Investigative journalists operating in high-risk environments face unprecedented digital threats that can compromise their safety, expose their sources, and derail critical investigations. Understanding and implementing journalist digital safety OSINT protocols has become essential for reporters covering conflict zones, authoritarian regimes, and sensitive corruption cases where adversaries actively target journalists through sophisticated digital attacks.
The threat landscape has undergone significant evolution in recent years. Journalists now face state-sponsored surveillance, targeted malware campaigns, location tracking, and coordinated digital harassment designed to silence reporting. Moreover, the tools and tactics once reserved for intelligence agencies have become accessible to criminal organizations, corrupt officials, and repressive governments determined to identify sources and prevent exposure of wrongdoing.
Therefore, modern investigative journalists must master defensive OSINT techniques alongside traditional reporting skills. These protocols protect not only journalists themselves but also the vulnerable sources who risk their lives to expose the truth. Furthermore, implementing robust digital safety measures ensures that investigations can continue despite hostile interference and that collected evidence remains secure for publication.
Understanding Digital Threats Facing Investigative Journalists
Adequate protection requires a comprehensive understanding of the specific threats targeting journalists in high-risk environments. These threats vary based on geographic location, reporting focus, and the adversaries that journalists seek to expose.
State-sponsored surveillance represents one of the most sophisticated threats facing investigative journalists. Governments with advanced cyber capabilities deploy targeted malware, conduct network-level monitoring, and exploit zero-day vulnerabilities to compromise journalists devices and communications. Additionally, these operations often involve physical surveillance coordinated with digital tracking to build comprehensive profiles of journalists activities and sources.
Commercial spyware has democratized surveillance capabilities, enabling even resource-limited adversaries to deploy sophisticated tracking tools. Products like Pegasus and similar commercial surveillance software can compromise smartphones without requiring user interaction, allowing access to encrypted communications, location data, and stored files. Consequently, journalists must assume that standard device security measures are insufficient against determined adversaries with access to these tools.
Common Attack Vectors and Exploitation Methods
Understanding how adversaries compromise journalist security helps inform effective defensive strategies. These attack vectors represent the most frequent methods used to target investigative reporters in hostile environments.
Phishing campaigns specifically target journalists with customized messages designed to exploit their professional curiosity and need for rapid response. Adversaries craft convincing fake communications from sources, editors, or professional contacts that contain malicious links or attachments. Similarly, watering hole attacks frequently compromise websites that journalists often visit, automatically infecting devices without requiring direct interaction.
Network exploitation targets the communications infrastructure journalists rely on for reporting and source protection. Man-in-the-middle attacks intercept communications between journalists and their sources, while compromised Wi-Fi networks in hotels, cafes, and airports provide entry points for adversaries to monitor journalist activities. Human rights OSINT investigations face similar network security challenges when documenting sensitive information.
| Threat Type | Primary Targets | Risk Level | Detection Difficulty |
|---|---|---|---|
| Targeted Malware | Devices, communications, stored files | Critical | High |
| Network Surveillance | Internet traffic, email, and messaging | High | Medium |
| Location Tracking | Physical movements, source meetings | Critical | Low |
| Social Engineering | Credentials, source information | High | Medium |
Essential Digital Safety Protocols for Journalist Security
Implementing comprehensive digital safety protocols requires a systematic approach that addresses multiple threat vectors simultaneously. These protocols must strike a balance between security and operational requirements to ensure compelling journalism in challenging environments.
Device security forms the foundation of journalists’ digital safety OSINT practices. Journalists should maintain separate devices for sensitive investigations, using dedicated hardware that never connects to personal accounts or social media. Additionally, regular device wiping and reinstallation ensure that any undetected compromises are eliminated before they can cause lasting damage.
Encryption must be implemented at multiple layers to protect journalist communications and stored information. End-to-end encrypted messaging applications provide basic protection, but journalists must also encrypt device storage, backup systems, and file transfers to ensure comprehensive security. Moreover, encryption keys should be managed carefully, with secure backup procedures that prevent both loss and unauthorized access.
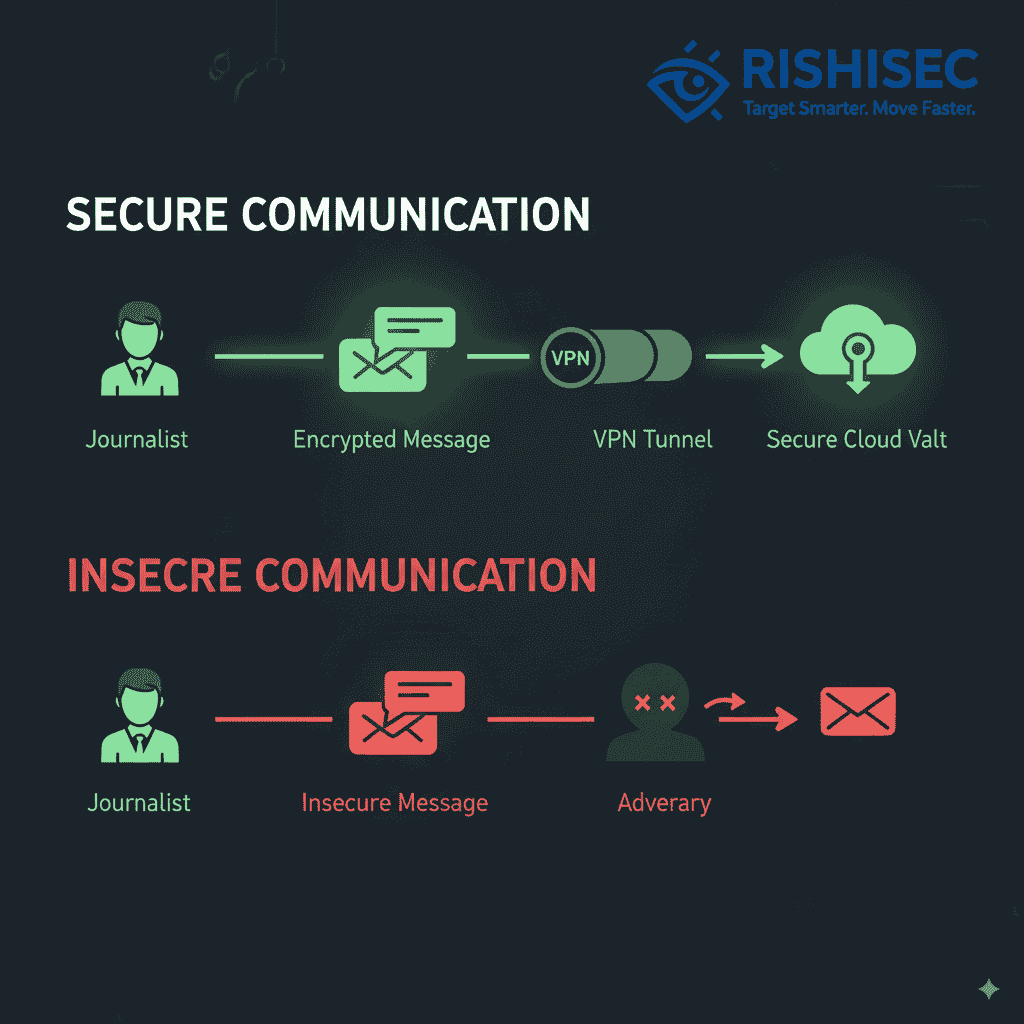
Secure Communication Strategies
Protecting communications with sources represents the highest priority for journalist digital safety protocols. These strategies must ensure that even if communications are intercepted, the content and source identities remain protected.
Signal and other end-to-end encrypted messaging applications provide strong protection for routine communications. However, journalists must understand the metadata these applications generate and the potential for traffic analysis to reveal communication patterns. Therefore, supplementary techniques like using Tor for accessing messaging services add additional protection layers.
Dead drop communication methods enable asynchronous information exchange between journalists and sources without direct digital contact. These methods involve using encrypted cloud storage, anonymous file sharing services, or custom secure communication platforms that minimize metadata exposure and prevent real-time interception.
Voice and video communications present unique challenges because they require real-time data transfer that is more vulnerable to interception. Consequently, journalists should avoid voice communications for highly sensitive matters or use specialized secure calling services that provide strong encryption and minimal metadata generation.
Operational Security Best Practices
Operational security (OPSEC) extends beyond technical measures to include behavioral practices that reduce journalist vulnerability. These practices address both digital and physical security concerns that affect investigation safety.
- Develop and maintain consistent cover identities for accessing sensitive information without revealing journalist status.
- Use virtual private networks (VPNs) or Tor to obscure internet traffic origins and destinations
- Implement strict compartmentalization, keeping different investigations and sources completely separated.
- Practice counter-surveillance techniques to detect physical and digital monitoring attempts
- Establish secure backup and emergency destruction procedures for sensitive materials
- Develop and test emergency response plans for scenarios involving device compromise or source exposure.
Advanced Source Protection Techniques Using OSINT
Protecting sources requires journalists to think like adversaries, using OSINT techniques defensively to identify potential compromises before they endanger sources. These advanced techniques combine technical analysis with behavioral security measures.
Defensive OSINT analysis helps journalists identify their own digital footprints and potential vulnerabilities that adversaries might exploit. By regularly searching for their own information across multiple platforms, journalists can discover exposed data and take corrective action before adversaries use it for targeting. Similarly, monitoring for mentions of investigation topics helps identify when adversaries become aware of journalist activities.

Digital hygiene training represents a critical but often overlooked aspect of journalist digital safety and OSINT protocols. Journalists must educate sources about basic security practices, explaining how their digital activities can expose their identity or relationship with journalists. Furthermore, providing sources with secure communication tools and clear instructions for safe usage prevents common mistakes that compromise source protection.
Tools like Kindi enable journalists to map relationships between sources, adversaries, and potential compromises through link analysis. The platform’s collaboration features allow investigation teams to securely share threat intelligence while maintaining operational security across distributed reporting environments.
Metadata Sanitization and Evidence Preservation
Digital evidence collected during investigations often contains metadata that can compromise sources or reveal investigation methods. Journalists must implement systematic metadata sanitization while preserving evidence integrity for publication.
Image and video metadata includes GPS coordinates, device information, and timestamps that can identify when and where content was captured. Before publishing or sharing investigative materials, journalists must strip this metadata using specialized tools that remove identifying information without degrading content quality. However, original files with complete metadata should be preserved securely for verification purposes.
Document metadata presents similar risks, revealing author information, editing history, and organizational details that can expose sources. Consequently, journalists should convert documents to sanitized formats before sharing, while maintaining secure archives of original materials that preserve complete provenance chains.
Secure Evidence Management Systems
Managing investigative evidence securely throughout the reporting process requires systematic approaches that protect both content and access patterns. These systems must strike a balance between security and the collaborative nature of modern investigative journalism.
Encrypted cloud storage solutions offer secure repositories for investigative materials; however, journalists must carefully configure access controls and sharing mechanisms. Additionally, using services with strong privacy protections and legal jurisdictions favorable to press freedom reduces risks of government-compelled disclosure.
Local storage encryption ensures that even if devices are seized or stolen, investigative materials remain protected. Full disk encryption, combined with strong passwords, provides basic protection, while additional file-level encryption adds a defence-in-depth layer for the most sensitive materials.
Backup strategies must address both data protection and secure disposal requirements. Regular encrypted backups stored in multiple secure locations prevent data loss, while secure deletion procedures ensure that abandoned devices or storage media don’t expose sensitive information. Documenting state violence with OSINT requires similar rigorous evidence management approaches.
Technical Tools and Platforms for Journalist Security
Selecting and properly configuring security tools represents a critical component of journalist digital safety OSINT protocols. These tools must provide strong protection while remaining usable under operational pressure in challenging environments.
Operating system selection impacts baseline security, with privacy-focused alternatives like Tails providing strong isolation and anti-forensic properties. These specialized systems run from USB drives without leaving traces on host computers, enabling secure work from untrusted devices. However, journalists must balance security benefits against usability constraints and technical expertise requirements.
Password management systems enable journalists to maintain strong, unique credentials across multiple platforms without creating memorization burdens. These tools should include encrypted storage, secure sharing capabilities for team collaboration, and emergency access procedures that enable colleagues to recover critical credentials in the event that journalists become unavailable.
Anonymous Research and Investigation Tools
Conducting investigations without exposing journalist identity requires specialized tools that obscure digital footprints while maintaining research effectiveness. These tools enable journalists to gather information without alerting adversaries to investigation focus or progress.
Tor browser provides anonymous web access by routing traffic through multiple encrypted relays that prevent website operators from identifying visitor locations or identities. However, journalists must understand Tor limitations, including potential exit node monitoring and correlation attacks that can compromise anonymity if used improperly.
Virtual machines and sandboxed environments enable journalists to test suspicious files or access potentially compromised websites without risking their primary systems. These isolated environments can be reset or destroyed after use, preventing persistent compromises from spreading to critical systems.
Anonymous email and identity services allow journalists to create research identities that cannot be traced back to their real identities. These services must be selected carefully, prioritizing providers with strong privacy protections and technical security measures that prevent correlation between anonymous and real identities.
Mobile Device Security Considerations
Smartphones present unique security challenges because they combine communications, location tracking, and always-on connectivity in devices that journalists must carry constantly. Managing these risks requires specialized approaches that balance functionality with protection.
Burner phones provide disposable communication devices for sensitive source contacts, but journalists must understand that even burner phones generate metadata and can be compromised through network-level surveillance. Therefore, burner phones should be acquired anonymously, used for limited purposes, and disposed of properly after investigations conclude.
Mobile security applications can provide additional protection layers, including malware detection, network security, and suspicious activity monitoring. However, journalists should recognize that these applications cannot protect against sophisticated state-sponsored attacks and should not create false confidence in device security.
Physical security measures remain important even with strong digital protections. Journalists should implement device tracking and remote wipe capabilities, use privacy screens to prevent visual surveillance, and develop procedures for rapidly securing or destroying devices if compromise appears imminent.
Building Security Culture in Newsrooms and Investigation Teams
Individual journalist security measures provide limited protection if broader organizational practices create vulnerabilities. Building comprehensive security cultures requires systematic approaches that engage entire investigation teams and supporting organizations.
Security training programs must address both technical skills and security awareness, helping journalists understand threats and appropriate responses. Regular training updates ensure that teams stay current with evolving threats and emerging protection techniques. Moreover, training should include practical exercises that test security procedures under realistic scenarios.
Threat modeling helps organizations identify their specific vulnerabilities and prioritize security investments accordingly. Different investigations and operating environments require different security approaches, and effective threat modeling ensures that resources focus on addressing the most critical risks facing specific journalism contexts.
Emergency Response and Incident Management
Despite best efforts, security incidents will occur, and organizations must prepare comprehensive response procedures that minimize damage and protect affected journalists and sources. These procedures should address both technical compromise and physical security incidents.
Incident response plans should define clear roles, communication channels, and decision-making authority for security emergencies. Additionally, plans must address notification requirements for affected sources, legal counsel engagement, and coordination with press freedom organizations that can provide specialized assistance.
Post-incident analysis helps organisations learn from security failures and strengthen defences against similar future attacks. However, these analyses must balance transparency with operational security, avoiding public disclosure of sensitive security measures while sharing lessons learned with the broader journalism community.
Collaboration with Security Experts and Support Organizations
Journalists should not face digital security challenges alone, and numerous organizations provide specialized support for at-risk reporters. Building relationships with these support networks before crises occur ensures rapid access to expertise when incidents happen.
Press freedom organizations like the Committee to Protect Journalists and Reporters Without Borders provide emergency assistance, security training, and advocacy support for threatened journalists. Similarly, digital security organizations like Access Now offer technical assistance and can provide expert analysis of suspected compromises.
Legal support becomes essential when journalists face government pressure, surveillance allegations, or attempts to compel source disclosure. Establishing relationships with media lawyers familiar with press freedom issues ensures rapid access to legal expertise during security incidents.
Ethical Considerations in Journalist Digital Safety
Implementing robust security measures raises ethical questions about journalist responsibilities to sources, audiences, and the communities they serve. These considerations require careful balancing of competing obligations and transparent decision-making about security tradeoffs.
Source protection obligations extend beyond simply maintaining confidentiality to actively protecting sources from digital compromise. Journalists must honestly communicate security limitations to sources, ensuring they understand risks associated with cooperation. Furthermore, journalists should decline source cooperation if security measures are insufficient to protect highly vulnerable individuals.
Transparency with audiences about security practices builds trust while avoiding specific disclosures that could compromise security. Journalists should explain general security approaches without revealing detailed methods that adversaries could exploit. Additionally, acknowledging security challenges and limitations demonstrates journalistic integrity while managing audience expectations.
Balancing Security with Journalistic Access
Strong security measures can create barriers that limit journalist ability to gather information and maintain source relationships. Finding appropriate balances requires careful consideration of specific circumstances and continuous refinement of security approaches.
Source accessibility suffers when security requirements become too burdensome, potentially preventing crucial information from reaching journalists. Therefore, security measures should be calibrated to specific threat levels, using stronger protections for highly sensitive sources while maintaining more accessible channels for lower-risk communications.
Verification requirements may conflict with source security needs, creating tensions between journalistic standards and protection obligations. Journalists must develop creative approaches that enable adequate verification without exposing sources to unacceptable risks, sometimes accepting higher uncertainty rather than demanding verification methods that compromise source safety.
Conclusion: Security as Foundation for Fearless Journalism
Journalist digital safety OSINT protocols represent essential foundations for effective investigative reporting in high-risk environments. These protocols enable journalists to pursue critical investigations despite hostile interference while protecting the vulnerable sources who make such journalism possible.
The digital threat landscape will continue evolving as adversaries develop new capabilities and tactics for targeting journalists. Therefore, security practices must remain dynamic, with continuous learning and adaptation to address emerging threats. Organizations that invest in comprehensive security cultures will enable their journalists to operate more safely and effectively in challenging environments.
Ultimately, robust digital security serves journalism’s core mission by protecting the reporting that holds power accountable and exposes injustice. Journalists who master these security protocols can pursue investigations that others abandon due to security concerns, ensuring that important stories reach their audiences despite efforts by adversaries to suppress them.
The investment required for comprehensive digital safety for journalists pays dividends through sustained investigative capabilities, protected sources, and reporters who can continue their critical work despite targeted attacks. As threats continue to escalate, security excellence becomes not merely protective but essential for journalism to survive and thrive.
Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training. Discover how Kindi’s secure collaboration features can protect your sensitive investigations and source relationships. Sign up for our newsletter to stay updated on journalist security best practices and emerging digital threats.
FAQ
What are the most critical digital security threats facing investigative journalists today?
The most critical threats include targeted malware and spyware like Pegasus, state-sponsored surveillance, network interception, location tracking, and coordinated phishing campaigns. These threats are particularly severe for journalists covering sensitive topics in authoritarian environments or investigating powerful adversaries.
How can journalists protect their sources from digital compromise?
Source protection requires end-to-end encrypted communications, metadata sanitization, secure evidence management, compartmentalization between different sources, and educating sources about digital security practices. Journalists should also use defensive OSINT to monitor for potential compromises and implement emergency response procedures.
What communication tools provide the strongest protection for journalist-source interactions?
Signal provides strong end-to-end encryption for routine communications, while Tor combined with secure email services like ProtonMail offers additional anonymity. For highly sensitive sources, dead drop methods using encrypted cloud storage or specialized secure drop systems provide the strongest protection by eliminating real-time connections.
How should journalists balance security requirements with journalistic accessibility?
Security measures should be calibrated to specific threat levels rather than applying maximum security universally. Lower-risk communications can use more accessible methods, while highly sensitive sources receive maximum protection. Journalists should communicate clearly with sources about security requirements and available options.
What should journalists do if they suspect their devices have been compromised?
Immediately stop using suspected compromised devices for sensitive activities. Secure any devices containing evidence or source information. Contact digital security experts for forensic analysis. Notify affected sources through secure alternative channels. Implement emergency response procedures. Organizations like Access Now provide emergency support for compromised journalists.

