Security Operations Centers (SOCs) are drowning in alerts. The average SOC analyst faces over 4,000 alerts daily, with alert fatigue leading to missed threats and burnout. Traditional Security Orchestration, Automation, and Response (SOAR) platforms promised relief, but many fell short due to rigid playbooks and limited intelligence. Enter 2025’s game-changer: AI-powered SOAR platforms that don’t just automate—they think, learn, and adapt.
The integration of artificial intelligence and machine learning into SOAR technology is fundamentally transforming how security teams handle alert triage. Instead of drowning in false positives, SOC analysts can now focus on genuine threats while AI handles the noise. This isn’t just incremental improvement—it’s a paradigm shift in security operations.
In this comprehensive guide, we’ll explore how AI-powered SOAR platforms are revolutionizing alert triage, the tangible benefits they deliver, and how your organization can implement them effectively.
The Alert Overload Crisis in Modern SOCs
Understanding the Scale of the Problem
Modern security infrastructure generates an overwhelming volume of alerts. Between SIEM systems, EDR solutions, network monitoring tools, and cloud security platforms, SOC teams face an impossible task: reviewing every alert while maintaining rapid response times.
The consequences are severe:
- Alert fatigue leads to decreased analyst performance and increased turnover
- Critical threats get buried in noise, extending dwell time
- Manual triage consumes 60-70% of analyst time on repetitive tasks
- Inconsistent prioritization results in misallocated resources
Traditional SOAR platforms attempted to address this through basic automation, but their rule-based approach couldn’t adapt to evolving threats or handle the nuanced decision-making required for effective triage.

How AI Transforms SOAR Platform Capabilities
Intelligent Alert Correlation and Contextualization
AI-powered SOAR platforms leverage machine learning algorithms to correlate alerts across multiple security tools, identifying patterns that human analysts might miss. Unlike traditional correlation rules that require manual configuration, AI models continuously learn from historical data and adapt to new threat patterns.
Key capabilities include:
- Behavioral analysis that identifies anomalies based on entity behavior rather than static rules
- Threat actor attribution using pattern recognition across global threat intelligence
- Automated context enrichment pulling relevant data from OSINT sources and internal systems
- Dynamic risk scoring that adjusts based on organizational context and current threat landscape
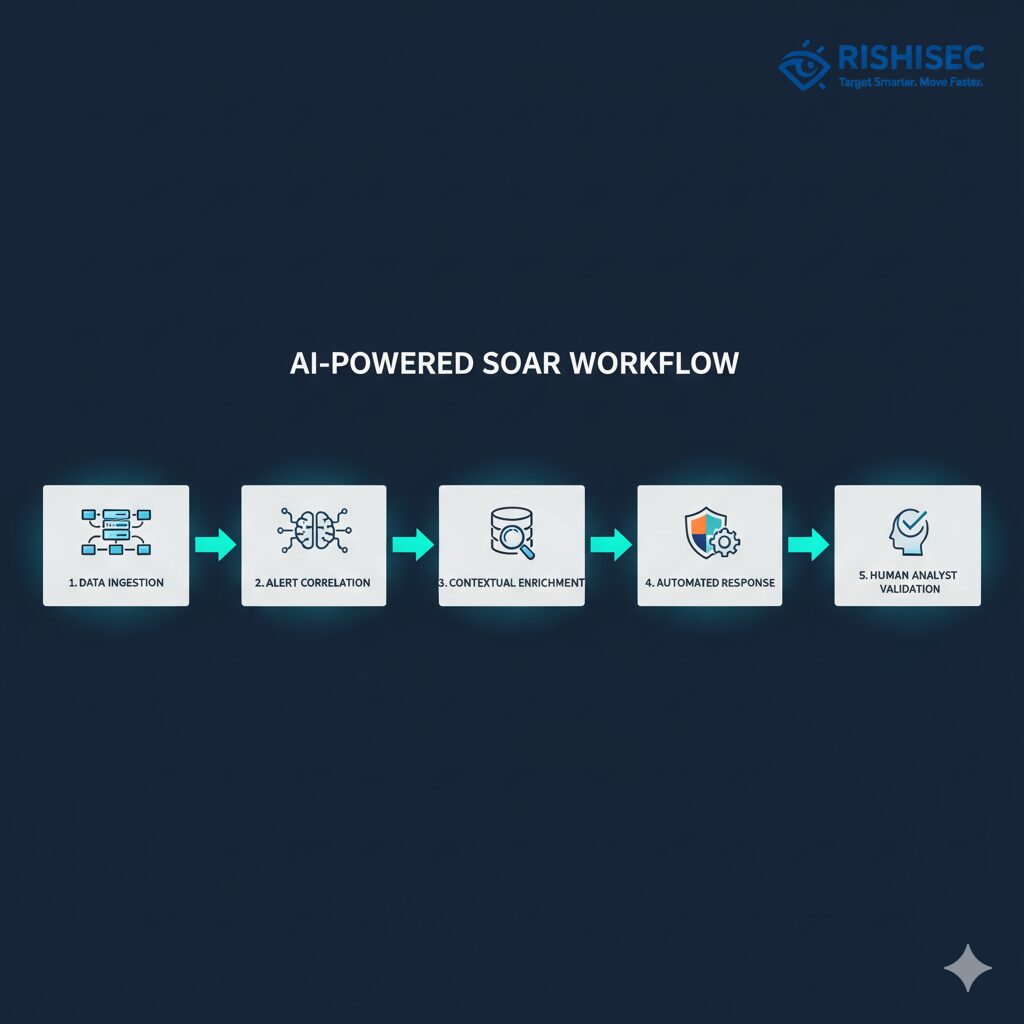
Predictive Threat Prioritization
The most significant advancement in AI-powered SOAR is predictive prioritization. Rather than relying solely on CVSS scores or predefined severity levels, AI models analyze multiple factors to predict which alerts represent genuine threats requiring immediate attention.
These systems consider:
- Historical incident data and outcomes
- Asset criticality and business context
- Current threat intelligence and campaign activity
- Attacker tactics, techniques, and procedures (TTPs)
- Environmental factors and security posture
This intelligent prioritization ensures that analysts focus on alerts most likely to represent real threats, dramatically reducing time-to-detection and response.
Adaptive Playbook Execution
Traditional SOAR playbooks are static—they execute the same steps regardless of context. AI-powered platforms introduce adaptive playbooks that modify their execution based on real-time analysis and learning from previous incidents.
For example, when investigating a potential phishing incident, an AI-powered SOAR might:
- Analyze email headers and content using natural language processing
- Check sender reputation across multiple threat intelligence sources
- Identify similar emails across the organization
- Assess user risk based on role and previous security awareness training
- Automatically adjust response actions based on threat confidence level
This adaptability ensures appropriate responses without requiring constant playbook maintenance.
Real-World Benefits: Measurable Impact on SOC Operations
Dramatic Reduction in Alert Volume
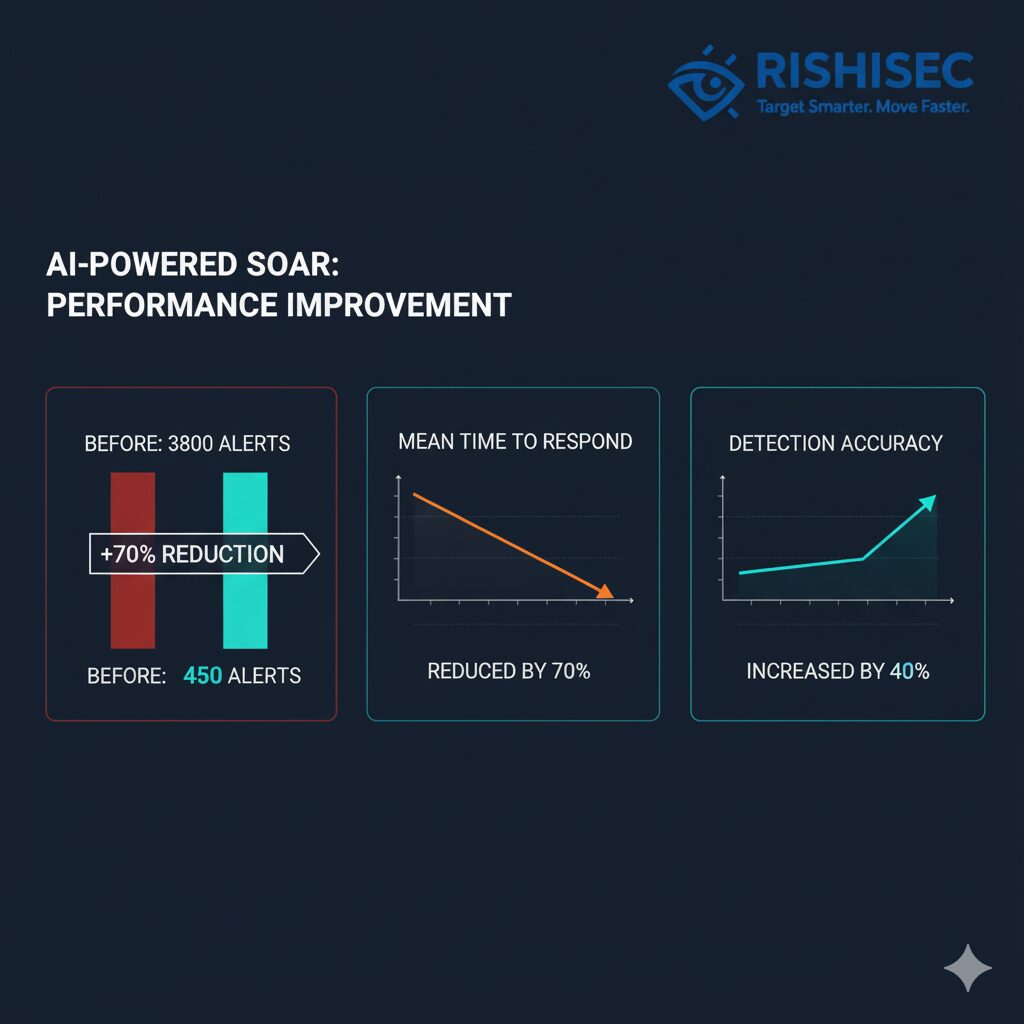
Organizations implementing AI-powered SOAR platforms report 60-80% reductions in alerts requiring human review. By automatically dismissing confirmed false positives and consolidating related alerts into single incidents, these platforms allow analysts to focus on meaningful work.
One Fortune 500 financial institution reduced their daily alert queue from 3,800 to 450 alerts after implementing AI-powered triage—a 88% reduction that transformed their SOC operations.
Faster Mean Time to Respond (MTTR)
AI-powered automation accelerates every phase of incident response. Automated enrichment, correlation, and initial containment actions can execute in seconds rather than hours. Organizations typically see 50-70% reductions in MTTR after implementation.
More importantly, AI ensures consistent response quality regardless of analyst experience level or time of day, eliminating the variability that plagues many SOC operations.
Enhanced Threat Detection Accuracy
By correlating signals across multiple security tools and applying behavioral analysis, AI-powered SOAR platforms identify threats that traditional approaches miss. This is particularly valuable for detecting sophisticated attacks that evade individual security controls.
Organizations report 30-40% increases in threat detection rates, particularly for advanced persistent threats (APTs) and insider threats that require behavioral analysis to identify.
Improved Analyst Productivity and Satisfaction
Perhaps the most underappreciated benefit is the impact on SOC analysts themselves. By eliminating repetitive triage tasks and providing clear, contextualized alerts, AI-powered SOAR platforms allow analysts to focus on investigation and threat hunting—the work they find most engaging.
Organizations report significant improvements in analyst retention and job satisfaction, with many seeing 40-50% reductions in turnover after implementation.
Integration with Advanced OSINT Capabilities
Modern AI-powered SOAR platforms excel when integrated with comprehensive OSINT capabilities. Platforms like Kindi provide the external threat intelligence and context that AI models need to make accurate triage decisions.
This integration enables:
- Automated threat actor profiling using social media intelligence and dark web monitoring
- Credential leak detection that triggers immediate response workflows
- Brand impersonation identification for phishing and fraud prevention
- Supply chain risk assessment based on third-party security posture
By combining internal security telemetry with external intelligence, AI-powered SOAR platforms gain the comprehensive visibility needed for accurate threat assessment. This approach aligns with best practices for integrating OSINT to prioritize alerts in modern security operations.
Implementation Best Practices
Start with Clear Use Cases
Don’t attempt to automate everything at once. Identify high-volume, repetitive triage tasks that consume significant analyst time. Common starting points include:
- Phishing email triage and response
- Endpoint alert correlation and investigation
- Vulnerability prioritization and remediation workflow
- User behavior anomaly investigation
Ensure Quality Training Data
AI models are only as good as their training data. Before implementation:
- Clean and normalize historical incident data
- Document incident outcomes and analyst decisions
- Establish consistent alert classification and severity standards
- Create feedback loops for continuous model improvement
Maintain Human Oversight
AI-powered automation should augment, not replace, human analysts. Implement appropriate oversight mechanisms:
- Require analyst approval for high-impact actions
- Establish confidence thresholds for automated decisions
- Create escalation paths for edge cases
- Regularly review automated decisions for accuracy
Integrate with Existing Security Stack
Successful AI-powered SOAR implementation requires seamless integration with your existing security tools. Prioritize platforms that offer:
- Pre-built integrations with major security vendors
- Flexible API frameworks for custom integrations
- Bidirectional data sharing capabilities
- Support for industry-standard formats (STIX, TAXII, etc.)
Understanding the critical role of SOC visibility is essential for effective integration planning.
Overcoming Common Implementation Challenges
Managing False Positive Rates During Initial Deployment
AI models require time to learn your environment. During initial deployment, expect higher false positive rates as models calibrate. Mitigate this by:
- Starting with conservative automation thresholds
- Implementing gradual rollout across alert types
- Maintaining detailed feedback mechanisms
- Scheduling regular model tuning sessions
Addressing Analyst Trust and Adoption
Analysts may be skeptical of AI-driven decisions, particularly if they’ve experienced failed automation projects. Build trust through:
- Transparent decision-making with clear explanations
- Gradual expansion of automation scope
- Regular demonstrations of value and accuracy
- Involving analysts in playbook development and tuning
Ensuring Compliance and Auditability
Automated decision-making must meet regulatory requirements. Ensure your platform provides:
- Complete audit trails of all automated actions
- Explainable AI capabilities that document decision rationale
- Role-based access controls and approval workflows
- Compliance reporting aligned with relevant frameworks
The Future of AI-Powered SOC Operations
The evolution of AI in security operations is accelerating. Emerging capabilities on the horizon include:
Autonomous Threat Hunting: AI systems that proactively search for threats based on hypothesis generation and testing, moving beyond reactive alert response.
Predictive Security Posture Management: Models that forecast likely attack vectors based on organizational changes, threat landscape evolution, and security control effectiveness.
Natural Language Incident Investigation: Conversational AI interfaces that allow analysts to investigate incidents through natural language queries, dramatically reducing investigation time.
Cross-Organizational Threat Intelligence: Federated learning models that improve detection accuracy by learning from anonymized data across multiple organizations without compromising confidentiality.
Organizations that embrace AI-powered SOAR now will be positioned to leverage these advanced capabilities as they mature, maintaining competitive advantage in an increasingly challenging threat landscape.
Conclusion
AI-powered SOAR platforms represent a fundamental shift in how SOCs handle alert triage and incident response. By combining intelligent automation with adaptive learning, these platforms address the alert overload crisis while improving detection accuracy and analyst productivity.
The benefits are clear: dramatic reductions in alert volume, faster response times, improved threat detection, and enhanced analyst satisfaction. Organizations that implement AI-powered SOAR effectively gain significant operational advantages and security improvements.
Success requires thoughtful implementation, starting with clear use cases, ensuring high-quality training data, maintaining human oversight, and integrating with existing security infrastructure. When combined with comprehensive OSINT capabilities like those provided by Kindi, AI-powered SOAR platforms deliver the visibility and intelligence needed for effective security operations in 2025 and beyond.
The question isn’t whether to adopt AI-powered SOAR, but how quickly you can implement it to stay ahead of evolving threats and operational demands. The SOCs that thrive in the coming years will be those that successfully harness AI to augment human expertise, creating security operations that are both more efficient and more effective.

