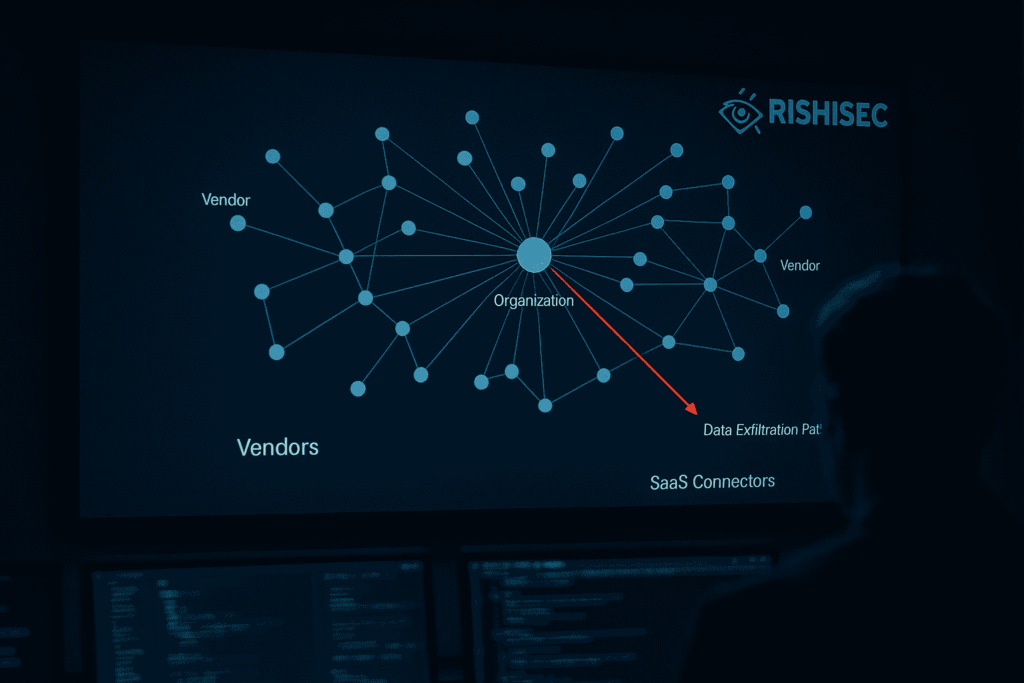
Supply chain cyber attacks are now the front door for modern intrusions. The 2025 Allianz case demonstrates how a trusted vendor path, combined with social engineering, can circumvent hardened perimeters and expose sensitive data on a large scale. This article distills the incident into a consultant-grade playbook you can apply across client environments today. The focus is practical; you will find controls, workflows, and OSINT techniques that reduce exposure, accelerate investigations, and raise resilience.
RishiSec provides OSINT solutions for practitioners. Our platform Kindi automates OSINT investigations, visual link analysis, and collaboration, so consultants can move from signal to insight quickly and consistently.
Why This Supply Chain Cyber Attack Matters in 2025
The Allianz breach was not a traditional perimeter failure. Instead, attackers leveraged a third-party SaaS workflow and persuaded employees to approve data access. Because trust expands through vendors, a small approval can unlock large datasets. Consequently, the impact echoes across identity theft, fraud operations, and follow-on phishing. For cybersecurity consultants, this is a priority scenario to test and fix, since most enterprises depend on complex vendor ecosystems.
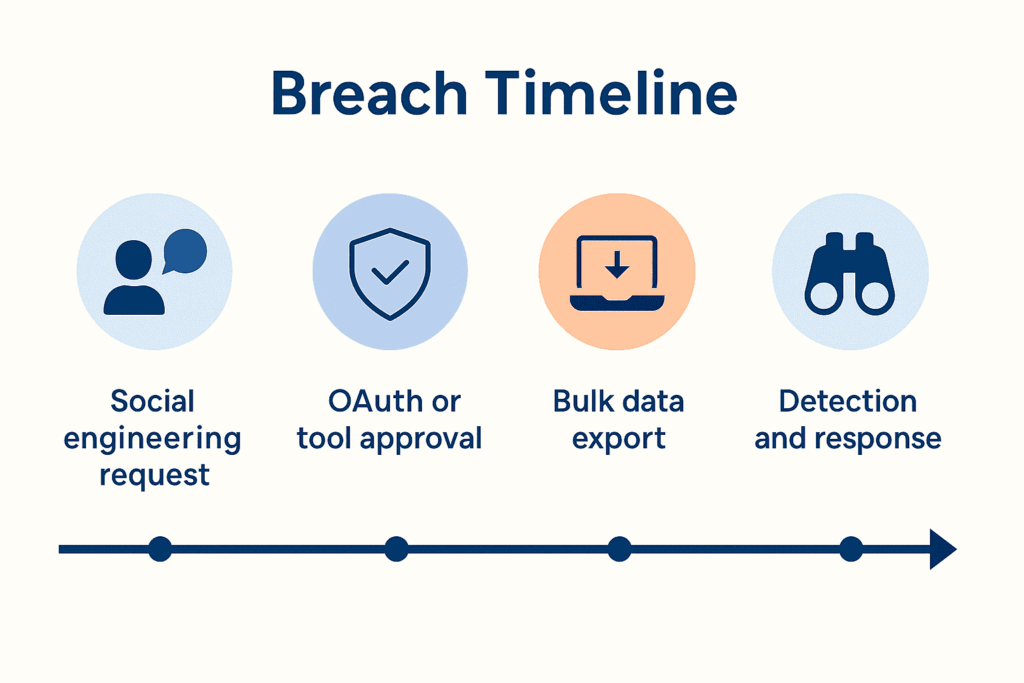
Breach Overview: Condensed Timeline and Tactics
Reports indicate an initial approach through social engineering; employees believed they were helping IT with a legitimate access flow. Next, a vendor-integrated data export tool enabled bulk extraction of sensitive records. Discovery and containment followed quickly, which is positive, yet the path to data remained open long enough to matter. Therefore, the lesson is clear; a supply chain cyber attack can succeed even when dwell time is short, if data export controls are weak.
For background reading on OSINT-driven investigations relevant to insurance and fraud, see Insurance Fraud Detection with OSINT and our guide on Using OSINT to Prioritize Alerts in SOC Environments. These articles help you prepare analytic workflows that turn breach indicators into investigative leads.
Root Cause: Vendor Access, SaaS Connectors, and Human Factors
The root cause pattern is familiar. Third-party SaaS integrations hold broad data access; approval flows feel routine; human trust is exploited. Attackers aim for an approval that looks normal. Once granted, a data loader or export interface can retrieve large volumes fast. This is not an edge case; it is now standard tradecraft. As a result, consultants should tune assessments to find where vendor scopes, OAuth grants, and export jobs exceed business need.
Defining a Supply Chain Cyber Attack in 2025
A supply chain cyber attack exploits a supplier, SaaS vendor, managed service, or contractor to reach target data. The attack path often involves normal business integrations. Because the target organization already trusts the vendor, controls may be lighter at the seams. Consultants should treat these seams as primary security perimeters and not as secondary coverage areas.
Data Exposure and Downstream Risk
Insurance data often combines identity markers with policy metadata. That combination is valuable to fraud rings. It enables targeted phishing and synthetic identity schemes. After a breach, criminals correlate these fields with older credential leaks, then craft convincing lures. In practice, a modest data set can fuel a large campaign, which makes early detection and damage control essential.
To frame response decisions, many teams use MITRE ATT&CK as a shared language. Techniques related to phishing and data exfiltration provide useful checklists during incident review. Guidance from the CISA Supply Chain Risk Management program also helps you align prevention with procurement and governance.
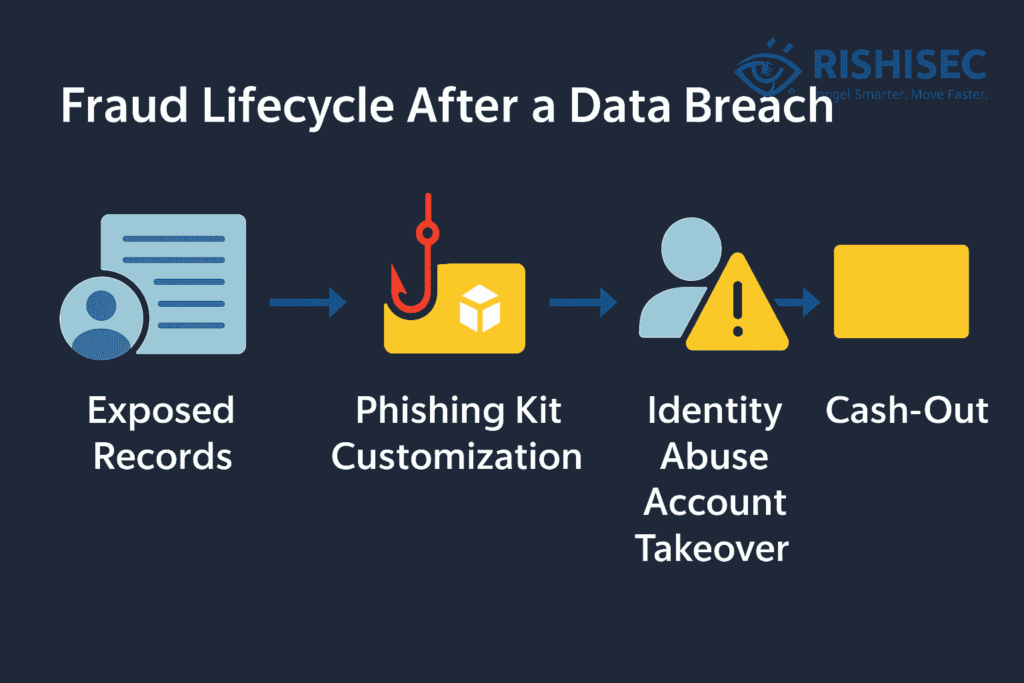
Consultant Playbook: Controls That Stop Supply Chain Cyber Attacks
The following controls are practical, testable, and measurable. They can be added to assessments, fixed in sprints, and verified in tabletop exercises. Use this section as an implementation checklist during client engagements, and adapt language for executive briefings.
| Control | Risk Addressed | What To Verify |
|---|---|---|
| Least-Privilege Vendor Scopes | Overbroad SaaS access | Per-app scopes, no wildcard grants, quarterly scope review |
| Block Unapproved Data Loaders | Bulk data export misuse | Allowlist of tools, change control, alert on new connectors |
| High-Risk Action MFA | Social engineering of approvals | Step-up MFA for approvals and export jobs |
| Exfiltration Analytics | Silent bulk export | API pagination anomalies, volume spikes, off-hours runs |
| Helpdesk Hardening | Impersonated IT staff | No approvals by chat or phone without second verifier |
OSINT and Link Analysis With Kindi
Kindi accelerates investigations when minutes matter. Analysts can map vendors, identities, and infrastructure on an interactive link graph; correlate breach chatter with exposed records; and build a repeatable workflow that less experienced staff can run. Because the platform supports timeline and geo mapping, it becomes easier to sequence access approvals, data pulls, and actor activity. Therefore, you reduce dwell time and move faster from suspicion to containment.
Quick Wins and Consultant Tips
- Inventory all active vendor connectors, then disable test or legacy integrations that touch sensitive data.
- Require step-up MFA for data exports and access grants; verify that helpdesk workflows enforce this policy.
- Instrument SaaS audit logs, then alert on anomalous API usage, especially off-hours or high-volume pulls.
- Run tabletop exercises that simulate a vendor approval request; measure time to containment and communication clarity.
- Align procurement with security; contracts should mandate evidence of controls and timely incident reporting.
Implementation Roadmap for Client Engagements
Consultants succeed when they deliver outcomes in short cycles. The roadmap below sequences discovery, fixes, and validation. Use it as a template, then tailor it to the client’s SaaS stack and vendor profile.
- Week 1, Discovery: Gather SaaS connector list, OAuth grants, export tools; pull 90 days of audit logs. Prioritize vendors by data sensitivity and scope size.
- Week 2, Hardening: Remove unused connectors; restrict scopes; enable step-up MFA for approvals and exports; establish an allowlist of data loaders.
- Week 3, Detection: Add alerts for volume spikes, pagination anomalies, new connector installs, and off-hours exports; route alerts to on-call with clear runbooks.
- Week 4, Validation: Run a tabletop based on a realistic supply chain cyber attack; verify escalation paths and executive communications.
For hands-on research techniques that support each phase, review Mastering OSINT for Red Teams. If your work aligns with SOC operations, this primer on integrating OSINT into SOC triage explains how to connect external signals to alert prioritization.
How This Case Fits the Bigger Picture
The Allianz incident is part of a broader shift where vendors and SaaS tools act as familiar pathways into critical data. Threat actor tradecraft evolves; however, business processes evolve more slowly. Because approvals, connectors, and exports are routine, they can be weaponized. With rigorous vendor governance and precise SaaS controls, the attack surface shrinks. With strong OSINT workflows and link analysis, your team sees the signal earlier and acts with more confidence.
For timely industry context, you can cross-reference coverage from reliable outlets such as Reuters and specialized security reporting from SecurityWeek. These sources help benchmark response timelines, attacker themes, and sector impacts without relying on vendor marketing.
Ready to map vendor risk and accelerate breach investigations with OSINT automation and link analysis? Explore Kindi, request a demo, or start a pilot with your team.
Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training.
FAQ
What is a supply chain cyber attack?
It is an intrusion that uses a supplier, SaaS vendor, managed service, or contractor to reach target data or systems. Because the victim already trusts the vendor, attackers exploit normal business integrations to move quickly.
Which controls block vendor-enabled data exports?
Block unapproved data loaders, restrict OAuth scopes, require step-up MFA for approvals and exports, and alert on anomalous API usage. In addition, verify these controls during tabletop exercises and incident rehearsals.
How does Kindi help during investigations?
Kindi provides automated OSINT enrichment, link graphs of vendors and identities, and timeline views. Therefore, analysts can see relationships, sequence events, and package evidence for leadership and legal teams without delay.