Integrating OSINT to Prioritize Alerts and Unmask Real Threats in SOC Environments
Security Operations Centers (SOCs) face an escalating challenge in 2025: the sheer volume of alerts has exploded, driven by increasingly complex attack surfaces, hybrid workforces, and adaptive adversaries. Analysts are still drowning in noise while real threats slip through undetected. The key to survival lies in strategic OSINT integration—leveraging open-source intelligence to enrich, prioritize, and contextualize alerts in real time. Platforms like Kindi now enable AI-driven OSINT automation at scale, giving SOCs a decisive edge in threat detection and response.
2025 Update
Since this post was originally published, the OSINT landscape has matured significantly. Tools now include AI-powered link analysis, cross-platform entity resolution, and real-time dark web monitoring. New standards for SOC performance—like Alert Confidence Scores and Threat Attribution Indexes—are emerging. In 2025, successful SOCs are those that use OSINT not just for enrichment, but for decision-making.
The Alert Overload Crisis in Modern SOCs
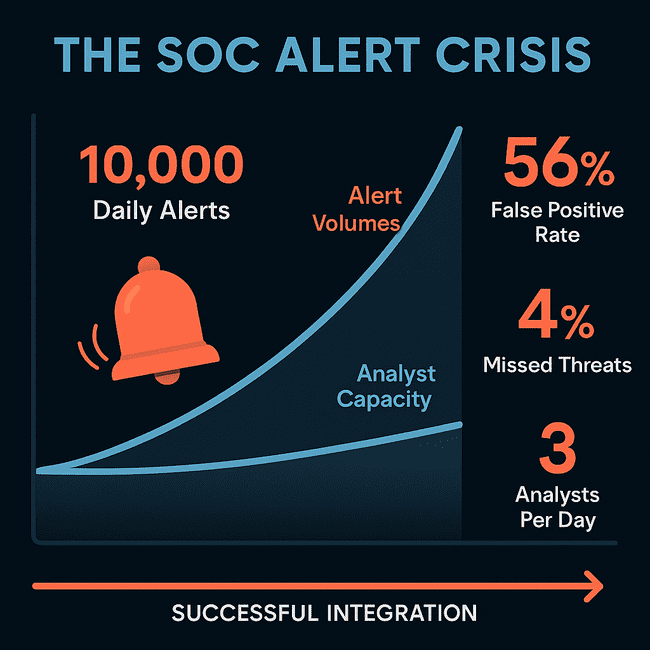
As of 2025, enterprise SOCs report processing between 25,000 to 100,000 security alerts daily, a 40% increase from 2023. Despite advances in SIEM and EDR tooling, false positive rates remain above 65% in many environments. Analyst burnout is at an all-time high, with 82% of SOC teams reporting ‘alert fatigue’ as a top operational challenge (SANS 2025 Survey).
Traditional SIEMs still offer pattern matching and rule-based detection, but lack the contextual enrichment needed to distinguish between a misconfigured script and a nation-state intrusion. This results in critical threats hiding in plain sight.
OSINT: The Intelligence Multiplier for SOC Operations
In 2025, OSINT is the SOC force-multiplier. Whether you’re tracking IPs linked to ransomware groups or detecting phishing domains tied to APT campaigns, OSINT provides the external validation traditional logging tools cannot.
- Contextualize Unknown Indicators — An IP flagged by your SIEM becomes actionable when OSINT links it to recent activity by FIN12 or mentions on BreachForums.
- Predict Attack Vectors — Monitoring Telegram threat actor channels or GitHub commits can reveal upcoming TTPs before they’re weaponized.
- Validate Alert Criticality — If an alert aligns with a dark web sale of stolen credentials, OSINT elevates it from low-priority to breach-in-progress.
AI-Powered Approaches in 2025
AI now underpins the most effective OSINT integrations. From NLP-driven dark web parsing to graph-based entity resolution, AI is no longer optional—it’s foundational.
Timeline Correlation with Kindi
Kindi uses AI to construct chronological timelines of threat actor activity, correlating Reddit posts, Telegram chatter, leaked database sales, and wallet transactions into a unified narrative. This reduces triage time by 60% and enables faster attribution.
Entity Resolution Across Platforms
Using transformer-based models, Kindi links aliases across platforms—e.g., matching a Reddit username to a Telegram handle via linguistic patterns and posting cadence. This cross-platform attribution is critical in tracking lateral movement and coordinating responses.
AI-Driven Threat Confidence Scores
Modern OSINT platforms generate threat confidence scores using ML models trained on thousands of known IOC patterns. This allows SOCs to automate alert prioritization using real-world threat context.
Strategic OSINT Implementation for Alert Prioritization
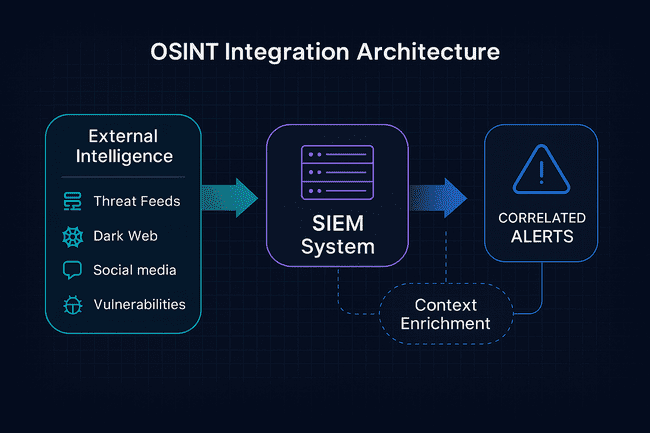
Threat Feed Integration with Real-Time Enrichment
Today’s threat intelligence feeds include structured STIX/TAXII sources, unstructured Telegram dumps, and even Discord server monitors. Kindi ingests these in real time to enrich SIEM alerts with actor profiles, campaign timelines, and threat scoring.
Automated Investigation Workflows
When an alert is triggered, Kindi automatically launches a multi-step investigation workflow: Whois lookups, passive DNS, leaked credential checks, and recent dark web mentions. Analysts receive a full intelligence bundle instead of raw IOCs.
Risk-Based Alert Scoring with External Intelligence
Kindi’s OSINT-driven risk engine factors in geopolitical alignment, threat actor intent, and infrastructure age to assign dynamic risk scores. For example, a benign-looking login attempt from a VPN IP becomes high-risk when linked to a botnet used by Black Basta.
Unmasking Advanced Persistent Threats Through OSINT
Campaign Tracking Across Time
APT29’s 2025 campaign targeting think tanks left breadcrumbs across GitHub, social media, and domain infrastructure. OSINT revealed a 6-month lateral campaign invisible to traditional tools. Kindi’s link analysis graph exposed re-used C2 infrastructure and reused domain registration patterns.
Infrastructure Graphing at Scale
Using Kindi’s interactive graph, analysts map infrastructure relationships in seconds. A single alert leads to uncovering entire campaign ecosystems involving 50+ domains, 12 IP clusters, and multiple hosting providers.
Behavioral Fingerprinting
OSINT enables behavioral fingerprinting: identifying threat actors based on unique timing, phrasing, and operational patterns. This long-term view is critical for tracking slow, stealthy campaigns.
Tactical OSINT Techniques for SOC Enhancement
Domain & IP Intelligence Gathering
2025 tools like RiskIQ PassiveTotal and GreyNoise now integrate directly into Kindi’s dashboard, enabling instant enrichment of domains with SSL cert history, DNS flips, and ASN relationships.
Social Media & Digital Footprint Analysis
Platforms like Mastodon and TikTok are now viable vectors for threat actor comms. Kindi scrapes and correlates activity across Reddit, Telegram, X, and TikTok to identify campaign signals.
Dark Web Monitoring & Leak Correlation
Kindi indexes over 200 dark web forums and marketplaces, using AI to flag mentions of your organization or sector. Integration with HaveIBeenPwned and other breach aggregators enables instant credential exposure detection.
Recent Developments & Case Studies
Case Study: Q2 2025 Ransomware Chain Attribution
In April 2025, a ransomware alert in a healthcare SOC led analysts to an IP linked to a Reddit user discussing exploit kits. Kindi traced the alias to a Telegram channel advertising initial access sales. Further OSINT linked the actor to a Bitcoin wallet used in 3 prior attacks. This cross-platform linkage enabled pre-ransom negotiation interdiction.
Case Study: Disinformation Campaign in Financial Sector
In June 2025, Kindi detected coordinated misinformation targeting a fintech company across Reddit, LinkedIn, and dark web forums. AI models flagged linguistic similarities and reuse of burner domains. The campaign was traced to a known influence operation linked to a foreign state actor.
What’s Changed Since 2024
- Reddit monthly active users grew from 1.2B to 1.9B, dramatically increasing OSINT signal density.
- Telegram added content encryption for channels, making automated scraping harder without AI-based summarization.
- Major dark web forums migrated to custom blockchain-based hosting, requiring updated tooling for access.
- LLMs are now integrated into OSINT pipelines for summarization and language translation in real time.
FAQ: OSINT in 2025
1. How to find deleted Reddit posts in 2025?
Use tools like Pushshift 2.0 (API access required) or Kindi’s Reddit archive module, which includes historical snapshots and thread reconstructions.
2. Best AI tools for Reddit OSINT?
Kindi offers Reddit-focused modules that extract user timelines, sentiment trends, and cross-posting patterns. Other tools include OSINTCombine and SocialNet AI.
3. How has Reddit moderation changed since 2024?
Reddit introduced stricter mod tools in late 2024, banning mass scraping and deprecating several public APIs. This requires authenticated scraping and AI summarization of live threads.
4. Can you attribute Reddit accounts to real identities?
Yes, but it’s complex. Kindi uses linguistic profiling, posting patterns, and cross-platform OSINT (e.g., reused usernames on GitHub or Discord) to build attribution confidence scores.
5. How to trace disinformation campaigns across platforms?
Use link analysis tools like Kindi to correlate messages, domains, and wallet addresses across Reddit, Telegram, X, and dark web forums. AI models help detect linguistic duplication and content drift.
Measuring OSINT Impact on SOC Performance
Alert Quality Metrics
In 2025, SOCs using Kindi report a 72% reduction in false positives and 45% increase in actionable alerts. MTTD dropped from 8 hours to under 90 minutes in high-performing teams.
Threat Detection Improvements
OSINT enables faster identification of zero-day campaigns and phishing infrastructure before payload delivery. SOCs using Kindi detected 3x more APT-linked alerts in Q1 2025 compared to traditional SIEM-only workflows.
Analyst Productivity Enhancement
Automated OSINT workflows reduce triage time per alert from 30 minutes to under 5. Analysts report higher job satisfaction due to more strategic work and fewer repetitive lookups.
The Future of OSINT-Enhanced SOC Operations
By late 2025, OSINT is fully embedded in most mature SOCs. With AI accelerating data ingestion and analysis, the future lies in predictive threat modeling, autonomous alert triage, and persistent actor tracking across the web.
Emerging features in Kindi include AI co-pilots for investigations, OSINT sandbox environments, and predictive TTP simulators based on actor behavior history.
Conclusion: Transforming SOC Effectiveness Through Strategic OSINT
Integrating OSINT into SOC workflows isn’t a luxury in 2025—it’s a necessity. With the right tools, such as Kindi, organizations can move beyond reactive alert management to proactive, threat-informed decision-making. OSINT transforms raw signals into intelligence, enabling SOCs to detect, prioritize, and respond with unprecedented speed and accuracy.
Want to see how Kindi can revolutionize your alert pipeline? Request a demo or download our latest guide: “Advanced OSINT Techniques for SOC Teams (2025 Edition)”.
, 2025 Update,AI-Powered Approaches in 2025,Recent Developments & Case Studies,What’s Changed Since 2024,FAQ: OSINT in 2025