Intelligence agencies face an unprecedented challenge. Digital threats multiply faster than human analysts can process them, and the volume of open source intelligence continues to grow exponentially. Special agents, cyber crime unit leads, and senior intelligence analysts need systematic approaches that maintain security clearances while accelerating investigations.
The traditional manual approach to OSINT collection creates operational bottlenecks that adversaries exploit. When analysts spend 70% of their time on data collection and only 30% on analysis, critical threats slip through undetected. Intelligence agency OSINT workflow automation addresses this imbalance by systematizing collection, enrichment, and analysis processes while maintaining strict compliance protocols.
Understanding Modern Intelligence Collection Requirements
Government intelligence operations require specialized OSINT frameworks that balance operational security with investigative speed. Unlike commercial investigations, classified environments demand air-gapped systems, compartmentalized access, and rigorous audit trails. These requirements create unique automation challenges that standard tools cannot address.
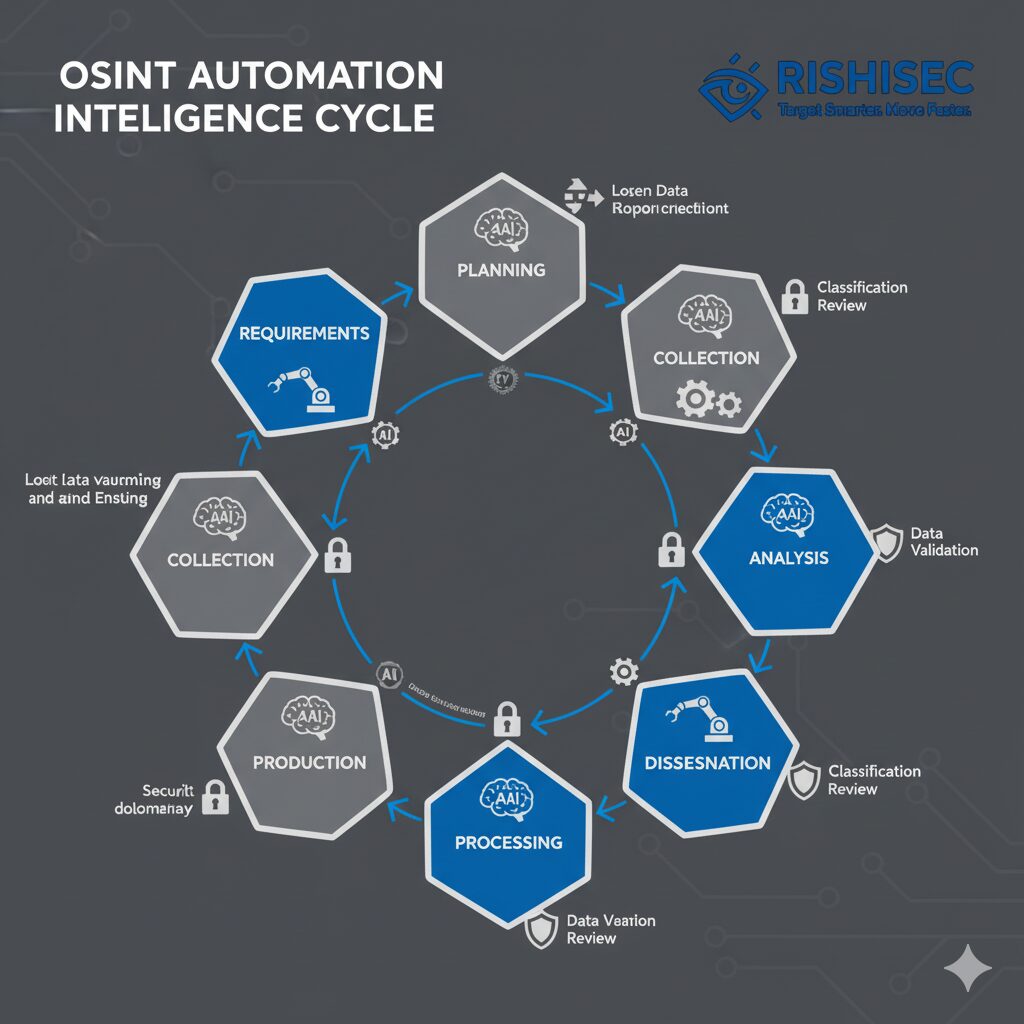
The intelligence cycle framework provides the foundation for effective automation. Modern platforms must support requirements definition, collection planning, automated data gathering, processing workflows, analytical tools, production systems, and secure dissemination channels. Each phase requires specific automation capabilities while maintaining classification boundaries and need-to-know principles.
Senior intel analysts at the Defense Intelligence Agency report that automation reduces collection time from weeks to hours while improving data quality through systematic verification protocols. Essential intelligence frameworks form the backbone of these automated workflows, ensuring consistency across distributed teams.
Building Secure Automation Workflows for Classified Environments
Intelligence agencies require automation architectures that operate within secure enclaves while accessing open source intelligence from unclassified networks. This dual-network challenge demands careful architectural planning and robust security controls.
| Workflow Component | Security Requirement | Automation Capability | Classification Level |
|---|---|---|---|
| Collection Tasking | Role-based access control | Automated queue management | Unclassified to Secret |
| Data Acquisition | Cross-domain solutions | Scheduled collection runs | Unclassified sources only |
| Processing Pipeline | Air-gapped processing | Enrichment and validation | Secret to Top Secret |
| Analysis Platform | Compartmented access | Link analysis and correlation | Secret to TS/SCI |
| Report Production | Automatic classification | Template-based generation | Secret to Top Secret |
| Dissemination | Need-to-know enforcement | Automated distribution lists | Compartmented channels |
Kindi’s AI-powered platform addresses these classified environment requirements through modular deployment options that separate collection, processing, and analysis components. Special agents can deploy collection modules on unclassified systems while maintaining analysis capabilities within secure enclaves, with automated data transfer through approved cross-domain solutions.
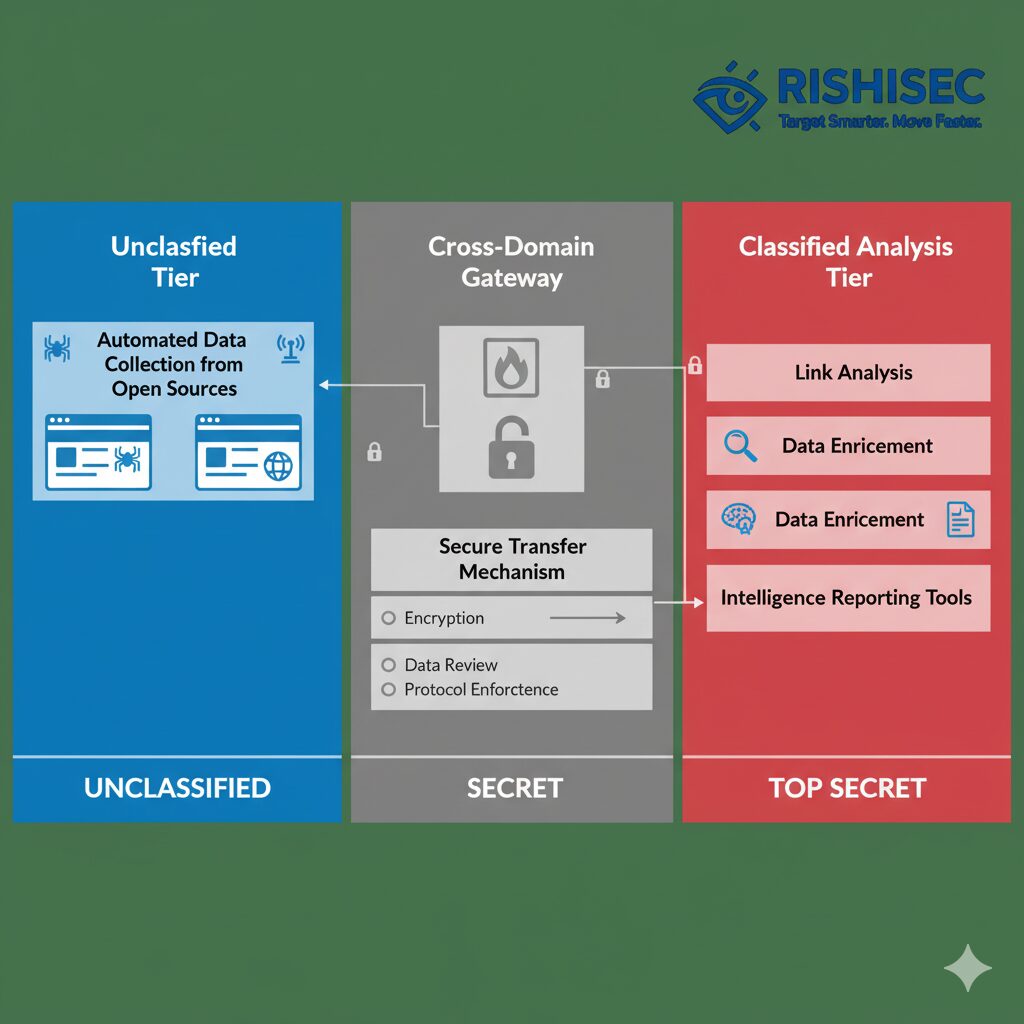
Implementing Automated Correlation and Link Analysis
The true power of intelligence automation emerges in correlation and link analysis capabilities. When multiple data sources converge on potential threats, automated systems can identify connections that human analysts might miss. This capability becomes critical when investigating transnational organized crime, terrorist networks, or state-sponsored cyber operations.
Cyber crime unit leads leverage automated correlation to connect seemingly unrelated indicators across multiple investigations. A suspicious financial transaction in one case might link to a known threat actor from another investigation, revealing a broader criminal enterprise. However, these connections only surface when automation systems can analyze patterns across large datasets while respecting compartmentation boundaries.
Link analysis automation transforms raw intelligence into actionable insights by mapping relationships between entities, events, and indicators. Advanced platforms use graph databases to store relationship data, enabling complex queries that would be impossible with manual methods. When combined with machine learning algorithms, these systems can predict likely connections and surface high-priority leads for analyst review.
Government teams working on tracking criminal networks find that automated link analysis reduces investigation timelines by identifying key nodes and communication patterns that manual analysis would take months to uncover.
Establishing Compliance Frameworks for Automated Collection
Intelligence automation must operate within strict legal and policy frameworks that govern government collection activities. The legal landscape includes Executive Order 12333, Attorney General Guidelines, and agency-specific directives that restrict certain collection methods and require oversight mechanisms.
Automated compliance frameworks embed legal restrictions directly into collection workflows. Before initiating any collection activity, the system validates collection authority, confirms proper approvals exist, and logs all activities for oversight review. This automation ensures consistency across distributed teams and reduces legal risk.
Senior intel analysts must configure retention policies that align with agency records schedules and legal hold requirements. Automated systems can enforce these policies by flagging data for review at predetermined intervals and preventing deletion of materials under legal hold. The audit trail created by these systems provides the documentation necessary for oversight reviews and legal proceedings.
For agencies developing comprehensive approaches, understanding OSINT compliance requirements ensures automation systems meet both operational needs and legal obligations from initial deployment.
Measuring Operational Impact Through Intelligence Metrics
Intelligence agencies require objective metrics to evaluate automation effectiveness and justify resource investments. Traditional metrics like collection volume fail to capture automation’s true impact on intelligence production quality and timeliness.
Effective automation metrics track multiple dimensions simultaneously. Collection efficiency measures the ratio of relevant intelligence to total data collected, with higher ratios indicating better targeting. Processing speed tracks time from collection to analyst review, while analysis depth measures the average number of enrichment steps applied to each intelligence item. Production velocity captures time from initial lead to finished intelligence product.
These metrics reveal automation’s compound benefits. When collection becomes more targeted, analysts spend less time filtering irrelevant data. When processing accelerates, time-sensitive intelligence reaches decision-makers while still actionable. When analysis deepens through automated enrichment, intelligence products gain strategic value beyond tactical reporting.
- Track collection-to-intelligence conversion rates to optimize automated targeting and reduce noise in analyst queues.
- Monitor processing pipeline performance to identify bottlenecks and maintain service level agreements for priority intelligence.
- Measure analyst productivity changes to quantify automation’s impact on investigation capacity and case closure rates.
- Calculate cost per intelligence product to demonstrate return on investment and support budget justification for automation programs.
- Assess intelligence product timeliness to ensure automated workflows meet operational tempo requirements for dynamic threats.
Integrating Automation with Existing Intelligence Systems
Government intelligence agencies operate complex technology ecosystems built over decades. Successful automation must integrate with legacy systems, intelligence community tools, and classified networks without requiring complete infrastructure replacement.
Modern automation platforms use API-based architectures that connect with existing systems through standardized interfaces. Intelligence analysts continue using familiar tools while automation handles routine tasks in the background. This approach minimizes training requirements and accelerates adoption across teams with varying technical capabilities.
Special agents working across multiple agencies benefit from automation platforms that support intelligence community standards like STIX/TAXII for threat intelligence sharing. When automated systems can import and export data using community standards, cross-agency collaboration becomes seamless and reduces duplication of effort.
Organizations implementing automation alongside modern intelligence practices find that integration challenges decrease significantly when platforms prioritize standards compliance and offer flexible deployment options that accommodate existing security architectures.
FAQ
How do intelligence agencies maintain operational security when automating OSINT collection?
Agencies deploy automated collection tools on unclassified networks with one-way data transfers to classified analysis environments through approved cross-domain solutions. Collection activities use attributed personas separate from operational identities, and all systems maintain comprehensive audit logs for security reviews. Modern platforms like Kindi support air-gapped deployments that physically separate collection and analysis functions.
What automation capabilities matter most for government intelligence workflows?
Priority capabilities include automated data collection from diverse sources, enrichment through multiple intelligence databases, entity resolution across datasets, relationship mapping for link analysis, classification management, and audit logging for compliance. Systems must support role-based access control and operate within classified environments while maintaining performance at scale.
How long does implementing intelligence automation typically require?
Pilot deployments focused on specific use cases can launch within 30-60 days, while enterprise-wide implementations across multiple teams and security domains typically require 6-12 months. Timeline factors include security approval processes, integration with existing systems, training requirements, and policy development for automated collection authorities.
Can automated OSINT systems operate in air-gapped classified environments?
Yes, modern platforms support on-premises deployment in air-gapped networks with automated collection occurring on separate unclassified systems. Data transfers use approved cross-domain solutions with automated sanitization and classification marking. Analysis and production functions operate entirely within the classified environment without external network dependencies.
What compliance frameworks govern automated intelligence collection for government agencies?
Government intelligence automation must comply with Executive Order 12333, Attorney General Guidelines for domestic intelligence operations, agency-specific directives, federal records retention requirements, and intelligence oversight policies. Automated systems embed these requirements through collection authority validation, approval workflows, retention management, and comprehensive audit trails.
How does automation affect intelligence analyst roles and responsibilities?
Automation shifts analysts from routine collection and processing tasks toward higher-value analytical work, strategic assessment, and intelligence production. Analysts become collection managers who configure and monitor automated systems rather than performing manual searches. This evolution requires training in automation tools and analytical methodologies that leverage machine-generated insights.
Ready to modernize your intelligence operations? Explore Kindi’s government-grade OSINT automation platform designed specifically for classified environments and intelligence community requirements.
Want to develop advanced intelligence tradecraft? Check out our OSINT courses covering automation strategies, link analysis methodologies, and operational security for intelligence professionals.