
Defense contractors face an unprecedented challenge: protecting complex global supply chains that span hundreds of vendors, multiple countries, and countless potential vulnerabilities. Traditional periodic audits and compliance checks are no longer sufficient to defend against sophisticated adversaries who increasingly target supply chain weaknesses to compromise defense systems and steal critical information. To stay ahead of these threats, many are now turning to supply chain security intelligence, a proactive strategy for identifying, analyzing, and mitigating risks before they escalate.
The Evolving Threat Landscape
Modern defense supply chains have evolved into intricate global networks involving thousands of suppliers, subcontractors, and service providers across multiple jurisdictions. This complexity creates numerous attack vectors that adversaries can exploit to compromise defense systems, steal intellectual property, or disrupt military operations.
State-sponsored threat actors represent the most sophisticated danger, conducting sustained campaigns targeting defense contractors and their supplier networks. These advanced persistent threat (APT) groups employ complex techniques, including supply chain infiltration, social engineering, and zero-day exploits, to achieve long-term access to defense networks and sensitive information.
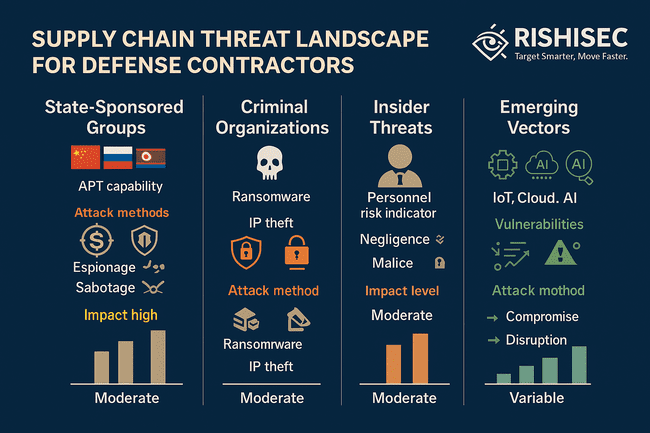
Criminal organizations increasingly target defense supply chains for financial gain, often selling stolen information to state-sponsored actors. Ransomware attacks against suppliers can cascade through defense networks, while intellectual property theft operations target valuable defense technologies and operational information.
Insider threats within supplier organizations present particularly challenging risks, as trusted individuals with legitimate access can bypass traditional security controls.
The Intelligence Advantage
Supply chain security intelligence transforms reactive vendor management into proactive threat identification and risk mitigation. This approach provides several critical advantages over traditional security assessments.
Speed and Timeliness: Intelligence-driven approaches provide real-time monitoring capabilities that identify threats and risks as they emerge, rather than waiting for periodic assessments or incident reports. This speed enables proactive response measures that can prevent or minimize security incidents.
Comprehensive Visibility: Advanced intelligence platforms can monitor hundreds of suppliers simultaneously, tracking changes in business operations, security posture, and threat exposure that might indicate emerging risks. This visibility extends beyond direct suppliers to include sub-tier suppliers and service providers.
Predictive Capabilities: By analyzing historical patterns, current indicators, and threat intelligence, advanced analytics can predict future risk scenarios and identify suppliers likely to experience security incidents or operational disruptions.
OSINT Sources for Supply Chain Intelligence
Practical supply chain security intelligence leverages diverse information sources to build a comprehensive understanding of supplier operations, threat landscapes, and risk factors.
Corporate Intelligence involves systematic collection and analysis of business information, including corporate registrations, financial reports, executive leadership changes, and business relationship networks. This intelligence helps identify potential conflicts of interest, financial instability, or problematic business associations that could create security risks.
Technical Intelligence examines supplier technical capabilities, research activities, and intellectual property portfolios through patent analysis, academic publications, and technical standards compliance. This intelligence helps assess supplier capabilities and identify potential technology dependencies or vulnerabilities.
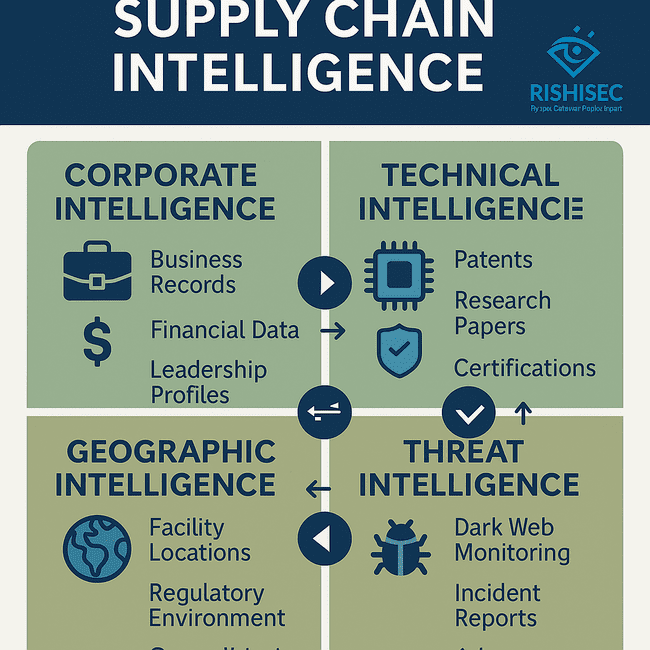
Geographic and Regulatory Intelligence provides essential context about the political, economic, and regulatory environments in which suppliers operate.
Threat Intelligence focuses on adversary activities, security incidents, and emerging attack techniques that could affect defense supply chains. This includes dark web monitoring for stolen credentials or criminal marketplace activities, security incident tracking, and threat actor analysis.
Advanced Analytical Techniques
Modern supply chain security intelligence employs sophisticated analytical methodologies that transform raw information into actionable intelligence products supporting risk-based decision-making.
Network Analysis creates comprehensive visualizations of supplier relationships and dependencies, revealing critical pathways and potential single points of failure within complex supply chains. This analysis helps identify suppliers whose compromise could have cascading effects throughout the defense contractor’s operations.
Risk Scoring and Prioritization uses multi-dimensional assessment frameworks that consider supplier criticality, threat exposure, security posture, and potential impact of disruption or compromise. These scoring systems enable defense contractors to allocate security resources effectively by focusing on the highest-priority risks.
Predictive Analytics leverages machine learning algorithms and historical data to forecast emerging risks and potential threat scenarios. These analytics help defense contractors anticipate future challenges and implement proactive risk mitigation measures.
Technology Platforms and Integration
Implementing adequate supply chain security intelligence requires sophisticated technology platforms that can collect, process, and analyze vast amounts of information while integrating with existing business systems.</p>
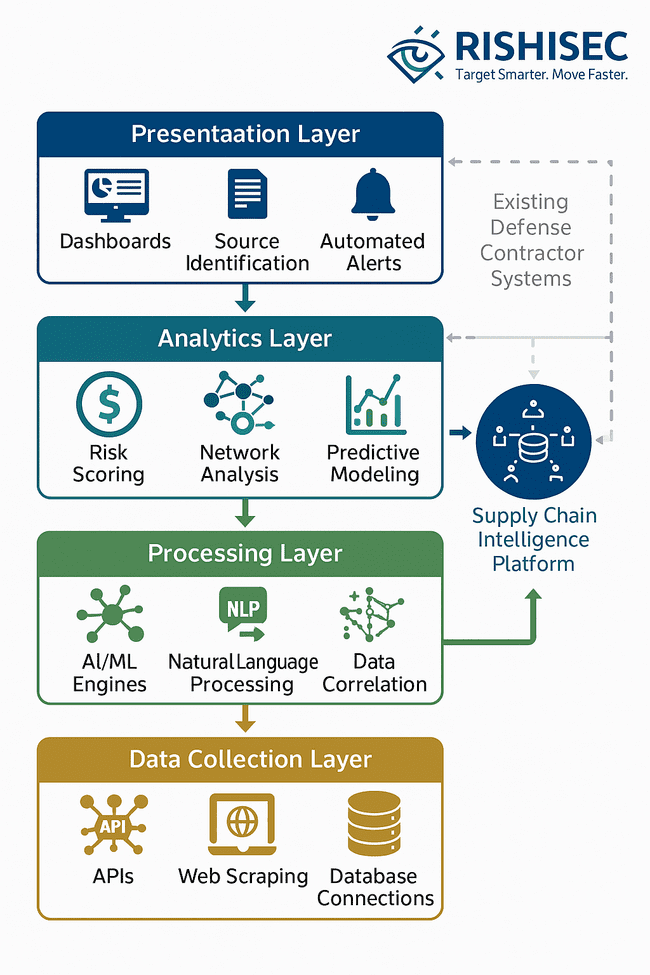
Automated Collection Systems gather information from hundreds of sources simultaneously, including corporate databases, regulatory filings, news sources, and social media platforms. These systems must handle various data formats and languages while maintaining operational security and avoiding detection by adversaries.
Advanced Analytics Engines use artificial intelligence and machine learning to identify patterns, assess risks, and generate intelligence insights from large datasets. These engines must be trained on relevant defense industry data and continuously updated to maintain accuracy and effectiveness.
Integration Capabilities connect supply chain intelligence platforms with existing defense contractor systems, including ERP systems, supplier management platforms, and security monitoring tools. This integration ensures that intelligence insights are available where and when needed for decision-making.
Platforms like Kindi provide defense contractors with comprehensive supply chain intelligence capabilities specifically designed for security applications. Kindi’s intelligent investigation agents can automatically trace supplier relationships and identify potential risks.
Vendor Risk Assessment and Monitoring
Supplier Profiling involves the systematic collection of information about suppliers’ business operations, financial stability, technical capabilities, and security posture. This profiling provides the foundation for risk assessments and ongoing monitoring activities.
Continuous Monitoring systems track changes in supplier status, security incidents, and risk factors using automated tools and analytical techniques. This monitoring provides early warning of potential problems and enables proactive risk mitigation measures.
Dynamic Risk Assessment adjusts supplier risk scores based on changing conditions, new threat intelligence, and evolving business relationships. This dynamic approach ensures that risk assessments remain current and accurate despite rapidly changing conditions.
Geographic and Geopolitical Risk Analysis</h2>
Defense supply chains span multiple countries and regions, each with distinct threat landscapes, regulatory environments, and operational challenges that must be understood and managed effe
ctively.</p>
<strong>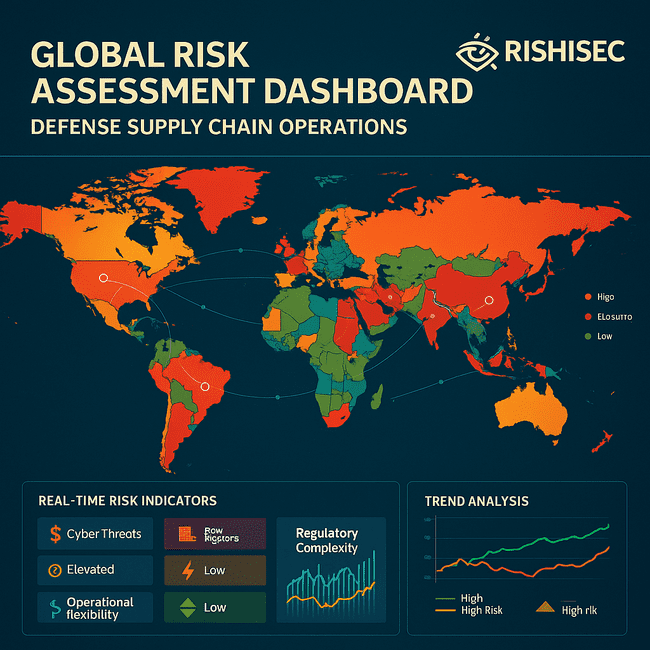
Country-Level Risk Assessment examines political stability, regulatory environments, cybersecurity capabilities, and threat actor presence in countries where suppliers operate. This assessment helps identify locations with elevated risk levels and inform supply chain configuration decisions.
Geopolitical Intelligence Integration monitors international relations, trade policies, and sanctions regimes that could affect supplier relationships or create new compliance requirements. This intelligence is essential for maintaining regulatory compliance and avoiding legal risks.
Transportation and Infrastructure Security analyzes the security of shipping lanes, airports, and ground transportation networks used for defense-related materials. This analysis identifies potential chokepoints and vulnerability areas that could affect supply chain operations.
Implementation and Best Practices
Successful implementation of supply chain security intelligence requires systematic approaches that address organizational, technical, and operational requirements.
Phased Implementation begins with foundation building including organizational structure development, baseline supplier assessments, and basic monitoring capabilities. Subsequent phases add advanced analytics, comprehensive monitoring, and full business process integration.
Cross-Functional Integration ensures that supply chain security intelligence supports procurement, contract management, and operational planning processes. This integration requires collaboration among security, procurement, and business operations teams.
Regulatory Compliance addresses government requirements including DFARS cybersecurity provisions, NISPOM security standards, and CMMC certification requirements. Compliance programs must incorporate intelligence gathering and reporting activities specified by these regulations.
Measuring Program Effectiveness
Comprehensive evaluation frameworks measure program effectiveness across multiple dimensions and provide objective assessments that support continuous improvement efforts.
Operational Metrics evaluate intelligence product quality, timeliness, and relevance while measuring customer satisfaction and operational impact. These metrics help optimize program performance and demonstrate value to stakeholders.
Risk Reduction Assessment measures the program’s effectiveness in identifying and mitigating supply chain security risks, including threat detection rates, incident prevention, and successful risk mitigation activities.</p>
<strong>Return on Investment Analysis compares program costs with achieved benefits, including cost avoidance, operational efficiency improvements, and enhanced security capabilities.
The Strategic Imperative
Supply chain security intelligence represents more than just enhanced vendor management. it’s a strategic transformation that enables defense contractors to protect critical capabilities while maintaining competitive advantages in an increasingly complex threat environment.</p>
The integration of advanced OSINT platforms with proven intelligence methodologies creates powerful capabilities for understanding and managing supply chain risks. Organizations that implement comprehensive supply chain security intelligence programs today will be better positioned to protect their operations, maintain customer trust, and support national security objectives.</p>
For defense contractors ready to transform their approach to supply chain security, professional platforms like Kindi provide the technological foundation necessary to implement sophisticated intelligence capabilities. Kindi’s automated investigation features, real-time monitoring capabilities, and visual analysis tools enable defense teams to achieve comprehensive supply chain visibility while maintaining operational efficiency.</p>
“post-13411-_wjbp6ruhisu3”>Ready to Secure Your Defense Supply Chain?
The frameworks, methodologies, and implementation strategies covered in this article represent the foundation of what’s possible with comprehensive supply chain security intelligence programs. Defense contractors worldwide are discovering that the right combination of intelligence methodology, advanced technology, and systematic implementation can revolutionize their approach to supply chain risk management.</p>
<strong>Download our complete 4,000-word implementation guide: “Supply Chain Security Intelligence: How Defense Contractors Identify Threats in Global Defense Networks – The Complete Strategic Guide”</p>
This comprehensive resource includes:
- ✅ Detailed threat actor analysis and attack vector assessments
- ✅ Step-by-step implementation roadmaps for defense organizations
- ✅ Advanced analytical methodologies and risk scoring frameworks
- ✅ Technology evaluation criteria and platform integration strategies
- ✅ Regulatory compliance guidelines and reporting procedures
- ✅ Continuous monitoring protocols and incident response procedures
Transform your supply chain security posture. Get the complete guide and start building your organization’s supply chain intelligence capabilities today.
[DOWNLOAD THE COMPLETE GUIDE]
This article provides strategic insights into supply chain security intelligence based on extensive research and analysis of successful defense programs. For organizations seeking to implement or enhance their supply chain security capabilities, professional platforms like Kindi can accelerate development timelines while ensuring operational effectiveness and regulatory compliance.


