Defense contractors face an unprecedented challenge today. While military technologies evolve at breakneck speed, traditional acquisition processes still crawl along multi-year timelines. This mismatch creates dangerous gaps in capability that near-peer adversaries exploit daily.
The reality is stark. By the time a cutting-edge AI system or cybersecurity tool completes the traditional procurement cycle, it’s often outdated. Meanwhile, adversaries deploy similar technologies in months, not years. However, the solution isn’t simply moving faster; it’s about modernizing defense acquisition frameworks to balance speed with necessary oversight.
Defense contractors must take the lead in reshaping how military organizations acquire and deploy critical technologies. This transformation requires understanding both the urgency of modern threats and the importance of maintaining security standards.
Understanding the Current Acquisition Bottleneck
Traditional defense acquisition cycles follow predictable patterns. First, requirements are developed over months. Then, requests for proposals circulate through bureaucratic channels. Next, evaluations and approvals stretch across quarters. Finally, funding allocation and contract execution add more delays.
This system worked when military technology changed slowly. However, today’s threat landscape demands different approaches. For instance, cyber threats evolve weekly, but acquiring new defensive tools can take years.
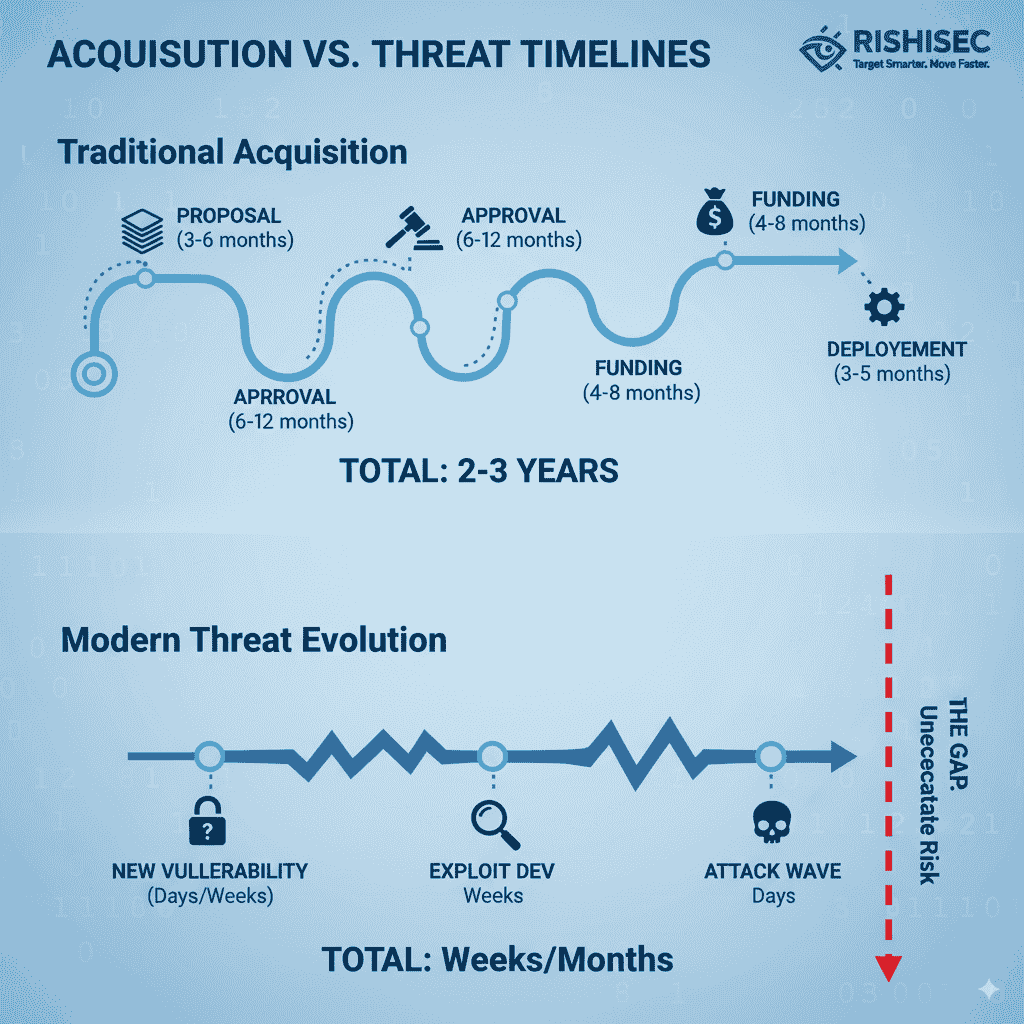
The bottleneck stems from several factors. Bureaucratic layers add review time without adding value. Furthermore, fragmented oversight creates redundant approvals. Additionally, risk-averse cultures prioritize process over outcomes. Consequently, modern intelligence teams struggle with outdated tools while waiting for procurement approvals.
| Traditional Acquisition Phase | Typical Duration | Modern Alternative | Potential Duration |
|---|---|---|---|
| Requirements Development | 6-12 months | Agile Requirements | 2-4 weeks |
| RFP Process | 3-6 months | Continuous Competition | 1-2 months |
| Evaluation & Selection | 6-9 months | Pilot Testing | 1-3 months |
| Contract Execution | 3-6 months | Framework Agreements | 2-4 weeks |
Why Speed Has Become Critical in Defense Technology
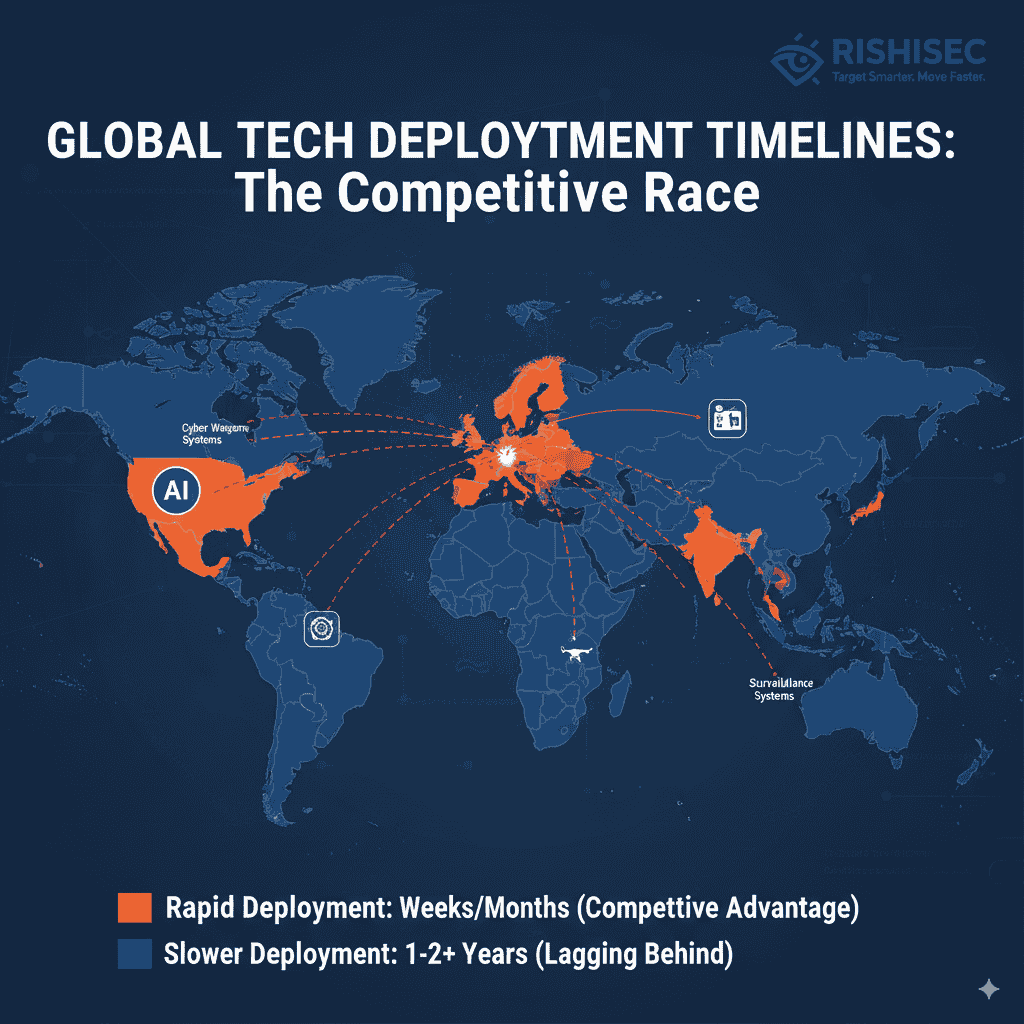
Geopolitical tensions drive the urgency for faster acquisition. Near-peer adversaries aren’t bound by Western bureaucratic processes. They deploy AI-powered surveillance, autonomous weapons, and cyber capabilities rapidly. This creates capability gaps that threaten national security.
Technology evolution compounds this challenge. AI algorithms improve monthly through continuous learning. Similarly, cybersecurity threats adapt daily to new defenses. Drone capabilities advance through rapid iteration cycles. Traditional acquisition timelines simply cannot match this pace.
Mission impact makes the difference tangible. Delayed intelligence tools mean missed threat detection. Slow cyber defense deployment leaves networks vulnerable. Outdated communication systems create operational blind spots. Each delay potentially costs lives and strategic advantage.
Consider recent examples from cross-border investigations. Intelligence agencies need real-time data analysis tools to track international threats. However, procurement delays mean analysts work with outdated systems while threats evolve daily.
The Risks of Moving Too Fast Without Proper Oversight
Speed without security creates different problems. Moving too quickly can bypass essential security vetting. Consequently, systems might contain vulnerabilities that adversaries exploit. This is particularly dangerous with dual-use technologies that originated in civilian markets.
Operational risks multiply when untested systems enter mission-critical environments. For example, rushing AI decision-making tools into combat situations without adequate testing could cause friendly fire incidents. Similarly, deploying unvetted communication systems might create intelligence leaks.
Compliance requirements exist for good reasons. They ensure systems meet security standards, protect classified information, and maintain operational integrity. However, the challenge lies in maintaining these standards while accelerating timelines.
Proven Reform Pathways for Modernizing Defense Acquisition
Agile acquisition frameworks offer the first solution. Instead of single, massive procurements, organizations can use incremental approvals. This approach involves pilot programs that test capabilities quickly. Then, successful pilots scale gradually with proper oversight.
Dual-use adoption models represent another pathway. Defense organizations can partner with technology startups while maintaining security layers. For instance, commercial AI platforms can be adapted for military use through secure integration frameworks.
Sandbox environments enable rapid testing without compromising security. These controlled spaces allow organizations to evaluate emerging technologies safely. Consequently, decision-makers can assess capabilities before full deployment.
The Role of Public-Private Partnerships
Strategic partnerships between government and industry drive meaningful reform. These collaborations reduce bureaucratic friction while maintaining oversight. Moreover, they leverage private sector agility with public sector security requirements.
Successful partnerships require clear frameworks. Government agencies need streamlined approval processes. Meanwhile, contractors need predictable security requirements. Together, they can create acquisition pipelines that balance speed with security.
Platforms like Kindi demonstrate how AI-powered tools can accelerate intelligence workflows while maintaining security standards. This approach shows how technology can support both speed and rigor in defense operations.
How Defense Contractors Can Drive Acquisition Reform
Defense contractors must become reform advocates, not just technology providers. This means proposing innovative acquisition approaches alongside technical solutions. Furthermore, contractors should demonstrate how rapid deployment maintains mission-critical security.
Building trust requires transparency in security practices. Contractors need comprehensive compliance documentation ready for review. Additionally, they should maintain current security certifications and demonstrate continuous improvement in security practices.
Innovation advocacy involves showing rather than telling. Contractors can demonstrate secure rapid deployment through pilot programs. They can also share case studies showing how agile approaches maintain security while accelerating capabilities.

Innovation Strategies That Work
Successful contractors use several proven strategies. First, they maintain continuous dialogue with acquisition teams throughout development cycles. This ensures solutions meet evolving requirements without major redesigns.
Second, they invest in security-first development practices. This means building security into systems from the ground up rather than adding it later. Consequently, security reviews proceed faster because risks are minimized by design.
Third, they leverage modular architectures that enable incremental improvements. This approach allows organizations to deploy initial capabilities quickly while adding features over time.
- Develop security-first solutions that expedite approval processes
- Create modular systems that support incremental deployment and testing
- Maintain continuous engagement with acquisition teams throughout development
- Document compliance thoroughly to streamline security reviews
- Propose pilot programs that demonstrate capabilities with minimal risk
- Share success stories that show how speed and security can coexist
Case Studies: Successful Acquisition Innovation in Action
DARPA’s rapid acquisition programs provide excellent models for reform. These programs demonstrate how organizations can maintain security while accelerating deployment. For example, DARPA’s cyber security initiatives move from concept to deployment in months rather than years.
NATO innovation funds support dual-use technology adoption across alliance partners. These programs show how international cooperation can accelerate capability development while maintaining security standards. Furthermore, they demonstrate how standardized approaches can reduce procurement complexity.
Leading contractors partner with agile procurement initiatives to reshape industry practices. These partnerships create proof-of-concept programs that demonstrate new acquisition approaches. Moreover, successful pilots often scale into organization-wide reforms.
Lessons from Successful Reforms
Successful acquisition reforms share common characteristics. They maintain clear security requirements while streamlining approval processes. Additionally, they use continuous feedback loops to improve both speed and oversight.
Another key factor is stakeholder alignment. Successful reforms ensure that technology teams, security personnel, and acquisition specialists work toward common goals. This alignment prevents conflicts that traditionally slow procurement processes.
For example, organizations using OSINT tools for investigative work need rapid access to new capabilities. Successful acquisition reforms enable these teams to evaluate and deploy new tools quickly while maintaining security standards.
Future Outlook: The Evolution of Defense Acquisition
Policy trends indicate significant changes ahead. The US Department of Defense is implementing new acquisition frameworks that prioritize agility. Similarly, NATO partners are developing standardized rapid procurement processes. These changes create opportunities for forward-thinking contractors.
Contractor opportunities center on digital transformation leadership. Organizations that can demonstrate secure, rapid deployment capabilities will lead future procurements. Moreover, those that can help government agencies modernize their acquisition processes will build lasting partnerships.
The predicted shift moves from rigid multi-year cycles to modular, adaptive frameworks. This transformation enables organizations to deploy initial capabilities quickly while adding features iteratively. Consequently, acquisition becomes continuous improvement rather than periodic replacement.
Preparing for the Future Acquisition Environment
Smart contractors are already preparing for this transformation. They’re investing in agile development practices, security-first architectures, and continuous compliance frameworks. Furthermore, they’re building relationships with acquisition reform advocates within government agencies.
Technology platforms that support this transformation will become increasingly valuable. Solutions that accelerate intelligence analysis, streamline security assessments, and enable rapid testing will drive future acquisitions.
Organizations using advanced OSINT platforms experience firsthand how modern tools can transform operational capabilities. This experience positions them to advocate effectively for acquisition reform that benefits both speed and security.
Conclusion: Leading the Modernizing Defense Revolution
The future of defense acquisition lies in balancing speed with security, not choosing between them. Forward-thinking contractors must lead this transformation by demonstrating how agile approaches can maintain the highest security standards.
Success requires more than just technological innovation. It demands partnership with government agencies to reshape acquisition processes. Moreover, it requires building trust through transparency, compliance, and proven results.
The opportunity is significant for organizations willing to lead this change. Those that can help defense agencies modernize their acquisition processes while maintaining security will become indispensable partners in national security.
Modern intelligence workflows require modern acquisition approaches. Tools that accelerate analysis, enhance collaboration, and maintain security enable the rapid deployment that current threats demand. This is where Kindi’s AI-powered OSINT automation and link analysis platform demonstrates the potential for balancing speed and rigor in defense operations.
Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training. Additionally, explore how Kindi can transform your intelligence workflows through secure, rapid automation.
FAQ
What are the biggest challenges in modernizing defense acquisition processes?
The primary challenges include balancing speed with security requirements, overcoming bureaucratic resistance to change, ensuring compliance with existing regulations, and managing the risk of deploying untested technologies in mission-critical environments. Additionally, organizations must maintain transparency while protecting classified information throughout the acquisition process.
How can defense contractors accelerate acquisition timelines without compromising security?
Contractors can accelerate timelines by implementing security-first development practices, maintaining continuous compliance documentation, proposing modular deployment approaches, and establishing pilot programs that demonstrate capabilities with minimal risk. Building trust through transparency and proven security practices also speeds approval processes.
What role does artificial intelligence play in modern defense acquisition?
AI transforms defense acquisition by automating compliance checking, accelerating threat assessment, enabling rapid capability evaluation, and supporting continuous monitoring of deployed systems. AI-powered tools can also streamline vendor assessment, contract management, and performance monitoring throughout the acquisition lifecycle.
How do international partnerships affect defense acquisition modernization?
International partnerships, particularly through NATO and allied frameworks, create opportunities for standardized acquisition processes, shared technology development, reduced individual country costs, and accelerated capability deployment across multiple organizations. These partnerships also enable knowledge sharing about successful acquisition reform strategies.
What are the key metrics for measuring successful acquisition reform?
Success metrics include reduced time from requirement to deployment, maintained or improved security standards, cost efficiency compared to traditional methods, stakeholder satisfaction across government and contractor teams, and demonstrated operational effectiveness of rapidly acquired capabilities. Organizations should also measure the frequency of successful pilot programs and their scaling success rates.