Every day, security operations centers process thousands of alerts. A suspicious IP address appears in firewall logs. An unknown hash triggers antivirus signatures. Domain reputation services flag a potentially malicious URL. These indicators suggest that something has occurred, but they rarely provide insight into its meaning for the organization.
Traditional SOC workflows treat each alert as an isolated incident. Analysts manually pivot between tools, searching threat intelligence platforms, querying WHOIS databases, and checking reputation services. This context gathering consumes 60 to 80 percent of investigation time, yet it remains critical for accurate triage decisions. The gap between alert generation and meaningful context creates bottlenecks that slow response times and increase analyst burnout.
Organizations implementing OSINT enrichment workflows report investigation time reductions of 60 to 70 percent. Analysts spend less time gathering context and more time responding to actual threats. Platforms like Kindi automate this enrichment process by connecting security alerts with open-source threat intelligence, creating visual relationship maps that reveal patterns invisible in isolated indicators.
Understanding OSINT Enrichment in Security Operations
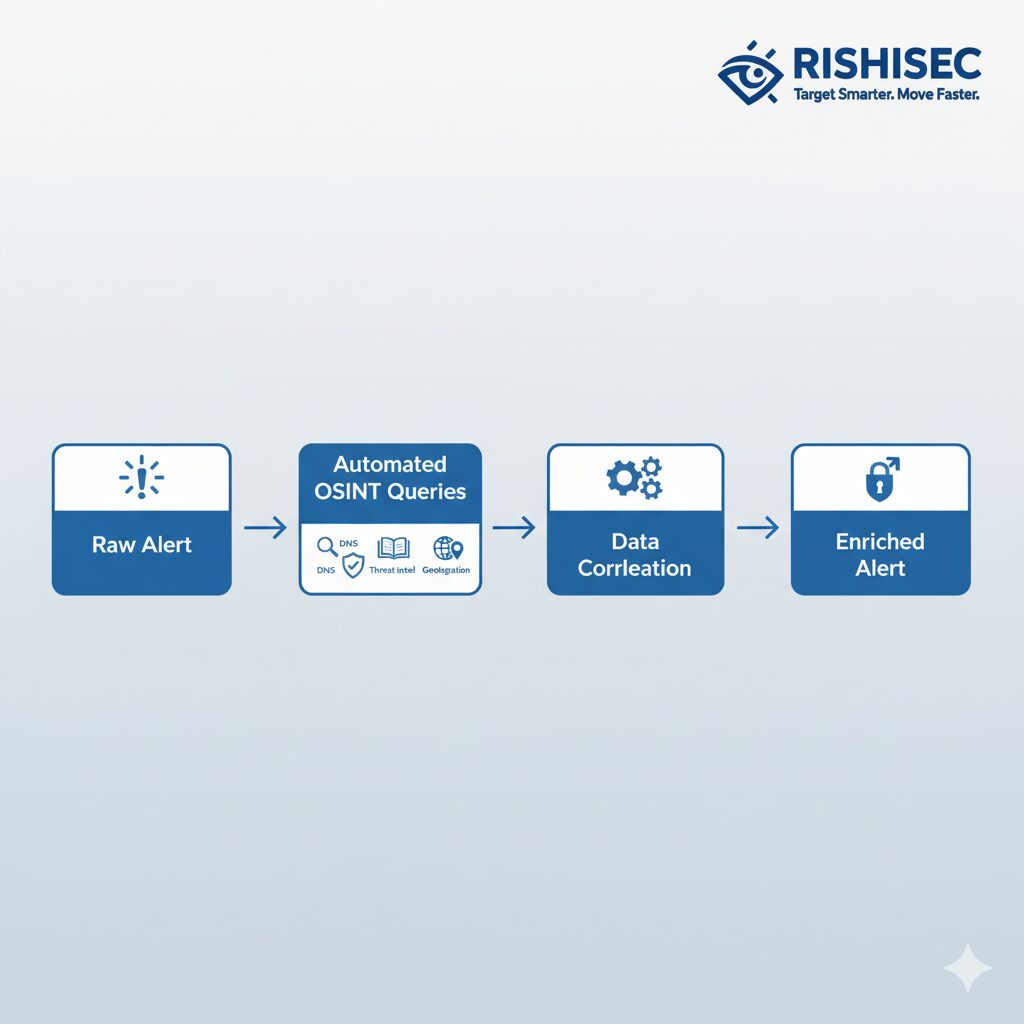
OSINT enrichment refers to the process of augmenting security alerts with additional context from open-source intelligence feeds. When a SIEM generates an alert for a suspicious IP address, enrichment systems automatically query dozens of data sources to build a comprehensive profile. This happens in seconds, delivering context that would take analysts minutes or hours to gather manually.
The enrichment process draws from diverse OSINT categories. Passive DNS data reveals domain associations and infrastructure relationships. WHOIS records provide registration details and ownership patterns. Geolocation services identify the physical or network location of IP addresses. Threat intelligence feeds correlate indicators with known campaigns, malware families, and threat actor tactics. Social media and paste site monitoring surfaces leaked credentials or discussions about targeting the organization.
This contextual layering transforms investigation workflows fundamentally. Instead of linear research where analysts chase one lead at a time, enrichment provides parallel insights that accelerate understanding. An alert about an unusual login attempt becomes actionable when enrichment reveals the source IP belongs to a compromised hosting provider frequently used in credential stuffing attacks, the user account was mentioned in a recent data breach, and similar login patterns targeted three other organizations in the same sector last week.
Successful enrichment requires balancing depth with speed. Querying too many sources creates latency that defeats the purpose of automation. Querying too few sources leaves critical context gaps. Effective implementations prioritize high-value data sources based on alert type, automate the most time-consuming lookups, and cache frequently accessed information to reduce API calls.
Core OSINT Sources for Alert Enrichment
Threat Intelligence Platforms and Feeds
Commercial and open-source threat intelligence feeds provide the foundation for alert enrichment. Services like AlienVault OTX, VirusTotal, and Shodan offer APIs that return reputation scores, malware associations, and historical activity for IP addresses, domains, file hashes, and URLs. These feeds aggregate data from global sensor networks, honeypots, and researcher submissions, creating comprehensive threat landscapes.
Passive DNS and Infrastructure Mapping
Passive DNS data reveals domain-to-IP relationships over time, exposing attacker infrastructure and command-and-control networks. When an alert triggers for a suspicious domain, passive DNS queries show which IP addresses hosted that domain historically, which other domains share the same infrastructure, and how frequently the DNS records change. These patterns help identify phishing campaigns, malware distribution networks, and threat actor infrastructure.
Infrastructure mapping extends beyond DNS to include SSL certificate analysis, ASN relationships, and hosting provider patterns. SSL certificates often link seemingly unrelated domains through shared certificate authorities, registration details, or certificate serial numbers. ASN data shows which network operator controls an IP address, helping identify bulletproof hosting providers favored by threat actors. When combined with comprehensive SOC visibility, these infrastructure insights create powerful detection capabilities.
WHOIS and Domain Registration Intelligence
WHOIS records provide registration details for domains and IP addresses, including registrant information, registration dates, and name server configurations. While privacy protections increasingly hide personal details, WHOIS data still offers valuable context for alert investigation. Newly registered domains warrant heightened scrutiny because attackers often register infrastructure immediately before campaigns. Domains using privacy protection services require additional investigation to determine legitimacy.
Geolocation and Network Context
IP geolocation data adds physical and network context to alerts involving network indicators. Knowing that a login attempt originated from a country where the organization has no presence immediately raises suspicion. Geolocation also reveals impossible travel scenarios, where the same user account authenticates from locations too distant to reach within the time elapsed between logins.
Network context extends beyond physical location to include hosting provider information, anonymization service detection, and proxy identification. An alert becomes more serious when enrichment reveals the source IP belongs to a Tor exit node, VPN service, or bulletproof hosting provider. Conversely, recognizing legitimate cloud services or corporate VPN infrastructure helps analysts quickly dismiss benign alerts.
ASN enrichment provides organizational context by identifying which company or entity controls an IP address block. This proves valuable for investigating lateral movement within networks, identifying compromised infrastructure, and tracking attacker command-and-control channels. When multiple alerts share the same ASN but different IP addresses, it suggests coordinated activity across related infrastructure.
Building Automated Enrichment Workflows
Effective OSINT enrichment requires automation because manual lookups cannot scale to handle modern alert volumes. Security orchestration platforms like SOAR systems provide the integration layer that connects security alerts with OSINT data sources. These platforms query enrichment APIs automatically when alerts trigger, aggregate the returned data, and present consolidated context to analysts.
Workflow design should prioritize alert types based on investigation frequency and analyst pain points. High-volume alerts like firewall denies benefit from lightweight enrichment that quickly categorizes traffic as benign or suspicious. Lower-volume but higher-stakes alerts such as malware detections warrant comprehensive enrichment across multiple data sources. Tailoring enrichment depth to alert type optimizes resource utilization while providing appropriate context for each investigation.
Caching strategies reduce API costs and improve response times. Frequently queried indicators should be cached locally with appropriate refresh intervals. Popular cloud service IP addresses rarely change their reputation characteristics within hours, making them excellent caching candidates. Conversely, newly observed indicators require real-time queries because threat intelligence about recent campaigns updates rapidly.
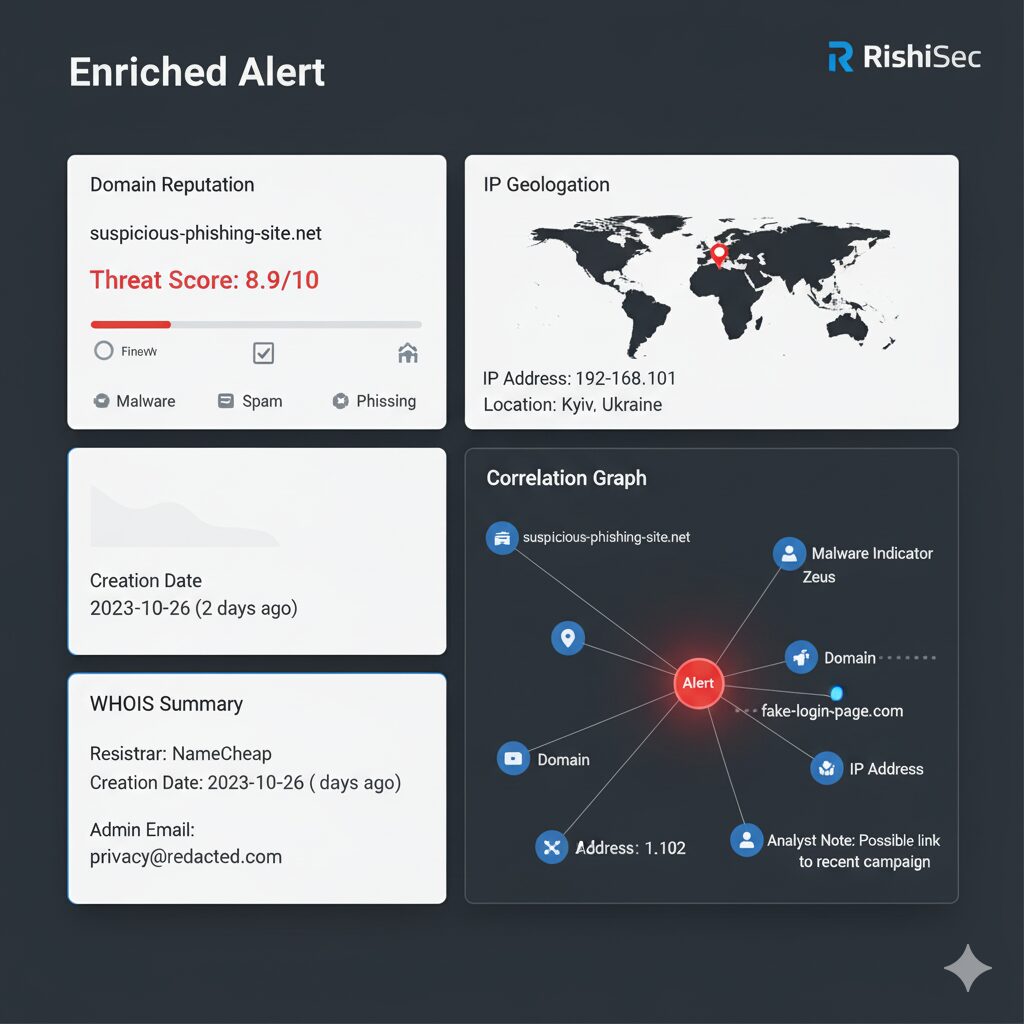
Integration with platforms like Kindi enables visual representation of enrichment results through link analysis graphs. Instead of reading through lists of enrichment data, analysts see visual networks connecting indicators, infrastructure, and threat intelligence. An IP address connects to associated domains, which link to SSL certificates, which relate to specific malware campaigns. This visual approach accelerates pattern recognition and reveals relationships that tabular data obscures.
Error handling proves critical in production enrichment workflows. External API failures should degrade gracefully rather than blocking alert processing. If threat intelligence enrichment fails, the alert should still reach analysts with whatever context succeeded. Implementing fallback data sources provides redundancy when primary enrichment APIs experience downtime or rate limiting.
Enrichment Best Practices for SOC Teams
Start enrichment implementation with high-impact alert categories rather than attempting comprehensive coverage immediately. Malware alerts, suspicious login attempts, and phishing indicators typically benefit most from OSINT context because they require extensive manual investigation without enrichment. Focus initial efforts on these categories to demonstrate value quickly and build organizational support for broader implementation.
Establish enrichment baselines by measuring investigation times before and after implementation. Document how long analysts spend gathering context manually, then track the same metrics after enrichment automation. These measurements justify continued investment and help identify which enrichment sources provide the most value. Organizations often discover that certain OSINT feeds contribute minimal value while consuming significant API quota, enabling optimization decisions.
Train analysts on interpreting enrichment data to maximize its value. Enrichment surfaces information, but analysts must understand what it means. A newly registered domain requires different interpretation than a ten-year-old domain suddenly appearing in alerts. Hosting provider context matters because different providers indicate different threat profiles. Ongoing training ensures analysts leverage enrichment effectively rather than ignoring valuable context.
Create enrichment playbooks that document how specific OSINT sources inform different alert types. Firewall alerts benefit from ASN and geolocation context but rarely need SSL certificate analysis. Email security alerts require domain reputation and WHOIS data but might not need passive DNS depth. Tailored playbooks help analysts navigate enrichment data efficiently without getting overwhelmed by irrelevant context.
Balance automation with analyst judgment by presenting enrichment as context rather than automated decisions. Enrichment should inform triage rather than replace it. Even comprehensive OSINT context requires human interpretation because attackers increasingly abuse legitimate services. Analysts must evaluate enrichment findings within the broader context of organizational risk, user behavior baselines, and current threat landscapes.
Many SOC teams find that understanding the difference between threat intelligence and threat data helps them use enrichment more effectively. Raw enrichment data becomes intelligence only when analyzed within operational context.
Measuring Enrichment Impact on SOC Performance
Track mean time to triage as the primary enrichment success metric. This measures how quickly analysts classify alerts as false positives or genuine threats requiring investigation. Enrichment should substantially reduce triage time by providing immediate context that eliminates manual research. Measure this metric by alert type because enrichment impact varies across different alert categories.
Monitor false positive rates before and after enrichment implementation. Effective enrichment helps analysts quickly identify benign activity, reducing false positive investigation effort. If false positive rates remain unchanged despite enrichment, it suggests the OSINT sources lack relevance to the organization’s alert profile or analysts need additional training on leveraging enrichment data.
Calculate alert escalation accuracy by tracking how often Level 1 triage decisions prove correct upon Level 2 review. Enrichment should improve escalation accuracy because analysts have better context for initial classification. Measuring escalation accuracy helps identify enrichment gaps where additional OSINT sources might provide value.
Document cost savings from reduced investigation time. When analysts spend less time gathering context, they handle more alerts with the same staffing levels or the organization requires fewer SOC positions. Calculate hourly investigation costs, multiply by time savings per alert, and aggregate across alert volumes to quantify enrichment ROI. These financial metrics help justify continued investment in enrichment infrastructure.
Survey analyst satisfaction with enrichment tools and workflows. Analyst morale improves when tedious manual research gets automated, but only if enrichment integrates smoothly into existing workflows. Friction in enrichment access or poor user interface design can negate automation benefits. Regular feedback ensures enrichment implementations actually help analysts rather than creating new frustrations.
Advanced Enrichment: Behavioral Context and Historical Analysis
Beyond infrastructure and threat intelligence enrichment, behavioral context adds temporal perspective to alerts. How frequently does this indicator appear in organizational logs? When did it first appear? Are we seeing escalating activity or an isolated incident? Historical enrichment transforms alerts from snapshots into narratives that reveal attack progression.
Implementing historical enrichment requires storing indicator metadata over time. When an IP address triggers an alert, enrichment should show whether the same IP appeared in logs previously, what actions it took, and how recently. This temporal context helps distinguish persistent threats from opportunistic scans. An IP address seen daily for months suggests different risk than one appearing for the first time.

Campaign clustering uses enrichment data to group related alerts into potential attack campaigns. When multiple alerts share enrichment attributes like common infrastructure, similar tactics, or related threat intelligence, they might represent a coordinated attack. Platforms like Kindi visualize these relationships through link graphs, making campaign identification faster and more accurate than manual correlation.
The Future of OSINT Enrichment in Security Operations
Artificial intelligence will transform enrichment from data retrieval to proactive intelligence generation. Current enrichment systems query data sources reactively when alerts trigger. Future AI-powered enrichment will continuously monitor OSINT sources for emerging threats relevant to the organization, pre-enriching indicators before they appear in alerts. This shift from reactive to proactive enrichment enables faster response to zero-day threats and targeted campaigns.
Predictive enrichment will use machine learning to forecast which indicators warrant investigation based on historical patterns. By analyzing thousands of previous investigations, ML models learn which enrichment attributes correlate with genuine threats versus false positives. These models can automatically adjust alert priorities based on enrichment findings, ensuring that analysts focus attention where it matters most.
Cross-organizational enrichment will expand beyond traditional threat intelligence sharing to include behavioral baselines and attack pattern data. Imagine enrichment that shows not just whether other organizations flagged an indicator but how they responded, what they discovered during investigation, and whether it proved malicious. This collective learning accelerates the entire security community’s response capabilities.
The line between OSINT enrichment and automated investigation will continue blurring as enrichment systems become more sophisticated. Rather than simply providing context, future enrichment will execute initial investigation steps automatically, gathering evidence and documenting findings that previously required analyst effort. This evolution will free analysts for higher-order tasks like threat hunting and security architecture improvement.
Transforming Alert Noise into Intelligence
OSINT enrichment represents one of the highest-impact improvements SOC teams can implement. By automatically layering intelligence onto security alerts, organizations transform raw indicators into actionable context that accelerates investigation and improves triage accuracy. The result is faster threat response, reduced analyst burnout, and more effective security operations overall.
As threat landscapes grow more complex and alert volumes continue increasing, manual context gathering becomes increasingly unsustainable. OSINT enrichment isn’t optional for modern security operations; it’s essential infrastructure that separates effective SOCs from overwhelmed ones. The question isn’t whether to implement enrichment but how quickly organizations can deploy it to start realizing benefits.
Ready to transform your alert investigation workflow? Discover how Kindi automates OSINT enrichment and visualizes threat intelligence relationships, helping your SOC team cut investigation time while improving detection accuracy.
Want to master OSINT techniques for security operations? Explore our OSINT training courses designed specifically for SOC analysts, covering threat intelligence integration, infrastructure analysis, and automated investigation workflows.
FAQ
What is OSINT alert enrichment in security operations?
OSINT alert enrichment is the automated process of adding open-source intelligence context to security alerts. When a SIEM or security tool generates an alert for a suspicious indicator like an IP address or domain, enrichment systems automatically query threat intelligence feeds, passive DNS databases, WHOIS records, and other OSINT sources to provide comprehensive background information. This transforms raw alerts into context-rich intelligence that enables faster, more accurate triage decisions.
How much does OSINT enrichment reduce investigation time?
Organizations implementing comprehensive OSINT enrichment workflows typically report investigation time reductions of 60 to 70 percent. By automatically gathering context that analysts would otherwise research manually, enrichment eliminates the most time-consuming aspects of alert investigation.
How do SOC teams measure enrichment ROI?
Measure mean time to triage before and after enrichment implementation to quantify investigation speed improvements. Track false positive rates to assess whether enrichment helps analysts identify benign activity faster.
What are the biggest challenges in implementing OSINT enrichment?
API rate limiting constrains scalability, especially when using free threat intelligence feeds with strict query limits. Data quality varies across OSINT sources, requiring continuous evaluation to ensure enrichment reliability. Integration complexity arises when connecting enrichment systems with diverse security tools and SIEM platforms.

