Human rights OSINT investigations represent a fundamental shift in how we document violations, pursue accountability, and seek justice for victims worldwide. Furthermore, these digital techniques enable investigators to uncover evidence that traditional methods might miss entirely. Additionally, the democratization of investigation tools means that human rights organizations, regardless of size, can now conduct sophisticated investigations.
Open Source Intelligence has transformed human rights work from reactive documentation to proactive investigation. Moreover, OSINT enables the verification of claims independently, establishes timelines with precision, and builds compelling evidence chains that courts and tribunals can accept. Consequently, human rights OSINT investigations have become essential tools for accountability in conflicts, protests, and systematic violations occurring globally.
The stakes for accurate documentation have never been higher. However, with great investigative power comes the responsibility to maintain ethical standards while ensuring that evidence meets legal requirements for accountability proceedings.
Essential OSINT Sources for Human Rights Investigations
Effective human rights OSINT investigations require systematic collection from diverse sources that provide complementary perspectives on events. Therefore, investigators must understand which sources offer the most reliable evidence for specific types of violations.
Social Media and User-Generated Content
Social media platforms serve as primary sources for real-time documentation of human rights violations. Nevertheless, investigators must navigate platform limitations, content removal policies, and the challenge of verifying user-generated content authenticity.
Key social media sources include:
- Twitter/X for real-time updates and eyewitness accounts during unfolding events
- Facebook groups and pages that document local incidents and community responses
- Instagram stories and posts that capture visual evidence of violations
- TikTok videos that often provide unfiltered perspectives from affected communities
- Telegram channels used by activists and citizen journalists in restrictive environments
Similarly, messaging platforms like WhatsApp, Signal, and local alternatives often contain critical evidence, though access requires careful ethical consideration and source protection protocols.
Satellite Imagery and Geospatial Intelligence
Satellite imagery provides objective documentation of large-scale violations such as mass displacement, infrastructure destruction, and environmental damage. Additionally, commercial satellite providers now offer historical imagery that enables before-and-after analysis of alleged violation sites.
Essential satellite imagery sources include:
| Source | Resolution | Coverage | Best Use Cases |
|---|---|---|---|
| Google Earth | 0.5-2.5 meters | Global, historical | Infrastructure analysis, displacement verification |
| Maxar/DigitalGlobe | 0.3-0.5 meters | On-demand, recent | Detailed damage assessment, current conditions |
| Planet Labs | 3-5 meters | Daily global coverage | Change detection, temporal analysis |
| Sentinel/Copernicus | 10 meters | Free, regular updates | Large-scale monitoring, environmental violations |
Furthermore, specialized analysis tools like QGIS, Google Earth Engine, and commercial platforms enable investigators to perform sophisticated geospatial analysis without extensive technical backgrounds.
Official Records and Government Data
Government databases, court records, and official statements provide crucial context for human rights investigations. However, investigators must account for potential bias, censorship, or deliberate misinformation in official sources.
Key official sources include:
- Legislative records and parliamentary proceedings that reveal policy intentions
- Court documents and legal filings that establish official timelines
- Police reports and incident records, when accessible
- Budget documents that show resource allocation for security forces
- Procurement records that reveal equipment purchases by state actors
Cross-referencing official records with independent sources helps establish comprehensive timelines while identifying discrepancies that may indicate cover-ups or misinformation campaigns.
Verification Standards and Ethical Guidelines
Human rights OSINT investigations demand rigorous verification standards that ensure evidence integrity while protecting sources and subjects. Moreover, ethical considerations must guide every aspect of the investigation process to prevent harm and maintain credibility.
Core Verification Principles
Effective verification requires systematic application of multiple authentication methods. Therefore, investigators should never rely on single sources or verification techniques for critical evidence.
Essential verification steps include:
- Source authentication: Verify the identity and credibility of content creators
- Content verification: Confirm that images and videos are authentic and unmanipulated
- Geolocation confirmation: Establish precise locations using multiple reference points
- Timestamp validation: Verify when content was created versus when it was shared
- Cross-referencing: Confirm details across multiple independent sources
Additionally, investigators should document their verification process thoroughly to ensure that evidence chains remain intact for potential legal proceedings.
International Standards and Frameworks
The Berkeley Protocol on Digital Open Source Investigations provides the gold standard for human rights OSINT work. Furthermore, this framework establishes minimum standards for evidence collection, verification, and preservation that courts increasingly expect.
Key Berkeley Protocol requirements include:
- Systematic documentation of all investigative steps and decisions
- Clear chain of custody procedures for digital evidence
- Verification protocols that meet legal admissibility standards
- Ethical guidelines that protect sources and prevent harm to subjects
Similarly, the Istanbul Protocol provides specific guidance for investigating torture and ill-treatment, while the Minnesota Protocol addresses extrajudicial killings and enforced disappearances.
Understanding OSINT techniques for journalists and human rights organizations helps investigators apply these frameworks effectively in real-world scenarios.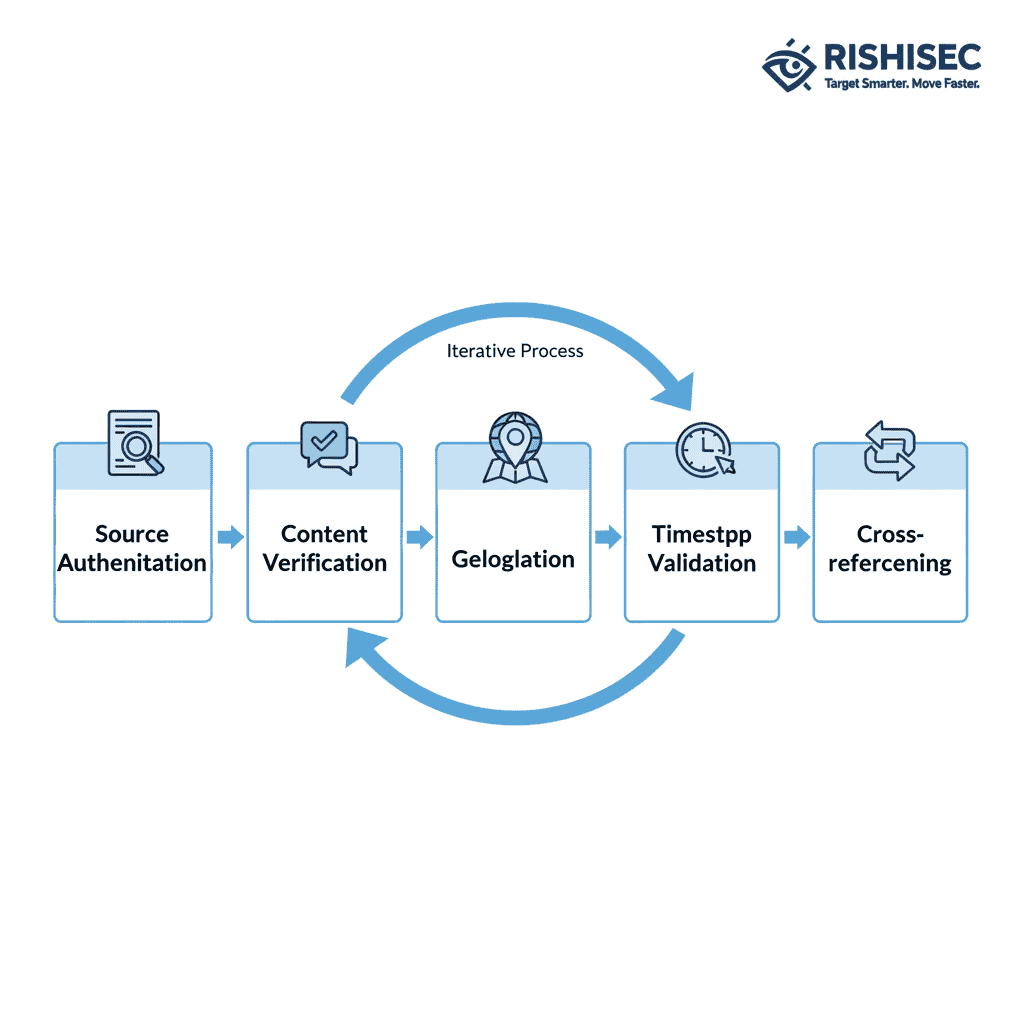
Systematic Workflow for Human Rights OSINT Projects
Successful human rights OSINT investigations follow structured workflows that ensure comprehensive evidence collection while maintaining ethical standards. Therefore, investigators should establish clear protocols before beginning collection activities.
Planning and Hypothesis Development
Effective investigations begin with clear objectives and testable hypotheses. Moreover, thorough planning prevents scope creep while ensuring that investigators collect relevant evidence systematically.
Essential planning elements include:
- Defining specific research questions and success metrics
- Identifying potential sources and collection strategies
- Establishing verification protocols and quality standards
- Creating security procedures for sensitive investigations
- Developing timelines and resource allocation plans
Furthermore, investigators should consider potential legal requirements early in the planning process to ensure that evidence collection methods meet admissibility standards.
Data Collection and Documentation
Systematic data collection requires both technical tools and organizational discipline. Additionally, investigators must balance comprehensive collection with ethical considerations and source protection requirements.
Key collection principles include:
- Comprehensive documentation: Record all sources, methods, and timestamps
- Evidence preservation: Maintain original formats and metadata
- Chain of custody: Track evidence handling throughout the investigation
- Quality control: Implement peer review and verification checkpoints
- Security measures: Protect sensitive information and source identities
Modern investigations increasingly rely on automated collection tools, though human oversight remains essential for quality control and ethical compliance.
Analysis and Verification Processes
Thorough analysis transforms raw data into actionable intelligence while verification ensures evidence integrity. Consequently, investigators must apply systematic analytical frameworks that produce reliable conclusions.
The analysis workflow includes:
| Analysis Stage | Key Activities | Quality Controls | Documentation Requirements |
|---|---|---|---|
| Initial Review | Content categorization, preliminary assessment | Peer review, bias checking | Source tracking, quality ratings |
| Technical Verification | Metadata analysis, authenticity testing | Multiple verification methods | Technical reports, tool outputs |
| Contextual Analysis | Timeline construction, pattern identification | Cross-referencing, expert consultation | Analytical memos, timeline documents |
| Conclusion Development | Evidence synthesis, finding formulation | Independent review, legal assessment | Final reports, evidence packages |
Additionally, investigators should maintain detailed analytical logs that document reasoning processes and alternative interpretations considered during analysis.
Legal Boundaries and Ethical Considerations
Human rights OSINT investigations must navigate complex legal and ethical terrain that varies significantly across jurisdictions. Therefore, investigators need clear guidance on acceptable collection methods and evidence handling procedures.
Evidence Admissibility Standards
Courts and tribunals apply increasingly sophisticated standards for digital evidence admissibility. Furthermore, investigators must understand these requirements to ensure that their work contributes effectively to accountability processes.
Key admissibility factors include:
- Authentication of digital evidence through technical and testimonial means
- Chain of custody documentation from collection through presentation
- Relevance and probative value of evidence to legal proceedings
- Reliability of sources and collection methods used
- Compliance with applicable privacy and data protection laws
Moreover, investigators should work closely with legal counsel throughout the investigation process to ensure that evidence collection methods meet jurisdictional requirements.
Privacy Protection and Source Security
Protecting sources and subjects requires careful balance between transparency and security. Additionally, investigators must consider potential harm that could result from disclosure of sensitive information.
Essential protection measures include:
- Anonymization techniques that remove identifying information
- Secure storage and transmission protocols for sensitive data
- Access controls that limit information exposure to authorized personnel
- Consultation protocols for potentially harmful disclosures
- Regular security assessments and protocol updates
Similarly, investigators should establish clear procedures for handling requests for source information from legal authorities while maintaining ethical obligations to protect vulnerable individuals.
For insights on documenting state violence with OSINT, investigators can learn specific techniques for protest monitoring and evidence preservation in high-risk environments.
Case Studies and Lessons Learned
Real-world applications of human rights OSINT investigations demonstrate both the potential and limitations of these techniques. Therefore, examining successful cases provides valuable insights for future investigations.
Successful OSINT-Based Accountability
The Syrian Archive project exemplifies systematic OSINT application in conflict documentation. Furthermore, their methodical approach to collecting, verifying, and preserving evidence has contributed to multiple legal proceedings.
Key success factors included:
- Systematic collection protocols that ensured comprehensive coverage
- Rigorous verification procedures that met legal admissibility standards
- Partnership with legal organizations that understood evidence requirements
- Technology infrastructure that supported large-scale evidence preservation
- Collaborative networks that enhanced source diversity and verification capabilities
Additionally, the project’s transparent methodology has enabled replication and improvement by other organizations working in similar contexts.
Challenges and Limitations
OSINT investigations face significant challenges that investigators must acknowledge and address proactively. Moreover, understanding these limitations helps set realistic expectations and develop mitigation strategies.
Common challenges include:
- Platform restrictions that limit access to relevant content
- Content manipulation and deliberate disinformation campaigns
- Technical limitations in verification tools and techniques
- Resource constraints that affect investigation scope and quality
- Security risks that threaten investigators and sources
Furthermore, investigators should develop contingency plans for addressing these challenges while maintaining investigation integrity and ethical standards.
Collaborative Investigation Networks
Modern human rights OSINT investigations increasingly rely on collaborative networks that combine diverse expertise and resources. Therefore, building effective partnerships enhances investigation capabilities while distributing risks and workloads.
Multi-Organizational Partnerships
Successful collaborative investigations combine the strengths of different organizational types. Additionally, these partnerships often produce more comprehensive and credible results than single-organization efforts.
Effective partnership models include:
- NGO-journalist collaborations: Combining investigative expertise with publication platforms
- Academic-practitioner partnerships: Integrating research capabilities with field experience
- Technology-advocacy alliances: Pairing technical tools with human rights expertise
- International networks: Enabling cross-border investigations and resource sharing
Moreover, collaborative investigations often benefit from diverse perspectives that identify blind spots and enhance analytical rigor.
Understanding cross-border investigation techniques helps teams coordinate effectively across jurisdictional boundaries while maintaining evidence integrity.
Training and Capacity Building
Sustainable human rights OSINT capabilities require systematic training programs that build technical skills while emphasizing ethical considerations. Furthermore, training should adapt to evolving technologies and threat environments.
Effective training programs include:
- Technical skills development in verification and analysis tools
- Ethical framework application in real-world scenarios
- Legal literacy regarding evidence requirements and admissibility
- Security awareness and operational security practices
- Collaborative investigation methods and communication protocols
Additionally, training should include regular updates that address new tools, techniques, and threats that affect investigation effectiveness and safety.
Technology Integration and Tool Selection
Choosing appropriate tools significantly affects investigation efficiency and evidence quality. Therefore, investigators should understand tool capabilities and limitations while maintaining focus on investigative objectives rather than technological features.
Essential Tool Categories
Human rights investigators need integrated tool suites that support collection, verification, analysis, and preservation activities. Moreover, tools should interoperate effectively to support comprehensive workflows.
Key tool categories include:
| Function | Tool Examples | Key Capabilities | Limitations |
|---|---|---|---|
| Content Collection | Social media APIs, web scraping tools | Automated gathering, metadata preservation | Platform restrictions, rate limits |
| Verification | InVID, RevEye, TinEye | Reverse search, metadata analysis | Limited databases, false negatives |
| Geolocation | Google Earth, Bing Maps, Wikimapia | Location matching, reference imagery | Image quality, coverage gaps |
| Analysis | Timeline tools, network analysis software | Pattern identification, relationship mapping | Complexity limitations, learning curves |
Furthermore, investigators should prioritize tools that offer transparent methodologies and enable reproducible results that support accountability objectives.
Best Practices for Sustainable Impact
- Establish clear investigation objectives and success metrics before beginning collection activities
- Implement systematic verification protocols that meet legal admissibility standards
- Maintain comprehensive documentation throughout the investigation process
- Protect source identities and sensitive information through appropriate security measures
- Collaborate with legal experts to ensure evidence collection meets jurisdictional requirements
- Build diverse partnerships that enhance investigation capabilities and credibility
- Invest in ongoing training that keeps pace with technological and methodological developments
- Develop contingency plans for addressing platform restrictions and content removal
- Regular evaluation of investigation impact and methodology effectiveness
The Future of Human Rights OSINT Investigations
Human rights OSINT investigations will continue evolving as technology advances and new challenges emerge. Therefore, investigators must remain adaptable while maintaining core ethical principles and quality standards.
Emerging trends include artificial intelligence integration for pattern recognition and content analysis, blockchain technologies for evidence preservation and authentication, and enhanced collaboration platforms that support secure international cooperation. However, these technological advances must be balanced against privacy protection and ethical investigation principles.
The growing acceptance of OSINT evidence in legal proceedings creates both opportunities and responsibilities for human rights investigators. Moreover, courts increasingly expect sophisticated verification and chain of custody procedures that meet evolving digital evidence standards.
Organizations that invest in systematic OSINT capabilities while maintaining ethical standards will be best positioned to contribute effectively to accountability processes. Furthermore, collaborative networks that share resources and expertise will likely produce the most significant impacts on human rights protection and accountability.
For comprehensive insights on building systematic investigation capabilities, explore our guide on automating OSINT investigations for modern intelligence teams.
The transformation of human rights work through OSINT represents both unprecedented opportunity and significant responsibility. Success requires combining technological sophistication with unwavering commitment to ethical principles and legal standards.
For more detailed information on OSINT evidence standards, consult the Berkeley Protocol on Digital Open Source Investigations published by the UN Office of the High Commissioner for Human Rights.
Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training.
Ready to enhance your human rights investigations with professional-grade OSINT capabilities? Discover how Kindi can support your accountability work with advanced verification and analysis tools.
FAQ
What makes OSINT evidence admissible in human rights cases?
Courts require proper authentication through technical verification, chain of custody documentation, and reliable source confirmation. Furthermore, evidence must be relevant, authentic, and collected through legally acceptable methods. The Berkeley Protocol provides specific standards that many tribunals now expect investigators to follow.
How do investigators protect sources while maintaining transparency?
Effective source protection combines technical anonymization with procedural safeguards. Additionally, investigators use secure communication channels, remove identifying metadata, and implement access controls. However, transparency requirements mean that methodologies and verification processes must remain open for scrutiny.
What are the biggest challenges in verifying social media content?
Platform manipulation, content removal, and sophisticated deepfakes create ongoing verification challenges. Moreover, investigators must distinguish between authentic content and deliberate disinformation while working within platform access limitations. Cross-referencing multiple sources and technical analysis help address these challenges.
How can small organizations build effective OSINT capabilities?
Small organizations should focus on training, collaborative partnerships, and appropriate tool selection rather than trying to build comprehensive in-house capabilities. Furthermore, many effective tools are free or low-cost, while training resources and collaborative networks provide access to expertise and resources.
What ethical guidelines govern human rights OSINT investigations?
Investigators must balance transparency with privacy protection, avoid harm to sources and subjects, and maintain accuracy throughout collection and analysis. Additionally, the “do no harm” principle requires careful consideration of potential consequences before publishing sensitive information or pursuing certain investigation paths.



