Cybersecurity analysts across private sector organizations face a common frustration: they know proactive threat hunting could significantly improve security posture, yet their programs remain stuck performing basic indicator searches that barely qualify as hunting. The issue isn’t lack of talent or motivation; instead, it’s the absence of systematic frameworks guiding program evolution from reactive detection to genuinely proactive threat discovery.
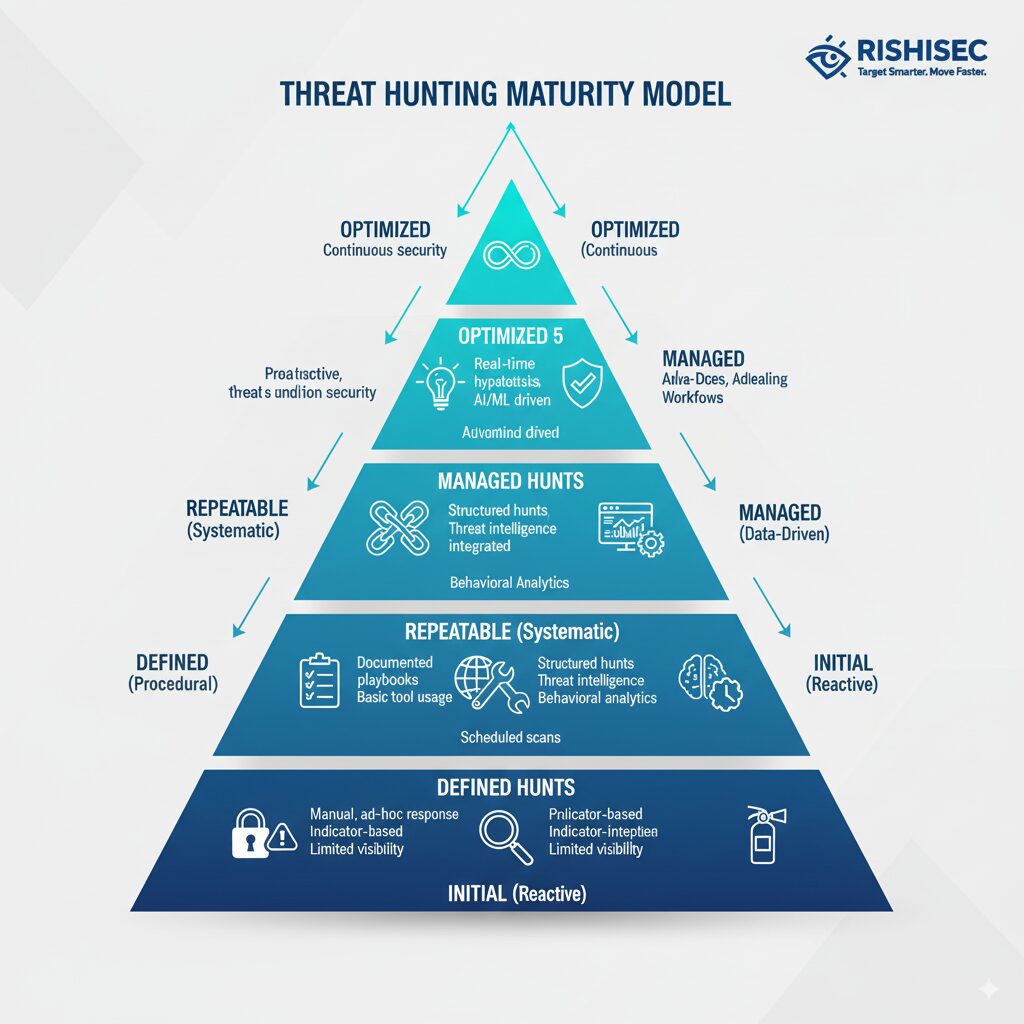
A threat hunting maturity model provides that framework by defining clear progression stages from initial ad hoc investigations through sophisticated hypothesis-driven hunting operations. Understanding where your program currently sits on this maturity spectrum and what capabilities separate each level enables cyber threat leads to chart realistic development paths rather than making random capability investments that don’t address fundamental gaps.
The stakes for maturity progression have never been higher. Adversaries increasingly employ living-off-the-land techniques that evade signature-based detection, maintain persistent access for months before discovery, and conduct low-and-slow operations designed to fly under automated alert thresholds. Organizations relying exclusively on automated detection miss threats that mature hunting programs routinely discover. Understanding the critical role of SOC visibility becomes essential as threat hunting maturity directly correlates with detection capabilities.
Assessing Your Current Threat Hunting Maturity Level
Most organizations overestimate their threat hunting maturity, believing they conduct proactive hunting when they actually perform reactive indicator searches triggered by external intelligence or alerts. Honest maturity assessment requires examining multiple capability dimensions including hunt process formality, data availability and quality, analytical techniques employed, tooling sophistication, personnel skills, and organizational support for hunting activities.
Initial maturity level organizations conduct threat hunting sporadically without formal processes or dedicated resources. Hunting occurs only when high-profile breaches or specific intelligence reports prompt leadership to ask whether similar compromises exist in their environment. These reactive hunts lack hypothesis development, rely on basic indicator searches, and produce limited documentation that doesn’t inform future hunting activities. Success depends entirely on individual analyst initiative rather than programmatic capability.
Defined maturity organizations establish basic hunting processes and dedicate resources to regular hunting activities; however, capabilities remain limited. They conduct scheduled hunts following documented procedures, maintain hunt logs tracking activities and findings, and employ standard techniques like indicator pivoting and anomaly identification. Nevertheless, hunts primarily focus on known threat patterns rather than discovering novel adversary behaviors. Analytical techniques remain relatively simple, and tooling consists mainly of SIEM searches and basic log analysis.
Key Maturity Level Characteristics
- Initial Level (Ad Hoc): No formal hunting process; sporadic activities triggered by external events; limited documentation; basic tools like grep and manual log review; success depends on individual analyst skill rather than programmatic capability.
- Defined Level (Procedural): Documented hunting procedures; scheduled hunt cadence; dedicated hunting team or roles; standardized hunt templates and workflows; basic analytics beyond simple searches; repeatable processes that new analysts can follow.
- Repeatable Level (Systematic): Hypothesis-driven hunting methodology; integration with threat intelligence; measurable hunt effectiveness metrics; automated data collection and normalization; collaborative hunting involving multiple analysts; formal knowledge management capturing hunt findings.
- Managed Level (Data-Driven): Advanced analytics including behavioral analysis and machine learning; comprehensive data coverage across enterprise; prioritized hunting based on risk assessment; automated alert generation from hunt findings; executive reporting demonstrating program value.
- Optimized Level (Continuous): Continuous automated hunting supplementing analyst-led activities; predictive analytics identifying likely compromise indicators; feedback loops improving detection and prevention; industry leadership sharing hunt methodologies and findings; innovation in hunting techniques and tools.
Building Foundational Capabilities for Maturity Progression
Advancing threat hunting maturity requires systematic capability building across multiple dimensions simultaneously. Organizations cannot skip maturity levels; attempting advanced techniques without foundational capabilities inevitably fails. Cyber threat leads must honestly assess current state and focus development efforts on capabilities enabling progression to the next maturity level rather than aspirational advanced capabilities.
Data availability and quality represent the most critical foundation. Threat intel analysts cannot hunt effectively without comprehensive visibility into endpoint activities, network traffic, authentication events, and cloud service usage. Many organizations discover their logging coverage contains significant blind spots where adversaries could operate undetected. Advancing maturity requires systematic assessment of data coverage, identification of visibility gaps, and implementation of additional logging before sophisticated hunting techniques prove feasible.
Data normalization and enrichment transform raw logs into huntable datasets. Raw security telemetry lacks context necessary for efficient analysis; enriching events with asset information, user details, geolocation data, and threat intelligence enables analysts to quickly distinguish normal activity from suspicious behavior. Organizations should implement automated enrichment pipelines that process security telemetry in real-time, making enriched data immediately available for hunting activities rather than requiring manual enrichment during each hunt.
| Capability Dimension | Initial State | Target State for Progression |
|---|---|---|
| Data Coverage | Partial visibility with significant blind spots; inconsistent log retention; limited endpoint telemetry | Comprehensive visibility across enterprise; standardized retention policies; rich endpoint behavioral data; cloud service logging |
| Analytical Techniques | Basic searches for known indicators; simple anomaly identification; manual correlation across limited sources | Hypothesis-driven investigations; behavioral analysis; statistical anomaly detection; automated correlation across multiple data sources |
| Process Maturity | Ad hoc hunting triggered by external events; minimal documentation; no formal methodology | Scheduled hunts following documented procedures; hypothesis development frameworks; comprehensive hunt documentation; knowledge management |
| Tooling Capabilities | Manual log searches; basic SIEM queries; limited automation | Purpose-built hunting platforms; automated data analysis; visualization tools; integration with threat intelligence platforms |
| Personnel Skills | Limited hunting expertise; reliance on individual analyst capabilities; no formal training | Trained hunting analysts; documented skill requirements; continuous education programs; cross-functional collaboration with threat intelligence and IR teams |
Process formalization enables consistent hunting effectiveness regardless of which analyst conducts activities. Mature programs document hunting methodologies, create hypothesis templates, establish investigation workflows, and maintain knowledge bases capturing previous hunt findings and techniques. This documentation transforms hunting from art dependent on individual expertise to science where any trained analyst can execute effective hunts following established procedures.
Developing Hypothesis-Driven Hunting Methodologies
The transition from indicator-based searching to hypothesis-driven hunting marks the most significant maturity progression for most organizations. Indicator searching looks for known bad things based on external intelligence or historical compromise indicators. Hypothesis-driven hunting starts with assumptions about how adversaries might operate in your environment, then tests those hypotheses through data analysis to discover evidence of actual compromise.
Effective hypotheses combine understanding of adversary tactics with knowledge of your specific environment’s characteristics and vulnerabilities. Rather than generic hypotheses like “adversaries might use PowerShell for malicious purposes,” mature hypotheses might state “adversaries targeting our manufacturing operational technology would likely conduct reconnaissance of SCADA systems from compromised corporate workstations, which would appear as unusual SMB traffic from non-engineering systems to OT network segments.”
Automating OSINT investigations accelerates hypothesis development by providing current intelligence about adversary tactics, targeting patterns, and campaign characteristics. Rather than analysts manually researching threat actor behaviors, AI-powered platforms continuously monitor open sources and intelligence feeds, surfacing relevant tactical intelligence that informs hypothesis creation. This automation enables threat intel analysts to maintain awareness of emerging adversary techniques and quickly develop hunt hypotheses addressing novel threats.
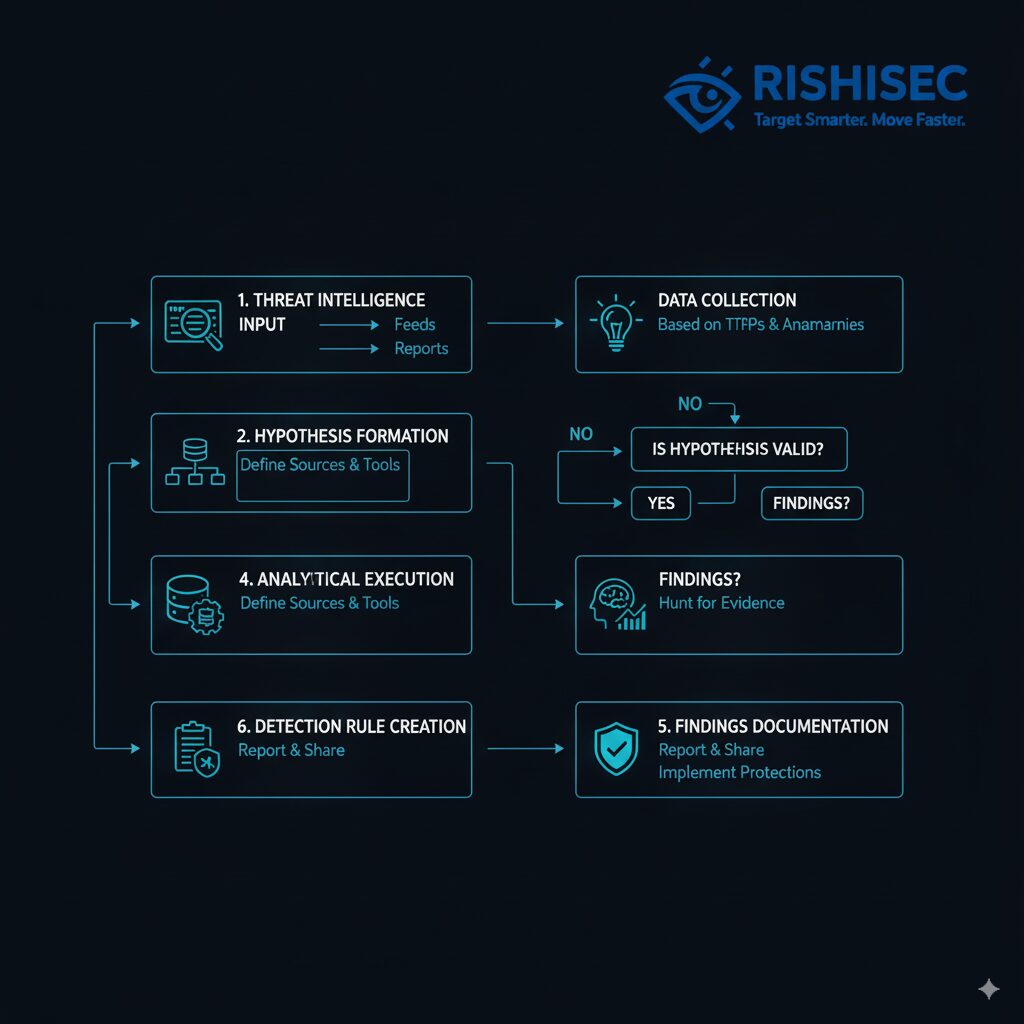
Kindi enhances hypothesis-driven hunting through comprehensive link analysis capabilities. When investigating suspicious activities identified during hypothesis testing, cybersecurity analysts need to understand relationships between observed indicators and broader threat actor infrastructure or campaigns. Kindi automatically maps connections between domains, IP addresses, user accounts, and system activities, revealing whether isolated suspicious events represent parts of larger compromise campaigns. This visibility transforms hunting from identifying individual suspicious activities to discovering complete attack chains and persistent adversary presence.
Leveraging Automation to Scale Hunting Operations
Manual hunting cannot scale to provide continuous security monitoring across modern enterprise environments. Organizations generate terabytes of security telemetry daily; human analysts cannot manually review more than tiny fractions of this data. Advancing hunting maturity requires automation that continuously analyzes security telemetry, identifies anomalies warranting investigation, and enables analysts to focus on high-value investigative work rather than repetitive data processing.
Automated hunting should complement rather than replace human analysts. Machines excel at processing vast data volumes, identifying statistical anomalies, and executing repetitive analytical procedures at scale. Humans excel at contextual interpretation, creative thinking about adversary behaviors, and making judgment calls about ambiguous situations. Mature programs combine these strengths, with automation handling continuous baseline hunting while analysts conduct sophisticated investigations of automated findings and pursue novel hypotheses that machines cannot independently develop.
The progression toward automation typically follows predictable stages. Organizations first automate simple repetitive hunts like checking for known malicious indicators across their environment. Next, they implement anomaly detection algorithms identifying statistical deviations from baseline behaviors. Advanced stages involve machine learning models that identify subtle behavioral patterns indicating compromise even when individual events appear benign. The most mature programs employ AI that learns from previous hunts to continuously improve detection capabilities and generate new hunting hypotheses based on emerging threat intelligence.
Integrating Threat Hunting with Broader Security Operations
Threat hunting programs that operate in isolation from broader security operations miss opportunities for synergy and fail to maximize their defensive impact. Mature programs establish tight integration between hunting, threat intelligence, incident response, and detection engineering functions. This integration creates feedback loops where each function continuously improves others.
Hunt findings should directly inform detection rule development. When hunters discover evidence of adversary techniques that current detection missed, detection engineers should create automated rules preventing future manual hunts for the same indicators. This feedback loop transforms one-time hunt discoveries into permanent defensive improvements. Organizations that fail to operationalize hunt findings waste investigative effort repeatedly hunting for threats that automated detection should catch.
Threat intelligence should drive hunt prioritization and hypothesis development. Rather than randomly selecting hunt topics, mature programs leverage current threat intelligence to focus hunting on adversary tactics most likely affecting their organization. When intelligence indicates specific threat actors target their industry or geographic region, hunting teams prioritize hypotheses addressing those actors’ known tactics. This intelligence-driven approach ensures limited hunting resources focus on highest-probability threats. Understanding the missing link in threat intelligence platforms helps frame hunting as essential capability addressing gaps in automated detection.
Incident response benefits enormously from mature hunting capabilities. When incidents occur, experienced hunters can quickly scope compromise by applying hunting techniques to identify all affected systems, determine initial access vectors, and map adversary activities across the environment. Without hunting expertise, incident response teams often miss parts of multi-stage attacks or fail to identify all compromised systems, leading to incomplete remediation and adversary persistence. According to MITRE ATT&CK research, organizations with mature hunting programs detect breaches an average of 60 days faster than those relying solely on automated detection.
Measuring Threat Hunting Maturity Program Effectiveness
Demonstrating hunting program value requires metrics connecting hunting activities to measurable security improvements. Cyber threat leads frequently struggle justifying dedicated hunting resources when leadership questions whether proactive hunting produces better outcomes than investing those resources in additional automated detection capabilities or incident response personnel.
Discovery metrics quantify unique threats that hunting identified which automated detection missed. How many compromises did hunting discover that would have remained undetected? How long had adversaries maintained access before hunting identified them? What severity levels characterized hunt-discovered incidents? These metrics demonstrate hunting’s unique value in discovering threats that evade automated detection systems.

Efficiency metrics reveal how hunting improves overall security operations effectiveness. Did hunt findings reduce false positive rates by improving detection rule accuracy? Did hunting-derived detection rules decrease analyst workload by automating identification of previously manual investigative tasks? Did hunting programs reduce mean time to detect (MTTD) for specific threat categories? Organizations with mature hunting programs typically demonstrate dramatic efficiency improvements as hunting continuously enhances automated detection capabilities.
Maturity progression metrics track program development over time. Are hunting processes becoming more formalized? Is data coverage expanding? Are analytical techniques growing more sophisticated? Is automation increasing? Measuring maturity progression helps leadership understand program development trajectory and whether capability investments produce expected maturity advancement. Organizations should establish baseline maturity assessments and conduct periodic reassessments to demonstrate continuous improvement.
Overcoming Common Maturity Progression Barriers
Organizations attempting to advance hunting maturity encounter predictable obstacles that stall progression if not addressed systematically. The most common barrier is insufficient data visibility preventing effective hunting. Cybersecurity analysts cannot find evidence of sophisticated attacks in data they don’t collect. Before investing in advanced analytical capabilities, organizations must ensure comprehensive logging coverage across endpoints, network infrastructure, cloud services, and critical applications.
Skills gaps represent another significant barrier. Effective threat hunting requires expertise combining deep technical knowledge, adversary tradecraft understanding, analytical thinking, and investigative creativity. Many organizations lack analysts possessing this combination of skills. Building hunting expertise requires dedicated training programs, mentorship from experienced hunters, and realistic practice opportunities. Organizations should consider starting with external hunting support while developing internal capabilities rather than expecting immediate proficiency from analysts without hunting backgrounds.
Organizational resistance to proactive security spending creates budgetary barriers. Leadership comfortable funding reactive incident response may question value of dedicating resources to hunting for threats that may not exist. Overcoming this resistance requires demonstrating hunting value through pilot programs, communicating findings in business impact terms, and showing how mature hunting programs prevent expensive incidents rather than simply adding security costs.
Practical Steps for Advancing Your Hunting Program Maturity
- Conduct honest maturity assessment: Evaluate current capabilities across all maturity dimensions without inflating accomplishments. Accurate assessment ensures development efforts address actual gaps rather than perceived weaknesses.
- Focus on foundational capabilities first: Organizations cannot skip maturity levels. Ensure comprehensive data coverage, basic process formalization, and adequate tooling before attempting advanced analytical techniques.
- Document everything: Create hunt playbooks, hypothesis templates, investigation procedures, and findings reports that enable knowledge transfer and consistent execution regardless of which analyst conducts hunts.
- Start with achievable hypotheses: Early hypothesis-driven hunts should address high-probability threats using available data rather than requiring significant new capability development. Build confidence through successes before tackling complex hunts.
- Operationalize findings immediately: Transform every hunt discovery into permanent defensive improvements through detection rule creation, response playbook updates, or remediation of identified vulnerabilities.
- Measure and communicate value: Track metrics demonstrating hunting effectiveness and regularly brief leadership on discovered threats, prevented incidents, and operational improvements resulting from hunting activities.
- Invest in continuous learning: Threat hunting requires staying current with evolving adversary tactics. Provide training opportunities, conference attendance, and collaboration with external hunting communities to maintain cutting-edge capabilities.
Ready to assess your threat hunting maturity and develop a structured progression plan? Explore our practical training programs designed for cybersecurity analysts and threat intelligence teams. Want to accelerate hunting maturity through AI-powered automation and comprehensive link analysis? Discover how Kindi transforms threat hunting operations for enterprise security teams.
FAQ
What is a threat hunting maturity model?
A threat hunting maturity model is a framework that defines progressive capability levels from reactive, ad hoc threat detection through sophisticated, continuous proactive hunting operations. It typically includes five levels: Initial (sporadic reactive activities), Defined (documented procedures and scheduled hunts), Repeatable (hypothesis-driven systematic hunting), Managed (data-driven operations with advanced analytics), and Optimized (continuous automated hunting with predictive capabilities). Organizations use maturity models to assess current capabilities, identify development priorities, and chart realistic progression paths.
How long does it take to progress between maturity levels?
Progression timelines vary significantly based on starting capabilities, resource availability, and organizational commitment. Moving from Initial to Defined level typically requires three to six months establishing basic processes and dedicated resources. Advancing to Repeatable level often takes six to twelve months developing hypothesis-driven methodologies and improving data coverage. Reaching Managed and Optimized levels may require one to two years implementing advanced analytics, automation, and comprehensive integration with broader security operations. Organizations cannot skip levels; attempting advanced capabilities without foundational maturity inevitably fails.
What data sources are essential for effective threat hunting?
Essential data sources include comprehensive endpoint telemetry capturing process execution, file modifications, network connections, and registry changes; network traffic data including full packet capture or metadata for internal and external communications; authentication logs tracking user and service account activities across systems; cloud service logs from SaaS applications and infrastructure-as-a-service platforms; and security tool alerts from EDR, SIEM, and other detection systems. Data quality and retention matter as much as coverage; hunters need historical data spanning weeks or months to identify low-and-slow adversary activities.
How do we justify threat hunting program costs to leadership?
Justify hunting programs by demonstrating measurable value through pilot projects that discover actual threats automated detection missed, quantifying potential incident costs prevented by early threat discovery, showing efficiency gains as hunt findings improve automated detection and reduce analyst workload, benchmarking against industry peers where hunting programs are standard practice, and framing hunting as insurance against sophisticated threats that evade automated defenses. Calculate return on investment by comparing hunting program costs against estimated costs of undetected breaches in your industry and organization size.
Can small security teams implement effective threat hunting programs?
Small teams can implement effective hunting by focusing on achievable maturity levels appropriate to their resources, leveraging automation platforms that provide hunting capabilities without large analyst teams, starting with scheduled hunts addressing highest-priority threats rather than attempting comprehensive coverage, collaborating with external hunting services or MSSPs for advanced capabilities beyond internal resources, and prioritizing quality over quantity by conducting fewer high-value hunts rather than numerous superficial investigations. Cloud-based hunting platforms and AI-powered automation enable small teams to achieve hunting effectiveness previously requiring large dedicated teams.