Intelligence agencies face an uncomfortable reality: traditional collection methods designed for Cold War adversaries cannot keep pace with today’s digital threat landscape. Special agents and senior intel analysts working in government agencies increasingly discover critical intelligence gaps only after operational failures occur. The problem isn’t a lack of effort or expertise; it’s a fundamental mismatch between legacy tradecraft and modern information environments.
Intelligence tradecraft gap analysis has emerged as an essential discipline for government and defense organizations seeking to modernize their collection and analytical capabilities. This systematic evaluation identifies where current methods fall short, which threats slip through existing frameworks, and how adversaries exploit these blind spots. Unlike traditional after-action reviews that focus on specific incidents, gap analysis examines the entire intelligence lifecycle to reveal structural weaknesses in collection, processing, analysis, and dissemination.
The challenge intensifies as state and non-state actors adopt sophisticated operational security measures. Terrorist networks operate across encrypted platforms, nation-state cyber units mask their activities through complex infrastructure, and criminal organizations leverage the same privacy tools designed to protect legitimate users. Meanwhile, legislative changes reshape what intelligence operations can legally accomplish, creating additional constraints on collection activities.
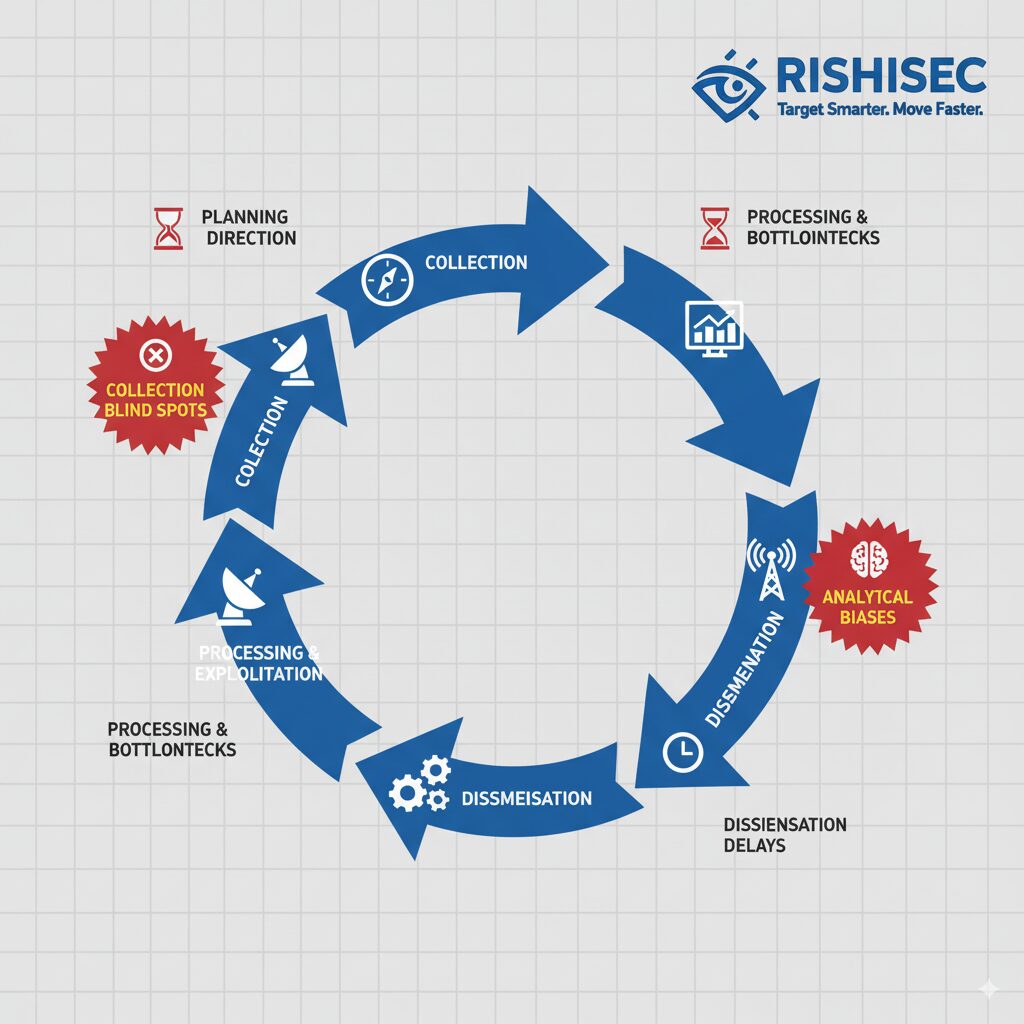
Identifying Critical Vulnerabilities in Intelligence Collection Workflows
Most intelligence tradecraft gaps emerge from three interconnected factors: technical limitations in collection platforms, organizational barriers between analytical teams, and cognitive biases that affect how analysts interpret information. Cyber crime unit leads routinely encounter situations where crucial evidence exists in open sources but remains undiscovered because collection systems lack the sophistication to identify relevant signals within massive data volumes.
Technical gaps often manifest as an inability to correlate information across disparate sources. An analyst might identify suspicious financial transactions through one system, discover related social media activity in another tool, and uncover supporting evidence in commercial databases, but lack the capability to visualize these connections efficiently. This fragmentation forces analysts to manually piece together intelligence mosaics, consuming time that should be spent on higher-level threat assessment.
Organizational gaps create equally serious problems. When cyber crime units, counterterrorism teams, and counterintelligence analysts operate in separate silos, critical intelligence about cross-domain threats remains compartmentalized. A nation-state actor conducting both cyber espionage and influence operations might be tracked by multiple teams without any group recognizing the full scope of the threat. These structural barriers persist despite decades of calls for better information sharing.
Common Intelligence Collection Blind Spots
- Multilingual open sources: Intelligence teams often miss critical information published in languages outside their analytical focus, particularly as adversaries deliberately communicate in less-monitored languages to avoid detection.
- Encrypted messaging platforms: While content remains inaccessible, metadata patterns and user behavior on these platforms can reveal network structures, but many agencies lack tools to analyze this peripheral information effectively.
- Decentralized platforms and alternative social networks: As mainstream platforms increase content moderation, threat actors migrate to smaller, regional platforms that receive less intelligence community attention.
- Technical infrastructure analysis: Understanding the digital infrastructure supporting adversary operations (hosting providers, domain registrations, CDN usage) requires specialized technical tradecraft that traditional intelligence training often overlooks.
Leveraging OSINT Automation to Close Intelligence Gaps
Open-source intelligence has evolved from a supplementary collection discipline to a primary intelligence source, but manual OSINT methods cannot scale to meet current demands. Intelligence teams can’t rely on manual work anymore when facing adversaries who operate at machine speed across global networks. Modern intelligence tradecraft requires platforms that automate collection while preserving analytical rigor.
Kindi addresses this challenge through AI-powered OSINT automation specifically designed for intelligence workflows. The platform enables special agents and senior intel analysts to define collection requirements once, then automatically monitors relevant sources for emerging threats. Rather than manually checking dozens of platforms daily, analysts receive prioritized alerts when significant developments occur within their areas of responsibility.
The link analysis capabilities prove particularly valuable for intelligence tradecraft gap analysis. When investigating complex networks, whether terrorist cells, state-sponsored cyber units, or transnational criminal organizations, analysts need to visualize relationships across multiple data types. Kindi automatically maps connections between individuals, organizations, digital infrastructure, and events, revealing patterns that manual analysis might miss. This capability transforms how cyber crime unit leads approach network investigations, reducing the time from initial lead to comprehensive network mapping from weeks to hours.
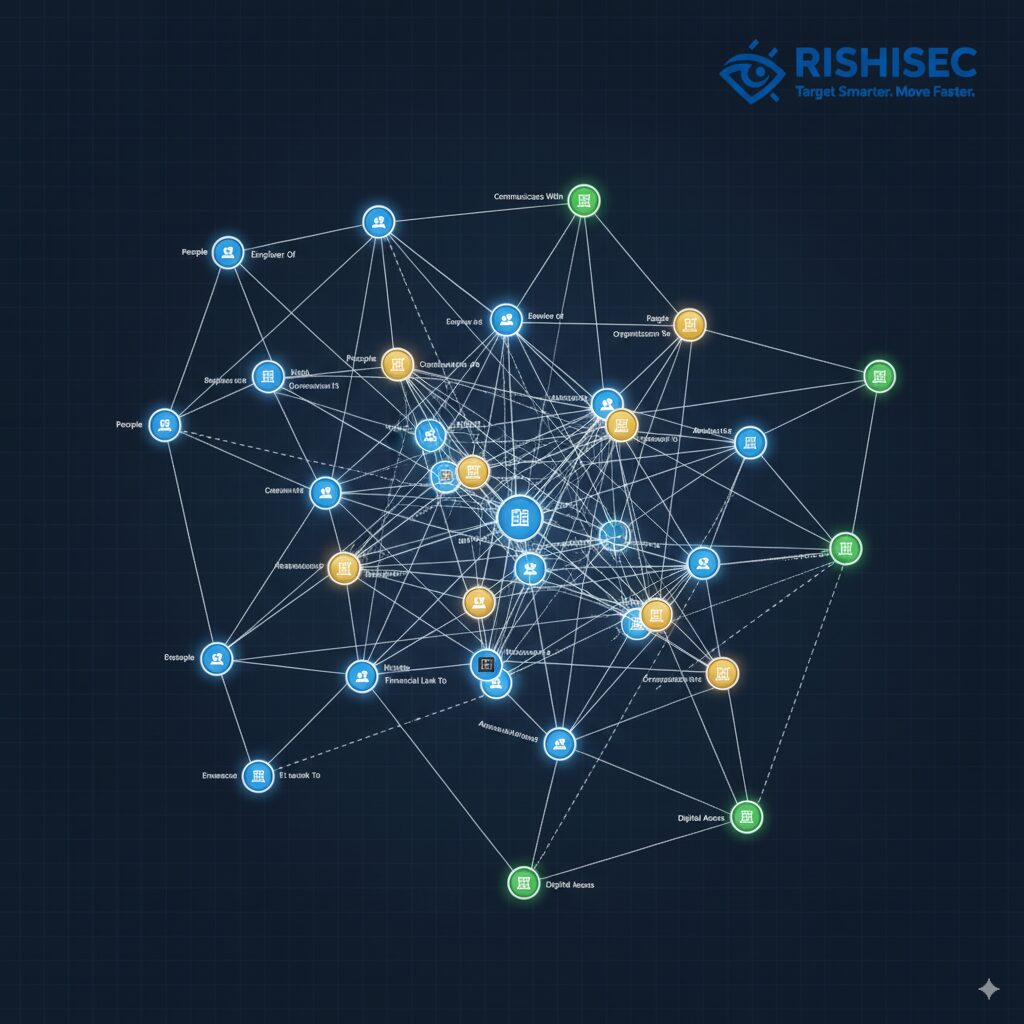
Implementing Systematic Gap Analysis in Intelligence Operations
Effective intelligence tradecraft gap analysis requires a structured methodology that examines every stage of the intelligence cycle. Begin with collection assessment by documenting all current sources and methods, then map these against intelligence requirements to identify coverage gaps. This process often reveals uncomfortable truths about how much essential intelligence never enters analytical workflows because no collection system targets those information spaces.
Processing and exploitation represent another critical examination area. Many agencies collect vast amounts of raw intelligence but lack the technical capacity or analytical bandwidth to extract value from it. Senior intel analysts should evaluate whether processing systems can handle current collection volumes, whether automated enrichment adds sufficient context, and whether analysts receive information in formats that support efficient analysis.
| Gap Analysis Stage | Key Questions | Common Findings |
|---|---|---|
| Collection Coverage | Which threat vectors lack adequate monitoring? What sources do adversaries use that we don’t collect from? | Insufficient coverage of regional platforms, limited multilingual capability, gaps in technical infrastructure monitoring |
| Processing Capacity | Can systems handle current data volumes? How much collected intelligence remains unprocessed? | Backlogs in unstructured data analysis, limited automation for routine tasks, manual processes creating bottlenecks |
| Analytical Methods | Do analytical frameworks address current threat characteristics? Where do cognitive biases affect assessments? | Over-reliance on familiar threat models, insufficient attention to emerging actors, confirmation bias in hypothesis testing |
| Dissemination | Do consumers receive intelligence in time to act? Is finished intelligence answering actual operational needs? | Production timelines exceeding operational tempo, intelligence products not aligned with consumer requirements |
Analytical tradecraft deserves particular scrutiny. Essential intelligence frameworks government agencies must master include structured analytical techniques designed to counter cognitive biases, but implementation often remains inconsistent. Gap analysis should examine whether analysts actually employ these methods, whether training provides practical application skills, and whether organizational culture supports analytical rigor over speed.
Building Intelligence Capabilities That Anticipate Future Threats
Forward-looking intelligence tradecraft gap analysis extends beyond addressing current deficiencies to anticipating future collection challenges. Adversaries continuously adapt their operational security, exploit new technologies, and shift to platforms that receive less intelligence attention. Government agencies must develop collection and analytical capabilities before threats fully mature, not after operational failures expose critical gaps.
This proactive approach requires intelligence leaders to monitor technology trends, understand how adversaries might weaponize emerging platforms, and invest in capability development ahead of urgent operational needs. When encrypted messaging platforms first emerged, intelligence agencies that anticipated their adoption by threat actors developed appropriate collection strategies. Those that waited until these platforms became ubiquitous among targets found themselves facing significant intelligence gaps with limited technical solutions.

Technology adoption must be paired with tradecraft evolution. New collection platforms and analytical tools require corresponding updates to training programs, analytical methodologies, and quality assurance processes. Special agents investigating cybercrime need different technical skills than those focused on traditional criminal networks, while senior intel analysts assessing nation-state threats require frameworks adapted to hybrid warfare that blends cyber operations, information campaigns, and conventional activities.
Translating Gap Analysis into Operational Improvements
Identifying intelligence gaps accomplishes nothing without systematic remediation efforts. Effective gap analysis produces actionable recommendations prioritized by operational impact and implementation feasibility. Some gaps require significant resource investments in new collection platforms or personnel increases, while others can be addressed through process improvements, better training, or enhanced collaboration between existing teams.
Quick wins often come from better leveraging existing capabilities. Many intelligence agencies already possess powerful OSINT collection tools but lack standardized workflows for their use, comprehensive training programs, or integration with other analytical platforms. Cyber crime unit leads can often achieve immediate improvements by implementing structured OSINT collection protocols, establishing regular cross-team collaboration sessions, and adopting platforms like Kindi that integrate multiple intelligence sources into unified analytical workspaces.
Long-term capability development requires sustained organizational commitment. Intelligence tradecraft must evolve continuously as adversaries adapt and new technologies emerge. Agencies should establish regular gap analysis cycles, perhaps quarterly or biannually, that reassess collection coverage, processing capacity, analytical methods, and dissemination effectiveness. This ongoing evaluation ensures intelligence capabilities keep pace with dynamic threat environments rather than falling progressively further behind adaptive adversaries.
Practical Tips for Intelligence Tradecraft Assessment
- Document everything: Create comprehensive inventories of current collection sources, analytical tools, and dissemination channels before attempting to identify gaps, as assumptions about existing capabilities often prove inaccurate.
- Involve operational personnel: Special agents and field investigators often identify collection gaps that headquarters analysts miss; their operational perspective proves invaluable during assessment phases.
- Test assumptions through red teaming: Have experienced personnel attempt to operate as adversaries would, identifying which activities your current collection posture would detect and which would succeed unobserved.
- Benchmark against peer organizations: Understanding how other agencies with similar missions approach collection and analysis can reveal gaps in your own tradecraft without requiring complete reinvention.
- Prioritize ruthlessly: Not every gap can be addressed simultaneously; focus resources on vulnerabilities that adversaries actively exploit or that affect high-priority intelligence requirements.
- Measure progress systematically: Establish clear metrics for gap remediation progress; vague improvement goals lead to indefinite timelines and incomplete solutions.
Moving Beyond Gap Identification to Intelligence Superiority
Intelligence tradecraft gap analysis ultimately serves a single purpose: ensuring government agencies maintain decision advantage over adversaries. Every unaddressed gap represents potential strategic surprise, operational failure, or preventable harm. Senior intel analysts and cyber crime unit leads bear responsibility for honestly assessing capability shortfalls and advocating for necessary improvements, even when doing so reveals uncomfortable organizational realities.
The intelligence community’s ongoing modernization efforts, as outlined in recent strategy documents, recognize that maintaining intelligence advantage requires continuous capability evolution. Traditional collection methods and analytical approaches that proved effective against previous adversaries must be supplemented and, in some cases, replaced by approaches suited to digital-age threats operating at global scale and machine speed.
Success requires both technical capability and organizational culture. Sophisticated OSINT platforms enable collection at necessary scale and speed, but their value depends on analysts skilled in their use, organizations that support analytical rigor, and leadership that acts on intelligence assessments even when they contradict preferred narratives or established assumptions. Intelligence tradecraft gap analysis reveals not just technical deficiencies but organizational and cultural factors that affect intelligence effectiveness.
Want to strengthen your intelligence tradecraft and eliminate critical gaps in your analytical workflows? Check out our OSINT courses for practical, hands-on training designed for government intelligence professionals. Ready to see how AI-powered OSINT automation can close your intelligence gaps? Try Kindi and transform your investigative capabilities.
FAQ
What is intelligence tradecraft gap analysis?
Intelligence tradecraft gap analysis is a systematic evaluation of an intelligence organization’s collection methods, processing capabilities, analytical frameworks, and dissemination processes to identify where current approaches fail to meet operational requirements or leave vulnerabilities that adversaries can exploit. This analysis examines the entire intelligence cycle to reveal structural weaknesses rather than focusing solely on individual operational failures.
How often should intelligence agencies conduct tradecraft gap analysis?
Intelligence agencies should perform comprehensive gap analysis at least annually, with focused assessments occurring quarterly to address rapidly evolving threat environments. Additionally, gap analysis should follow any significant operational failure, major technological shift in adversary capabilities, or implementation of new intelligence collection or analytical platforms to ensure these changes effectively address existing vulnerabilities.
What role does OSINT play in closing intelligence gaps?
Open-source intelligence plays a crucial role in closing collection gaps because adversaries increasingly operate in publicly observable digital spaces, even while employing operational security measures. Modern OSINT platforms enable intelligence teams to monitor vast open-source environments at scale, identify relevant signals within massive data volumes, and correlate open-source information with intelligence from other disciplines to develop comprehensive threat assessments.
How can smaller intelligence units with limited resources conduct effective gap analysis?
Smaller intelligence units can conduct effective gap analysis by focusing on high-priority threats relevant to their operational mandate, leveraging peer organizations’ expertise through information-sharing arrangements, and prioritizing quick wins that improve capabilities without requiring major resource investments. Starting with structured documentation of current collection sources and analytical methods often reveals addressable gaps that don’t require sophisticated tools or large budgets to fix.
What are the most common intelligence gaps in government agencies today?
The most common intelligence gaps include insufficient coverage of multilingual open sources, limited capacity to analyze technical infrastructure supporting adversary operations, inadequate collaboration between specialized analytical teams tracking different aspects of the same threats, and delays in dissemination that reduce intelligence value for time-sensitive operational decisions. Many agencies also struggle with processing backlogs where collected intelligence remains unanalyzed due to limited analytical bandwidth.




