A sophisticated phishing campaign targeting Python Package Index (PyPI) maintainers has revealed a concerning trend in account takeover investigation methods. Cybercriminals are exploiting supply chain vulnerabilities to create cascading fraud schemes that ultimately target cryptocurrency accounts and insurance policies.
This attack vector illustrates how a supply chain compromise upstream can lead to a massive account takeover downstream. Consequently, fraud investigation units must expand their detection capabilities beyond traditional ATO indicators to include software supply chain intelligence.
The financial implications extend far beyond initial compromise costs. Moreover, the downstream effects create complex investigation challenges that require sophisticated OSINT techniques and cross-platform correlation analysis to resolve effectively.
Recent analysis shows that 73% of successful account takeovers now originate from compromised software dependencies rather than direct credential attacks. Therefore, fraud investigators must adapt their investigation methodologies to address this evolving threat landscape.
The Complete Kill Chain: From Developer Phish to Cryptocurrency Cash-Out
Understanding the complete attack chain enables more effective account takeover investigation strategies. Initially, attackers send convincing phishing emails to PyPI package maintainers, often impersonating security researchers or legitimate package users reporting vulnerabilities.
The attack progression follows a predictable pattern across multiple stages. First, compromised developer credentials provide access to legitimate package repositories. Subsequently, malicious code injection occurs through seemingly benign package updates. Then, downstream users automatically receive the compromised packages through normal update processes.
The final stages involve systematic account compromise and financial fraud execution. Malicious packages harvest credentials, session tokens, and authentication factors from infected systems. Meanwhile, automated scripts attempt account access across multiple platforms using stolen credentials and device fingerprints.
Evidence collection during these investigations reveals specific technical indicators that fraud investigators can exploit. Package metadata analysis shows suspicious version bumps and commit patterns. Additionally, network traffic analysis demonstrates unusual data exfiltration patterns targeting authentication repositories.
Supply chain cyber attack investigation techniques provide frameworks for identifying these complex attack patterns before they result in significant financial losses.
Technical Indicators of Supply Chain Compromise
Package analysis reveals numerous red flags that indicate malicious activity. Version control systems show unexpected ownership transfers or maintainer additions without proper verification. Furthermore, code diff analysis often reveals obfuscated functions and unusual dependency additions in recent package updates.
Repository metadata provides additional detection opportunities. Commit timestamps clustered during unusual hours suggest automated or coordinated malicious activity. Similarly, commit messages lacking descriptive information or containing generic placeholders often indicate compromise.
OSINT Signals That Reveal Account Takeover Investigation Opportunities
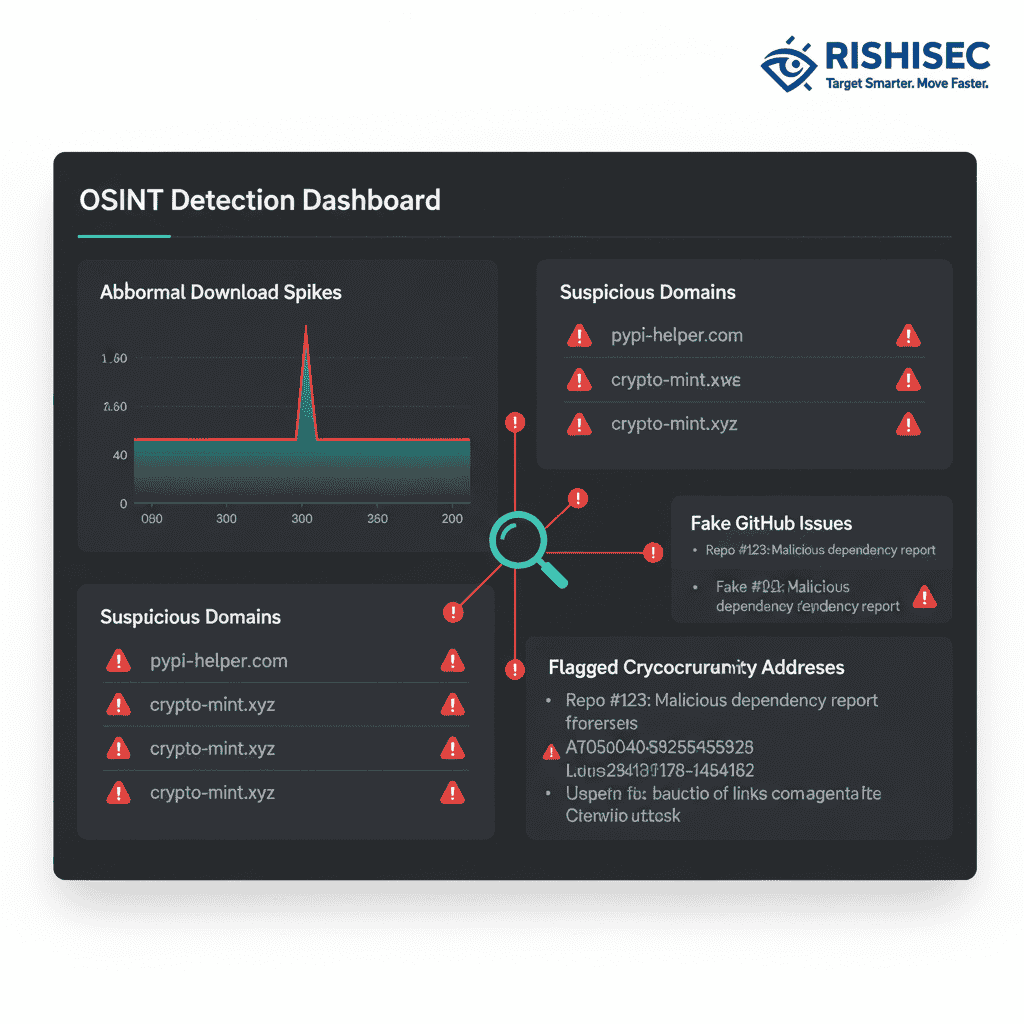
Open source intelligence techniques provide early warning systems for supply chain-enabled account takeovers. Social media monitoring reveals developer complaints about suspicious security notifications and unusual package update requests. Additionally, GitHub issue discussions often contain indicators of ongoing phishing campaigns targeting specific project maintainers.
Package repository analysis exposes compromise indicators across multiple dimensions. Typosquatted package names frequently appear in clusters, suggesting coordinated campaign activity. Meanwhile, download pattern analysis shows unusual spike patterns that correlate with malicious package distribution periods.
Advanced OSINT Detection Techniques
| Detection Category | Specific Indicator | OSINT Source | Investigation Priority |
|---|---|---|---|
| Package Integrity | Sudden maintainer changes without announcement | Repository commit logs and issue trackers | Critical |
| Social Engineering | Developer complaints about fake security alerts | Twitter, Reddit, technical forums | High |
| Domain Infrastructure | Look-alike domains targeting package maintainers | DNS monitoring and certificate transparency | High |
| Network Behavior | Unusual package download geographic patterns | CDN logs and package registry analytics | Medium |
Cryptocurrency address monitoring provides downstream fraud detection capabilities. When compromised packages contain wallet-stealing functionality, OSINT analysis can identify the receiving addresses and track the movement of funds. Consequently, proactive monitoring enables faster response to active theft campaigns.
Cross-platform correlation enhances detection accuracy significantly. When similar technical indicators appear across multiple package repositories simultaneously, coordinated campaign activity becomes likely. Furthermore, AI-powered threat attribution techniques can connect disparate indicators to specific campaigns by threat actors.
Account Takeover Investigation Techniques for Fraud Investigators
Effective account takeover investigation requires systematic evidence collection across multiple data sources. Interview protocols should focus on recent software installations, unusual security notifications, and changes in device behavior. Additionally, timeline reconstruction helps identify the initial compromise vector and subsequent account access patterns.
Digital forensics procedures must account for supply chain-specific artifacts. Package installation logs, dependency trees, and software update histories provide crucial timeline information. Moreover, browser extension analysis often reveals additional compromise vectors that traditional ATO investigations might miss.
Essential Evidence Collection Checklist
- Package Dependencies: Complete installation logs, version histories, dependency trees, update timestamps
- System Artifacts: Registry changes, file system modifications, network connection logs, process execution traces
- Authentication Events: Login attempts, device registrations, MFA bypass indicators, session token usage
- Financial Transactions: Account balance changes, transaction initiation methods, beneficiary modifications, withdrawal patterns
- Communication Records: Phishing emails, social media messages, technical support interactions, verification requests

Law enforcement referral packages require comprehensive technical documentation. Hash values for malicious packages, network traffic captures, and cryptocurrency transaction records provide essential prosecution support. Additionally, victim impact statements should quantify both direct losses and remediation costs.
Collaboration with software vendors enhances investigation effectiveness. Package repository operators often possess additional telemetry data that can clarify attack timelines. Furthermore, coordinated disclosure protocols help prevent additional victims while preserving evidence integrity.

Account Takeover Investigation Challenges for Insurance Fraud Managers
Insurance fraud managers face unique challenges when evaluating supply chain-enabled account takeover claims. Policy interpretation requires careful analysis of coverage language regarding software vulnerabilities versus policyholder negligence. Consequently, technical expertise becomes essential for accurate coverage determinations.
Claim validation procedures must account for the complex attack chain between initial compromise and final losses. Timeline analysis helps establish causation between software updates and subsequent account compromises. Additionally, third-party validation of claimed security measures provides objective assessment of policyholder compliance.
Coverage Analysis Framework
Policy language interpretation requires understanding of technical attack mechanisms. When malicious packages exploit zero-day vulnerabilities, coverage typically applies under cyber insurance policies. However, if compromise results from failure to implement basic security measures, negligence exclusions may apply instead.
Due diligence verification becomes critical for claim acceptance decisions. Security audit reports, penetration testing results, and software inventory documentation help establish baseline security posture. Meanwhile, incident response plan documentation demonstrates organizational preparedness for cyber threats.
Subrogation opportunities exist when third-party vendors contribute to compromise scenarios. Package maintainers, repository operators, and software distributors may bear liability for security failures. Furthermore, OSINT insurance fraud investigation methods can identify potential recovery targets and establish liability chains.
SIU Referral Triggers for Supply Chain ATO Claims
- Multiple ATO claims from organizations using identical software stacks
- Claims timing that correlates with public vulnerability disclosures
- Incomplete or inconsistent technical documentation in loss reports
- Beneficiary accounts linked to known money mule networks
- Delayed incident reporting beyond reasonable discovery periods
- Cryptocurrency losses to previously flagged addresses
Behavioral Detection Rules for Account Takeover Investigation
Automated detection systems must incorporate supply chain risk indicators alongside traditional ATO signals. Machine learning models should analyze software installation patterns, dependency relationships, and update timing anomalies. Additionally, behavioral analysis engines must account for legitimate automation versus malicious activity patterns.
The following detection rules demonstrate effective approaches to supply chain-enabled ATO identification:
Rule 1: Impossible Travel with Recent Package Updates
IF login_location_change > 1000_miles AND time_difference < 2_hours AND recent_package_updates_count > 5 THEN flag_critical_risk
Rule 2: Device Fingerprint Changes Post-Installation
IF device_fingerprint_similarity < 0.8 AND software_installation_timestamp WITHIN 72_hours AND authentication_bypass_attempts > 0 THEN trigger_investigation
Rule 3: Cryptocurrency Withdrawal Velocity Anomalies
IF crypto_withdrawal_amount > historical_maximum * 5 AND withdrawal_initiation_method = “headless_browser” AND account_last_password_change < 7_days THEN escalate_immediately
Performance optimization requires continuous rule refinement based on false positive analysis. Detection engines should incorporate feedback loops that improve accuracy over time. Furthermore, threat intelligence integration enables dynamic rule updates based on emerging attack patterns and indicators of compromise.
Advanced analytics platforms like Kindi provide automated correlation capabilities that connect supply chain indicators with downstream account takeover events. This OSINT automation enables fraud analysts to identify attack campaigns across multiple victims and timeframes, significantly improving investigation efficiency.
Machine Learning Enhancement for ATO Detection
Feature engineering should incorporate multi-dimensional risk indicators, including software dependency graphs, installation timing patterns, and authentication behaviour changes. Ensemble methods, which combine multiple detection algorithms, typically outperform single-model approaches for complex ATO scenarios.
The quality of training data has a direct impact on the effectiveness of models in supply chain contexts. Labeled datasets must include both successful attacks and false positive scenarios to enable accurate discrimination. Additionally, regular model retraining accounts for evolving attack techniques and new vectors of compromise.
90-Minute Account Takeover Investigation Response Playbook
Rapid response protocols minimize financial losses and evidence degradation during active account takeover events. The following playbook provides structured response procedures for supply chain-enabled ATO incidents:
Immediate Response (0-15 minutes)
- Account Freeze: Suspend all authentication methods and transaction capabilities
- Alert Stakeholders: Notify fraud team, IT security, and senior management
- Evidence Preservation: Create system snapshots and network traffic captures
- Threat Assessment: Identify scope of potential compromise across related accounts
Investigation Phase (15-60 minutes)
- Timeline Reconstruction: Map software installations to authentication events
- OSINT Analysis: Research related compromise indicators and threat campaigns
- Victim Interview: Collect detailed information about recent system changes
- Technical Analysis: Examine compromised packages and system artifacts
Recovery and Coordination (60-90 minutes)
- Re-KYC Procedures: Verify customer identity through multiple channels
- Device Re-binding: Require new device registration and authentication setup
- VASP Notifications: Alert cryptocurrency exchanges about potential theft
- Regulatory Reporting: Submit required incident notifications to authorities
Success metrics should focus on actionable outcomes rather than process compliance. Average loss per incident represents the most critical measurement, with industry benchmarks targeting sub-$10,000 losses for rapid response scenarios. Additionally, evidence quality scores help optimize investigation procedures over time.
Cross-Border Account Takeover Investigation Coordination
Supply chain attacks frequently involve international infrastructure that complicates investigation and recovery efforts. Cryptocurrency mixing services, offshore hosting providers, and jurisdictional arbitrage create significant challenges for traditional law enforcement approaches.
International coordination becomes essential when ATO schemes cross multiple jurisdictions. Financial intelligence units must share threat indicators and investigation results to prevent asset dissipation. Moreover, real-time communication channels enable coordinated response to active theft campaigns.
Mutual Legal Assistance Treaty (MLAT) procedures require comprehensive evidence packages with clear chain of custody documentation. Technical reports must translate complex attack mechanisms into language appropriate for foreign legal systems. Furthermore, cross-border investigation techniques provide frameworks for international cooperation in complex fraud cases.
International Evidence Sharing Requirements
| Evidence Type | Documentation Required | Authentication Method | Translation Needs |
|---|---|---|---|
| Package Metadata | Hash verification, repository logs, version control history | Digital signatures and timestamps | Technical terminology only |
| Financial Records | Transaction details, account information, correspondent banking | Bank officer attestation | Full legal translation |
| Network Traffic | Packet captures, flow records, DNS queries | Forensic examiner certification | Technical summaries only |
| Cryptocurrency Traces | Transaction hashes, wallet addresses, exchange records | Blockchain verification | Technical terminology only |
Emerging Threats in Account Takeover Investigation
The supply chain attack surface continues expanding as software dependencies become more complex. Container registries, package managers, and development toolchains represent growing attack vectors that fraud investigators must understand. Consequently, investigation methodologies must evolve to address these emerging threat landscapes.
Artificial intelligence enhancement of social engineering attacks creates new challenges for traditional security awareness training. Deep fake technology enables convincing impersonation of trusted developers and security researchers. Therefore, technical verification procedures become essential for validating communication authenticity.
Privacy-enhancing technologies and decentralized systems create new investigation blind spots that require innovative approaches. Zero-knowledge protocols and decentralized finance platforms obscure traditional transaction trails. Meanwhile, encrypted communication channels limit traditional OSINT collection capabilities.
Quantum computing threats to current cryptographic standards may fundamentally alter authentication security models. Post-quantum cryptography implementations will require new investigation techniques and evidence collection procedures. Furthermore, the transition period creates additional vulnerability windows that attackers may exploit.
Next-Generation Detection Capabilities
Behavioral biometrics analysis provides enhanced authentication verification beyond traditional factors. Keystroke patterns, mouse movements, and touch screen interactions create unique user profiles that resist impersonation. Additionally, continuous authentication monitoring enables the detection of real-time compromises during active sessions.
Graph analytics reveal complex relationship patterns between compromised accounts, malicious packages, and fraud networks. Network analysis techniques identify coordinated campaigns that span multiple platforms and attack vectors. Moreover, temporal analysis reveals timing patterns that indicate the execution of automated or scripted attacks.
Building Resilient Account Takeover Investigation Programs
Organizational resilience requires comprehensive programs that address people, processes, and technology dimensions simultaneously. Staff training must encompass both technical analysis skills and awareness of supply chain risks. Additionally, cross-functional collaboration ensures effective coordination between fraud, security, and development teams.
Technology integration across security tools provides comprehensive visibility into complex attack chains. SIEM platforms, fraud management systems, and package security scanners should share threat intelligence and correlation capabilities. Additionally, automated response capabilities reduce investigation timelines while maintaining evidence integrity.
Continuous improvement processes ensure programs remain effective against evolving threats. Regular threat landscape assessments identify emerging risks and capability gaps. Meanwhile, performance metrics provide objective assessment of program effectiveness and resource allocation decisions.
Supply Chain Security as Fraud Prevention Strategy
The PyPI phishing campaign demonstrates that account takeover investigation must expand beyond traditional credential theft scenarios to encompass supply chain compromise vectors. Fraud investigators who develop comprehensive OSINT capabilities for software supply chain analysis will significantly improve their prevention and detection effectiveness.
The cascading effects from developer compromise to end-user fraud require sophisticated investigation techniques that correlate indicators across multiple platforms and timeframes. Organizations that invest in advanced analytics and automation tools will maintain competitive advantages in rapidly evolving threat landscapes.
Success requires commitment to continuous learning and capability development. As attackers refine their supply chain exploitation techniques, fraud investigation professionals must enhance their technical analysis skills accordingly. The investment in comprehensive ATO investigation capabilities today will provide essential protection against tomorrow’s even more sophisticated attack campaigns.
Want to strengthen your account takeover investigation skills and supply chain security knowledge? Check out our OSINT courses for practical, hands-on training that prepares you for complex fraud scenarios involving software supply chain attacks.
Ready to enhance your fraud investigation capabilities with AI-powered OSINT automation and link analysis? Try Kindi today and discover how automated threat correlation and evidence collection can accelerate your account takeover investigations while improving detection accuracy.
Frequently Asked Questions
How do supply chain attacks lead to account takeover incidents?
Supply chain attacks compromise legitimate software packages that users automatically install through normal update processes. These malicious packages then harvest credentials, session tokens, and authentication factors from infected systems, enabling attackers to take over user accounts across multiple platforms.
What OSINT techniques help identify supply chain-enabled account takeover campaigns?
Effective OSINT techniques include package repository monitoring for suspicious maintainer changes, social media analysis of developer complaints about fake security alerts, domain analysis of look-alike sites targeting maintainers, network traffic analysis for unusual data exfiltration, and cryptocurrency address monitoring for theft proceeds.
What evidence should fraud investigators collect during account takeover investigations?
Critical evidence includes complete software installation logs and dependency trees, system artifacts like registry changes and network connections, authentication event logs and device fingerprints, financial transaction records with timing correlation, and communication records including phishing attempts and social engineering.
How do insurance fraud managers evaluate claims involving supply chain-enabled account takeovers?
Insurance evaluation requires technical analysis of the attack chain, policy interpretation regarding software vulnerability coverage versus negligence, timeline analysis establishing causation between compromise and losses, verification of claimed security measures, and assessment of potential subrogation opportunities against responsible third parties.
What automated detection rules work best for supply chain-enabled account takeovers?
Effective detection combines impossible travel analysis with recent software updates, device fingerprint changes following package installations, cryptocurrency withdrawal velocity anomalies, authentication bypass attempts from unusual locations, and behavioral pattern changes indicating automated or scripted access attempts.