Military contractors face unprecedented challenges in today’s rapidly evolving threat landscape. Traditional intelligence gathering methods are no longer sufficient to meet the demands of modern warfare and national security operations. Consequently, military OSINT tools have become essential components of defense modernization initiatives, offering capabilities that transform how contractors support military operations worldwide.
The integration of advanced open source intelligence platforms enables military contractors to process vast amounts of publicly available information in real-time. These tools provide critical insights for mission planning, threat assessment, and operational security. Moreover, they offer cost-effective solutions that complement classified intelligence sources while maintaining compliance with stringent defense regulations.
Recent developments in artificial intelligence and machine learning have revolutionized OSINT capabilities for military applications. These technologies enable automated data collection, pattern recognition, and predictive analytics that support decision-making at operational and strategic levels. Furthermore, modern military OSINT tools integrate seamlessly with existing command and control systems, enhancing overall operational effectiveness.
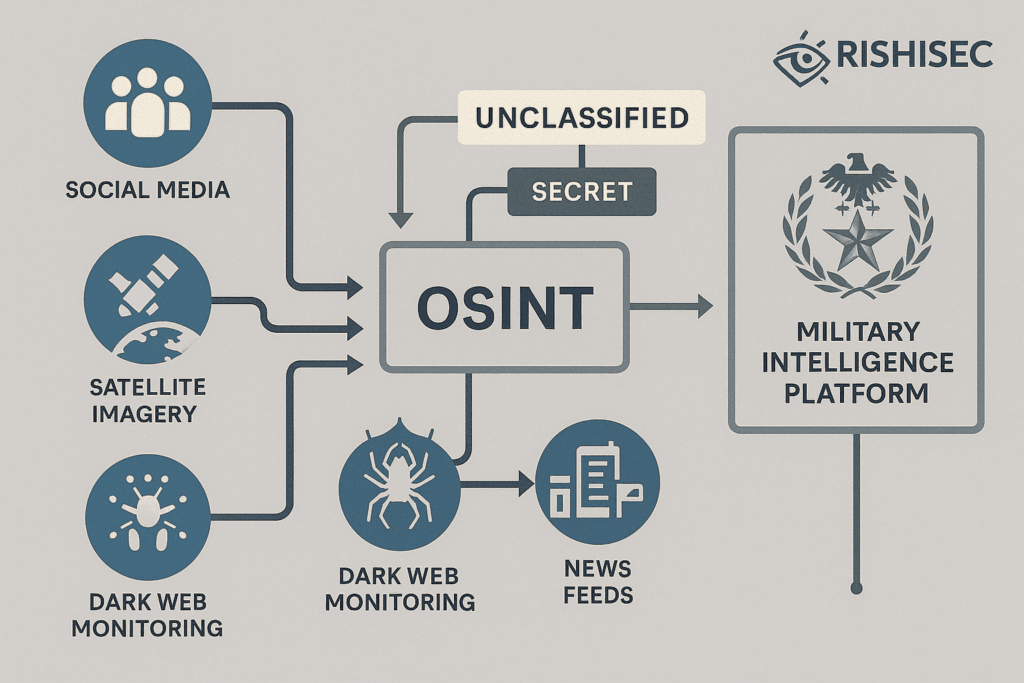
Essential Military OSINT Tools Capabilities for Defense Contractors
Modern military contractors require OSINT platforms that deliver comprehensive intelligence across multiple domains. These capabilities must address both tactical and strategic requirements while ensuring compliance with defense acquisition regulations and security protocols. Additionally, tools must provide scalable solutions that adapt to changing mission requirements and operational environments.
Advanced geospatial intelligence capabilities represent a cornerstone of military OSINT tools. These features enable contractors to analyze satellite imagery, track infrastructure changes, and monitor regional developments that impact mission planning. Similarly, social media intelligence capabilities provide insights into public sentiment, threat indicators, and information warfare campaigns that affect operational security.
Network analysis and link analysis functionalities are crucial for understanding complex relationships between entities, organizations, and individuals. Tools like Kindi excel in this area, providing military contractors with AI-powered link analysis capabilities that accelerate investigation timelines and enhance collaborative intelligence analysis across defense teams.
Core Military OSINT Tool Requirements
- Multi-Source Data Integration: Seamlessly combine intelligence from social media, news sources, government databases, and technical repositories into unified analytical environments.
- Real-Time Monitoring: Continuously track developments across global information sources with automated alerting for critical intelligence indicators and warnings.
- Geospatial Analysis: Process satellite imagery, mapping data, and location-based intelligence to support operational planning and situational awareness requirements.
- Automated Translation: Provide real-time translation capabilities for foreign language sources to ensure comprehensive global intelligence coverage.
- Secure Collaboration: Enable secure information sharing and collaborative analysis across distributed military contractor teams and government partners.
Implementation Strategies for Military OSINT Tools
Successful implementation of military OSINT tools requires comprehensive planning that addresses technical, operational, and compliance requirements. Military contractors must develop implementation strategies that align with defense acquisition frameworks while ensuring seamless integration with existing intelligence architectures. Furthermore, these strategies must account for personnel training, security protocols, and ongoing maintenance requirements.
The implementation process begins with a thorough requirements analysis that identifies specific intelligence gaps and operational needs. This analysis should evaluate current capabilities, assess technological limitations, and define success metrics for OSINT tool deployment. Additionally, contractors must consider interoperability requirements with government systems and partner organizations.
Phased deployment approaches minimize implementation risks while enabling continuous improvement based on user feedback and operational experience. These approaches typically begin with pilot programs that test core functionalities before expanding to full operational deployment. Moreover, they allow for iterative refinement of workflows and procedures that maximize tool effectiveness.

Key Implementation Phases
- Assessment and Planning: Conduct comprehensive needs analysis, define requirements, and develop implementation roadmaps that align with military objectives and compliance standards.
- Pilot Testing: Deploy limited-scope implementations to validate capabilities, test integration points, and refine operational procedures before full deployment.
- Training and Certification: Provide comprehensive training programs that ensure personnel can effectively utilize OSINT tools while maintaining security protocols and best practices.
- Full Deployment: Execute organization-wide implementation with continuous monitoring, performance optimization, and user support to ensure operational success.
Compliance and Security Considerations for Military OSINT
Military contractors operating OSINT tools must navigate complex compliance requirements that govern defense information systems and intelligence operations. These requirements encompass data handling procedures, security classifications, and access controls that protect sensitive military information. Additionally, contractors must ensure OSINT operations comply with applicable laws and regulations governing intelligence collection and analysis.
Security architecture design plays a critical role in military OSINT tool deployment. These systems must implement robust access controls, data encryption, and network security measures that protect against cyber threats and unauthorized access. Furthermore, they must support multiple security classifications and enable secure information sharing across different clearance levels.
Regular security assessments and compliance audits ensure ongoing adherence to defense security standards and regulatory requirements. These assessments evaluate system configurations, user access patterns, and data handling procedures to identify potential vulnerabilities or compliance gaps. Moreover, they support continuous improvement efforts that enhance security postures and operational effectiveness.
For military contractors working with military teams to boost threat intelligence and battlefield awareness, understanding these compliance frameworks becomes essential for successful OSINT program implementation and sustainment.
| Compliance Area | Key Requirements | Implementation Considerations |
|---|---|---|
| NIST Cybersecurity Framework | Risk management, security controls, incident response | Comprehensive security architecture design and monitoring |
| DFARS Requirements | Controlled unclassified information protection | Data classification and access control implementation |
| FISMA Compliance | Information system security and authorization | Security assessment and authorization procedures |
Advanced Capabilities and Future Trends in Military OSINT
The future of military OSINT tools lies in advanced artificial intelligence capabilities that enhance analytical speed and accuracy while reducing analyst workload. Machine learning algorithms can process vast datasets to identify patterns and relationships that human analysts might miss. Additionally, natural language processing capabilities enable automated analysis of multilingual content from diverse global sources.
Predictive analytics represent a significant advancement in military OSINT capabilities. These tools can forecast potential threats, assess conflict probability, and predict adversary behavior based on historical patterns and current intelligence indicators. Furthermore, they support proactive decision-making that enables military contractors to anticipate and prepare for emerging challenges.
Integration with emerging technologies such as quantum computing and advanced sensors will further enhance OSINT capabilities for military applications. These technologies promise unprecedented processing power and data collection capabilities that will transform intelligence operations. Moreover, they will enable new analytical approaches that provide deeper insights into complex security environments.
Emerging Military OSINT Trends
- AI-Powered Threat Detection: Advanced machine learning algorithms that automatically identify and classify threats from open source intelligence across multiple domains and languages.
- Quantum-Enhanced Processing: Next-generation computing capabilities that enable real-time analysis of massive datasets with unprecedented speed and accuracy.
- Augmented Reality Visualization: Immersive analytical environments that enable intuitive data exploration and collaborative intelligence analysis for military applications.
- Autonomous Intelligence Collection: Self-directed OSINT systems that automatically adapt collection strategies based on changing intelligence requirements and emerging threats.
Building Effective Military OSINT Programs
Successful military OSINT programs require comprehensive organizational support that extends beyond technology deployment. Military contractors must establish governance structures, training programs, and operational procedures that ensure sustainable program success. Additionally, they must develop metrics and evaluation frameworks that demonstrate program value and support continuous improvement efforts.
Personnel development represents a critical success factor for military OSINT programs. Analysts require specialized training in open source collection techniques, analytical methodologies, and tool-specific capabilities. Furthermore, they need ongoing professional development that keeps pace with evolving technologies and threat environments.
Quality assurance processes ensure OSINT outputs meet military standards for accuracy, timeliness, and relevance. These processes include validation procedures, peer review mechanisms, and feedback systems that maintain analytical rigor. Moreover, they support credibility and reliability that are essential for military decision-making processes.
For organizations implementing comprehensive OSINT programs, understanding how to effectively integrate OSINT to prioritize alerts and unmask real threats in SOC environments becomes crucial for maximizing operational effectiveness and resource utilization.
Program Success Factors
- Executive Leadership Support: Secure organizational commitment and resources necessary for successful OSINT program implementation and long-term sustainability.
- Cross-Functional Integration: Establish collaborative relationships between intelligence, operations, and technology teams to ensure comprehensive program effectiveness.
- Continuous Training: Implement ongoing education programs that develop analytical skills and maintain proficiency with evolving OSINT tools and techniques.
- Performance Measurement: Develop metrics and evaluation frameworks that demonstrate program value and identify opportunities for improvement and optimization.
The modernization of military OSINT tools represents a critical capability enhancement for defense contractors operating in today’s complex security environment. These tools provide essential intelligence capabilities that support mission success while ensuring compliance with stringent military requirements. Success requires careful planning, comprehensive implementation, and ongoing commitment to excellence in intelligence operations.
Want to strengthen your OSINT skills and enhance your military intelligence capabilities? Check out our OSINT courses for practical, hands-on training. Ready to experience AI-powered OSINT automation designed for military applications? Explore Kindi and discover how it can transform your defense intelligence operations.
FAQ
What are the key differences between military and civilian OSINT tools?
Military OSINT tools incorporate enhanced security features, classification handling capabilities, and compliance with defense regulations such as DFARS and NIST frameworks. They also provide specialized analytical capabilities for threat assessment, geospatial intelligence, and multilingual content analysis that are specifically designed for military operations and requirements.
How do military contractors ensure OSINT tool compliance with defense regulations?
Contractors must implement comprehensive compliance programs that include security assessments, regular audits, personnel clearance verification, and adherence to data handling procedures. Additionally, they must maintain current certifications, document compliance procedures, and provide ongoing training to ensure all personnel understand and follow applicable regulations and security protocols.
What training requirements exist for military OSINT tool operators?
Military OSINT operators typically require security clearances, specialized training in intelligence analysis methodologies, and certification in tool-specific programs. Training should cover collection techniques, analytical frameworks, legal and ethical considerations, and technical proficiency with OSINT platforms. Ongoing professional development ensures operators maintain current skills and knowledge.
How can military contractors measure the effectiveness of their OSINT programs?
Effectiveness metrics should include intelligence production timeliness, analytical accuracy, operational impact assessment, and cost-effectiveness analysis. Contractors should establish baseline measurements, track key performance indicators, conduct user satisfaction surveys, and evaluate program contributions to mission success and decision-making processes.
What are the main challenges in modernizing military OSINT capabilities?
Key challenges include budget constraints, technology integration complexity, personnel training requirements, and compliance with evolving regulations. Additionally, contractors must address interoperability issues, maintain security standards, and balance modernization needs with operational continuity while ensuring all implementations meet stringent military requirements and standards.




