Red team operations demand reconnaissance that leaves zero traces. Traditional penetration testing methods often trigger detection systems; however, advanced red team OSINT reconnaissance techniques enable operators to build comprehensive target profiles without ever touching the network perimeter. The difference between getting caught and maintaining operational security often comes down to how effectively you leverage passive intelligence gathering.
Modern red team engagements require more than basic Google searches. Defenders have become sophisticated, security operations centers monitor for anomalies, and attackers who get detected early lose their advantage. Therefore, mastering passive OSINT reconnaissance has become non-negotiable for red team operators, penetration testers, and cybersecurity consultants who need to simulate real-world adversary tactics.
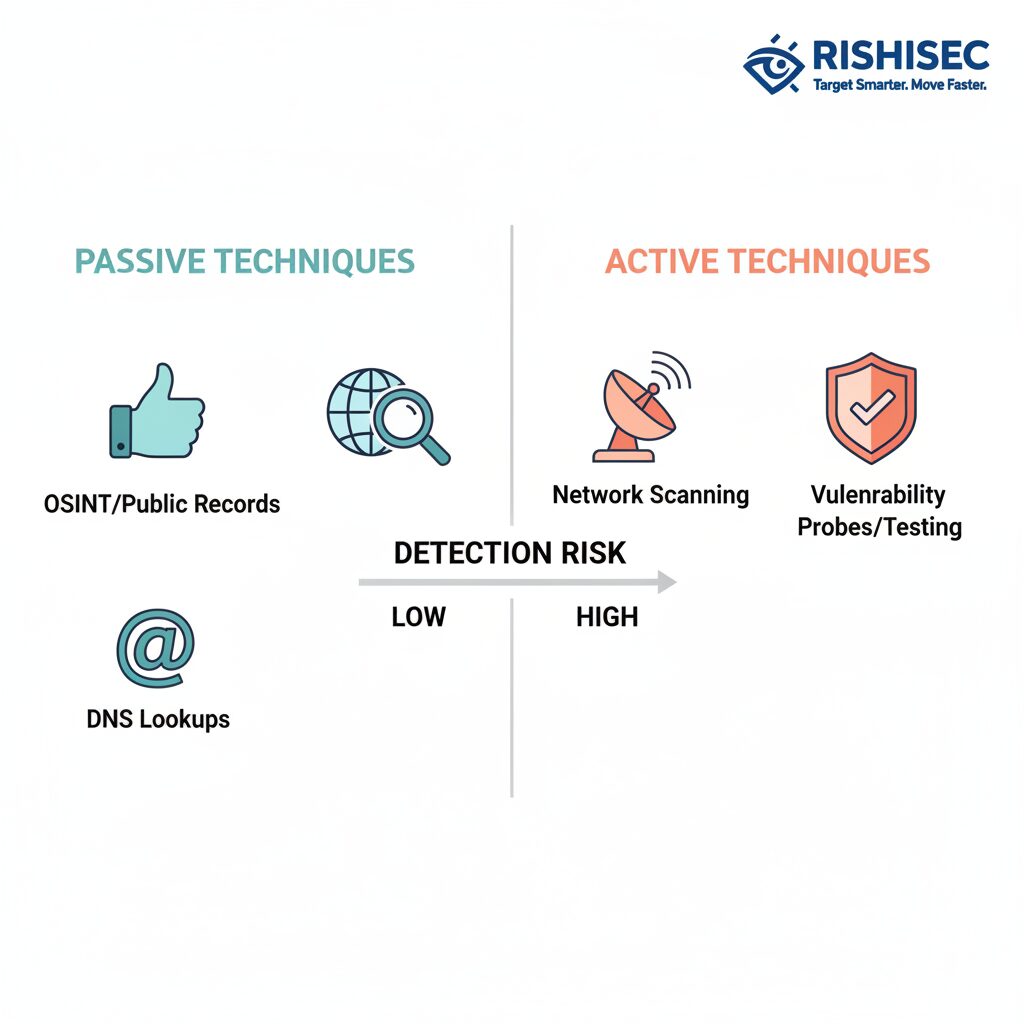
Understanding Passive vs Active Red Team OSINT Reconnaissance
Passive reconnaissance forms the foundation of every successful red team engagement. Unlike active scanning that sends packets directly to target systems, passive OSINT reconnaissance techniques gather intelligence from publicly available sources without alerting the target. This approach mirrors how sophisticated threat actors operate in the wild, making it essential for realistic security assessments.
The core principle separating passive from active reconnaissance is interaction. When you query DNS records, scrape social media profiles, or analyze public cloud storage buckets, you are conducting passive intelligence collection. However, when you port scan a server, send phishing emails, or probe web applications, you have crossed into active territory where detection becomes likely.
Red team OSINT reconnaissance typically follows a structured intelligence cycle. First, you define your objectives based on the engagement scope. Then, you identify information sources relevant to your target. Next comes collection, where you systematically gather data without triggering alarms. Processing involves organizing raw intelligence into usable formats, and analysis transforms data into actionable insights about vulnerabilities, personnel, infrastructure, and potential attack vectors.
Successful passive reconnaissance requires understanding what defenders can see. Security teams monitor for direct interactions: port scans, vulnerability probes, authentication attempts, and unusual traffic patterns. SOC analysts prioritize alerts based on behavioral signatures, which means your reconnaissance must blend with normal internet activity to remain undetected.
Critical OSINT Data Sources for Red Team Intelligence Gathering
Domain intelligence provides the starting point for most red team reconnaissance. WHOIS records reveal registration details, nameservers, and historical ownership information. DNS enumeration uncovers subdomains, mail servers, and infrastructure relationships without directly querying the target. Certificate transparency logs expose every SSL certificate ever issued for a domain, revealing forgotten subdomains and development environments that defenders may have overlooked.
Social media reconnaissance extends beyond simple profile browsing. Employee LinkedIn profiles reveal organizational structure, technology stacks, and potential social engineering targets. Twitter and GitHub activity expose development practices, internal tool usage, and sometimes accidental credential leaks. Reddit discussions and technical forums often contain detailed infrastructure information shared by IT staff seeking troubleshooting help.
| Intelligence Source | Information Revealed | Operational Value |
|---|---|---|
| Certificate Transparency Logs | Subdomains, internal hostnames, development servers | Expands attack surface, identifies forgotten assets |
| Job Postings | Technology stack, security tools, infrastructure details | Reveals defensive capabilities, informs tool selection |
| Public Cloud Storage | Exposed S3 buckets, Azure blobs, misconfigured permissions | Direct access to sensitive data, credentials, source code |
| Code Repositories | API keys, passwords, infrastructure configurations | Immediate compromise vectors, architecture understanding |
| Internet Archives | Historical website versions, deleted content, old vulnerabilities | Identifies persistent weaknesses, legacy systems |
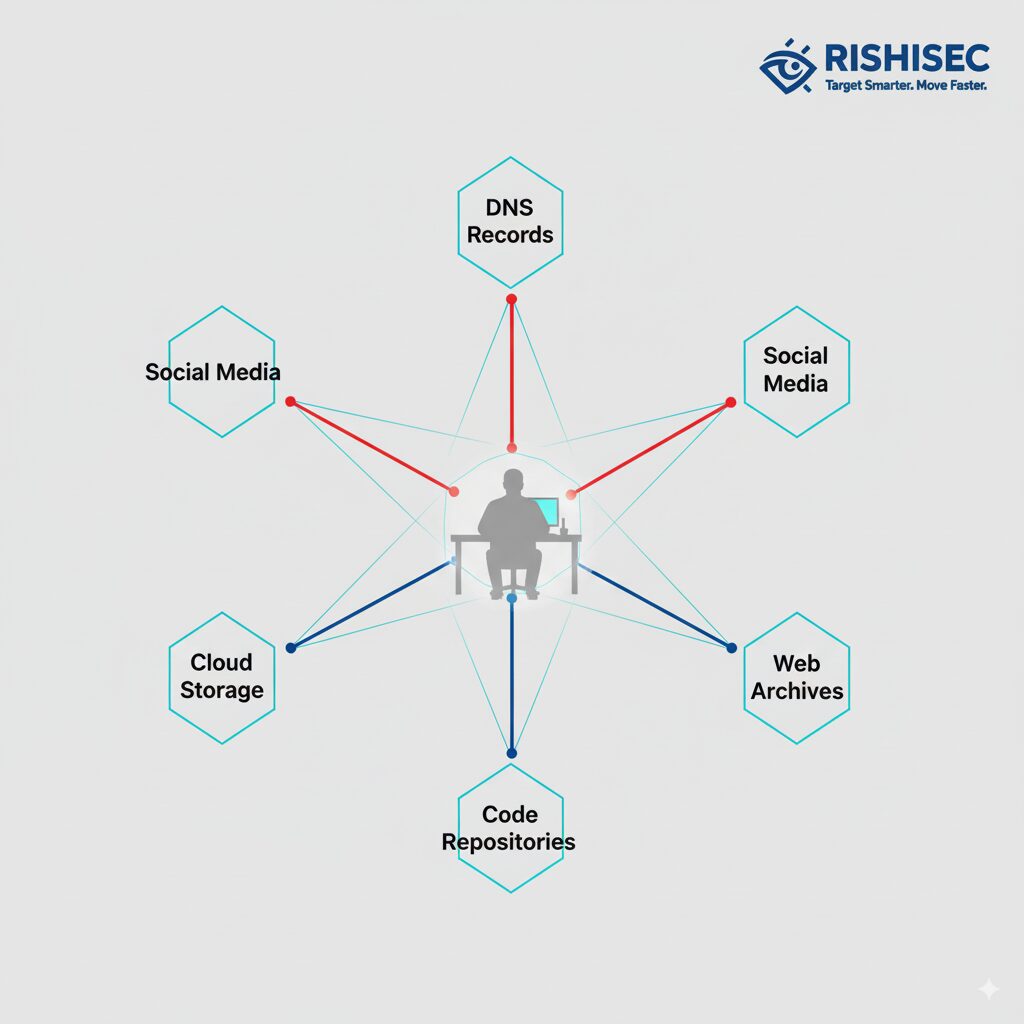
Public code repositories deserve special attention during red team OSINT reconnaissance. Developers frequently commit configuration files containing database credentials, API keys, and internal hostnames. Even after deletion, Git history preserves these secrets indefinitely. Automated scanning tools can process thousands of repositories searching for specific patterns, but manual review often uncovers context that automated tools miss.
Technical documentation and support forums provide unexpected intelligence goldmines. Stack Overflow posts detail specific error messages that reveal software versions and configurations. Technical blogs written by target employees describe infrastructure decisions and security implementations. Conference presentations and webinar recordings sometimes include architecture diagrams that would normally require months of reconnaissance to reconstruct.
Automation and AI-Powered OSINT for Red Team Operations
Manual reconnaissance cannot keep pace with modern engagement timelines. Red teams typically have limited time to build target profiles before active testing begins. Automation bridges this gap by continuously collecting, processing, and correlating intelligence while operators focus on analysis and planning.
Modern OSINT automation goes beyond simple web scraping. AI-powered platforms analyze relationships between disparate data points, identifying patterns that human analysts might miss. Machine learning models can predict infrastructure based on partial information, suggest likely vulnerabilities based on technology fingerprints, and prioritize intelligence based on attack potential.
Platforms like Kindi transform red team OSINT reconnaissance by automating the intelligence collection cycle. Instead of manually querying dozens of sources, operators define their targets and let AI-driven automation handle systematic data gathering. Link analysis capabilities connect employees to infrastructure, infrastructure to vulnerabilities, and vulnerabilities to potential attack paths, creating a visual intelligence map that accelerates target profiling.
Automation also solves the temporal challenge in red team operations. Targets evolve constantly as they deploy new systems, hire personnel, and modify infrastructure. Continuous automated monitoring detects these changes in real-time, ensuring your intelligence remains current throughout the engagement. However, automation requires careful operational security configuration to prevent reconnaissance tools from inadvertently alerting the target.
Advanced Techniques: Stealth, Opsec, and Avoiding Detection
Operational security separates amateur reconnaissance from professional red team intelligence gathering. Every query you make, every page you visit, and every API you call generates logs that defenders can analyze. Sophisticated security teams correlate reconnaissance patterns to identify potential threats before they materialize into attacks.
Network attribution represents your first opsec challenge. Reconnaissance from your home IP address or corporate network creates a direct link to your identity. Professional red team operators use residential proxies, VPN chains, and cloud-based infrastructure to anonymize their intelligence collection. However, simple VPN usage is not sufficient as many providers maintain detailed logs and respond to legal requests.

Timing patterns reveal reconnaissance activity to alert analysts. Automated tools that query resources too quickly or too systematically create signatures that security systems flag. Effective reconnaissance mimics human behavior through randomized delays, varied query patterns, and distributed collection across multiple timeframes. Additionally, respecting robots.txt and avoiding aggressive crawling prevents your activity from triggering rate-limiting or abuse-detection systems.
Browser fingerprinting poses another detection vector that many operators overlook. Websites collect detailed information about your browser configuration, installed extensions, screen resolution, and dozens of other characteristics that create unique fingerprints. Anti-fingerprinting measures include using clean browser profiles, disabling JavaScript when possible, and routing traffic through browser automation frameworks that normalize fingerprints.
Counter-intelligence awareness is crucial during red team OSINT reconnaissance. Sophisticated targets deploy honeytokens, false information designed to detect reconnaissance activity. Fake employee profiles on LinkedIn, deliberately exposed but monitored credentials, and intentionally misconfigured systems can all serve as tripwires. OSINT deception requires careful validation of intelligence before trusting it for operational planning.
Building Reconnaissance Workflows That Scale
Structured workflows transform scattered reconnaissance into systematic intelligence operations. Professional red teams document their processes, creating repeatable methodologies that new team members can follow and that engagements can reproduce consistently. Workflow documentation also facilitates quality assurance, ensuring no critical intelligence sources get overlooked during time-pressured engagements.
Intelligence prioritization determines where operators focus their limited time. Not all reconnaissance findings carry equal weight for red team operations. Exposed credentials provide immediate access, while organizational charts inform social engineering. Outdated software versions suggest specific vulnerabilities, and network architecture details guide lateral movement planning. Effective workflows triage findings based on operational impact.
Collaboration becomes essential when multiple operators work the same engagement. Shared intelligence repositories prevent duplicate work and ensure all team members access the same information. However, collaboration tools must maintain operational security, encrypting data at rest and in transit while providing access controls that limit exposure if credentials become compromised.
Reporting transforms raw intelligence into actionable briefings for both red team operators and client stakeholders. Operators need technical details: IP addresses, vulnerable systems, credential findings, and attack paths. Clients need strategic context: what the intelligence reveals about their security posture, how it compares to industry peers, and which findings represent the highest risk.
Practical Red Team OSINT Reconnaissance Checklist
Successful reconnaissance follows structured processes that ensure comprehensive coverage while maintaining operational security. The following checklist provides a framework for systematic intelligence gathering during red team engagements.
- Define clear intelligence requirements based on engagement objectives and rules of engagement
- Establish operational security baseline including attribution controls and detection avoidance measures
- Enumerate all target domains, subdomains, and associated infrastructure through passive DNS and certificate transparency
- Map organizational structure through employee social media profiles, particularly LinkedIn and Twitter
- Identify technology stack through job postings, conference talks, and technical blog posts
- Search public code repositories for credentials, configuration files, and infrastructure documentation
- Scan for exposed cloud storage buckets across AWS, Azure, and Google Cloud platforms
- Review internet archives for historical website versions and deleted content
- Monitor technical forums and support channels for infrastructure details and troubleshooting discussions
- Document all findings in a centralized repository with source attribution and collection timestamps
- Validate intelligence through cross-referencing multiple sources before operational use
- Maintain continuous monitoring for new intelligence throughout the engagement duration
FAQ
What makes OSINT reconnaissance passive versus active?
Passive OSINT reconnaissance gathers intelligence from publicly available sources without directly interacting with target systems. You collect information that already exists online without sending any traffic to the target network. Active reconnaissance involves direct interaction like port scanning, vulnerability testing, or probing applications, which generates logs on target systems that defenders can detect.
How long should red team reconnaissance take before active testing?
Reconnaissance duration depends on engagement scope and timeline, but typically ranges from several days to two weeks for enterprise targets. Rushing reconnaissance leads to incomplete intelligence that compromises later attack phases. However, excessive reconnaissance can delay active testing and reduce the time available for exploitation. Most red teams conduct intensive initial reconnaissance followed by continuous passive monitoring throughout the engagement.
Can automation replace manual OSINT analysis in red team operations?
Automation accelerates data collection and correlation but cannot fully replace human analysis. AI-powered tools excel at processing large datasets, identifying patterns, and connecting disparate intelligence. However, understanding context, validating findings, and making strategic decisions about attack paths require the experienced judgment of an operator. The most effective red team OSINT reconnaissance combines automated collection with expert analysis.
What legal considerations affect red team OSINT reconnaissance?
Even passive reconnaissance must respect legal boundaries defined in your engagement contract. Rules of engagement specify which systems, domains, and subsidiaries fall within scope. Reconnaissance that exceeds these boundaries can violate computer fraud laws even if no active exploitation occurs. Additionally, some jurisdictions restrict specific OSINT techniques like social media scraping or automated data collection. Always obtain written authorisation and a clearly defined scope before beginning reconnaissance.
How do you maintain operational security during extended reconnaissance operations?
Operational security requires multiple layers of protection. Use dedicated infrastructure isolated from your primary identity, route traffic through anonymizing services that do not maintain logs, and employ browser fingerprinting countermeasures. Vary your reconnaissance timing and patterns to avoid creating detectable signatures. Never use personal accounts or credentials during reconnaissance. Finally, assume sophisticated targets deploy honeytokens and counter-intelligence measures designed to detect reconnaissance activity.
Want to strengthen your OSINT skills and accelerate your red team reconnaissance? Check out our OSINT courses for practical, hands-on training that covers advanced intelligence gathering techniques. Ready to automate your reconnaissance workflow? Explore Kindi and discover how AI-powered OSINT can transform your red team operations.
