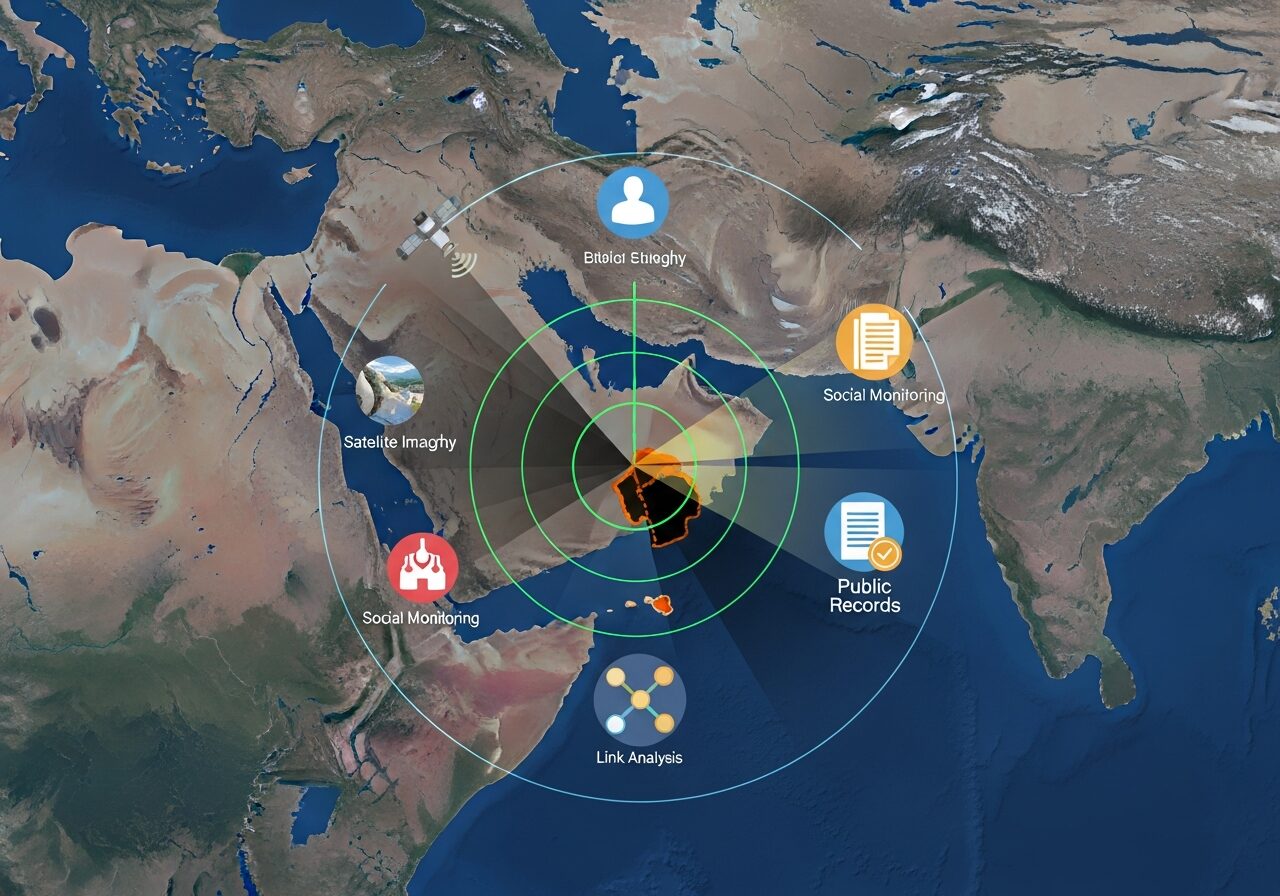
Furthermore, modern threats operate across digital boundaries, making government intelligence OSINT strategies more crucial than ever. From tracking state-sponsored cyber campaigns to monitoring terrorist recruitment networks, intelligence professionals need sophisticated approaches that can adapt to rapidly changing threat environments.
Government intelligence agencies face an unprecedented challenge in today’s digital landscape. Moreover, with over 4.9 billion internet users generating massive amounts of data daily, traditional intelligence gathering methods are no longer sufficient. Consequently, Open Source Intelligence (OSINT) has evolved from a supplementary tool to a critical cornerstone of national security operations.
This comprehensive guide explores the essential OSINT frameworks and methodologies that government intelligence agencies must implement. Additionally, it provides insights into maintaining operational superiority in an increasingly complex information landscape.
Strategic OSINT Framework for Government Operations
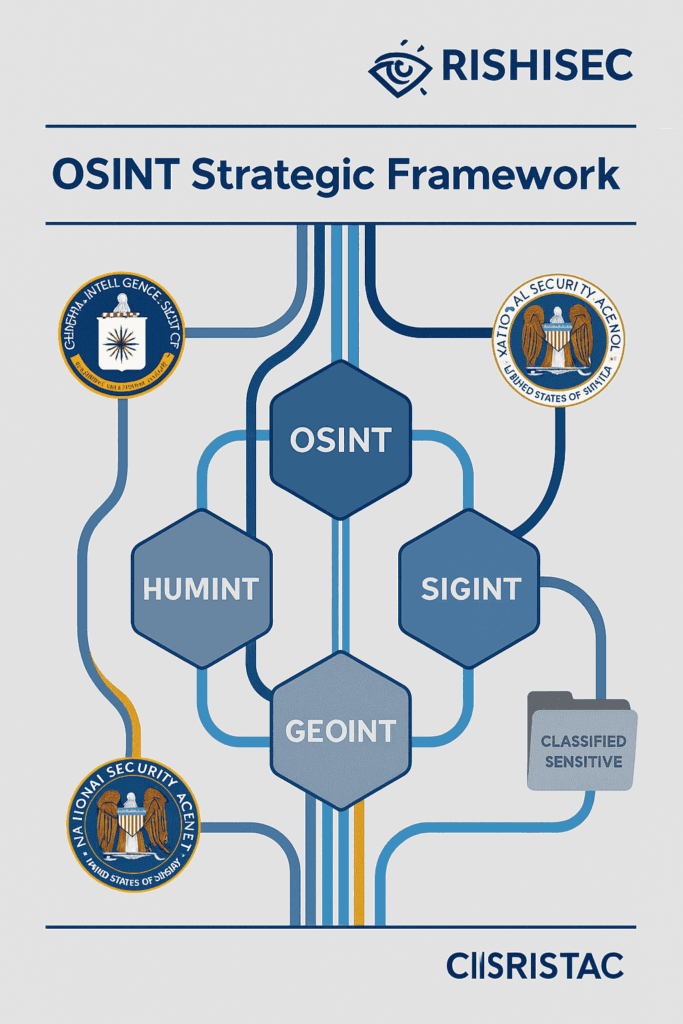
Government intelligence OSINT strategies require a structured approach that balances comprehensive coverage with operational security. Therefore, the most effective frameworks incorporate multiple intelligence disciplines while maintaining strict protocols for data handling and source protection.
The modern intelligence cycle has expanded beyond traditional collection phases. Subsequently, today’s government analysts must consider digital footprint management, cross-platform correlation, and real-time threat assessment capabilities. This evolution demands new methodologies that can process vast datasets while identifying actionable intelligence signals.
Advanced OSINT platforms like Kindi have revolutionized how government teams approach link analysis and data correlation. By automating time-intensive research processes, these tools allow analysts to focus on higher-level threat assessment and strategic planning rather than manual data collection.
Furthermore, effective government intelligence OSINT strategies must account for adversarial awareness. Sophisticated threat actors actively monitor their digital exposure, requiring intelligence teams to employ more subtle collection techniques and advanced analytical frameworks.
Advanced Collection Methodologies for Intelligence Teams

Modern collection techniques extend far beyond basic social media monitoring. Therefore, government intelligence professionals must master multi-layered approaches that can penetrate sophisticated operational security measures while maintaining legal compliance.
Network analysis has become particularly valuable for understanding complex threat structures. By mapping relationships between digital identities, communication patterns, and infrastructure elements, analysts can uncover hidden connections that traditional methods might miss. This approach proves especially effective when implementing OSINT for law enforcement investigations, where understanding criminal networks is crucial.
Technical collection methods now include advanced image analysis, metadata extraction, and cross-reference validation across multiple platforms simultaneously. However, these techniques require specialized training and careful implementation to avoid detection by adversarial surveillance systems.
Government teams increasingly rely on collaborative intelligence platforms that enable secure information sharing between departments and allied agencies. These systems must balance accessibility with strict security protocols to protect sensitive sources and methods.
Threat Intelligence Integration and Analysis
Effective government intelligence OSINT strategies depend on seamless integration with existing threat intelligence frameworks. Consequently, this integration enables analysts to correlate open source findings with classified intelligence streams, creating more comprehensive threat assessments.
Real-time monitoring capabilities have become essential for tracking evolving threats. Government agencies must implement systems that can detect emerging patterns across multiple data sources while filtering out noise and false positives. This is particularly important when integrating OSINT to prioritize alerts in SOC environments.
Advanced analytical techniques include behavioral pattern recognition, temporal analysis, and predictive modeling based on historical threat data. These methods help intelligence teams anticipate potential security risks before they materialize into active threats.
Cross-platform correlation represents another critical capability. Modern threats often span multiple digital environments, requiring analysts to track activities across social networks, forums, messaging platforms, and technical infrastructure simultaneously.
Military and Defense Applications
Government intelligence OSINT strategies must also address military applications and battlefield intelligence requirements. Military teams require specialized approaches that can support tactical operations while maintaining strategic awareness of global threat landscapes.
The integration of OSINT with traditional military intelligence disciplines creates powerful analytical capabilities. For instance, military teams use OSINT to boost threat intelligence and battlefield awareness through real-time monitoring of adversarial communications and infrastructure changes.
Additionally, defense contractors and supply chain security represent critical areas where government intelligence OSINT strategies must evolve. Understanding global defense networks and potential vulnerabilities requires sophisticated analytical frameworks that can process complex relationship data.
According to recent U.S. Intelligence Community assessments, the integration of OSINT capabilities across military and civilian intelligence agencies has significantly enhanced national security posture and threat detection capabilities.
Operational Security and Legal Compliance
Government intelligence OSINT strategies must prioritize operational security while maintaining strict adherence to legal and ethical guidelines. This balance requires careful protocol development and ongoing team training to ensure compliance with privacy regulations and constitutional protections.
Attribution challenges represent a significant concern for government intelligence operations. Analysts must verify source authenticity while protecting their own investigative methods from detection by sophisticated adversaries.
Data retention and handling protocols require special attention in government environments. Teams must implement secure storage systems that protect collected intelligence while enabling authorized access for ongoing investigations and analysis.
International cooperation frameworks add another layer of complexity. Government agencies must navigate varying legal jurisdictions while maintaining effective information sharing relationships with allied intelligence services. The Cybersecurity and Infrastructure Security Agency (CISA) provides essential guidance for maintaining security standards while enabling effective intelligence sharing.
Implementation Checklist for Government OSINT Programs
The successful implementation of government intelligence OSINT strategies requires systematic planning and effective allocation of resources. Consider these essential elements:
- Establish secure collection infrastructure with appropriate legal safeguards and constitutional protections
- Develop comprehensive analyst training programs covering advanced OSINT techniques and specialized tools
- Implement automated monitoring systems for high-priority threat indicators and emerging risks
- Create secure collaboration platforms for multi-agency intelligence sharing and coordination
- Design data retention policies that balance operational needs with legal requirements
- Establish robust source verification protocols to ensure intelligence authenticity and reliability
- Develop comprehensive operational security measures to protect collection methods and sources
- Create regular assessment procedures to evaluate program effectiveness and identify improvements
Additionally, government teams should consider specialized training programs that keep analysts current with evolving OSINT methodologies and emerging threats.
Technology Integration and Future Planning
The future of government intelligence OSINT strategies lies in the integration of artificial intelligence and the development of automated analysis capabilities. Machine learning algorithms can process vast datasets at unprecedented speeds while identifying subtle patterns that human analysts might overlook.
However, technology integration must be carefully balanced with human expertise. While AI can enhance collection and initial analysis, experienced analysts remain essential for contextual interpretation and strategic assessment.
Government agencies should also prepare for emerging challenges including deepfake detection, encrypted communication analysis, and quantum-resistant security measures. These evolving threats require proactive planning and continuous capability development.
Investment in next-generation OSINT platforms will be crucial for maintaining competitive advantages. Tools that offer advanced link analysis, automated correlation, and secure collaboration features will become increasingly valuable for government intelligence operations.
FAQ
What makes government intelligence OSINT strategies different from those in the private sector?
Government intelligence OSINT strategies operate under stricter legal frameworks and must balance public safety concerns with constitutional protections. Furthermore, government teams have access to specialized resources and inter-agency collaboration capabilities that private organizations cannot access.
How can government agencies ensure OSINT compliance with privacy laws?
Compliance requires comprehensive training, clear operational guidelines, and regular legal review of collection methods. Additionally, agencies must establish protocols that respect privacy rights while enabling effective threat detection and investigation capabilities.
What are the most critical skills for government OSINT analysts?
Essential skills include technical research capabilities, analytical thinking, awareness of legal compliance, and operational security consciousness. Moreover, analysts need strong communication skills to translate complex findings into actionable intelligence reports.
How should government agencies assess the effectiveness of OSINT tools?
Evaluation should focus on accuracy, speed, security features, and integration capabilities with existing systems. Therefore, agencies should also consider vendor reliability, the quality of ongoing support, and compliance with government security standards.
Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training. Ready to revolutionize your intelligence operations? Discover how Kindi can streamline your OSINT investigations and enhance your team’s analytical capabilities.