Legacy surveillance frameworks were built for a different era. They assumed that terror networks communicated through interceptable channels, were organized into identifiable cells, and operated within geographic boundaries that intelligence agencies could monitor. These assumptions no longer hold. Modern terrorism has digitized, decentralized, and adapted to evade traditional collection methods, creating visibility gaps that threaten national security.
The speed of digital communication has collapsed operational timelines. Terror networks can radicalize recruits, coordinate logistics, and execute attacks in timeframes that make traditional intelligence cycles obsolete. By the time analysts write reports and decision-makers review options, the operational landscape has already shifted. This temporal mismatch between intelligence production and threat evolution demands fundamental transformation in how agencies collect and analyze information.
Open-source intelligence now fills the visibility gap that SIGINT and HUMINT alone cannot cover. Terrorists communicate through commercial platforms, fund operations with cryptocurrency, recruit on social media, and coordinate through encrypted messaging apps. These activities generate digital traces in open or semi-open environments where traditional surveillance has limited reach. OSINT fusion in counterterrorism operations provides precision, speed, and automation that legacy frameworks cannot match.
The transformation is not merely technological. It represents a conceptual shift from reactive monitoring to proactive threat hunting. Rather than waiting for signals intelligence to intercept communications or human sources to report activities, fusion centers actively search for threat indicators across digital ecosystems, correlating weak signals into actionable intelligence before adversaries complete operational preparations.

The OSINT Fusion Framework: Architecture and Integration
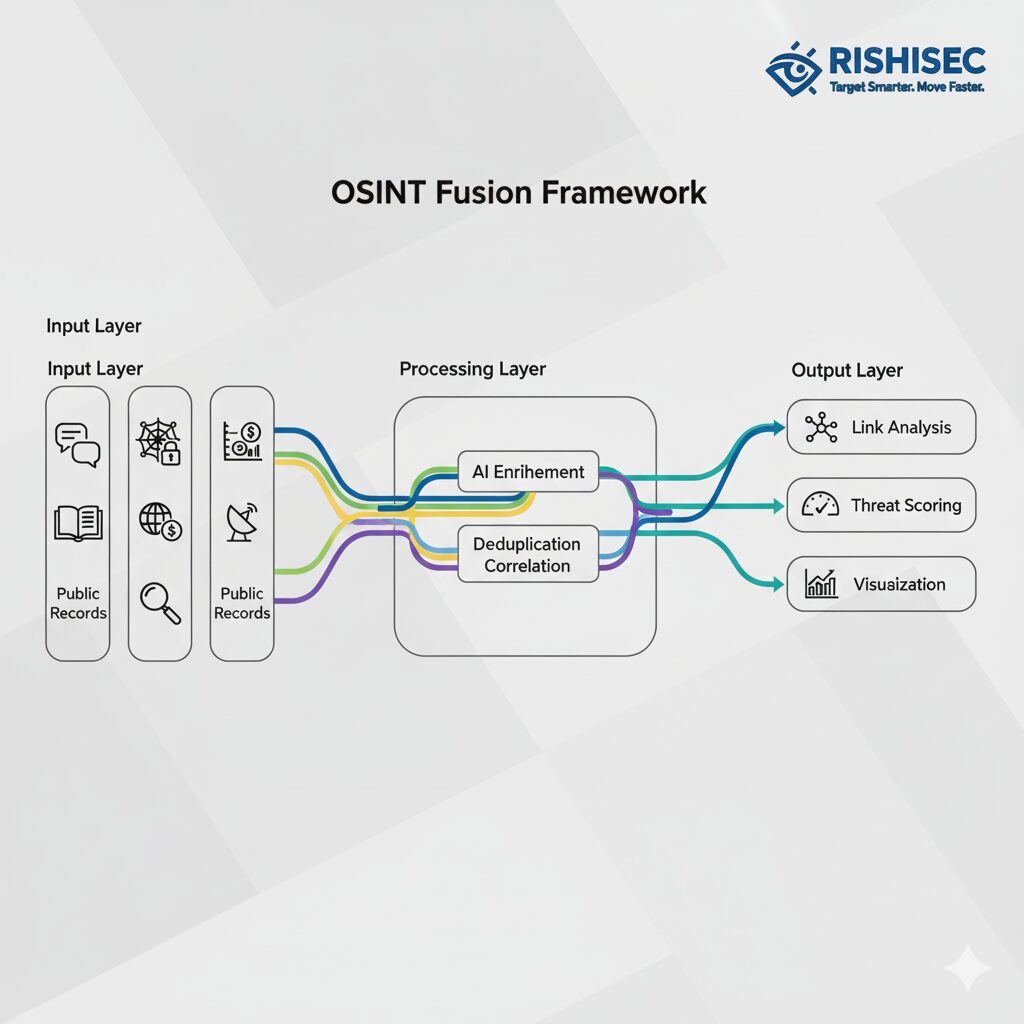
Building effective OSINT fusion capabilities requires more than collecting open-source data. It demands architectural integration that brings together multi-source collection, automated enrichment, deduplication, and real-time visualization into unified intelligence workflows. This framework transforms fragmented data streams into coherent threat assessments that analysts can act upon immediately.
Multi-source collection forms the foundation. Modern fusion systems simultaneously monitor social media platforms, dark web forums, financial transaction records, domain registration databases, satellite imagery repositories, and public records. This comprehensive coverage ensures analysts don’t miss critical information because they were looking at the wrong source. Automated collection agents continuously scan designated sources, extracting relevant information based on predefined indicators and adaptive learning models.
Automated enrichment adds context that transforms raw data into intelligence. When the system identifies a social media account of interest, enrichment engines automatically search for associated email addresses, phone numbers, cryptocurrency wallets, and other online identities. They geolocate posts, identify language patterns, and map social connections. This contextual layering happens automatically and instantaneously, providing analysts with comprehensive profiles rather than isolated data points.
Deduplication ensures analytical efficiency by eliminating redundant information. The same individual might appear across multiple platforms under different usernames. The same event might be reported by dozens of sources. Without deduplication, analysts waste time reviewing identical information repeatedly. Fusion systems use entity resolution algorithms to identify when different data points refer to the same person, organization, or event, consolidating information and reducing noise.
Real-time visualization through link graphs makes complex relationships immediately comprehensible. Platforms like Kindi display network connections, communication patterns, financial flows, and operational relationships as interactive visual graphs. Analysts can zoom in on suspicious clusters, trace connections between entities, and identify network hubs that warrant deeper investigation. This visual intelligence dramatically accelerates analysis compared to reading linear reports or spreadsheet data.
Real-World Counterterrorism Use Cases
The value of OSINT fusion becomes concrete when examining operational applications. Intelligence agencies worldwide now rely on these capabilities to detect threats that would remain invisible using traditional methods. These real-world use cases demonstrate how fusion transforms counterterrorism from reactive investigation to predictive defense.
Detecting lone-wolf mobilization patterns through behavioral data represents one of the most challenging counterterrorism problems. Unlike organized cells with multiple members who communicate and therefore create interceptable signals, lone actors often radicalize privately and give few explicit warnings. However, behavioral OSINT can identify subtle indicators. Changes in social media activity, shifts in information consumption patterns, research into operational security practices, and expressions of grievance or admiration for previous attackers collectively paint a risk profile that warrants intervention before violence occurs.
Identifying extremist propaganda networks via language clustering helps disrupt information operations that fuel radicalization. Terror organizations run sophisticated propaganda campaigns across multiple platforms simultaneously. By analyzing linguistic patterns, narrative themes, posting schedules, and audience engagement, intelligence units can map these networks, identify central nodes, and work with platforms to disrupt dissemination. Advanced language analysis techniques reveal coordination that might otherwise appear as organic grassroots activity.
Exposing cross-border logistics through domain and financial metadata prevents operational cells from acquiring resources. Terror attacks require funding, materials, and coordination. These necessities leave traces in cryptocurrency transactions, domain registrations for fundraising or propaganda sites, and commercial logistics channels. By correlating financial metadata with travel records, communications data, and operational intelligence, fusion systems reveal supply chains and support networks that enable violence.
Collaboration Through Fusion Center Models
No single intelligence agency possesses complete visibility into modern terror threats. Effective counterterrorism requires information sharing across agencies, jurisdictions, and international partners. The fusion center model provides the organizational framework and technical infrastructure that enables this collaboration while maintaining security and protecting sensitive sources.
Secure federated OSINT frameworks allow agencies to share intelligence without compromising classified methods or sources. Rather than centralizing all data in a single repository, federated systems enable distributed agencies to query across multiple databases, access relevant information based on need-to-know principles, and contribute their own intelligence to collective threat assessments. This architecture balances information sharing with operational security requirements.
Automated confidence scoring for shared data helps receiving agencies assess intelligence reliability. When multiple organizations contribute information to fusion centers, consistency and quality vary. Machine learning models can analyze metadata about sources, corroboration across different intelligence streams, and historical accuracy to assign confidence scores. Analysts receiving shared intelligence therefore understand its reliability and can weight it appropriately in their assessments.
International intelligence partnerships like NATO, INTERPOL, and regional fusion centers demonstrate the power of collaborative intelligence. Terror networks operate globally, and effective response requires global intelligence cooperation. Fusion centers enable real-time information sharing, coordinated operations, and collective threat assessments that no single nation could produce independently. Strategic OSINT frameworks guide this international cooperation while respecting sovereignty and legal boundaries.
Integrating AI for Real-Time Threat Correlation
Artificial intelligence transforms OSINT fusion from enhanced data collection to predictive threat intelligence. Modern AI capabilities enable pattern recognition across vast datasets, predictive analysis of network formation, and adaptive prioritization that focuses analytical resources on highest-probability threats. However, effective AI integration requires careful architecture that balances automation with human judgment and maintains explainability.
Pattern recognition in encrypted traffic metadata provides visibility even when content remains inaccessible. While intelligence agencies cannot decrypt end-to-end encrypted communications without significant technical operations, metadata about who communicates with whom, when, how frequently, and from where reveals network structures and operational tempo. AI algorithms trained on historical terror network patterns can identify suspicious communication structures that suggest operational preparation even without accessing message content.
Predictive analysis for cell formation helps agencies intervene before networks become operational. Machine learning models analyze how previous terror cells formed, what indicators preceded mobilization, and which factors distinguished operational threats from ideological sympathizers. Applied to current intelligence streams, these models can flag emerging networks based on early-stage indicators like rapid network growth, increased operational security practices, or coordination across previously disconnected actors.
Adaptive prioritization for high-risk alerts ensures analysts focus on genuine threats. Fusion systems generate thousands of potential alerts daily. Without intelligent prioritization, analysts either become overwhelmed by volume or miss critical threats buried in noise. AI models that learn from analyst feedback continuously improve their ability to distinguish high-probability threats from false positives, adjusting alert rankings based on contextual factors and historical outcomes.
Kindi’s integration of CrewAI and SwarmNode enables autonomous threat linking across multiple domains. Rather than requiring analysts to manually search for connections between different intelligence sources, swarm intelligence systems deploy specialized AI agents that collaboratively analyze data, share findings, and collectively build threat assessments. One agent might specialize in social media analysis while another focuses on financial flows. Together, they produce comprehensive threat pictures faster and more completely than traditional linear analysis.
Ethics, Oversight, and the Risk of Overreach
The capabilities enabled by OSINT fusion and artificial intelligence create profound ethical responsibilities. Intelligence agencies must navigate the tension between comprehensive threat detection and fundamental civil liberties. This balance is not merely a constraint on operations but a necessary condition for maintaining democratic legitimacy and public trust that effective security institutions require.
The line between surveillance and intelligence is often blurred but critically important. Surveillance implies broad monitoring of populations to identify threats. Intelligence implies targeted collection against specific threats based on reasonable suspicion. OSINT fusion should operate according to intelligence principles, using automated collection to identify threats rather than monitoring populations indiscriminately. Clear legal frameworks must define what triggers intelligence interest and when open-source monitoring crosses into surveillance requiring judicial authorization.
Transparency protocols help maintain accountability while protecting operational security. Democratic intelligence agencies should publish aggregate statistics about collection activities, provide public reporting on privacy safeguards, and submit to regular independent audits. While specific operations and sources must remain classified, the legal authorities, oversight mechanisms, and policy frameworks governing OSINT fusion should be transparent to enable informed public debate about appropriate security measures.
Minimization principles require agencies to collect only information necessary for specific threat assessments and purge data that no longer serves active investigations. Just because intelligence systems can collect and retain vast amounts of information doesn’t mean they should. Data minimization protects privacy, reduces storage costs, and limits the potential damage from breaches or unauthorized access. Automated retention schedules should delete data according to predefined timelines based on threat relevance.
AI explainability in national security applications ensures human oversight remains meaningful. When AI systems flag individuals or networks as threats, analysts must understand why. Black-box algorithms that cannot explain their reasoning undermine human judgment and risk embedding biases into security decisions. Explainable AI architectures show analysts which factors contributed to threat scores, enabling them to validate algorithmic assessments and identify potential errors or biases before operational actions occur.

The Future of Counterterrorism Intelligence
The trajectory of counterterrorism intelligence points toward increasing automation, predictive capabilities, and AI systems that identify threats before human analysts recognize emerging patterns. These advances promise unprecedented effectiveness but also raise fundamental questions about appropriate human control, algorithmic transparency, and the boundaries of acceptable security measures in democratic societies.
Autonomous OSINT collection agents will operate continuously without human direction, monitoring designated sources and automatically extracting relevant information based on learned threat indicators. These systems will adapt to adversary behavior, identifying new platforms and techniques as terror networks evolve. The challenge lies in ensuring these autonomous systems remain aligned with legal boundaries and ethical principles even as they operate independently.
AI models detecting radicalization through sentiment shifts will identify individuals at risk of violent mobilization based on subtle changes in online behavior, language use, and network associations. This capability could enable preventive interventions before radicalization progresses to violence. However, it also risks flagging individuals based on protected expression or minority viewpoints, requiring robust safeguards against discriminatory targeting and ensuring transparency about what behaviors trigger intelligence interest.
Real-time geospatial cross-correlation of threat movements will integrate satellite imagery, location data from social media, financial transaction locations, and telecommunications metadata to track suspected operatives in near real-time. This capability could help agencies interdict attacks in progress or disrupt operational cells before they strike. The privacy implications of persistent location tracking demand clear legal frameworks and judicial oversight to prevent abuse.
FAQ
How is OSINT fusion different from traditional intelligence gathering?
Traditional intelligence relies on separate collection disciplines that operate in silos. OSINT fusion integrates open-source data with classified intelligence streams in real-time, automatically correlating information across sources to reveal connections invisible to single-source analysis. This integration enables predictive threat detection rather than reactive investigation.
What makes OSINT fusion essential for modern counterterrorism?
Modern terror networks operate across digital platforms that generate massive amounts of open-source data. Traditional SIGINT and HUMINT cannot provide comprehensive visibility into these activities. OSINT fusion processes this digital exhaust systematically, identifying threat indicators, mapping network structures, and detecting mobilization patterns that would otherwise remain hidden.
Can smaller agencies implement OSINT fusion capabilities?
Yes. While large intelligence agencies have extensive resources, platforms like Kindi make sophisticated OSINT fusion accessible to smaller agencies. Cloud-based architecture, automated collection and correlation, and AI-powered analysis eliminate the need for massive infrastructure investments. Agencies can scale capabilities based on their specific needs and budgets.
What safeguards prevent OSINT fusion from becoming mass surveillance?
Effective safeguards include legal frameworks requiring reasonable suspicion before collection, data minimization principles that limit retention, independent oversight by judicial or legislative bodies, transparency about collection authorities, and technical controls like access logging and automated compliance monitoring. Democratic intelligence agencies must balance security effectiveness with civil liberties protection.
How do fusion centers share intelligence across international borders?
International fusion centers use secure federated systems that enable intelligence sharing without centralizing sensitive data. Agencies maintain control over their own databases while providing query access to partners based on treaties, memoranda of understanding, and need-to-know principles. Automated confidence scoring helps receiving agencies assess intelligence reliability from foreign partners.
Discover how Kindi’s OSINT Fusion Platform empowers government analysts to turn raw data into actionable counterterrorism intelligence. Want to strengthen your OSINT capabilities? Check out our OSINT courses for practical, hands-on training that builds real-world skills.

