Credential exposure creates the fastest path from reconnaissance to system access. Moreover, leaked passwords and API tokens provide red teams with realistic attack vectors that do not require access to production systems. When you master credential leakage OSINT techniques, you transform scattered breach data into actionable intelligence that demonstrates real business risk.
Red teams, SOC analysts, and security professionals need systematic approaches to credential discovery. Furthermore, the volume of leaked data requires automation and structured analysis. This guide shows you how to build repeatable workflows that find leaked credentials, analyze reuse patterns, and present findings that drive immediate remediation.
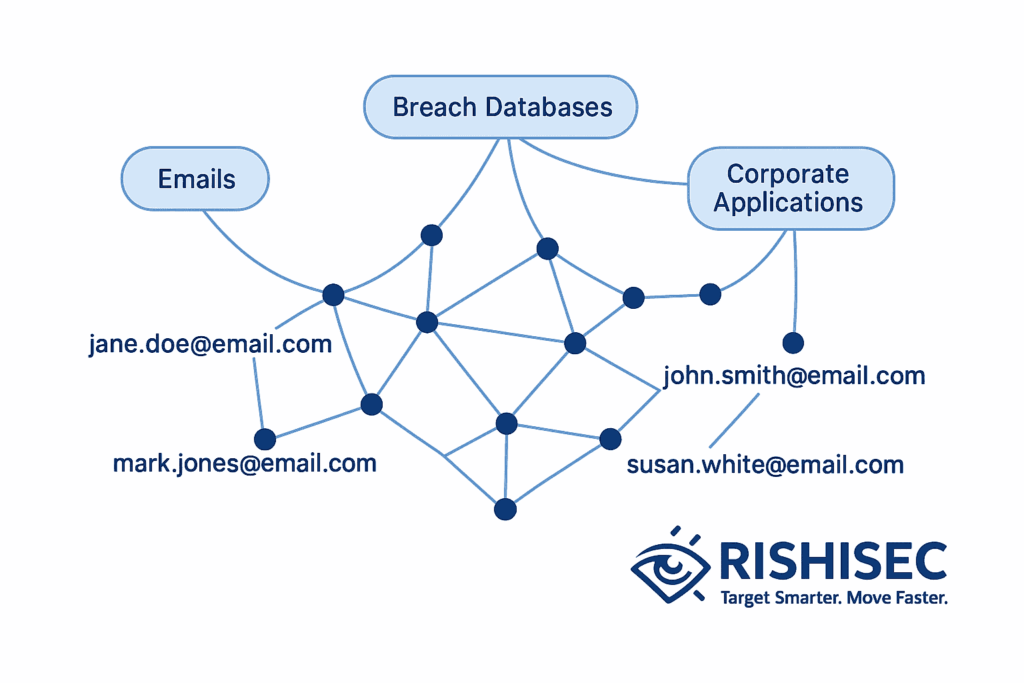
How to Discover Credential Leakage Through OSINT Sources
Successful credential leakage OSINT starts with knowing where to look. Additionally, different sources provide varying levels of detail and credibility. Here’s how to build a comprehensive collection strategy:
Primary Data Sources for Credential Discovery
Start your credential leakage OSINT investigation with these key sources. However, always verify findings across multiple platforms before taking action:
- Breach notification databases: HaveIBeenPwned and similar services provide breach timelines and affected email domains
- Code repositories: GitHub, GitLab, and Bitbucket often contain accidentally committed API keys and database credentials
- Paste sites and forums: Temporary pastes frequently expose credential subsets that never reach major breach collections
- Dark web marketplaces: Monitor seller reputations and dataset descriptions to understand exposure scope
According to the Verizon Data Breach Investigations Report, stolen credentials remain involved in over 80% of breaches. Therefore, systematic credential monitoring becomes critical for organizational security.
Automated Collection and Monitoring
Manual credential hunting scales poorly and misses time-sensitive exposures. Instead, implement automated collectors that run scheduled queries across multiple sources. Additionally, set up alerts for new mentions of your organization’s domains or email patterns.
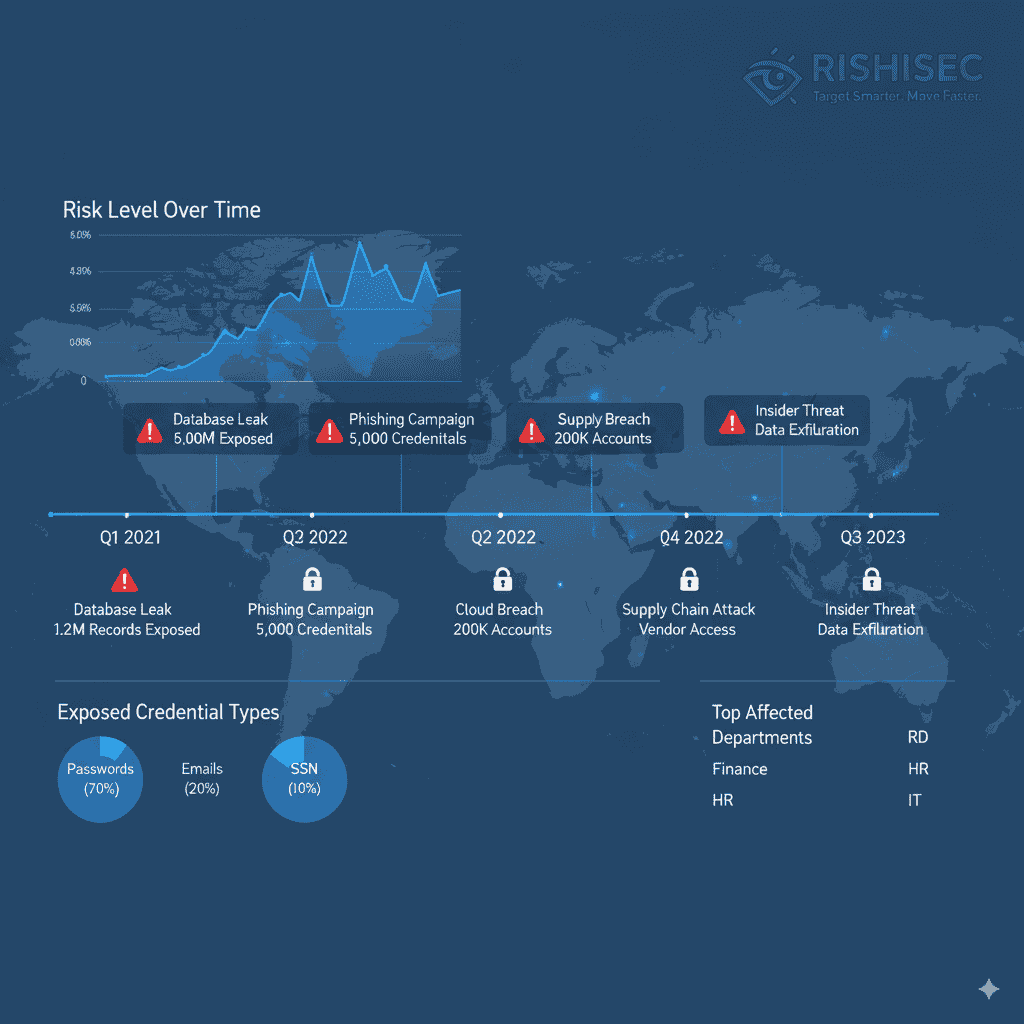
Analyzing Password Reuse Patterns and Risk Assessment
Once you discover leaked credentials, the next step involves analyzing reuse patterns. Furthermore, understanding password semantics helps predict where employees might reuse similar credentials across business applications.
Password Pattern Analysis Techniques
Look for these common patterns in your credential leakage OSINT analysis:
- Quarter-year suffixes (Password2024Q1)
- Company or product abbreviations
- Sequential numbering schemes
- Keyboard patterns combined with dates
Map these patterns to applications that resist mandatory password resets. Additionally, identify shared admin accounts and third-party services that often escape centralized credential management.
Risk Prioritization Framework
Not all credential exposures carry equal risk. Therefore, use this framework to prioritize remediation efforts:
| Risk Level | Credential Type | Potential Access | Business Impact | Action Required |
|---|---|---|---|---|
| Critical | Admin accounts with SSO access | Multiple business systems | Data breach, system compromise | Immediate reset and MFA enforcement |
| High | Service accounts with API access | Cloud infrastructure, databases | Service disruption, data exposure | Token rotation within 24 hours |
| Medium | Employee accounts with limited scope | Email, productivity apps | Data leakage, lateral movement | Forced password reset within 72 hours |
| Low | Inactive or terminated user accounts | Legacy systems, archived data | Historical data exposure | Account verification and cleanup |
Building Automated Credential Leakage OSINT Workflows
Effective credential leakage OSINT requires systematic automation. Moreover, manual processes introduce inconsistency and miss critical exposures during high-volume periods.
Essential Automation Components
Build your automated workflow around these core components:
- Scheduled data collectors: Query multiple sources on regular intervals
- Normalization engines: Standardize email formats and deduplicate entries
- Enrichment modules: Add organizational context like job roles and system access
- Risk scoring algorithms: Automatically prioritize findings based on business impact
- Alert mechanisms: Notify security teams of high-priority discoveries
For organizations implementing Continuous Threat Exposure Management, automated credential monitoring becomes a foundational capability that feeds into broader risk assessment programs.
Leveraging Kindi for Advanced Analysis
While manual tools work for small-scale investigations, enterprise credential leakage OSINT requires specialized platforms. Kindi provides automated collection, entity linking, and collaborative analysis features that accelerate credential discovery and risk assessment.
Teams using Kindi can visualize credential exposures across interactive link graphs. Additionally, the platform enables timeline analysis of breach events and supports collaborative investigation workflows that keep security teams aligned during incident response.
Translating Technical Findings Into Business Risk
Technical teams excel at finding leaked credentials, but executives need clear business impact explanations. Therefore, your credential leakage OSINT reports must connect technical findings to operational risks that leadership understands.
Effective Risk Communication Strategies
Use these approaches to make credential exposure findings actionable:
- Map each exposed credential to specific business processes it could disrupt
- Calculate potential financial impact using industry breach cost data
- Provide clear remediation steps with estimated timelines and resource requirements
- Include compliance implications for regulated industries
- Show how fixes reduce both likelihood and impact of successful attacks
When presenting findings, reference established frameworks like NIST Digital Identity Guidelines to demonstrate alignment with security best practices. However, avoid overwhelming executives with technical implementation details.
Practical Tips for Credential Leakage OSINT Success
These proven techniques will improve your credential leakage OSINT effectiveness:
- Maintain separate collection infrastructure to avoid exposing corporate networks to malicious sites
- Document chain of custody for all evidence to support legal proceedings if necessary
- Test credential validation procedures in isolated environments before production testing
- Coordinate with legal teams on breach notification requirements and disclosure timelines
- Build relationships with threat intelligence vendors for access to premium breach datasets
- Practice responsible disclosure when discovering third-party credential exposures
- Regularly update collection sources as new leak sites and forums emerge
FAQ
How often should organizations run credential leakage OSINT scans?
Run automated scans daily for high-risk domains and executive accounts. Additionally, perform comprehensive monthly reviews of all organizational email patterns. Trigger immediate scans after public breach announcements affecting your industry or vendors.
What legal considerations apply to credential leakage OSINT?
Always consult legal counsel before accessing breach databases or validating discovered credentials. Moreover, maintain clear documentation of data sources and handling procedures. Some jurisdictions restrict access to certain types of leaked data, even for legitimate security purposes.
How can small security teams manage large volumes of credential exposures?
Focus automation on high-impact scenarios first. Additionally, prioritize credentials with administrative access or those tied to critical business systems. Consider outsourcing initial data collection while keeping analysis and validation in-house.
What metrics should organizations track for credential exposure programs?
Track time from exposure discovery to remediation, percentage of credentials requiring immediate action, and reduction in successful credential-based attacks. Furthermore, measure employee compliance with password reset requests and adoption of multi-factor authentication.
Ready to strengthen your credential security posture? Try Kindi for automated credential leakage monitoring and analysis. Additionally, explore our specialized OSINT training courses to build advanced investigation capabilities for your security team.




