For modern red teams, success doesn’t hinge on exploiting sophisticated zero-day vulnerabilities, but begins with what’s already exposed across the internet. In today’s threat landscape, overlooked assets such as forgotten subdomains, misconfigured cloud storage, and publicly accessible developer repositories often become the initial entry points for serious breaches. This is where OSINT for red teams becomes indispensable. By leveraging open-source intelligence to identify external attack surfaces, red teams can map exposed infrastructure, trace digital footprints, and simulate realistic adversary behavior, all before a single exploit is launched.
In this article, we’ll explore how to build a strategic OSINT workflow tailored for red team operations — one that enables precision targeting, stealthy reconnaissance, and maximum impact during adversary emulation exercises.
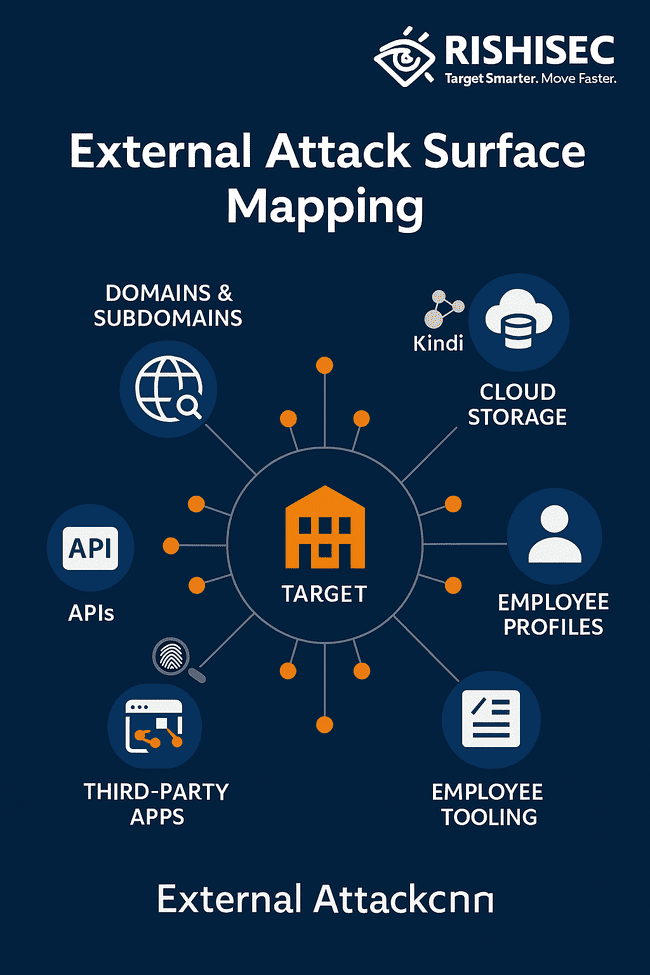
What Is the External Attack Surface?
Most people think the external attack surface is just “stuff facing the internet.” That’s like saying a car is “stuff with wheels”, technically correct but missing the point entirely.
The external attack surface encompasses every piece of digital evidence that reveals insights into your target’s infrastructure, people, and processes. It’s not just what they intentionally published, it’s what they accidentally leaked, forgot about, or assumed nobody would find. Here’s what smart attackers (and smarter red teams) actually look for:
The Technical Footprint
- Domains and subdomains (including the ones IT forgot existed)
- Login portals and web applications (especially the ones with “staging” in the URL)
- Exposed APIs (bonus points if they’re returning user data in error messages)
- Cloud infrastructure (S3 buckets, Azure blobs, and the inevitable “backup-prod-DONT-DELETE” folder)
- DNS records and certificates (because DNS is basically a roadmap of your infrastructure)
- Third-party integrations (that SaaS tool your marketing team installed last year)
The Human Element (This Is Where It Gets Interesting)
- Employee information scattered across LinkedIn, GitHub, Twitter, and those conference speaker bios nobody remembers writing
- Credential dumps from breaches (because “Password123!” works everywhere, right?)
- Social media oversharing (“Just deployed the new auth server! #DevLife #YesImATarget”)
- Public repositories with more secrets than a CIA vault
The magic is understanding how they connect. Is that forgotten subdomain pointing to a misconfigured Jenkins instance? That’s not just a vulnerability. That’s your pathway to simulating a full compromise without ever touching the production network.
Why OSINT Is Red Teaming’s Foundation
Here’s the truth most red teams won’t admit: Modern attackers don’t need fancy zero-days when you’re handing them everything they need on a silver platter.
Real attackers operate like intelligence agencies. They gather, correlate, and act on information. They don’t immediately start launching exploits because that’s noisy, risky, and unnecessary when you can just walk through the unlocked side door.
Think about it: Why would an attacker burn a zero-day exploit when they can:
- Find your VPN login page through subdomain enumeration
- Grab employee emails from LinkedIn
- Test those emails against credential dumps from old breaches
- Walk right into your network using legitimate, stolen credentials
When you master OSINT, you’re not just finding vulnerabilities. You’re building complete attack narratives that show clients exactly how a breach would unfold in the real world.
The OSINT Recon Workflow (Broken Down)
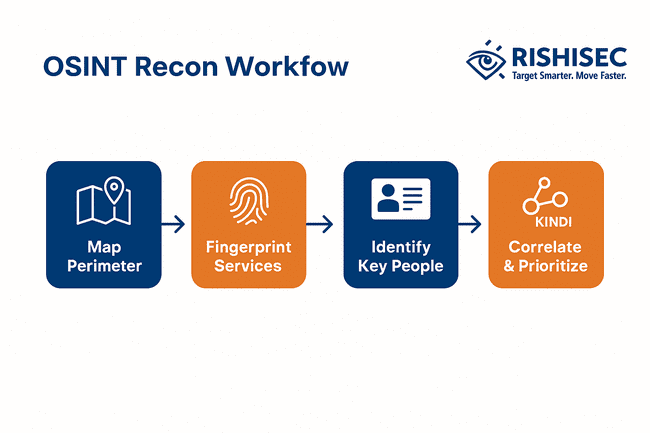
To go from chaos to clarity, red teams need a workflow that pulls together multiple discovery methods into one structured process:
1. Map the Perimeter
Start with asset discovery:
- Run subdomain enumeration using Subfinder, crt.sh, or DNS history
- Use Shodan or Censys to find exposed services
- Look up WHOIS and DNS records to track infrastructure relationships
2. Fingerprint Services
For each discovered asset, identify what’s running:
- What web apps are exposed?
- Do login portals reveal internal tool names?
- Is there a misconfigured API or staging site?
Tools like httpx, nmap, and favicon hashes can help here.
3. Identify Key People
Use LinkedIn and GitHub to map out technical staff:
- Developers often leak information about internal tools
- Email patterns help with phishing simulation
- Public repos can expose tokens, configurations, or credentials
4. Correlate and Prioritize
This is where Kindi becomes essential.
Instead of dumping all your findings into a spreadsheet, use Kindi’s AI-powered link analysis to:
- Automatically connect domains, user profiles, leaked data, and infrastructure
- Visualize relationships in an interactive graph
- Highlight the strongest attack paths based on exposure and priority
You can export these findings as a timeline, report, or client-facing slide.
Advanced OSINT Techniques
HUMINT Integration
Your OSINT isn’t complete without understanding the human elements:
- Social engineering reconnaissance through customer service calls
- Dumpster diving (when legally authorized) for physical intelligence
- Social media relationship mapping to understand organizational dynamics
AI-Powered Reconnaissance
Modern tools can analyze patterns across massive datasets:
- Use LLMs to analyze company communications patterns from press releases
- Automate correlation between technical and human intelligence
- Generate realistic phishing content based on actual company communication styles
The “Living Off the Land” OSINT Approach
Instead of relying on specialized tools, leverage legitimate services:
- Use actual business intelligence platforms to research your targets
- Leverage recruitment websites for organizational charts and technology stacks
- Mining customer support forums for internal process information
How Red Teams Exploit OSINT Paths
Once you’ve built your graph and mapped relationships, it’s time to simulate impact. Here are four high-impact exploitation methods red teams use based on OSINT data:

Credential-Based Attack Simulation
The Process:
- Collect employee email addresses from OSINT
- Cross-reference with known breach databases
- Test credential reuse against discovered login portals
- Document access levels without escalating (unless explicitly in scope)
Why This Works: Password reuse is endemic. I’ve seen Fortune 500 executives using the same password they used for a forum that was breached in 2014.
Kindi automatically flags matched credentials across known breaches and ties them to exposed services.
2. Phishing with Internal Tool Context
The Setup:
- Identify internal tools and processes through OSINT
- Craft phishing emails that reference specific internal tools (“Okta password reset required”)
- Use AI tools to match company communication styles
- Build landing pages that perfectly mimic internal login portals
The McCray Touch: I use LLMs to analyze all the company’s public communications (press releases, blog posts, executive speeches) to generate phishing content that sounds authentically corporate. It’s scary how well this works.
3. Cloud Asset Misconfigurations
Common Scenarios:
- AWS credentials leaked in GitHub repositories
- S3 buckets with predictable naming conventions
- Azure storage accounts with anonymous access enabled
- Google Cloud Platform instances with default configurations
The Reality Check: I’ve found customer databases, employee records, and internal documentation sitting in publicly accessible cloud storage. This isn’t theoretical—this is Tuesday for most red teams.
4. Forgotten DevOps Tooling
High-Value Targets:
- Jenkins instances with build secrets
- GitLab/GitHub enterprise installations
- Monitoring dashboards (Grafana, Kibana)
- Container registries with internal tools
- CI/CD pipelines with production access
Personal War Story: Found a company’s Jenkins instance through subdomain enumeration. No authentication required. Full access to deployment scripts, production database credentials, and internal API keys. Total time from domain to “game over”? Forty-seven minutes.
These tools often have weak or default credentials and tend to be excluded from security monitoring.
OSINT Toolkit Comparison: Manual vs Automated
| Category | Traditional Tools | With Kindi |
|---|---|---|
| Subdomain Enumeration | Amass, Subfinder | Built-in crawler with exportable graph |
| Breach Correlation | Dehashed, HaveIBeenPwned | Integrated identity + breach graph |
| Link Analysis | Maltego, spreadsheets | Automated visual graph with timeline |
| Profile Matching | Google dorking, manual search | AI agents across GitHub, LinkedIn, pastebins |
| Reporting | Manual screenshots | Exportable PDFs, CSVs, and client slides |
Kindi centralizes everything in one platform, saving hours of pivoting across disconnected tools.
Case Study: Red Team Recon for a Financial Client
The Setup: A fintech company hired our team to simulate an external threat actor with no prior knowledge of their infrastructure.
The Challenge: “Show us how an outsider could compromise our systems without touching our production networks.”
The OSINT Phase (Day 1):
- Started with main domain: financorp.com
- Discovered 47 subdomains through certificate transparency and DNS enumeration
- Found employee profiles on LinkedIn revealing technology stack (AWS, Okta, Salesforce)
- Located the development team’s GitHub repositories
The Discovery (Day 2):
- Found developer’s personal repo with .env file containing database credentials
- Discovered staging subdomain: staging-api.financorp.com
- Cross-referenced the developer’s email with HaveIBeenPwned (found in 3 breaches)
- Located the company Slack workspace through public GitHub issues
The Connection (Day 3):
- Staging API used the same database credentials found in GitHub
- Developer’s breached password worked on staging environment
- Staging environment had access to production customer data (oops)
The Simulation: Used SwarmNode AI to craft phishing emails referencing internal Salesforce deployment issues (found through GitHub commit messages). Created landing page mimicking their Okta login. Simulated session hijacking using replay tokens mentioned in public GitHub issues.
The Result: Complete kill chain from public information to simulated customer data access. No exploits, no vulnerability scanning, no firewall touching. Just good old-fashioned intelligence gathering and social engineering.
Client Reaction: “Holy shit, you found all of this in three days?”
Our Response: “This is what attackers do in three hours.”
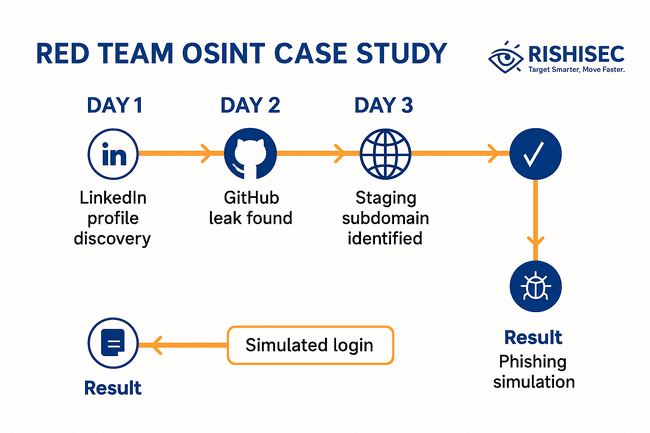
Result:
The red team presented a complete kill chain, starting from a LinkedIn profile and ending with a simulated credentialed login without using any exploits.
Related Reading
Want more ways to boost red team operations with OSINT?
Conclusion
Mapping and exploiting external attack surfaces isn’t just a red team routine; it’s where modern engagements begin. From exposed credentials to forgotten staging environments, what a target leaves in the open is often more revealing than what they protect behind a firewall.
But identifying these weak points takes more than passive reconnaissance. It requires a disciplined OSINT workflow, reliable tooling, and the ability to turn fragmented public data into coherent attack narratives.
This is where platforms like Kindi offer a real strategic advantage. By automating multi-source intelligence gathering and presenting it in clear, actionable graphs and timelines, Kindi helps red teams move faster without missing critical links. From breach data correlation to live infrastructure mapping, every step of the recon phase is accelerated, organized, and more impactful.
If you’re part of a red team, pen testing group, or offensive security unit, mastering external surface OSINT is non-negotiable. It informs everything from your phishing lures to privilege escalation simulations. And the teams who do it well are the ones delivering the highest-fidelity simulations and the clearest value to their clients.