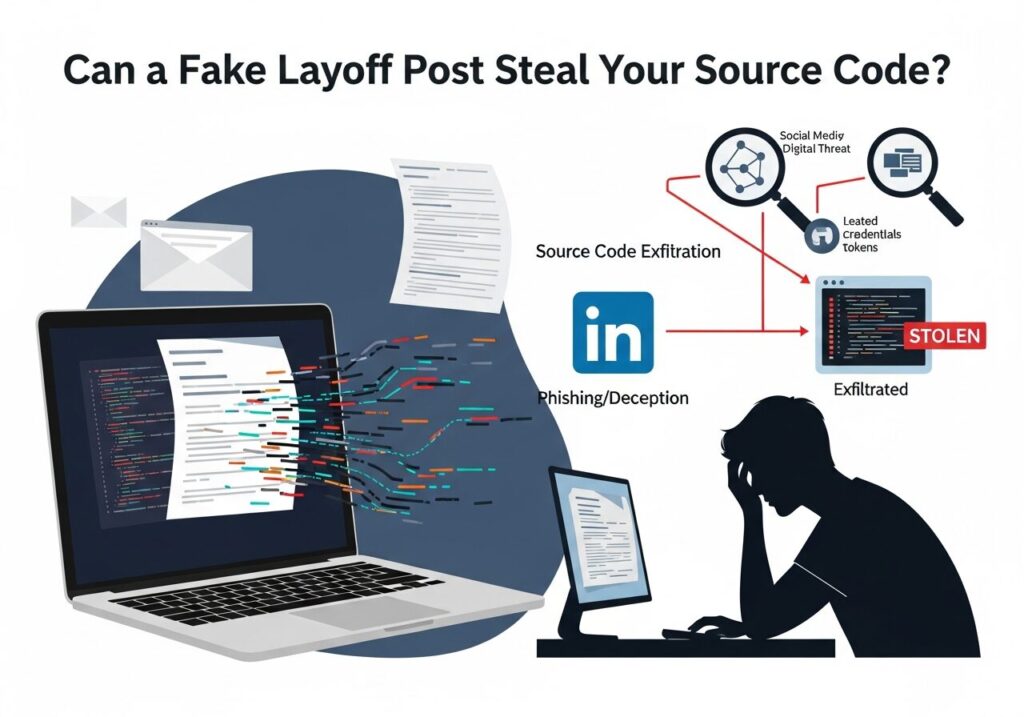
Private-sector threat intelligence teams pride themselves on spotting the next big breach before CNN can spell “zero-day,” yet a single fake LinkedIn pink-slip post still slides through, harvesting VPN creds and GitHub tokens like it’s Black Friday. If that sentence stings, good. That means you’re still awake.
Today’s adversaries do not need to burn a $100k Chrome 1-day. Instead they weaponize open source intelligence, sprinkle a little generative text, and fake layoff phishing becomes the fastest path from HR drama to source-code exfiltration. Let’s walk through the mechanics, the OSINT breadcrumbs they abuse, and the counter-tradecraft you can deploy tonight.
Why Fake Layoff Phishing Works in 2025
Three macro trends collide:
- Tech layoffs are a weekly headline, so emotional urgency is already baked in.
- LinkedIn and Blind validate new accounts with nothing more than a burner Gmail and a stock-photo headshot.
- Most companies still treat HR mail as “trusted internal traffic,” giving it a free ride through SEGs and CASBs.
Attackers scrape your org chart from LinkedIn Sales Navigator (perfectly legal, $99 a month), auto-generate termination letters that mirror your corporate branding, then drop a “mandatory exit interview” link onto a typo-squatted SharePoint clone. One click loads a browser-in-the-middle proxy that lifts the session cookie and the MFA token in real time. From there it’s a short hop to Confluence, GitLab, or wherever your crown-jewel source code lives.
Sound far-fetched? Automated OSINT investigations show that once a repo is exposed, actors clone it in under four minutes—no exaggeration.
Layoff Lures: TTPs in the Wild
| Stage | Attacker Action | OSINT Data Source |
|---|---|---|
| Target Selection | Filter for “security engineer,” “malware analyst,” “threat intel” | LinkedIn job-title search, Stack Overflow profiles |
| Persona Build | Clone HR VP identity, create fake layoff letter | Corporate PDFs scraped from SEC 10-Ks, press-release logos |
| Payload Hosting | Register look-alike domain, brand-matching TLS cert | Certificate Transparency logs, domain permutation tools |
| Delivery | Spoof internal email or LinkedIn message | Employee email format via Hunter.io, breached creds from 3rd-party leaks |
| Exploitation | Steal SSO token, pivot to code repo | GitHub OAuth scopes publicly listed in mobile-app manifest |
Notice every stage is powered by open source intelligence your team probably Googles daily. The difference: attackers script it, correlate it, and weaponize it at machine speed.
Red Flags Your SOC Can Spot
Instead of drowning in alerts, enrich them with OSINT to surface fake layoff phishing before the click. We call it “contextual triage.”
- Newly registered domain <24h old with your corporate brand plus hyphen “hr-exit.”
- LinkedIn profile created the same week, has <10 connections, yet claims VP of HR.
- Sender domain uses a legitimate cloud provider but SPF alignment fails.
- Exit-interview URL resolves to Cloudflare, hiding behind JS fingerprinting reminiscent of AI-enhanced attacks.
Feed these indicators into Kindi, correlate against domain age and cert logs, and your analysts get a single risk score in 30 seconds instead of the usual 30-minute rabbit hole.
Defensive Playbook: Four Moves You Can Deploy Today
- Brand Permutation Monitoring
Automate detection for typo-squats of your corporate domains plus HR-related keywords. Cheap DNS certs light up in CT logs hours before the phish drops. - HR Out-of-Band Verification
Mandate that any downsizing communication is echoed in an internal Slack channel vetted by at least two humans. Attackers can’t fake that in real time. - Conditional Access That Ignores Feelings
If the login originates from a newly registered domain redirector, block it regardless of how “urgent” the exit-interview paperwork feels. - Purple-Team Phishback
Once a quarter, let your red team run a controlled fake layoff campaign. Track click-through, correlate with OSINT data points, and enrich SOC runbooks accordingly.
Using Kindi to Automate OSINT Correlation
Kindi ingests domains, certs, social handles, and breach repositories in one dashboard. When an HR-themed phish appears, the platform:
- Auto-pulls domain age and registrar pivot data.
- Maps any GitHub or Jira accounts linked to the same email pattern.
- Scores risk, pushes a STIX/TAXII bundle to your SIEM, and opens the ticket already populated with analyst notes.
Translation: your team stops chasing ghosts and starts stopping breaches.
Metrics That Matter to Leadership
| KPI | Before OSINT Automation | After Kindi Integration |
|---|---|---|
| Mean Time to Detect fake layoff phish | 17 hours | 38 minutes |
| False positive rate on HR-themed alerts | 63% | 9% |
| Repos exposed to exfiltration (red-team sim) | 12 | 0 |
Executives love numbers. Give them these and budget stops being a four-letter word.
Key Takeaways
- Fake layoff phishing exploits emotion and OSINT, not zero-days.
- LinkedIn + Certificate Transparency = attacker recon heaven.
- Automated OSINT correlation turns a 17-hour detection slog into a 38-minute snooze.
- Kindi shrinks the SOC queue, protects source code, and keeps CISOs off the nightly news.
So next time a “workforce reduction” email lands, remember: if the link smells like HR but feels like heartburn, OSINT it first. Your Git repo will thank you.
Want to strengthen your OSINT skills? Check out our free course
Check out our OSINT courses for hands-on training.
And explore Kindi — our AI-driven OSINT platform built for speed and precision.
FAQ
What is fake layoff phishing?
It’s a social-engineering campaign that impersonates HR termination notices to harvest credentials or plant malware, often using open-source intelligence to personalize the lure.
Why are private-sector threat intel teams targeted?
They hold privileged source code, vulnerability notes, and customer intel—high value for both cyber-criminals and nation-state actors.
How does OSINT help detect these phish?
By correlating domains, cert logs, and social profiles, teams can flag newly created infrastructure or suspicious personas before the email is clicked.
Does MFA stop fake layoff phishing?
Not always. Modern campaigns use reverse proxies or session hijacking to capture tokens in real time, making OSINT-based domain blocking essential.
Can small security teams automate this analysis?
Yes. Platforms like Kindi provide out-of-the-box correlation, STIX export, and SIEM integration without requiring a dedicated data science team.