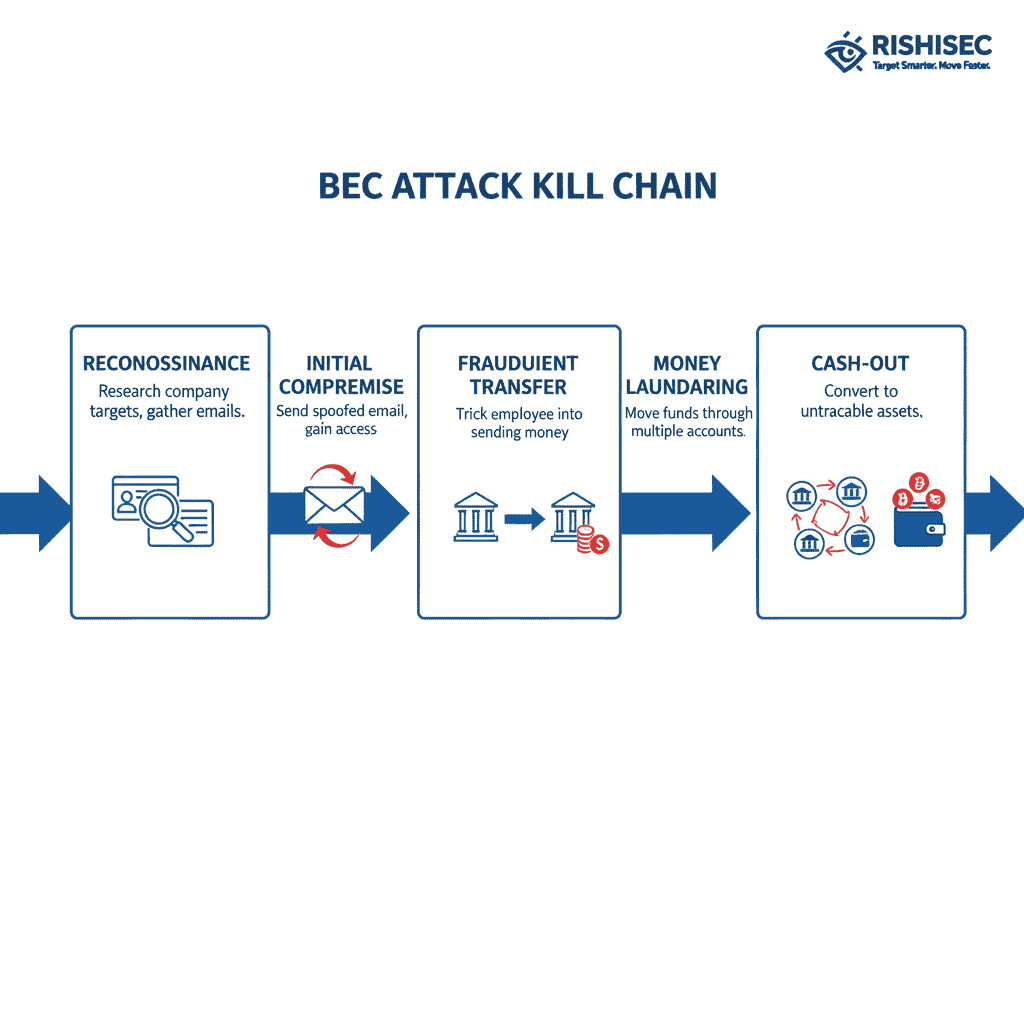
Evidence collection during investigations typically reveals several key artifacts. Domain registration records often show recently created domains with privacy protection services. Additionally, phone logs from vishing campaigns frequently contain VOIP numbers registered to fictitious identities. Meanwhile, transaction records demonstrate characteristic hopping patterns across multiple jurisdictions within 72 hours of initial compromise.
OSINT fraud investigation techniques can help identify these patterns early in the attack lifecycle, potentially preventing significant losses.
Email Infrastructure Red Flags
Technical indicators provide the strongest signals for fraud detection systems. Domain age analysis reveals that 87% of BEC domains are less than 60 days old at the time of attack. Similarly, DMARC policy absence creates opportunities for email spoofing that attackers consistently exploit.
DNS records often contain telltale signs of malicious intent. For instance, look-alike MX records frequently point to free email services rather than legitimate corporate mail servers. Additionally, SSL certificate analysis shows patterns of bulk certificate generation using automated tools rather than established certificate authorities.
Critical Business Email Compromise Red Flags for Fraud Investigation Units
Fraud investigators must recognize specific patterns that distinguish BEC attempts from legitimate business communications. Beneficiary mismatches represent the most common red flag, occurring when payment instructions suddenly change for established vendor relationships without proper verification protocols.
Geographic indicators provide additional detection opportunities. New payment corridors to previously unused jurisdictions should trigger immediate scrutiny. Furthermore, payment timing anomalies, particularly requests sent during off-hours or weekends, warrant enhanced due diligence procedures.
Behavioral Analysis Indicators
| Red Flag Category | Specific Indicator | Detection Method | Risk Score |
|---|---|---|---|
| Communication Pattern | Urgent payment requests with unusual language patterns | Natural language processing analysis | High |
| Technical Infrastructure | Recently registered domains with privacy protection | WHOIS analysis and domain age verification | Critical |
| Financial Patterns | Payment amounts just below reporting thresholds | Transaction amount clustering analysis | Medium |
| Geographic Anomalies | New beneficiary locations in high-risk jurisdictions | Geolocation and sanctions screening | High |
Language analysis reveals additional detection opportunities. Specifically, subtle changes in writing style, unusual greetings, or uncharacteristic urgency levels often indicate compromise. Meanwhile, metadata analysis of email headers can reveal routing inconsistencies that expose fraudulent origins.
Money Mule Typologies and OSINT Detection Strategies
Understanding mule recruitment patterns enables proactive fraud prevention. College students represent the largest demographic targeted by mule recruiters, primarily through social media platforms and campus job boards. Additionally, gig economy workers seeking supplemental income frequently fall victim to “easy money” schemes advertised through legitimate-appearing job postings.
OSINT techniques can identify recruitment campaigns before they produce active mules. Telegram channels frequently advertise money mule opportunities using coded language and promises of cryptocurrency payments. Similarly, LinkedIn job postings for “payment processing” or “financial coordination” roles often mask mule recruitment efforts.
Social media monitoring reveals recruitment patterns across multiple platforms. Job-seeking groups on Facebook and Reddit frequently contain mule recruitment posts disguised as legitimate employment opportunities. Furthermore, sudden increases in account activity following periods of dormancy often indicate successful mule recruitment.
Financial behaviour analysis confirms mule activity. Account balance spikes followed by rapid outbound transfers within 24-48 hours demonstrate classic mule behavior patterns. Additionally, multiple small incoming transfers from different sources followed by single large outbound transfers indicate mule account usage.
Advanced OSINT Mule Detection Techniques
Sophisticated investigators utilise multiple OSINT sources for identifying mules. Phone number analysis reveals connections between recruitment advertisements and active mule accounts through shared contact information. Similarly, email address variations often link multiple mule accounts operated by a single individual.
Cross-platform correlation enhances detection accuracy. When suspicious job postings appear simultaneously across multiple platforms with identical contact information, the likelihood of mule recruitment increases significantly. Moreover, OSINT insurance fraud detection methods can identify patterns that connect BEC schemes to fraudulent insurance claims.
Business Email Compromise Red Flags for Insurance Fraud Managers
Insurance fraud managers face unique challenges when evaluating BEC-related claims. Coverage determinations require careful analysis of policy language regarding social engineering losses versus traditional fraud exclusions. Consequently, detailed investigation protocols help distinguish covered losses from excluded criminal activities.
Claims handling procedures must account for BEC-specific evidence requirements. Email header analysis, domain registration records, and financial transaction timelines provide crucial documentation for coverage decisions. Additionally, third-party validation of claimed security measures helps verify policyholder compliance with cybersecurity requirements.
SIU Referral Triggers for BEC Claims
- Multiple BEC claims from single policyholder within a 12-month period
- Claimed losses immediately following cybersecurity policy changes
- Beneficiary accounts linked to previously flagged mule networks
- Inconsistent technical details in loss documentation
- Delayed reporting beyond reasonable discovery periods
Pattern recognition across claim portfolios reveals potentially fraudulent schemes. When multiple policyholders report similar BEC scenarios with identical technical indicators, coordinated fraud becomes likely. Furthermore, geographic clustering of claims often indicates organized criminal activity rather than random targeting.
Detection Rules and Analytics for Fraud Analysts
Effective fraud detection requires automated rules that balance sensitivity with specificity. The following pseudocode demonstrates key detection logic for business email compromise red flags:
Rule 1: Domain Age and Email Routing Analysis
IF domain_age < 60_days AND sender_mx_records != recipient_organization_mx AND urgency_keywords > 2 THEN flag_high_risk
Rule 2: Payment Pattern Anomaly Detection
IF new_beneficiary_country AND payment_amount > historical_average * 3 AND request_timestamp BETWEEN 18:00-06:00 THEN trigger_manual_review
Rule 3: Communication Behavioral Analysis
IF language_similarity_score < 0.7 AND contains_payment_urgency AND lacks_standard_verification_protocols THEN escalate_investigation
Key performance indicators should focus on actionable metrics rather than vanity numbers. Detection to action time represents the most critical measurement, with industry benchmarks targeting sub-one-hour response for high-risk alerts. Similarly, false positive rates should remain below 5% to maintain investigator confidence in automated systems.
Advanced analytics platforms, such as Kindi, enable fraud analysts to automatically correlate multiple data sources. This OSINT automation platform accelerates investigation timelines while improving link analysis between seemingly unrelated fraud indicators, making it essential for modern fraud investigation units.
Machine Learning Enhancement Strategies
Machine learning models improve detection accuracy over time through continuous feedback loops. Feature engineering should incorporate email metadata, financial transaction patterns, and OSINT-derived risk indicators. Additionally, ensemble methods combining multiple detection approaches typically outperform single-algorithm solutions.
The quality of training data directly impacts model performance. Consequently, maintaining accurate labels for confirmed BEC cases versus false positives enables continuous model improvement. Furthermore, regular model retraining accounts for evolving attack techniques and new red flag patterns.
Evidence Collection and Law Enforcement Coordination
Successful prosecutions require comprehensive evidence packages that meet legal standards for admissibility. Digital forensics procedures must preserve email headers, routing information, and timestamp data while maintaining chain of custody requirements. Additionally, financial transaction records must be correlated with communication timelines to establish causation.
Critical IOC Documentation Checklist
- Domain Infrastructure: Registration records, DNS history, SSL certificates, hosting providers
- Email Evidence: Complete headers, routing paths, authentication results, content analysis
- Financial Trails: Account numbers, transaction IDs, correspondent banking details, beneficiary information
- Network Indicators: IP addresses, user agents, device fingerprints, geolocation data
- Cryptocurrency Traces: Wallet addresses, transaction hashes, exchange identifiers, mixing service usage
Law enforcement agencies require specific documentation formats to facilitate effective investigations. Standardized reporting templates ensure consistent information collection across different fraud cases. Meanwhile, law enforcement OSINT guides provide frameworks for evidence collection that meet prosecutorial standards.
International coordination becomes essential when BEC schemes cross jurisdictional boundaries. Mutual Legal Assistance Treaty (MLAT) requests require detailed evidence packages with transparent chain of custody documentation. Furthermore, real-time coordination with foreign financial intelligence units can prevent asset dissipation during ongoing investigations.
Future-Proofing Business Email Compromise Red Flags Detection
The BEC threat landscape continues evolving rapidly, requiring adaptive detection strategies. Artificial intelligence enhancement of social engineering attacks presents new challenges for traditional email security measures. Consequently, fraud investigators must anticipate next-generation threats while strengthening current detection capabilities.
Integration across security tools becomes increasingly important for comprehensive protection. SIEM platforms, email security gateways, and fraud management systems should share threat intelligence to provide holistic visibility. Additionally, threat hunting capabilities enable proactive identification of sophisticated attacks that bypass automated detection systems.
Emerging technologies offer new detection opportunities alongside fresh challenges. Blockchain analysis tools provide enhanced cryptocurrency tracking capabilities for BEC investigations. However, privacy-enhancing technologies and decentralized finance protocols create new blind spots that require innovative investigation approaches.
Industry collaboration remains essential for staying ahead of evolving threats. Information sharing initiatives enable faster identification of new attack patterns and red flag indicators. Furthermore, public-private partnerships provide access to threat intelligence that individual organizations cannot generate independently.
Conclusion: The $439M Lesson for Fraud Investigation Units
Interpol’s massive BEC seizure represents more than a successful law enforcement operation. It demonstrates the critical importance of recognizing and acting on business email compromise red flags before losses occur. Fraud investigation units that implement comprehensive OSINT-based detection strategies will significantly improve their prevention and recovery rates.
The sophisticated mule networks and technical infrastructure revealed in this operation show that traditional fraud detection methods are insufficient against modern BEC schemes. Consequently, fraud investigators must embrace advanced OSINT techniques and automated analysis tools to maintain effectiveness against evolving threats.
Success requires commitment to continuous improvement and adaptation. As criminals refine their techniques, fraud investigation professionals must enhance their detection capabilities accordingly. The organizations that invest in comprehensive BEC red flag detection today will be best positioned to protect against tomorrow’s even more sophisticated schemes.
Want to strengthen your OSINT skills and fraud detection capabilities? Check out our OSINT courses for practical, hands-on training that prepares you for real-world BEC investigations.
Ready to enhance your fraud investigation capabilities with AI-powered OSINT automation? Try Kindi today and discover how automated link analysis and threat correlation can accelerate your BEC detection and investigation processes.
Frequently Asked Questions
What are the most common business email compromise red flags fraud investigators should watch for?
The most critical red flags include beneficiary payment changes without proper verification, newly registered domains (less than 60 days old), urgent payment requests made outside of regular business hours, geographic payment anomalies to new jurisdictions, and changes in communication patterns indicating potential account compromise.
How can OSINT techniques help detect BEC schemes before financial losses occur?
OSINT techniques enable proactive detection through domain analysis, social media monitoring of mule recruitment, email infrastructure investigation, cryptocurrency wallet tracking, and correlation of threat indicators across multiple data sources to identify attack campaigns in progress.
What evidence should fraud investigators collect for successful BEC prosecutions?
Critical evidence includes complete email headers with routing information, domain registration records, financial transaction details with timestamps, IP addresses and device fingerprints, cryptocurrency wallet addresses and transaction hashes, and documentation of communication timelines showing attack progression.
How do insurance fraud managers evaluate BEC-related claims for coverage decisions?
Insurance fraud managers must analyse policy language regarding social engineering coverage, verify claimed security measures were in place, document the attack methodology and timeline, assess policyholder compliance with cybersecurity requirements, and investigate whether proper verification procedures were followed before authorising payments.
What automated detection rules are most effective in identifying BEC attempts?
Effective detection rules combine domain age analysis (flagging domains under 60 days), payment pattern anomalies (new beneficiaries or unusual amounts), communication behavioural analysis (language pattern changes and urgency indicators), timing analysis (off-hours requests), and geographic risk assessment (payments to high-risk jurisdictions).