The cybersecurity landscape has entered a new era where artificial intelligence isn’t just a defensive tool—it’s become the weapon of choice for sophisticated threat actors. In October 2025, a staggering 77% of CISOs identify AI-generated phishing attacks as their primary emerging threat, while email malware has surged 39.5% quarter-over-quarter. Traditional email security measures are struggling to keep pace with these hyper-realistic, contextually aware attacks that can bypass conventional detection systems.
For corporate security teams and CISOs, the challenge is clear: how do you defend against threats that evolve faster than your security protocols? The answer lies in combining Open Source Intelligence (OSINT) with advanced threat intelligence to create a proactive, adaptive defense strategy. This comprehensive guide reveals how enterprise security leaders can leverage OSINT methodologies to identify, analyze, and neutralize AI-generated phishing campaigns before they compromise your organization.
Understanding the AI-Generated Phishing Threat Landscape
The Evolution of Phishing in the AI Era
AI-generated phishing represents a quantum leap from traditional phishing campaigns. Unlike mass-distributed emails with obvious grammatical errors and generic content, AI-powered attacks leverage large language models to create highly personalized, contextually relevant messages that mirror legitimate business communications with alarming accuracy.
These sophisticated attacks analyze publicly available information about your organization, executives, and employees to craft convincing scenarios. They can:
- Replicate writing styles of specific executives or departments
- Reference recent company events or projects found through OSINT
- Adapt messaging based on the target’s role and responsibilities
- Generate convincing fake documents and visual assets
- Automate multi-stage social engineering campaigns at scale
The financial impact is severe—75% of organizations reported financial damage from cyberattacks in the past year, with phishing serving as the primary entry vector for many successful breaches.
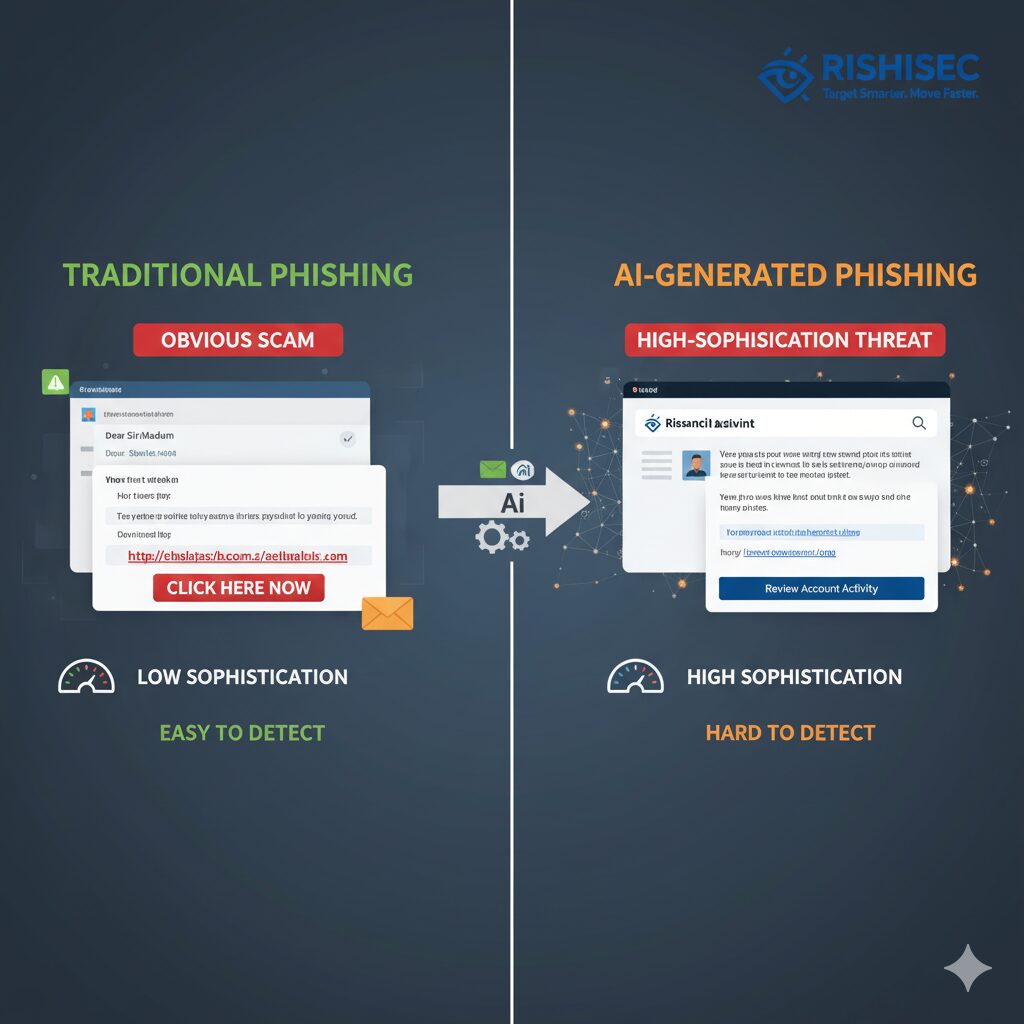
Why Traditional Email Security Falls Short
Legacy email security solutions rely heavily on signature-based detection, known malicious domains, and pattern recognition. However, AI-generated phishing campaigns circumvent these defenses through:
- Zero-day domains created specifically for each campaign
- Polymorphic content that changes with each iteration
- Legitimate infrastructure abuse using compromised accounts
- Advanced evasion techniques that detect and avoid sandbox environments
- Contextual awareness that makes content appear authentic
Email spoofing attacks have increased 54% year-over-year, with attackers exploiting new vectors like ICS calendar files for social engineering. This evolution demands a fundamentally different approach—one that combines human intelligence gathering with automated threat detection.
Leveraging OSINT for Proactive Phishing Defense
Building a Comprehensive OSINT Framework
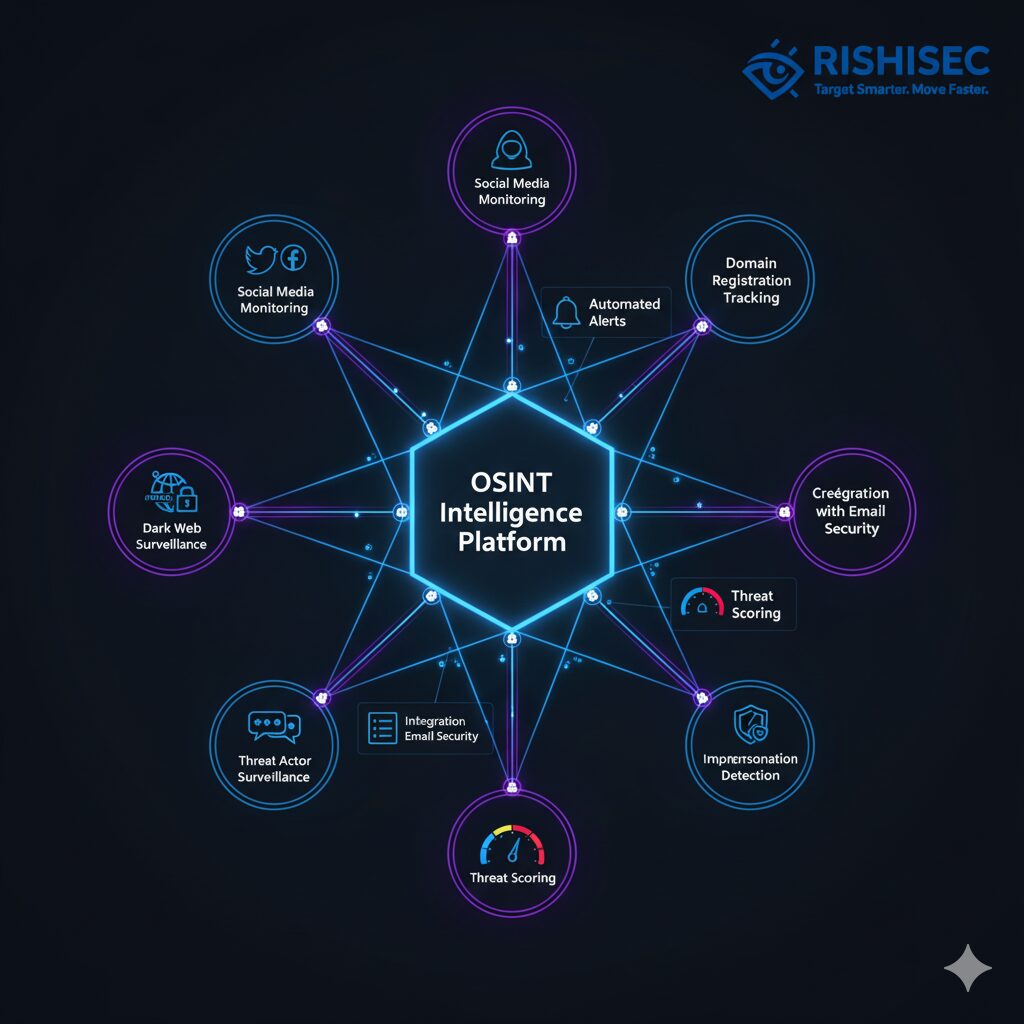
Open Source Intelligence provides corporate security teams with the same visibility that attackers use to craft their campaigns. By implementing a robust OSINT framework, you can identify vulnerabilities, monitor threat actor activity, and detect phishing campaigns in their early stages.
Key OSINT Components for Phishing Defense:
- Digital footprint analysis of your organization’s public presence
- Executive and employee exposure monitoring across social media and professional networks
- Domain and infrastructure monitoring for typosquatting and brand impersonation
- Dark web monitoring for leaked credentials and planned attacks
- Threat actor tracking across forums, marketplaces, and communication channels
- Brand mention monitoring to detect impersonation attempts
Modern OSINT platforms like Kindi enable security teams to automate these monitoring activities, providing real-time alerts when potential threats emerge. By understanding what information attackers can access about your organization, you can proactively reduce your attack surface and prepare targeted defenses.
Identifying AI-Generated Phishing Indicators Through OSINT
OSINT methodologies can reveal the infrastructure and patterns behind AI-generated phishing campaigns before they reach your inbox. Security teams should focus on:
Infrastructure Intelligence:
- Monitor newly registered domains containing your brand name or variations
- Track SSL certificate issuance for suspicious domains
- Analyze DNS records and hosting patterns associated with phishing campaigns
- Identify shared infrastructure across multiple phishing attempts
Threat Actor Intelligence:
- Monitor underground forums where phishing kits and AI tools are traded
- Track threat actor discussions about targeting specific industries or organizations
- Identify emerging phishing-as-a-service platforms leveraging AI
- Analyze leaked or shared phishing templates and techniques
Social Engineering Reconnaissance:
- Identify what public information exists about your executives and employees
- Monitor for data leaks that could enable personalized attacks
- Track organizational changes, events, and announcements that attackers might exploit
- Analyze employee social media activity that could be weaponized
For organizations looking to enhance their threat intelligence capabilities, integrating OSINT into your security operations center creates a force multiplier effect that dramatically improves detection rates.
Implementing Advanced Detection and Response Strategies
Integrating OSINT with Email Security Infrastructure
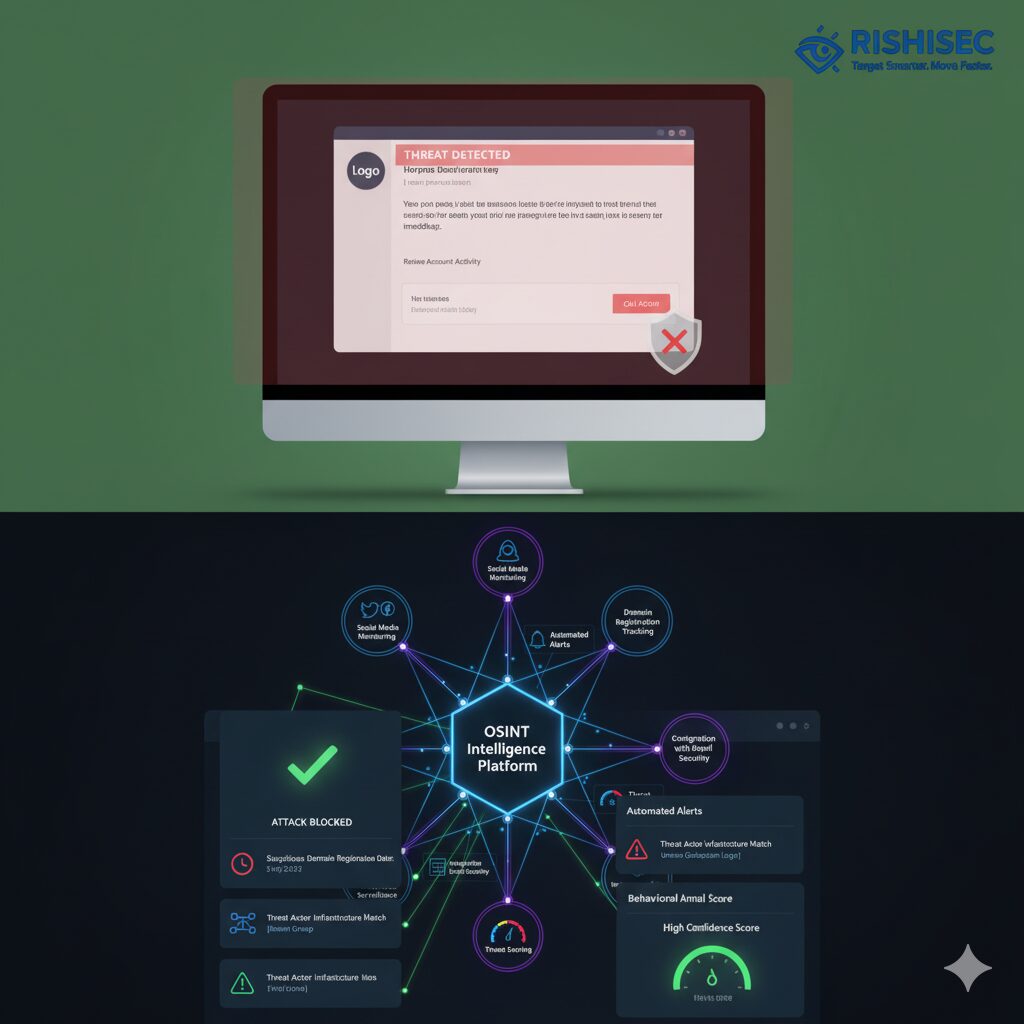
The most effective defense against AI-generated phishing combines OSINT-derived intelligence with your existing email security stack. This integration creates multiple layers of detection that can identify threats traditional systems miss.
Implementation Framework:
- Threat Intelligence Enrichment: Feed OSINT-gathered indicators of compromise (IOCs) into your email gateway, SIEM, and security orchestration platforms
- Behavioral Analysis: Use OSINT to establish baseline communication patterns and flag anomalies
- Sender Verification: Cross-reference sender information against OSINT databases of known threat infrastructure
- Content Analysis: Compare email content against known phishing templates and AI-generated text patterns
- Link and Attachment Scrutiny: Validate URLs and files against real-time OSINT threat feeds
Organizations implementing OSINT-enhanced SOC operations report significant improvements in alert accuracy and reduced false positive rates, allowing analysts to focus on genuine threats.
Automating OSINT Collection and Analysis
Manual OSINT gathering cannot keep pace with the volume and velocity of modern phishing campaigns. Automation is essential for corporate security teams to maintain effective defenses.
Automation Priorities:
- Continuous monitoring of domains, social media, and dark web sources
- Automated threat scoring based on multiple OSINT indicators
- Real-time alerting when high-confidence threats are identified
- Intelligence correlation across multiple data sources
- Automated response workflows for common threat scenarios
Advanced platforms enable security teams to create custom monitoring rules tailored to their organization’s specific risk profile. For example, you might configure alerts for:
- New domains registered containing your company name
- Executive names appearing in credential dumps
- Discussions of your organization in threat actor forums
- Sudden increases in brand impersonation attempts
- Suspicious job postings that could indicate reconnaissance
Training and Awareness Programs Enhanced by OSINT
Even the most sophisticated technical defenses require human vigilance. OSINT can dramatically improve security awareness training by providing real-world examples specific to your organization.
OSINT-Enhanced Training Approaches:
- Personalized threat scenarios based on actual reconnaissance of your organization
- Executive-specific training addressing their unique exposure and targeting
- Department-tailored content reflecting role-specific phishing tactics
- Real-time threat briefings when active campaigns target your industry
- Simulated attacks using techniques observed through OSINT monitoring
By showing employees actual examples of how attackers research and target your organization, you create more engaging and effective training that resonates with real-world threats.
Building a Sustainable OSINT-Driven Defense Program
Establishing Metrics and Continuous Improvement
Effective phishing defense requires measurable outcomes and continuous refinement. Corporate security teams should track:
Key Performance Indicators:
- Time to detect phishing campaigns targeting your organization
- Percentage of phishing attempts blocked before reaching users
- False positive rates in phishing detection
- Employee reporting rates for suspicious emails
- Mean time to respond to confirmed phishing incidents
- Reduction in successful phishing compromises
Regular assessment of these metrics enables data-driven improvements to your OSINT collection priorities, detection rules, and response procedures.
Integrating OSINT Across the Security Stack
OSINT shouldn’t exist in isolation—it should enhance every component of your security infrastructure. Consider how OSINT intelligence can improve:
- Identity and access management through credential monitoring
- Endpoint detection and response via threat actor TTPs
- Network security through infrastructure intelligence
- Incident response with contextual threat information
- Vulnerability management by prioritizing based on active exploitation
Organizations implementing comprehensive OSINT strategies for corporate risk detection report improved security posture across all domains, not just email security.
Collaboration and Intelligence Sharing
No organization faces AI-generated phishing threats in isolation. Participating in industry-specific Information Sharing and Analysis Centers (ISACs) and threat intelligence communities amplifies your defensive capabilities.
Collaboration Best Practices:
- Share anonymized indicators of compromise with industry peers
- Participate in threat intelligence platforms and communities
- Contribute to collective defense initiatives
- Maintain relationships with law enforcement and regulatory bodies
- Engage with security researchers tracking emerging threats
Conclusion
AI-generated phishing attacks represent one of the most significant threats facing corporate security teams in 2025, but they’re not insurmountable. By leveraging OSINT methodologies to gain visibility into threat actor activities, infrastructure, and tactics, security teams can shift from reactive defense to proactive threat hunting.
The key to success lies in integration—combining OSINT intelligence with automated detection systems, employee awareness programs, and continuous improvement processes. Organizations that embrace this comprehensive approach don’t just defend against today’s threats; they build adaptive security programs capable of evolving alongside the threat landscape.
For CISOs and security leaders looking to implement these strategies, platforms like Kindi provide the automation and intelligence capabilities necessary to operationalize OSINT at enterprise scale. The question isn’t whether AI-generated phishing will target your organization—it’s whether you’ll be prepared when it does.
Start building your OSINT-driven phishing defense program today, and transform your security team from reactive responders to proactive threat hunters who stay one step ahead of even the most sophisticated AI-powered attacks.

