OSINT Exposes Fake Drug Trials Exploiting Desperate Patients

Post-holiday medical bills are sky-high, so crooks launch fake drug trials to harvest cash and personal data from sick people. We will walk through the OSINT or open source intelligence techniques that uncover the forged domains, ghost investigators, and regulatory filing lies that keep these scams alive. Why January Is Open-Season on Desperate Patients Every […]
Sanctions Evasion Tracking: OSINT Tactics That Actually Work
Right now a rusty bulker flying a Panamanian flag is offloading crude into a lightering fleet outside Kalamata. The bill of lading says “Malaysia,” the insurer is a one-man shop in St. Kitts, and the buyer’s domain was registered in Moscow—48 hours after the EU embargo hit. If you’re still grep-ing for “sanctions” in CSV […]
Darknet Diplomacy Leaks Expose Covert Embassy Cash Routes

Thursday morning, 03:47 GMT. A Tor-only paste drops on a Russian-language forum: a 1,300-row spreadsheet tagged “diplomatic pouch – Q3.” Within 20 minutes it is mirrored to six more onions, hashed on GitHub, and blasted across Telegram. Government & intelligence agencies wake up to the uncomfortable truth that embassy ATMs, diplomatic pouches, and cash-for-visas schemes […]
Uncovering Encrypted Protest Chatter Before Flashpoints Ignite

If you work in government or intelligence, you already know the nightmare: encrypted protest chatter spikes on Telegram, Signal, and closed Discord servers, and forty-eight hours later the Capitol—or the local parliament square—is on fire. The bad guys plan in the open, but they do it behind encryption stickers and disappearing stories. That means your […]
Tracking Shadow Donors Bankrolling Election Violence
Let me cut through the fluff: if you are an investigative journalist still relying on leaked PDFs and anonymous tips alone, you are bringing a butter knife to a gunfight. Election violence funding moves at the speed of crypto, Telegram channels vanish in minutes, and shell companies breed faster than rabbits on Red Bull. The […]
Did OSINT Miss the Stealth Frigate Heading for Taiwan?

The word on the street—well, the open digital street anyway—is that a stealth frigate might be slipping past radar and intel headed straight for Taiwan. The buzz: Did our open source intelligence pipelines drop the ball? In a world where stealth surface vessels are becoming craftier, OSINT’s role in stealth frigate detection is more critical […]
After Cloudflare Outage, Are Government DNS Defenses Ready?

Government & intelligence agencies, if the recent Cloudflare outage didn’t jolt you awake, I don’t know what will. When the internet’s backbone trembles, so do critical state operations that rely on Domain Name System (DNS) infrastructures. The big question is: in 2025, with all the chatter about modernization and cyber resilience, how ready are your […]
The Hidden Cost of Intelligence Work: Why OSINT Analyst Burnout Is a National Security Issue

At 3 AM on a Tuesday, a senior intelligence analyst submitted her resignation. She’d spent eight years building expertise in counterterrorism, earned commendations for critical threat assessments, and trained dozens of junior analysts. Her reason for leaving? “I can’t unsee what I’ve seen anymore.” This isn’t an isolated incident. OSINT analyst burnout has become one […]
The Attention Economy of OSINT – Managing Credibility and Risk in High-Velocity Intelligence

I am going to be straight with you: modern open source intelligence is a battlefield for attention. Signals flash, social posts amplify, and every analyst in the loop faces two relentless forces: the pressure to move fast and the duty to be right. If you are a Special Agent, Cyber Crime Unit Lead, or Senior […]
Orchestrating Cross-Agency OSINT Collaboration to Break Intelligence Silos

Alright, listen up, government & intelligence agency folks: if your intel is as fragmented as a jigsaw puzzle missing half the pieces, you’re in the right place. In a world where threats evolve faster than your morning coffee can kick in, breaking down these intelligence silos through effective cross-agency OSINT collaboration isn’t just a nice-to-have—it’s […]
The Clock Just Ran Out on Government Cyber Collaboration

The CISA expiration in October 2025 threatens government cybersecurity collaboration. Learn how to build resilient information-sharing frameworks without legal protections.
How Intelligence Agency OSINT Workflow Automation Accelerates National Security Operations

Intelligence agencies face an unprecedented challenge. Digital threats multiply faster than human analysts can process them, and the volume of open source intelligence continues to grow exponentially. Special agents, cyber crime unit leads, and senior intelligence analysts need systematic approaches that maintain security clearances while accelerating investigations. The traditional manual approach to OSINT collection creates […]
AI-Powered Deception: How LLM Honeypots Transform Threat Intel
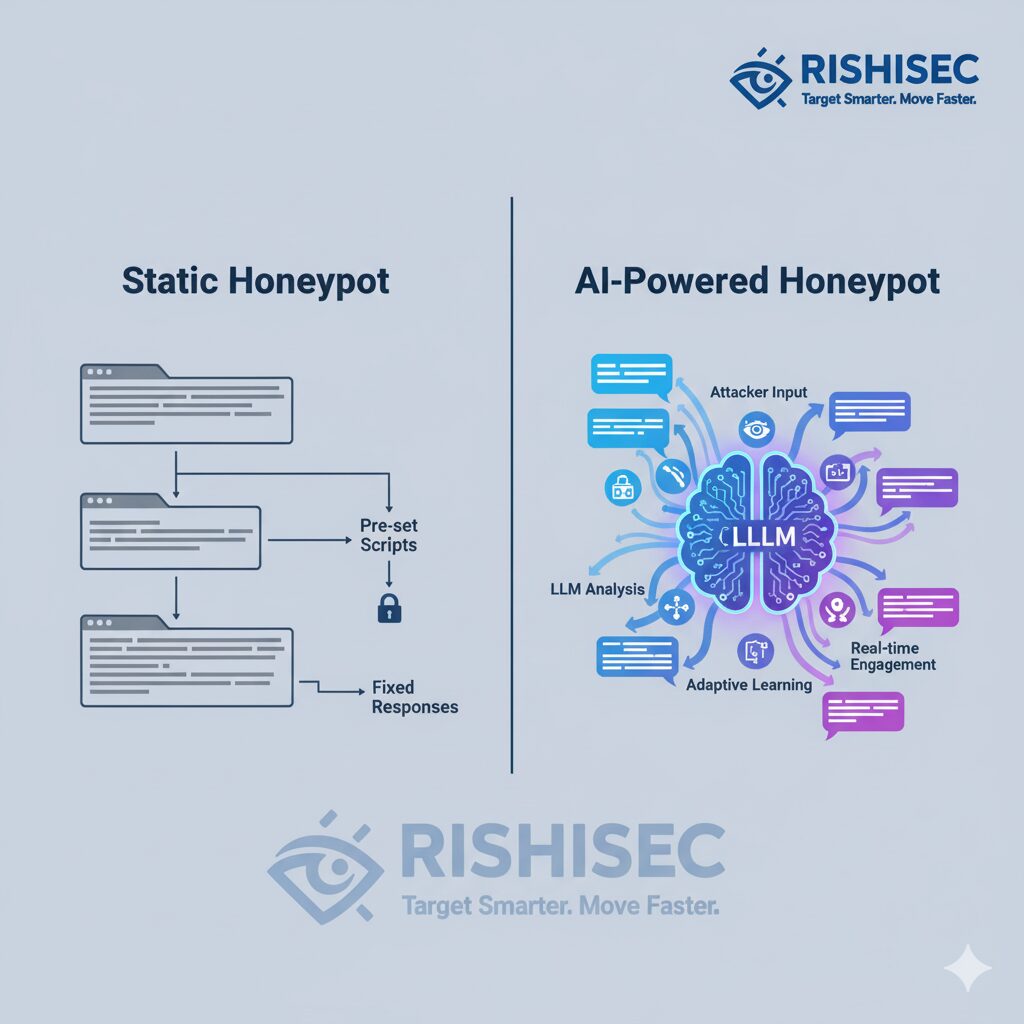
Discover how AI-powered honeypots with LLM technology are revolutionizing threat intelligence gathering, enabling SOC teams to outsmart attackers with dynamic deception.
Beyond Surveillance: How OSINT Fusion is Transforming Counterterrorism Intelligence Operations

Legacy surveillance frameworks were built for a different era. They assumed that terror networks communicated through interceptable channels, were organized into identifiable cells, and operated within geographic boundaries that intelligence agencies could monitor. These assumptions no longer hold. Modern terrorism has digitized, decentralized, and adapted to evade traditional collection methods, creating visibility gaps that threaten […]
Why Traditional Intelligence Collection Methods Are Failing Modern Threat Environment

Intelligence agencies face an uncomfortable reality: traditional collection methods designed for Cold War adversaries cannot keep pace with today’s digital threat landscape. Special agents and senior intel analysts working in government agencies increasingly discover critical intelligence gaps only after operational failures occur. The problem isn’t a lack of effort or expertise; it’s a fundamental mismatch […]
Why Generic Threat Intelligence No Longer Supports Strategic Intelligence Operations

Government intelligence operations face increasingly sophisticated adversaries who understand surveillance techniques, employ advanced operational security, and deliberately manipulate their digital footprints to deceive analysts. Generic threat intelligence that treats all actors within a category as interchangeable fails to capture the nuanced behaviors, capabilities, and intentions that distinguish specific threats. Special agents and senior intel analysts […]
Legislative Changes Reshaping Intelligence Operations
The 2025 Intelligence Authorization Act represents the most significant transformation of open-source intelligence operations in decades. Congressional leaders are implementing sweeping House Intel Bill 2025 OSINT reforms that fundamentally change how intelligence agencies collect, procure, and manage open-source data across the intelligence community. These changes extend far beyond minor policy adjustments, creating structural reforms in […]
OSINT deception risks: How to overcome them
The explosion of open-source intelligence has fundamentally transformed how intelligence professionals gather and analyze information. However, this unprecedented access to data brings a hidden danger that threatens the foundation of analytical integrity. OSINT deception risks are escalating as adversaries become more sophisticated in manipulating publicly available information to mislead investigators and decision-makers. Intelligence analysts today […]
How OSINT Powers Geopolitical Strategy and Foreign Relations
Geopolitical landscapes shift rapidly in our interconnected world. Furthermore, traditional diplomatic intelligence often arrives too late to inform critical policy decisions. This reality has transformed OSINT geopolitical intelligence gathering from a supplementary tool into an essential component of foreign relations strategy. From satellite imagery revealing military buildups to social media posts predicting political unrest, open-source […]
Why OSINT is Critical in Modern Counterterrorism

Today’s terrorism and espionage threats don’t operate in isolation. Moreover, they leave digital footprints across social media platforms, public databases, and online forums. Consequently, government agencies worldwide are discovering that classified intelligence alone isn’t enough to stay ahead of evolving threats. This is where OSINT counterterrorism intelligence analysis becomes a game-changer. Open Source Intelligence (OSINT) […]
Election Forensics & Social Signals: Advanced OSINT Techniques for Government Intelligence

Election security has become one of the most critical challenges facing modern democracies. Consequently, government intelligence agencies must now deploy sophisticated Open Source Intelligence capabilities to monitor, detect, and counter threats to electoral integrity. Furthermore, the 2020 and 2024 U.S. elections demonstrated how rapidly disinformation campaigns can spread across digital platforms, making election forensics OSINT […]
OSINT Strategy: Essential Intelligence Frameworks Government Agencies Must Master

Furthermore, modern threats operate across digital boundaries, making government intelligence OSINT strategies more crucial than ever. From tracking state-sponsored cyber campaigns to monitoring terrorist recruitment networks, intelligence professionals need sophisticated approaches that can adapt to rapidly changing threat environments. Government intelligence agencies face an unprecedented challenge in today’s digital landscape. Moreover, with over 4.9 billion […]
