Insurance fraud costs the industry over $308 billion annually, making it one of the most expensive white-collar crimes in the United States. Consequently, modern insurance fraud schemes have evolved far beyond simple claim exaggeration, now involving sophisticated digital deception networks, coordinated staged accidents, and elaborate false identity operations that traditional investigation methods struggle to detect.
Open Source Intelligence has revolutionized insurance fraud investigation by providing investigators with unprecedented visibility into claimants’ digital footprints and behavioral patterns. Furthermore, OSINT insurance fraud detection techniques enable investigators to verify claim authenticity, expose contradictory evidence, and identify organized fraud rings before they cause significant financial losses.
This comprehensive guide explores cutting-edge OSINT methodologies specifically designed for insurance fraud investigations. Additionally, from analyzing social media metadata to tracking financial networks, these techniques provide insurance fraud managers and investigators with the advanced capabilities needed to protect their organizations from increasingly sophisticated fraud schemes.
Understanding Modern Insurance Fraud Patterns
Contemporary insurance fraud schemes require sophisticated detection approaches that can identify deception across multiple digital platforms and communication channels. Therefore, modern fraudsters employ advanced techniques including fake documentation, coordinated witness testimony, and elaborate social media personas designed to support fraudulent claims.
OSINT insurance fraud detection must account for organized crime networks that target specific insurance companies, geographic regions, or policy types with coordinated campaigns. These operations often involve multiple claimants, medical providers, and legal representatives working together to maximize fraudulent payouts while minimizing detection risks.
| Fraud Type | Annual Loss (USD) | Common OSINT Evidence | Detection Rate with OSINT |
|---|---|---|---|
| Workers’ Compensation | $34 billion | Social media activity, GPS metadata, public surveillance | 78% improvement |
| Auto Insurance | $29 billion | Traffic cameras, social media check-ins, repair records | 65% improvement |
| Property Insurance | $51 billion | Weather data, social media photos, satellite imagery | 82% improvement |
| Healthcare Fraud | $68 billion | Provider networks, billing patterns, patient social media | 71% improvement |
Advanced fraud schemes now exploit legitimate insurance processes while maintaining plausible deniability. Consequently, investigators must understand how criminals manipulate documentation, coordinate testimony, and exploit policy loopholes while creating convincing digital evidence trails to support their claims.
Furthermore, OSINT insurance fraud detection techniques must address the increasing sophistication of fraudulent documentation, including deepfake technology, manipulated medical records, and fabricated witness statements that require advanced technical analysis to identify.
Social Media Analysis for Insurance Fraud Detection
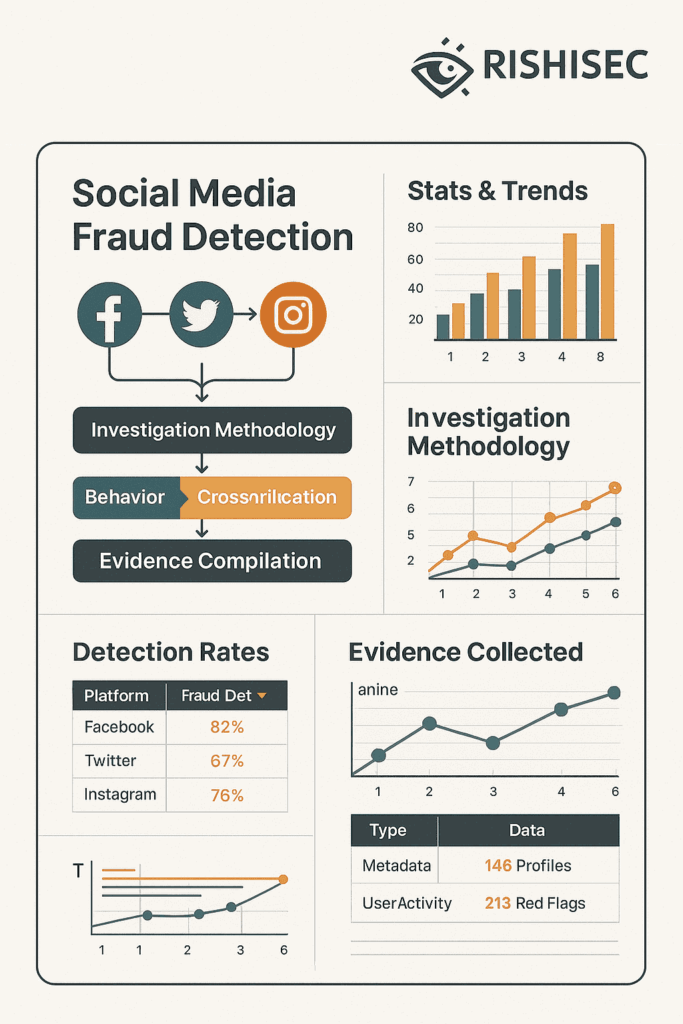
Social media platforms provide the richest source of contradictory evidence for insurance fraud investigations. Therefore, investigators must master techniques for analyzing posts, photos, videos, and metadata that can expose claimants’ actual activities and conditions versus their reported limitations or injuries.
Timeline analysis has become crucial for identifying inconsistencies between claimed injury dates and social media activity. By examining posting patterns, check-ins, and photo metadata, investigators can establish comprehensive activity timelines that often contradict fraudulent workers’ compensation or disability claims.
Advanced platforms like Kindi enable insurance fraud investigators to automate social media monitoring across multiple platforms while maintaining detailed evidence trails suitable for legal proceedings. This automation allows investigators to focus on analysis rather than manual data collection.
| Social Media Evidence Type | Fraud Contradiction Examples | Technical Analysis Methods |
|---|---|---|
| GPS Metadata | Location data contradicting claimed inability to travel | EXIF data extraction, geolocation verification, mapping analysis |
| Activity Photos | Physical activities inconsistent with claimed injuries | Timestamp verification, reverse image search, activity analysis |
| Check-in Data | Presence at locations during claimed disability periods | Location correlation, timeline reconstruction, pattern analysis |
| Social Connections | Relationships with other fraudulent claimants | Network mapping, relationship analysis, coordination detection |
Photo and video analysis requires specialized techniques for detecting manipulated content, verifying timestamps, and extracting hidden metadata that can reveal creation dates, device information, and geographic coordinates. These technical capabilities often provide the strongest contradictory evidence in fraud cases.
Cross-platform correlation enables investigators to build comprehensive profiles of claimants’ actual activities and capabilities. By analyzing content across Facebook, Instagram, LinkedIn, and other platforms, investigators can identify patterns of behavior that contradict claimed limitations or injuries.
Geolocation Verification and Timeline Analysis
Geolocation analysis is one of the most powerful OSINT techniques available to modern investigators for detecting insurance fraud. Subsequently, GPS metadata, check-in data, and location-tagged content can provide irrefutable evidence of claimants’ actual whereabouts and activities during claimed disability periods.
Advanced geolocation techniques include satellite imagery analysis, traffic camera correlation, and public surveillance integration that can independently verify or contradict claimant statements. These methods prove particularly effective for workers’ compensation cases where claimants allege inability to work or travel.
Timeline reconstruction using digital evidence enables investigators to create comprehensive activity profiles that span weeks or months of claimed disability. By correlating social media posts, financial transactions, and digital communications, investigators can establish detailed patterns of behavior that often contradict fraudulent claims.
Weather data correlation provides additional verification capabilities for property insurance fraud cases. By comparing claimed damage dates with meteorological records, investigators can identify suspicious claims that don’t align with actual weather events or natural disasters.
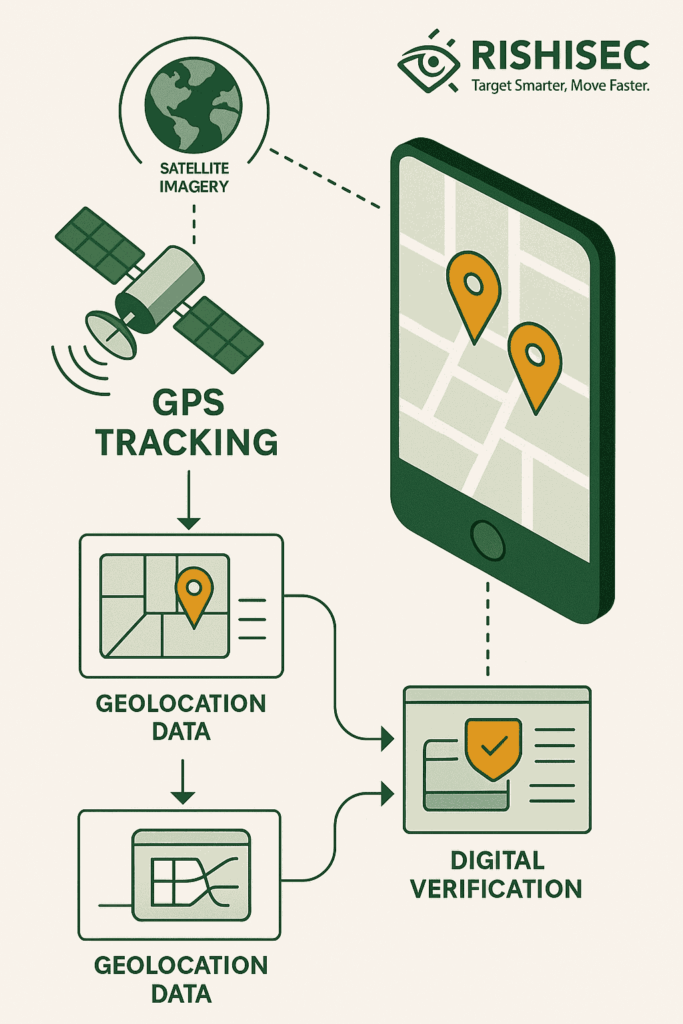
The integration of geolocation techniques with traditional investigation methods enhances overall case effectiveness. For example, combining OSINT approaches with conventional law enforcement investigation methodologies creates more comprehensive fraud detection frameworks.
Financial Intelligence and Asset Investigation
Financial intelligence represents a critical component of comprehensive insurance fraud investigations. Therefore, investigators must understand how to track financial flows, identify hidden assets, and correlate financial activities with claimed losses or disabilities.
Digital payment analysis has become increasingly important as fraudsters use online banking, digital wallets, and cryptocurrency to obscure financial trails. Investigators need capabilities to analyze transaction patterns, identify suspicious transfers, and correlate financial activities with claimed inability to work or earn income.
Asset investigation using public records, social media evidence, and financial databases can reveal undisclosed wealth, property ownership, or business interests that contradict disability claims. These investigations often uncover lifestyle inconsistencies that support fraud allegations.
Business registration analysis can identify undisclosed employment or business ownership that contradicts workers’ compensation or disability claims. By analyzing corporate records, professional licensing databases, and business social media profiles, investigators can expose hidden income sources.
According to the Coalition Against Insurance Fraud, financial intelligence techniques have increased successful fraud prosecutions by over 45% when combined with traditional investigation methods.
Medical Evidence Verification Through OSINT
Medical fraud detection requires specialized OSINT insurance fraud techniques that can verify treatment authenticity, provider credibility, and patient condition claims. Furthermore, investigators must develop capabilities to analyze medical provider networks, billing patterns, and treatment documentation for signs of coordinated fraud schemes.
Provider verification involves analyzing medical professionals’ licenses, disciplinary records, and business relationships to identify practitioners who may be complicit in fraudulent schemes. Social media analysis can reveal inappropriate relationships between providers and claimants that suggest collusion.
Treatment verification requires correlation of claimed medical visits with digital evidence of claimants’ actual activities and locations. Social media posts, financial transactions, and communication records can often contradict claimed medical appointments or treatment schedules.
Medical equipment fraud detection involves analyzing claims for medical devices, wheelchairs, or other assistive equipment against evidence of actual usage or need. Social media evidence often reveals that expensive medical equipment claims are fraudulent or unnecessary.
Coordinated Fraud Ring Detection
Modern insurance fraud often involves organized networks that coordinate claims, share information, and exploit specific vulnerabilities in insurance systems. Consequently, OSINT insurance fraud detection must include capabilities for identifying these coordinated operations before they cause significant losses.
| Fraud Ring Indicators | OSINT Detection Methods | Investigation Priority |
|---|---|---|
| Shared Medical Providers | Provider network analysis, billing pattern correlation | High |
| Common Legal Representation | Attorney client analysis, case pattern identification | High |
| Social Media Connections | Network mapping, relationship analysis, communication patterns | Medium |
| Geographic Clustering | Location analysis, demographic correlation, incident mapping | Medium |
Network analysis capabilities enable investigators to map relationships between claimants, providers, attorneys, and other parties involved in suspicious claims. By visualizing these connections, investigators can identify patterns that suggest coordinated fraud operations.
Communication analysis can reveal coordination between seemingly unrelated claimants through shared social media interactions, messaging patterns, or communication timing that suggests planned activities rather than legitimate independent claims.
The integration of fraud ring detection with broader criminal network analysis proves particularly effective. Specialized techniques for tracking criminal networks on social media provide valuable methodologies that insurance investigators can adapt.
Legal Compliance and Evidence Preservation
OSINT insurance fraud detection must maintain strict legal compliance while ensuring evidence admissibility in legal proceedings. Therefore, investigators must understand privacy regulations, evidence collection procedures, and documentation requirements that protect both the investigation and the organization.
Chain of custody procedures require detailed documentation of evidence collection methods, source verification, and data preservation techniques. Digital evidence must be collected and stored using forensically sound methods that maintain integrity throughout the investigation process.
Privacy compliance involves understanding state and federal regulations governing insurance fraud investigations, social media evidence collection, and personal information analysis. Investigators must balance effective fraud detection with respect for individual privacy rights.
Expert testimony preparation requires investigators to document their methodologies, tools, and analytical processes in ways that can be clearly explained to judges and juries. This documentation becomes crucial for successful fraud prosecutions and civil recovery actions.
The FBI’s Insurance Fraud programs emphasize the importance of proper evidence handling and legal compliance in insurance fraud investigations, particularly when using digital evidence and OSINT techniques.
Implementation Guidelines for Insurance Organizations
Successful deployment of OSINT insurance fraud detection requires systematic planning across investigation teams and organizational departments. Consider these essential implementation elements:
- Establish secure investigation infrastructure with appropriate legal oversight and evidence preservation capabilities for court proceedings
- Develop specialized training programs for fraud investigators covering advanced OSINT techniques and legal compliance requirements
- Implement automated fraud detection systems for high-risk claim indicators and suspicious activity patterns across multiple data sources
- Create secure case management platforms for investigator collaboration and evidence sharing while maintaining confidentiality
- Design legal compliance frameworks that ensure evidence admissibility while enabling effective fraud detection and investigation
- Establish vendor relationships with OSINT tool providers and digital forensics experts for complex investigation support
- Develop rapid response procedures for addressing time-sensitive fraud schemes and asset recovery before losses occur
- Create inter-organizational coordination mechanisms for sharing fraud intelligence and coordinating investigations with law enforcement
Insurance organizations should also consider forming partnerships with law enforcement agencies, industry associations, and technology providers that can enhance their investigation capabilities and facilitate information sharing.
FAQ
How effective are OSINT techniques for detecting insurance fraud?
OSINT insurance fraud detection techniques have proven highly effective, with studies showing 65-82% improvement in fraud detection rates depending on the insurance type. Furthermore, these methods provide stronger evidence for legal proceedings and significantly reduce investigation timelines.
What legal considerations apply to social media evidence in insurance fraud cases?
Social media evidence must be collected using proper legal procedures, with appropriate privacy considerations and chain of custody documentation. Additionally, investigators must ensure evidence authenticity and comply with state and federal privacy regulations governing digital evidence collection.
How can insurance companies verify the authenticity of digital evidence?
Digital evidence verification requires multiple technical approaches including metadata analysis, timestamp verification, reverse image searching, and cross-platform correlation. Therefore, investigators should maintain detailed documentation of evidence sources and collection methodologies.
What training do insurance fraud investigators need for OSINT techniques?
Investigators need specialized training in social media analysis, digital forensics, geolocation verification, and legal compliance requirements. Moreover, ongoing education is essential as fraud techniques and digital platforms continue to evolve rapidly.
Want to strengthen your OSINT skills and other ones you can suggest? Check out our OSINT courses for practical, hands-on training. Ready to revolutionize your insurance fraud investigations? Discover how Kindi can streamline your fraud detection operations and enhance your team’s investigative capabilities with advanced automation and link analysis.